Security Advisory 0105
Date: October 29, 2024
| Revision | Date | Changes |
|---|---|---|
| 1.0 | October 29, 2024 | Initial release |
Description
Multiple vulnerabilities exist for the Arista Edge Threat Management - Arista NG Firewall (NGFW):
1) Description: A user with administrator privileges can perform command injection
CVE: CVE-2024-9131 (ZDI-CAN-24015)
CVSSv3.1 Base Score: 7.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
Common Weakness Enumeration: CWE-88: Improper Neutralization of Argument Delimiters in a Command ('Argument Injection')
This vulnerability is being tracked by NGFW-14800
2) Description: The administrator is able to configure an insecure captive portal script
CVE: CVE-2024-9132 (ZDI-CAN-24019)
CVSSv3.1 Base Score: 8.1 (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H)
Common Weakness Enumeration: CWE-94: Improper Control of Generation of Code ('Code Injection')
This vulnerability is being tracked by NGFW-14744
3) Description: A user with administrator privileges is able to retrieve authentication tokens
CVE: CVE-2024-9133 (ZDI-CAN-24324)
CVSSv3.1 Base Score: 6.6 (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:L)
Common Weakness Enumeration: CWE-287: Improper Authentication
This vulnerability is being tracked by NGFW-14800
4) Description: Multiple SQL Injection vulnerabilities exist in the reporting application. A user with advanced report application access rights can exploit the SQL injection, allowing them to execute commands on the underlying operating system with elevated privileges.
CVE: CVE-2024-9134 (ZDI-CAN-24325)
CVSSv3.1 Base Score: 8.3 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:L)
Common Weakness Enumeration: CWE-89: Improper Neutralization of Special Elements used in an SQL Command
This vulnerability is being tracked by NGFW-14721
5) Description: Expired and unusable administrator authentication tokens can be revealed by units that have timed out from ETM access
CVE: CVE-2024-47517
CVSSv3.1 Base Score: 6.8 (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:L/A:L)
Common Weakness Enumeration: CWE-1230: Exposure of Sensitive Information Through Metadata
This vulnerability is being tracked by NGFW-14754
6) Description: Specially constructed queries targeting ETM could discover active remote access sessions
CVE: CVE-2024-47518
CVSSv3.1 Base Score: 6.4 (CVSS:3.1AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:L/A:L/)
Common Weakness Enumeration: CWE-552: Files or Directories Accessible to External Parties
This vulnerability is being tracked by NGFW-14626
7) Description: Backup uploads to ETM subject to man-in-the-middle interception
CVE: CVE-2024-47519 CVSSv3.1 Base Score: 8.3 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:L)
Common Weakness Enumeration: CWE-322: Key Exchange without Entity Authentication
This vulnerability is being tracked by NGFW-14708
8) Description: A user with advanced report application access rights can perform actions for which they are not authorized
CVE: CVE-2024-47520
CVSSv3.1 Base Score: 7.6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:L)
Common Weakness Enumeration: CWE-653: Improper Isolation or Compartmentalization
This vulnerability is being tracked by NGFW-14707
9) Description: Specially constructed queries cause cross platform scripting leaking administrator tokens
CVE: CVE-2024-9188 (ZDI-CAN-24407)
CVSSv3.1 Base Score: 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H)
Common Weakness Enumeration: unknown
This vulnerability is being tracked by NGFW-14822
Arista would like to acknowledge and thank Mehmet INCE from PRODAFT.com, working with Trend Micro's Zero Day Initiative for responsibly reporting CVE-2024-9131, CVE-2024-9132, CVE-2024-9133, CVE-2024-9134, CVE-2024-47517,CVE-2024-47519, CVE-2024-47520, and CVE-2024-47521.
We would also like to acknowledge and thank Gereon Huppertz, working with Trend Micro's Zero Day Initiative for responsibly reporting CVE-2024-9188
Vulnerability Assessment
Affected Software
- Arista Edge Threat Management - Arista NG Firewall Versions
- 17.1.1 and prior
Affected Platforms
- Arista Edge Threat Management - Arista NG Firewall (Formerly Untangle)
- Arista EOS-based products:
- 710 Series
- 720D Series
- 720XP/722XPM Series
- 750X Series
- 7010 Series
- 7010X Series
- 7020R Series
- 7130 Series running EOS
- 7150 Series
- 7160 Series
- 7170 Series
- 7050X/X2/X3/X4 Series
- 7060X/X2/X4/X5/X6 Series
- 7250X Series
- 7260X/X3 Series
- 7280E/R/R2/R3 Series
- 7300X/X3 Series
- 7320X Series
- 7358X4 Series
- 7368X4 Series
- 7388X5 Series
- 7500E/R/R2/R3 Series
- 7800R3/R4 Series
- 7700R4 Series
- AWE 5000 Series
- AWE 7200R Series
- CloudEOS
- cEOS-lab
- vEOS-lab
- CloudVision eXchange, virtual or physical appliance
- Arista Wireless Access Points
- CloudVision CUE, virtual appliance or physical appliance
- CloudVision CUE cloud service delivery
- CloudVision Portal, virtual appliance or physical appliance
- CloudVision as-a-Service
- CloudVision AGNI
- Arista 7130 Systems running MOS
- Arista Converged Cloud Fabric and DANZ Monitoring Fabric (Formerly Big Switch Nodes for BCF and BMF)
- Arista Network Detection and Response (NDR) Security Platform (Formerly Awake NDR)
- Arista NetVisor OS, Arista NetVisor UNUM, and Insight Analytics (Formerly Pluribus)
Required Configuration for Exploitation, Indicators of Compromise and Mitigation Options
To determine if you are vulnerable to and to mitigate, see the following:
1) CVE-2024-9131 (ZDI-CAN-24015) - A user with administrator privileges can perform command injection
Required Configuration for Exploitation
No required configuration.
Indicators of Compromise
Any compromise will reveal itself via unapproved processes, A typical unapproved process might be an a reverse shell attempt that could look like the following:
# ps awwwux | grep [n]vlp root 23100 0.0 0.0 2464 1784 pts/1 S+ 12:02 0:00 nc -nvlp 1337
Mitigation
No known mitigation.
2) CVE-2024-9132 (ZDI-CAN-24019) - The administrator is able to configure an insecure captive portal script
Required Configuration for Exploitation
- As the NGFW administrator, log into the user interface and navigate to the Apps and Services page.
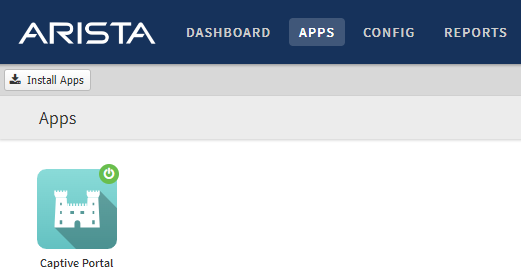
- If you do not see the Captive Portal application, it is not installed and the system is not
- vulnerable.
- Click the Captive Portal application
- If you see the status that Captive Portal is disabled, the system is not vulnerable.
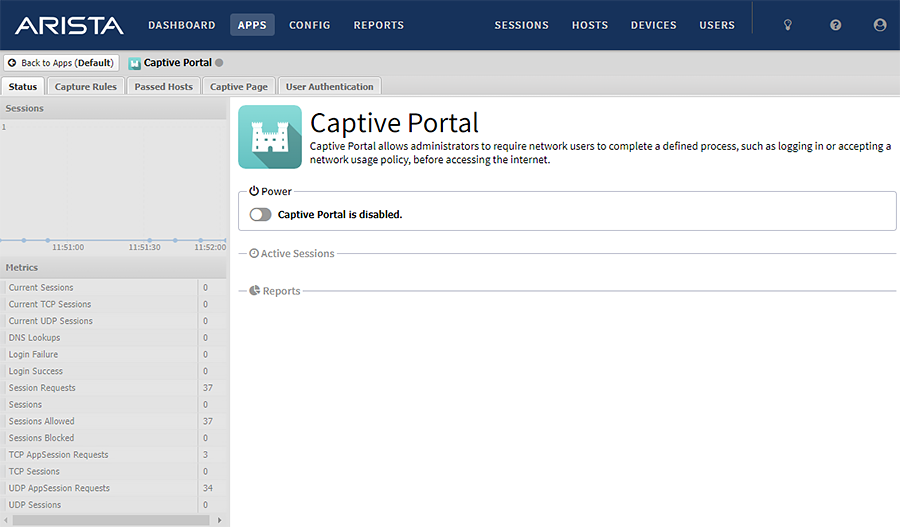
- Click the Captive Page tab.
- If the Custom radio button is not selected, the system is not vulnerable.
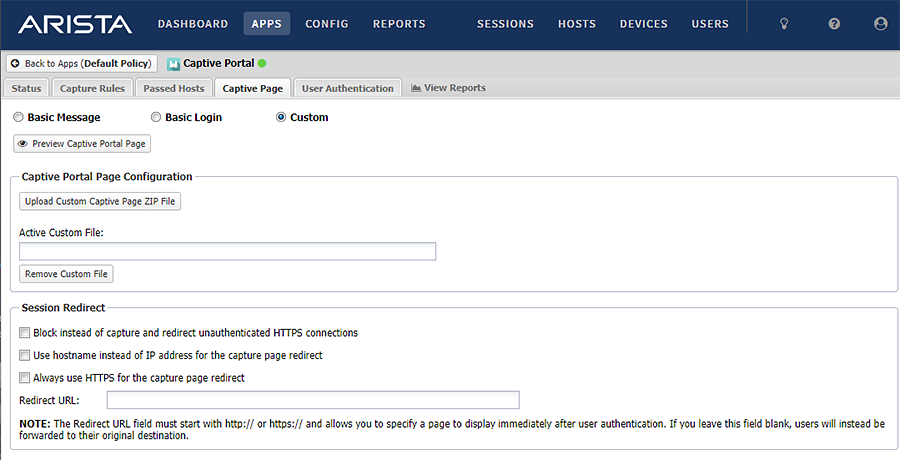
An example of a vulnerable page (The “Custom” radio button is selected)
Indicators of Compromise
Any compromise will reveal itself via unapproved processes. A typical unapproved process might be an a reverse shell attempt that could look like the following:
# ps awwwux | grep [n]vlp root 23100 0.0 0.0 2464 1784 pts/1 S+ 12:02 0:00 nc -nvlp 1337
Mitigation
- As the NGFW administrator, log into the UI and navigate to the Captive Portal application.
- Select either “Basic Message” or “Basic Login”
- Click Save.
3) CVE-2024-9133 (ZDI-CAN-24324) - A user with administrator privileges is able to retrieve authentication tokens
Required Configuration for Exploitation
No required configuration.
Indicators of Compromise
Any compromise will reveal itself via unapproved processes, A typical unapproved process might be an a reverse shell attempt that could look like the following:
# ps awwwux | grep [n]vlp root 23100 0.0 0.0 2464 1784 pts/1 S+ 12:02 0:00 nc -nvlp 1337
Mitigation
No known mitigation.
4) CVE-2024-9134 (ZDI-CAN-24325) - Multiple SQL Injection vulnerabilities exist in the reporting application.
Required Configuration for Exploitation
If the NGFW has one or more Report application Report Users with Online Access enabled they are vulnerable.
- As the NGFW administrator, log into the UI and navigate to the Reports application.
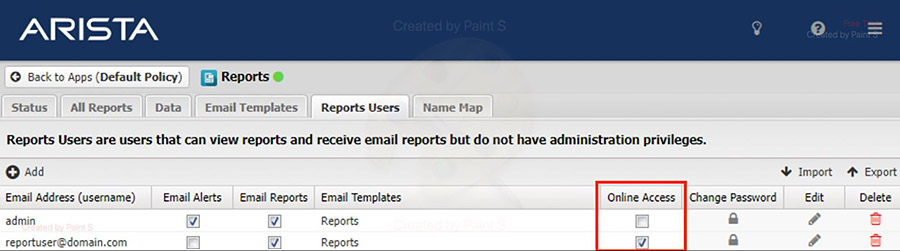
The above picture shows the configuration panel for user access. The “このメールアドレスはスパムボットから保護されています。閲覧するにはJavaScriptを有効にする必要があります。” user has “Online Access” checked, which is required in order to be vulnerable.
Indicators of Compromise
Any compromise will reveal itself via the postgres user running a non-standard postgres process.
For example, an appropriate process list for running the postgres database will look like:
# ps -u postgres -f UID PID PPID C STIME TTY TIME CMD postgres 94057 1 0 Feb06 ? 00:00:00 /usr/lib/postgresql/13/bin/postgres -D /var/lib/postgresql/13/main -c config_file=/etc/postgresql/13/main/postgresql.conf postgres 94063 94057 0 Feb06 ? 00:00:02 postgres: 13/main: checkpointer postgres 94064 94057 0 Feb06 ? 00:00:00 postgres: 13/main: background writer postgres 94065 94057 0 Feb06 ? 00:00:12 postgres: 13/main: walwriter postgres 94066 94057 0 Feb06 ? 00:00:00 postgres: 13/main: autovacuum launcher postgres 94067 94057 0 Feb06 ? 00:00:01 postgres: 13/main: stats collector postgres 94068 94057 0 Feb06 ? 00:00:00 postgres: 13/main: logical replication launcher
Additional processes run by the postgres user indicating a potential compromise may look like:
postgres 100172 100171 0 Feb06 pts/2 00:00:00 bash
Mitigation
For the Reports application, for all Reports Users, disable Online Access.
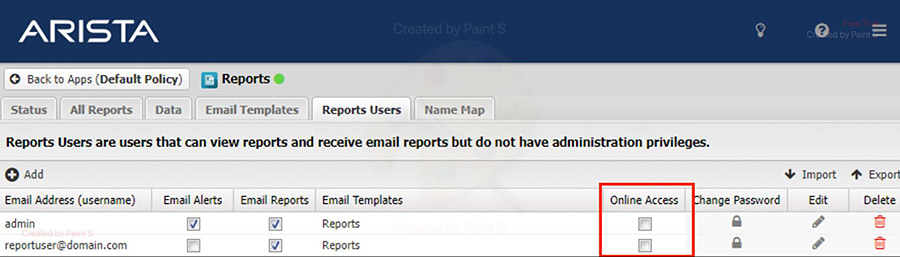
- As the NGFW administrator, log into the UI and go to the Reports application.
- For all users with the Online Access checkbox (red box) enabled, uncheck it.
- Click Save.
5) CVE-2024-47517 - Expired and unusable administrator authentication tokens can be revealed by units that have timed out from Edge Threat Management (ETM) access
Required Configuration for Exploitation
- Log into Edge Threat Management (ETM).
- Go to Appliances, and click your target NGFW.
- On the NGFW appliance page, click Remote Access.
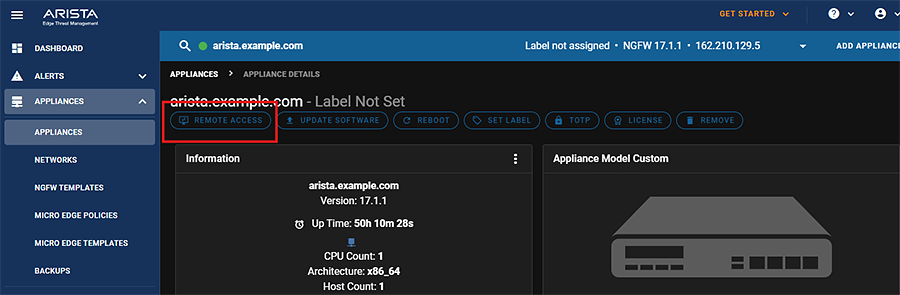
- With the NGFW UI in a new tab or window, let the connection expire.
- After the session has expired, any attempt to perform actions will notify you of the need to enable Remote Access again.
Indicators of Compromise
A specially crafted script pointing to the IP port used by the now expired connection will show recurring queries from the UI.
Mitigation
After you have completed NGFW operations with Remote Access, close the browser window or tab.
6) CVE-2024-47518 - Specially constructed queries targeting Edge Threat Management (ETM) could discover active remote access sessions
Required Configuration for Exploitation
- Log into Edge Threat Management (ETM).
- Go to Appliances, and click your target NGFW.
- On the NGFW appliance page, click Remote Access.

- Leave the connection running.
Indicators of Compromise
- As the NGFW administrator, log into the UI and go to the Reports.
- Under Administration, click Admin Login Events
- Invalid login attempts may appear as failed logins with an “invalid password” reason such as:
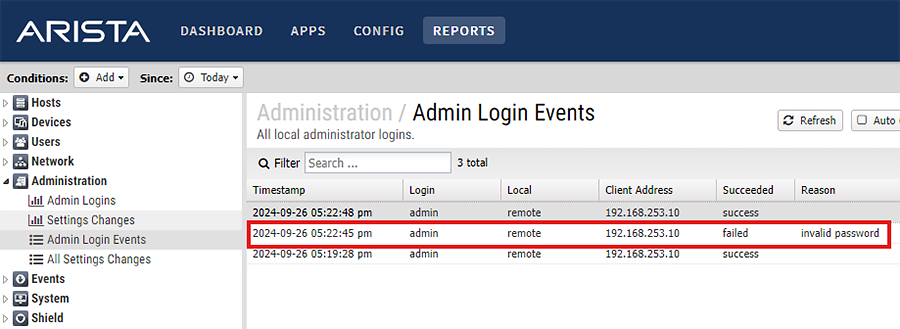
Mitigation
After you have completed your Remote Access session, close the NGFW window.
7) CVE-2024-47519 - Backup uploads to ETM subject to man-in-the-middle interception
Required Configuration for Exploitation
- As the NGFW administrator, log into the user interface and navigate to the Apps and Services page.

- If you do not see the Configuration Backup service application, it is not installed and the system is not vulnerable.
- Click the Configuration Backup application
- If you see the status that Configuration Backup is disabled, the system is not vulnerable.
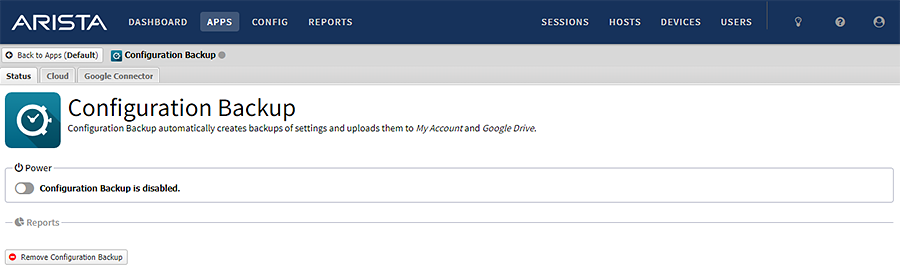
- Click the Cloud tab.
- Click Backup Now.
- Log into Edge Threat Management.
- Go to Appliances and Backups.
- Verify that you see a new backup.
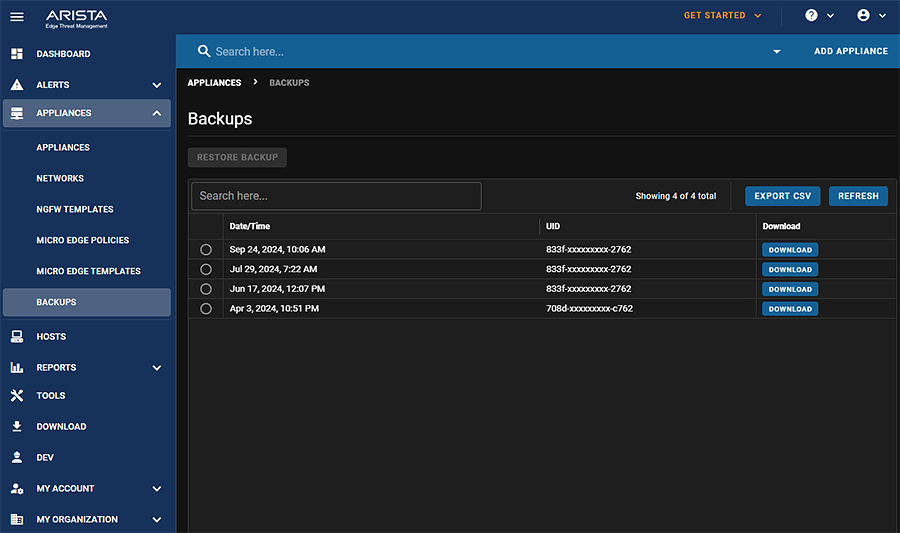
Indicators of Compromise
If you do not see a backup in the above list, you may be compromised.
Mitigation
Disable Configuration Backup application.
8) CVE-2024-47520 - A user with advanced report application access rights can perform actions for which they are not authorized
Required Configuration for Exploitation
If the NGFW has one or more Report application Report Users with Online Access enabled they are vulnerable.
- As the NGFW administrator, log into the UI and navigate to the Reports application.

The above picture shows the configuration panel for user access. The “このメールアドレスはスパムボットから保護されています。閲覧するにはJavaScriptを有効にする必要があります。” user has “Online Access” checked, which is required in order to be vulnerable.
Indicators of Compromise
- As the NGFW administrator, log into the UI and go to the Reports.
- Under Administration, click All Settings Changes
- Compromised settings for a このメールアドレスはスパムボットから保護されています。閲覧するにはJavaScriptを有効にする必要があります。 would appear as:
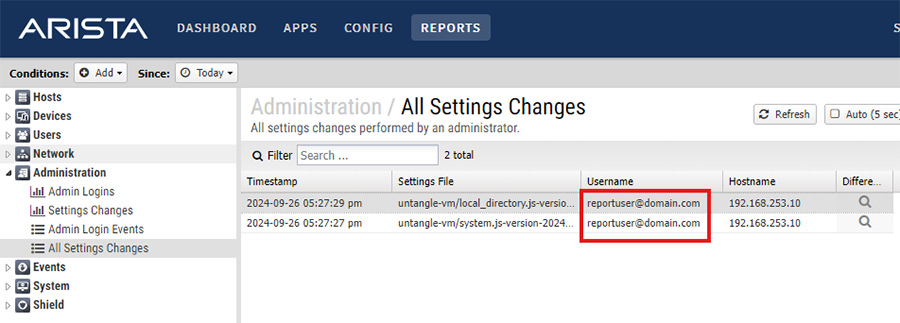
Mitigation
For the Reports application, for all Reports Users, disable Online Access.

- As the NGFW administrator, log into the UI and go to the Reports application.
- For all users with the Online Access checkbox (red box) enabled, uncheck it.
- Click Save.
9) CVE-2024-9188 (ZDI-CAN-24407) - Specially constructed queries cause cross platform scripting leaking administrator tokens
Required Configuration for Exploitation
No required configuration.
Indicators of Compromise
- As the NGFW administrator, log into the UI and go to the Reports.
- Under Administration, click All Settings Changes
- Compromised settings changes from this exploit would appear from a hostname IP address that you have not logged in from such as:
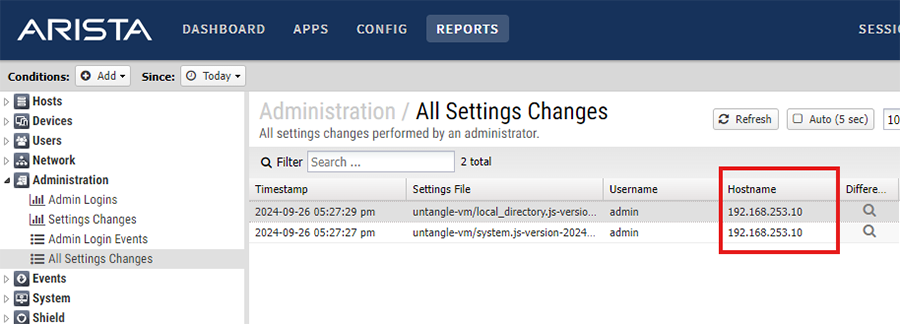
Mitigation
No known mitigation.
Resolution
- 17.2 Upgrade
For More Information
If you require further assistance, or if you have any further questions regarding this security notice, please contact the Arista Networks Technical Assistance Center (TAC) by one of the following methods:
Open a Service Request
Contact information needed to open a new service request may be found at: https://www.arista.com/en/support/customer-support
