EVPN Multicast VRF Leaking
Overview
EVPN Multicast virtual routing and forwarding (VRF) Leaking forwards multicast traffic from a sender in a tenant or external domain (VRF) to a different domain (VRF) with connected receivers. The source VRF refers to the VRF of the multicast sender, and the receiver VRF refers to the VRF of the multicast receiver.
Typically, a multicast receiver sends IGMP messages to a multicast stream, and a last hop router converts the IGMP message to a Protocol Independent Multicast (PIM) message and propagates them upstream on the network. When a VRF receives an IGMP or PIM message, a corresponding VRF leak occurs where the IGMP or PIM messages leak to the source VRF, which the source VRF processes. The corresponding EVPN Selective Multicast Ethernet Tag (SMET) route originates with the Supplementary Broadcast Domain (SBD) route target of the VRF and the route distinguisher (RD) where the sources connect. The receiver VRF RT and RD do not originate SMET routes.
When configuring EVPN Multicast VRF Leaking, the source VRF contains the Multicase Outgoing Interface (OIF) list of multicast routes from the receiver VRF. When the source VRF forwards traffic, the VRF sends a copy of the OIF list across the VRF.
EVPN Multicast VRF Leaking supports a per multicast group configuration to leak multicast traffic.
In the following EVPN topology, two VRF tenants, red and blue, have multicase receivers and senders. The receiver, Rb1, on the blue VRF looks for group G on VRF, red, which has the resources. To enable the feature, configure VRF Leaking for group G on the PE connected to the Rb1 with VRF red as the source VRF.
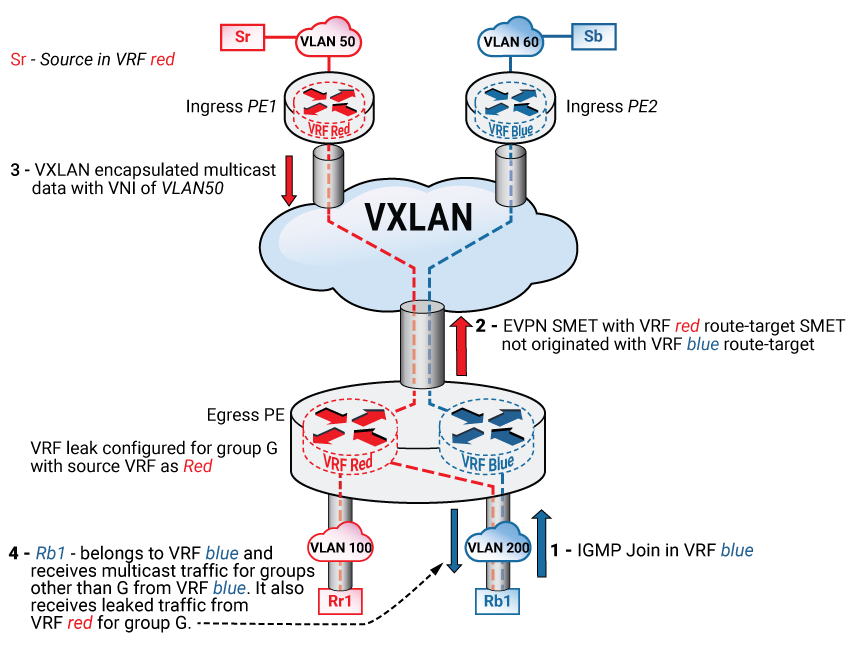
- Rb1 sends an IGMP join request for (*,G), and the host device is unaware of VRF Leaking.
- VRF blue has the configuration for VRF Leaking for G, so the egress Provider Edge (PE) router sends a SMET to the red VRF, and does not send a SMET to the blue VRF or the VLAN100.
- The ingress PE connected to the source on VRF red, sends VXLAN-encapsulated multicast packets with the VNI of the source VLAN across the EVPN core.
- The egress PE receives the VXLAN packet, decapsulates it, and routes the data packet to VRF blue.
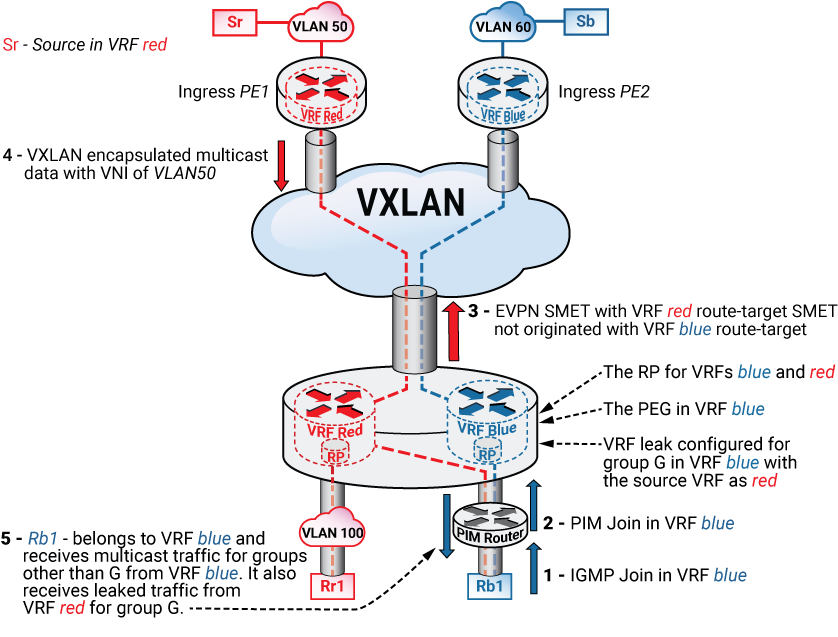
EVPN Multicast VRF Leaking with a PIM EVPN Gateway (PEG)
On an EVPN network with a PEG role, the PEG acts as the rendezvous point (RP) for the leaked groups. The PEG also functions as the Rendezvous Point (RP) of the source VRF, which follows the PIM network model, where the PEG acts as the RP of the source and receiver VRFs. The configuration requires synchronization using a protocol such as Multicast Source Discovery Protocol (MSDP), and the source synchronization may be necessary with the source and receiver VRFs.
If an RP exists in the external PIM domain, then Multicast VRF Leaking can be configured on that RP instead of the PEG, but this requires that both the source and receiver VRFs extend into the PIM domain that includes the RP.
In this case, the sources on the EVPN tenant VRFs exist in a different VRF from the RP, and the unicast route leaks to the source from the tenant VRF into the external domain VRF to build the multicast trees and perform Reverse Path Forwarding (RPF) validation.
Using MLAG as a PEG on an EVPN Network
When configuring VRF Leaking on MLAG devices used as PEGS, configure the MLAG devices as a PEG in both the receiver VRF and the source VRF. Typically, the external PIM domain connects to the receiver. To enable PEG functionality on the source VRF, configure a stub VLAN and a corresponding SVI on both MLAG peers. Enable PIM on the SVIs of both peers and attach them to the source VRF. This enables PEG functionality in the source VRF as well.
