Test Access Point Aggregation
This section describes Test Access Point (TAP) aggregation and the data structures that it requires. Topics in this section include:
- TAP Aggregation Introduction
- TAP Aggregation Description
- TAP Aggregation Extra MPLS Pop (4 to 6 Labels)
- TAP Aggregation Configuration
- TAP Aggregation Traffic Steering
- TAP Aggregation GUI
- TAP Aggregation Keyframe and Timestamp Configuration
- TapAgg GRE Tunnel Termination
- Tap Aggregation Hardware Forwarding Profile
- TAP Aggregation MPLS Pop
- TAP Aggregation 802.1br EVN Tag Stripping
- TAP Aggregation Commands
TAP Aggregation Introduction
Ethernet-based switches are commonly deployed in dedicated networks to support Test Access Point (TAP) and mirror port traffic toward one or more analysis applications. Ports configured to mirror data can simultaneously switch traffic to its primary destination while directing a copy of that traffic to analysis or test devices. TAP ports are typically part of a dedicated environment that allows for the aggregation of data streams from multiple sources that can be directed to multiple destinations.
Arista switches support port mirroring and TAP aggregation and the data structures required by these functions.
TAP Aggregation Description
TAP Aggregation
Test Access Point (TAP) aggregation is the accumulation of data streams and the subsequent dispersal of these streams to devices and applications that analyze, test, verify, parse, detect, or store data. TAP aggregation requires an environment free from switching operations. Arista switches operate in one of two device modes:
- Switching mode: the switch performs normal switching and routing operations. Data mirroring is supported in switching mode. Tap aggregation is not available in switching mode.
- TAP aggregation mode: The switch is a data-monitoring device and does not
provide normal switching and routing services. Data mirroring is not available in
tap aggregation mode.
Access control lists, port channels, LAGs, QoS, and VLANs function normally in both modes.
Ethernet and port channel interfaces are configured as TAP and tool ports to support tap aggregation.
- TAP ports: a tap port is an interface that receives a data stream that two
network ports exchange.
TAP ports prohibit egress traffic. MAC learning is disabled. All control plane interaction is prevented. Traps for inbound traffic are disabled. Tap ports are in STP forwarding mode.
- Tool ports: A tool port is an interface that replicates data streams received
by one or more tap ports. Tool ports connect to devices that process the monitored
data streams.
Tool ports prohibit ingress traffic. MAC learning is disabled. All control plane interaction is prevented. Tool ports are in STP forwarding mode.
TAP and tool ports are configured with the switchport mode command. These ports are active when the switch is in tap aggregation mode and error-disabled when the switch is in switching mode.
TAP and tool ports are designated through switchport mode commands and act similar to trunk ports, in that they can allow access to VLANs specified through allowed-VLAN lists. Tap ports also specify a native VLAN for handling untagged frames.
Access, trunk, and dot1q-tunnel mode ports are active when the switch is in switching mode and error-disabled when the switch is in tap aggregation mode.
TAP and tool mode ports are active when the switch is in TAP aggregation mode and error-disabled when the switch is in switching mode.
TAP aggregation groups are data structures that map a set of TAP ports to a set of tool ports. Both TAP and tool ports may belong to multiple TAP aggregation groups, and a TAP aggregation group may contain multiple TAP and tool ports.
Timestamps and Keyframes
FM6000 platform switches support packet timestamping of packets sent from any port at line rate. Timestamps are used to correlate network events and in performance analysis. Keyframes provide information to assist in the interpretation of timestamps.
The switch contains two 64-bit counters to maintain ASIC time and UTC time. ASIC time is based on an internal 350 MHz counter. UTC is absolute time that is maintained by a precision oscillator and synchronized through PTP.
Timestamps are derived from the least significant 31 bits of ASIC time. Based on the 350 MHz counter period and 31-bit resolution, timestamp values repeat every 6.135 seconds.
Keyframes are periodically inserted into the data stream to provide context for interpreting timestamps. Keyframes contain the 64-bit value of the ASIC time counter, the corresponding 64-bit value of the UTC time counter, and the elapsed time since the last PTP synchronization of the UTC counter. Inserting one keyframe every second into the data stream assures that the timestamp value in each egress packet can be associated with values of the complete 64-bit ASIC time counter and the corresponding UTC counter.
Timestamps
Timestamps are based on a frame’s ingress time and applied to frames sent on egress ports, ensuring that timestamps on monitored traffic reflect ingress timing of the original frames. Timestamping is configured on the egress port where the timestamp is applied to the frame.
A timestamp consists of the least significant 31 bits of the ASIC time counter. The most significant bit of the least significant byte is a 0 pad, resulting in a 32-bit timestamp with 31 bits of data. The keyframe mechanism provides recovery of the most significant 33 bits of the ASIC counters and a map to UTC time. Applications use this mechanism to determine the absolute time of the frame timestamp.
- Disabled: timestamping is disabled.
- FCS Replacement Mode: the original FCS is discarded, and the ingress timestamp is appended to frame data, followed by a new FCS that is based on the appended timestamp. The result is a valid Ethernet frame, but the headers of all nested protocols are not updated to reflect the timestamp.
- FCS Appending Mode: the original FCS is discarded and replaced by the ingress timestamp. The size of the original frame is maintained without any latency impact, but the FCS is not valid.
Keyframes
- MAC fields (12 bytes):
- Source MAC address is the address of the egress interface transmitting the keyframe.
- Destination MAC address is configured through a CLI command.
- IP Header (20 bytes):
- Source IP address is configured through CLI; default is management interface IP address.
- Destination IP address is configured through a CLI command.
- TTL is set to 64.
- TOS is set to 0.
- Protocol field is set to 253.
- IP header’s ID field is set to 0.
- ASIC time: (64 bits) ASIC time counter. (2.857 ns resolution).
- UTC time:(64 bits) Unix time that corresponds to ASIC time (ns).
- Last sync time: (64 bits) ASIC time of most recent PTP synchronization.
- Keyframe time: (64 bits) ASIC time of the keyframe’s egress (ns).
- Egress interface drops: (64 bits) Number of dropped frames on keyframe’s egress interface.
- Device ID: (16 bits) device ID (user defined).
- Egress interface: (16 bits) Keyframe’s egress switchport.
- FCS type (8 bits): Timestamping mode configured on keyframe’s egress
port.
- 0: timestamping disabled.
- 1: timestamp is appended to payload; new FCS is added to the frame.
- 2: timestamp overwrites the existing FCS.
- Reserved (8 bits): reserved for future use.
- Skew numerator/skew denominator: form a ratio indicating the ASIC clock skew. If the ratio is greater than 1, the clock is skewed fast; if the ratio is less than 1, the clock is skewed slow.
Last sync time equals 0 when there was no previous synchronization or the time since the last synchronization is greater than 8 hours.
The 31-bit frame timestamp provides high-resolution timing, rolling over about every 6.135 seconds (31 bits at 2.857ns per tick). To obtain the full ASIC time and to correlate the timestamp to an absolute UTC time, the switch sends keyframes. Each keyframe contains the current ASIC time and UTC time; hence an application can compute the high order bits of the ASIC time (for precise, relative timing) from the ASIC to UTC time mapping, and then determine absolute time.
ASIC to UTC time conversion is not quite immediate, so the UTC time in the frame will not be the current time. A keyframe timestamp is provided for this purpose. The frame also includes the timestamping mode (FCS type) so applications can dynamically determine the timestamp’s byte offset. Each field is shown in the following table.
| 0 7 | 8 15 | 16 31 |
| ASIC time | ||
| UTC time | ||
| Last sync time | ||
| Skew numerator | ||
| Skew denominator | ||
| Keyframe timestamp | ||
| Drop count | ||
| Device ID | Egress interface | |
| FCS type | Reserved | |
TAP Aggregation Extra MPLS Pop (4 to 6 Labels)
Available starting with EOS Release 4.23.1F extra MPLS pop for TAP Aggregation allows you to remove four to six MPLS labels from a packet. Previously, only one to three labels were able to be popped.
When configured, popping four to six MPLS labels works in all the cases where popping one to three MPLS labels works.
TAP Aggregation Extra MPLS Pop Configuration
MPLS pop is configurable per tap port as follows to pop one to three labels:
Example
(config-if-Et1/1)# switchport tap mpls pop allHowever, MPLS pop for four to six labels requires a user defined TAP Aggregation profile based on off of tap-aggregation-extended. This profile musthave one action and three fields configured under the tapagg port feature, such as the following:
Example
(config)# hardware tcam
(config-hw-tcam)# profile foo copy tap-aggregation-extended
(config-profile-foo)# feature tapagg port
(config-profile-foo-feature-tapagg-port)# action set-fwd-header
(config-profile-foo-feature-tapagg-port)# key field mpls-label1-lower-24b mpls-label2-lower-24b mpls-label3-lower-24b
(config-profile-foo-feature-tapagg-port)# tap aggregation
Saving new profile 'foo'
(config-tap-agg)# mode exclusive profile fooWith the above profile changes, four to six MLPS label pop is additionally supported when the MPLS pop feature is configured on a tap port.
To check if a profile is installed correctly, use the show hardware tcam profile command.
Example
(config-tap-agg)# show hardware tcam profileUpon successful installation of a TAP Aggregation profile, you should see a display similar to the following:
Example
Configuration Status
FixedSystem foo* foo
* configuration overridden by TapAggConfiguring a Local LFIB Convergence Delay for Protected Node or Adjacency Segments
The Point of Local Repair (PLR) switches to the TI-LFA backup path on link failure or BFD neighbor failure but switches back to the post-convergence path once the PLR computes SPF and updates its LFIB. This sequence of events can lead to micro-loops in the topology if the PLR converges faster than other routers along the post-convergence path. So a configuration option is provided to apply a delay, after which the LFIB route being protected by the TI-LFA loop-free repair path will be replaced by the post-convergence LFIB route.
To configure a convergence delay only to LFIB routes that are being protected, the following command is used either in the router IS-IS mode or the router IS-IS address-family sub-mode. A default of 10 seconds is used when using the command without an explicitly specified delay.
Example
switch(config-router-isis-af)# timers local-convergence-delay [<delay_in_milliseconds>] protected-prefixesLimitations
IP Steering
IP steering does not work for MPLS packets with four or more labels. Currently, you must work around this limitation with a configuration similar to the Configuration for IP Steering. This workaround does not work when MPLS pop is not enabled.
Configuration for IP Steering
When MPLS pop is enabled, you can enable IP steering for for to six MPLS labels by adding an extra port into the configuration as a tap-tool port.
For example,you want to perform IP steering from interface Ethernet1 to a set of interfaces and also want MPLS labels to be popped. Add a new interface Ethernet2, which will not receive any external traffic, as a tap-tool port with traffic loopback. Then configure Ethernet1 to forward to Ethernet2 as its default interface. The commands would look similar to the following:
Example
(config-if-Et2)# swi mode tap-tool
(config-if-Et2)# traffic-loopback source system device phy
(config-if-Et2)# int et1
(config-if-Et1)# swi tap default interface et2All of Ethernet1’s old tool ports should be disabled and become Ethernet2’s tool ports. Then, all IP steering configuration that was originally meant to be between ET1 and its old tool ports should be configured with Ethernet2 in place of Ethernet1. Finally, configure MPLS pop on Ethernet1.
TAP Aggregation Extra MPLS POP (4 to 6 Labels) Commands
TAP Aggregation Configuration
Enabling Tap Aggregation Mode
The switch supports switching mode and TAP aggregation mode. In switching mode, normal switching and routing functions are supported while TAP aggregation functions are disabled. In TAP aggregation mode, TAP aggregation functions are enabled while normal switching and routing functions are disabled. By default, the switch is in switching mode.
- Tap aggregation mode enabled: TAP and tool ports are enabled. Switching ports are errdisabled.
- Tap aggregation mode disabled: TAP and tool ports are errdisabled. Switching ports are enabled.
To enable the switch to carry out TAP aggregation, first enter TAP aggregation configuration mode using the tap aggregation command, then set the mode to tap aggregationexclusive.
Example
switch(config)# tap aggregation
switch(config-tap-agg)# mode exclusive
switch(config-tap-agg)# show active
tap aggregation
mode exclusive
switch(config-tap-agg)#To return the switch to switching mode, remove the mode command from running-config.
- These commands enter TAP aggregation configuration mode, then place the switch in
switching
mode.
switch(config)# tap aggregation switch(config-tap-agg)# no mode switch(config-tap-agg)# show active switch(config-tap-agg)# - These commands enter switching mode and remove all TAP aggregation configuration
mode
statements.
switch(config)# no tap aggregation switch(config)#
TAP Aggregation Mixed Mode
Mixed Mode Platform Compatibility
The following platforms support TAP Aggregation Mixed Mode.
- DCS-7500R
- DCS-7500R2
Mixed Mode Configuration
TAP Port Configuration
TAP ports function when the switch is in TAP aggregation mode. TAP ports receive traffic for replication to one or more tool ports. In TAP aggregation mode, TAP ports are in STP forwarding state and prohibit egress traffic. MAC learning, control plane interaction and traps for inbound traffic are disabled.
TAP mode ports are configured through switchport mode commands. TAP mode command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP aggregation mode.
Configuring an Interface as a Tap Mode Port
Ethernet and port-channel interfaces are configured as TAP ports with the switchport mode command.
Example
switch(config)# interface ethernet 41-43
switch(config-if-Et41-43)# switchport mode tap
switch(config-if-Et41-43)# show interface ethernet 41-43 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et41 tap tap 1 1 0 ---
Et42 tap tap 1 1 0 ---
Et43 tap tap 1 1 0 ---
switch(config-if-Et41-43)#TAP Port Allowed VLAN List Configuration
By default, TAP mode interfaces handle tagged traffic for all VLANs. Thecommand creates or modifies the set of VLANs for which a TAP port handles tagged traffic.
Example
switch(config)# interface ethernet 41
switch(config-if-Et41)# switchport tap allowed vlan 401-410
switch(config-if-Et41)# interface ethernet 42
switch(config-if-Et42)# switchport tap allowed vlan 411-420
switch(config-if-Et41)# interface ethernet 41-42
switch(config-if-Et41-42)# show active
interface Ethernet41
switchport mode tap
switchport tap allowed vlan 401-410
interface Ethernet42
switchport mode tap
switchport tap allowed vlan 411-420
switch(config-if-Et41-42)#TAP Port Native VLAN
Tap mode Interfaces associate untagged frames with the tap mode native VLAN. The switchport tap native vlan command specifies the TAP-mode native VLAN for the configuration-mode interface. The default TAP-mode native VLAN for all interfaces is vlan 41.
Example
switch(config)# interface ethernet 41
switch(config-if-Et41)# switchport tap native vlan 400
switch(config-if-Et41)# show interface ethernet 41-43 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et41 tap tap 400 1 0 ---
Et42 tap tap 1 1 0 ---
Et43 tap tap 1 1 0 ---
switch(config-if-Et41)#TAP Port Packet Truncation
TAP ports can be configured to truncate inbound packets. The switchport tap truncation command configures the configuration-mode interface, as a TAP port, to truncate inbound packets to the specified packet size. By default, TAP ports do not truncate packets.
- These commands configure interface ethernet
41 to truncate packets to
150
bytes.
switch(config)# interface ethernet 41 switch(config-if-Et41)# switchport tap truncation 150 switch(config-if-Et41)# show interface ethernet 41-43 tap Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et41 tap tap 400 1 150 --- Et42 tap tap 1 1 0 --- Et43 tap tap 1 1 0 --- switch(config-if-Et41)# - These commands configure interface ethernet
41 to send complete packets for
replication.
switch(config-if-Et41)# no switchport tap truncation switch(config-if-Et41)# show interface ethernet 41 tap Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et41 tap tap 400 1 0 --- switch(config-if-Et41)#
Tool Port Configuration
Tool ports replicate traffic received by TAP ports. Tool ports are mapped to the TAP ports through TAP aggregation groups. A tool port may belong to multiple aggregation groups and an aggregation group may contain multiple tool ports.
Tool ports function when the switch is in TAP aggregation mode. In this switch mode, tool ports are in STP forwarding state and ingress traffic is prohibited. MAC learning, control plane interaction, and traps for inbound traffic are disabled. All control plane interaction is prevented and L2 agents do not send PDUs to tool-mode interfaces. When the switch is in switching mode, tool ports are error-disabled.
Tool-mode ports are configured through switchport commands. Tool-mode command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP aggregation mode.
Configuring an Interface as a Tool-mode Port
Ethernet and port channel interfaces are configured as tool ports with the switchport mode command.
Example
switch(config)# interface port-channel 101-103
switch(config-if-Po101-103)# switchport mode tool
switch(config-if-Po101-103)# show interface port-channel 101-103 tool
Port Configured Status Allowed Id Timestamp
Mode Vlans Tag Mode
-----------------------------------------------------------------------
Po101 tool tool All Off ---
Po102 tool tool All Off ---
Po103 tool tool All Off ---
switch(config-if-Po101-103)#Tool Port Allowed VLAN List Configuration
By default, tool mode interfaces handle tagged traffic for all VLANs. The switchport tool allowed vlan command creates or modifies the set of VLANs for which a tool port handles tagged traffic.
Example
switch(config)# interface port-channel 101-103
switch(config-if-Po101-103)# switchport tool allowed vlan 1010-1020
switch(config-if-Po101-103)# interface port-channel 101
switch(config-if-Po101)# switchport tool allowed vlan add 1001-1009
switch(config-if-Po103)# interface port-channel 102
switch(config-if-Po102)# switchport tool allowed vlan remove 1016-1020
switch(config-if-Po102)# interface port-channel 103
switch(config-if-Po103)# switchport tool allowed vlan add 1021-1030
switch(config-if-Po103)# show interface port-channel 101-103 tool
Port Configured Status Allowed Id Timestamp
Mode Vlans Tag Mode
-----------------------------------------------------------------------
Po101 tool tool 1001-1020 Off ---
Po102 tool tool 1010-1015 Off ---
Po103 tool tool 1010-1030 Off ---
switch(config-if-Po103)#Tool Port Packet Truncation
Tool ports can be configured to truncate outbound packets. The switchport tool truncation command configures the configuration-mode interface, as a tool port, to truncate outbound packets to 160 bytes. By default, tool ports do not truncate packets.
Tool port packet truncation is supported only on the 7150 series platform.
- These commands configure interface ethernet
41, as a tool port, to truncate
packets on egress to 160
bytes.
switch(config)# interface ethernet 41 switch(config-if-Et41)# switchport mode tool switch(config-if-Et41)# switchport tool truncation 160 switch(config-if-Et41)# - These commands configure interface ethernet
41 to send complete
packets.
switch(config-if-Et41)# no switchport tool truncation switch(config-if-Et41)#
Per-linecard TCAM Profile Configuration
This feature gives the ability to specify different profiles for different linecards in mixed mode.
To enable the TAP aggregation mode and configure a TCAM profile for a linecard set, complete the following steps:
- Enable the switch for
configuration.
switch> configure terminal - Enable TAP aggregation
mode.
switch(config)# tap aggregation - Configure the TCAM profile for a linecard
set.
switch(config-tap-agg)# mode mixed module linecard 3,4 profile tap-aggregation-default switch(config-tap-agg)# mode mixed module linecard 5,6 profile tap-aggregation-extended switch(config-tap-agg)#
To disable TAP aggregation on a linecard set, complete the following steps:
- Enable the switch for
configuration.
switch> configure terminal - Enable TAP aggregation
mode.
switch(config)# tap aggregation - Disable TAP aggregation for a linecard
set.
switch(config-tap-agg)# no mode mixed module linecard 3,4 switch(config-tap-agg)#
Two-Way Ports for TAP Aggregation
Two-Way Ports Platform Compatibility
Two-way ports are available on selected platforms as described here: https://www.arista.com/en/support/product-documentation/supported-features.
Two-Way Ports Configuration
To enable a two-way port, use the tap-tool option of the switchport mode command.
Example
switch(config)# interface ethernet 4/1
switch(config-if-Et4/1)# switchport mode tap-tool
switch(config-if-Et4/1)#Additional configurations for TAP and tool functionality on the interface remain the same. Once the user enables the TAP-tool switchport mode on the interface, they can use the existing TAP and tool mode commands to enable their respective configurations.
Arista recommends using this feature with unidirectional send-receive enabled on the interface, which allows the receiver and transmitter for the interface to operate independently. If one goes down, the other remains active. To enable unidirectional send-receive on an interface, use the unidirectional send-receive command.
Example
switch(config)# interface ethernet 4/1
switch(config-if-Et4/1)# unidirectional send-receive
switch(config-if-Et4/1)#TAP Aggregation QoS Handling on TAP Ports
QoS Handling Platform Compatibility
The following platforms support QoS handling on TAP ports.
- DCS-7280E
- DCS-7280R
- DCS-7500E
- DCS-7500R
- DCS-7280R2
QoS Handling Configuration
Trust Mode of TAP Ports
TAP ports are in QoS untrusted mode by default. This means that the QoS marking of an incoming packet is not trusted when determining the QoS attributes of the packet. Therefore, the default QoS handling takes place. Consider the default CoS to traffic class mapping in the following example.
switch(config)# show qos maps
[...]
Cos-tc map:
cos: 0 1 2 3 4 5 6 7
----------------------------
tc: 1 0 2 3 4 5 6 7
[...]The Class of Service (CoS) field of incoming packets is ignored and is assumed to be zero. In this example, all packets are assigned to traffic class 1 when using the above mapping.
To override the default trust mode behavior on a TAP port, use the qos trust command.
Example
switch(config-if-Et1)# qos trust cos
switch(config-if-Et1)#Class of Service Rewrite of TAP Ports
By default, TAP ports do not override the existing Class of Service (CoS) field of incoming packets. In other words, the CoS marking of steered packets is not changed in any way.
However, the CoS field of added tags may change according to the traffic class to CoS mapping. For example, the identity tag added by TAP ports may have the CoS value from the global traffic class to CoS mapping. Consider the following mapping:
switch(config)# show qos maps
[...]
Tc-cos map:
tc: 0 1 2 3 4 5 6 7
----------------------------
cos: 1 7 2 3 4 5 6 0
[...]Displaying QoS Handling Status
Use the show qos maps command to see the active QoS mappings.
Example
switch# show qos maps
Number of Traffic Classes supported: 8
Number of Transmit Queues supported: 8
Cos Rewrite: Disabled
Dscp Rewrite: Disabled
Cos-tc map:
cos: 0 1 2 3 4 5 6 7
----------------------------
tc: 1 0 2 3 4 5 6 7
Dscp-tc map:
d1 : d2 0 1 2 3 4 5 6 7 8 9
--------------------------------------
0 : 1 1 1 1 1 1 1 1 0 0
1 : 0 0 0 0 0 0 2 2 2 2
2 : 2 2 2 2 3 3 3 3 3 3
3 : 3 3 4 4 4 4 4 4 4 4
4 : 5 5 5 5 5 5 5 5 6 6
5 : 6 6 6 6 6 6 7 7 7 7
6 : 7 7 7 7
Tc-cos map:
tc: 0 1 2 3 4 5 6 7
----------------------------
cos: 1 0 2 3 4 5 6 7
Tc-dscp map:
tc: 0 1 2 3 4 5 6 7
-----------------------------
dscp: 8 0 16 24 32 40 48 56
Tc - tx-queue map:
tc: 0 1 2 3 4 5 6 7
---------------------------------
tx-queue: 0 1 2 3 4 5 6 7
switch#Identity VLAN Tagging
By default, tool port output packets are identical to the replicated packets they receive from the tap ports to which they are associated. Identity tagging modifies packets sent by tool ports by adding a dot1q VLAN tag that identifies the originating TAP port. Each TAP port is associated with an identity number. Tool ports that are configured to add an identity tag append the originating TAP port’s identity number in the outer layer (or s-VLAN) tag.
Tap Port Identity Value Configuration
The switchport tap identity command configures the TAP port identity value for the configuration-mode interface. The default identity value for all TAP ports is 1.
Example
switch(config)# interface ethernet 42
switch(config-if-Et42)# switchport tap identity 1042
switch(config-if-Et42)# show interface ethernet 41-43 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et41 tap tap 400 1 0 ---
Et42 tap tap 1 1042 0 ---
Et43 tap tap 1 1 0 ---
switch(config-if-Et42)#Tool Port Identity Tag Configuration
The switchport tool identity command configures the configuration-mode interface to include a tier-1 VLAN tag (dot1q) in packets it transmits. The VLAN number on the dot1q tag is the identity value configured for the TAP port that supplies the packets. By default, tool ports do not encapsulate packets with the tier-1 VLAN tag.
Example
switch(config)# interface port-channel 102
switch(config-if-Po102)# switchport tool identity dot1q
switch(config-if-Po102)# show interface port-channel 101-103 tool
Port Configured Status Allowed Id Timestamp
Mode Vlans Tag Mode
-----------------------------------------------------------------------
Po101 tool tool 1001-1020 Off ---
Po102 tool tool 1010-1015 On ---
Po103 tool tool 1010-1030 Off ---
switch(config-if-Po102)#TAP Aggregation Group Configuration
TAP aggregation groups associate a set of TAP ports with a set of tool ports. A tool port replicates packets it receives from TAP ports that are in the aggregation groups to which it belongs. A TAP port can be configured to send data to multiple TAP aggregation groups. Tool ports may belong to multiple TAP aggregation groups. TAP aggregation groups may contain multiple TAP ports and multiple tool ports.
Assigning a Tool Port to a TAP Aggregation Group
Tool ports are assigned to a TAP aggregation group through the switchport tool group command. Each command either creates a list or alters the existing list of groups to which a tool port belongs.
- These commands assign port-channel interface
101 to TAP aggregation groups
analyze1,
analyze2, and
analyze3.
switch(config)# interface port-channel 101 switch(config-if-Po101)# switchport tool group set analyze1 analyze2 analyze3 switch(config-if-Po101)# show active interface Port-Channel101 switchport mode tool switchport tap identity 2101 switchport tool allowed vlan 1001-1020 switchport tap default group tag-9 switchport tool group set analyze3 analyze1 analyze2 switch(config-if-Po101)# - These commands remove
analyze-1 from
port channel 101’s TAP
aggregation group
list.
switch(config-if-Po101)# switchport tool group remove analyze1 switch(config-if-Po101)# show active interface Port-Channel101 switchport mode tool switchport tap identity 2101 switchport tool allowed vlan 1001-1020 switchport tap default group tag-9 switchport tool group set analyze3 analyze2 switch(config-if-Po101)#
Assigning TAP Ports to a TAP Aggregation Group
TAP ports are assigned to a TAP aggregation group using the switchport tap default group command.
Multiple ports can be added to a group simultaneously by entering the command in group interface configuration mode for all of the ports to be included.
Example
switch(config)# interface ethernet 41-42
switch(config-if-Et41-42)# switchport tap default group analyze2
switch(config-if-Et41-42)# interface ethernet 43
switch(config-if-Et43)# switchport tap default group analyze2
switch(config-if-Et43)# show interface ethernet 41-43 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et41 tap tap 400 1 0 analyze2
Et42 tap tap 1 1042 0 analyze2
Et43 tap tap 1 1 0 analyze3
switch(config-if-Et43)#Default TAP Aggregation Groups
A TAP port has multiple default groups. When traffic entering a TAP port does not match any filtering or traffic-steering rules for TAP aggregation groups configured on that port, it is sent to all default groups.
Example
switch(config)# interface ethernet 43
switch(config-if-Et43)# switchport tap default group analyze2 group analyze3
switch(config-if-Et43)#Viewing TAP Aggregation Group Assignments
TAP aggregation group membership is displayed by show tap aggregation groups. Options allow the display of individual groups or of all configured groups. The command displays active tool and TAP ports by default, and provides an option to display configured ports that are not active.
Example
switch# show tap aggregation groups
Group Name Tool Members
---------------------------------------------------------
analyze2 Po101, Po102
analyze3 Po101, Po103
Group Name Tap Members
---------------------------------------------------------
analyze2 Et41, Et42
analyze3 Et43
switch#LAGs in Tool Groups
Link Aggregation Groups (LAGs) can be included in tool groups for load balancing. A tool group can contain both LAGs and regular ports. Each member of a tool group receives one copy of the traffic destined to the group. Traffic is replicated to tool group members using multicast replication. The traffic replicated to LAGs is then load balanced to their members as per load-balance policies configured on the system.
If a tool group has no more than 60 members with at least one hardware LAG, then the replication mode of the tool group is set to ingress-only. Otherwise, the replication mode of the tool group is set to the configured system default multicast replication mode. See platform sand multicast replication default for more information on configuration of the system default replication mode.
Example
switch(config)# platform sand multicast replication default ingress
switch(config)#TAP Aggregation Traffic Steering
Traffic steering is a TAP aggregation process that uses class maps and policy maps to direct data streams at tool ports that are not otherwise associated to the ingress TAP port. A policy map is a data structure that filters data streams upon which identity VLAN tagging or TAP aggregation group assignment is implemented.
TAP-aggregation class maps and policy maps are similar to QoS and control-plane maps. However, policy maps and their components are not interchangeable among function types.
TAP Aggregation Policies
- A class map uses ACLs that identify packets that comprise a specified data stream.
- Packet content descriptors specify packet field values that are compared to inbound packets.
- A traffic resolution command or parameter specifies data handling methods for filtered traffic.
Each data packet entering an entity to which a policy map is assigned is managed as defined by the traffic resolution command of the highest priority class or rule that matches the packet.
- specify a TAP aggregation group to direct the packet.
- specify a VLAN number for identity tagging the packet.
TAP aggregation policy maps do not define an implicit deny statement. Packets that do not match a policy map class or rule are replicated and sent out tool ports specified by the default aggregation group assigned to the ingress TAP port. If no default group is selected, these packets are dropped.
Configuring TAP Aggregation Traffic Policies
TAP aggregation traffic policies are implemented by creating class maps and policy maps, then applying the policy maps to Ethernet and port-channel interfaces.
Creating Class Maps
A class map is an ordered list of IPv4 Access Control Lists (ACLs). Each ACL is assigned a sequence number that specifies its priority in the class map. TAP aggregation class maps utilize ACL permit rules to pass packets and deny rules to drop packets.
Class maps are created and modified in class-map configuration mode, which is entered using the class-map type tapagg. The match (class-map (tapagg)) command inserts a specified ACL into the class map, assigning it a sequence number that denotes its placement.
Class-map configuration mode is a group-change mode. Changes made in a group-change mode are saved by exiting the mode. The show active command displays the saved version of class map. The exit command returns the switch to global configuration mode and saves pending class-map changes. The abort command returns the switch to global configuration mode and discards pending changes.
- This command creates a TAP aggregation class map named
t-class_1 and places the switch in the
class-map configuration
mode.
switch(config)# class-map type tapagg match-any t-class_1 switch(config-cmap-t-class_1)# - These commands add two IPv4 ACLs (tacl-1 and
tacl-2) to the
t-class_1 class map. The commands use the
default method of assigning sequence numbers to the
ACLs.
switch(config-cmap-t-class_1)# match ip access-group tacl-1 switch(config-cmap-t-class_1)#match ip access-group tacl-2 switch(config-cmap-t-class_1)# - These commands exit class-map configuration mode, store pending changes to
running-config, then display the class
map.
switch(config-cmap-t-class_1)# exit switch(config)# class-map type tapagg match-any t-class_1 switch(config-cmap-t-class_1)# show active class-map type tapagg match-any t-class_1 10 match ip access-group tacl-1 20 match ip access-group tacl-2 switch(config-cmap-t-class_1)#
Creating Policy Maps
Policy maps are created and modified in policy-map configuration mode. A policy map is an ordered list of classes and match rules. Policy maps are edited by adding or removing map elements. Data packets are managed by commands of the highest priority class or rule that matches the packet.
Classes
- The class map identifies a data stream by using an ordered list of ACLs. Class maps are configured in class-map (tapagg) configuration mode.
- The set command specifies the replication method for filtered data packets, either through an associated aggregation group or identity VLAN tagging.
- The sequence number specifies the class’s priority within the policy map. Lower sequence numbers denote higher priority.
Matching Rules
- The filter list identifies a data stream by using a set of packet field values.
- The action, (SET_VALUE parameter) specifies the replication method of filtered data packets, either through an associated aggregation group or identity VLAN tagging.
- The sequence number specifies the rule’s priority within the policy map. Lower sequence numbers denote higher priority.
Policy-map and policy-map-class configuration modes are group-change modes. Changes are saved with the exit command or discarded with the abort command. The show active and show pending commands display the saved and modified policy map versions respectively.
The class (policy-map (tapagg)) command enters policy-map configuration mode.
Example
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)#- specifies an aggregation group.
- specifies a VLAN identity tag for replicated packets.
- specifies an aggregation group and a VLAN identity tag.
Examples
- These commands add the t-class_1 class map to the
t-policy_1 policy map, associate a set
statement with the class, then save the policy map by exiting the modes. Packets
filtered by the class map are identity tagged with VLAN
444 and replicated as specified by the
t-grp aggregation
group.
switch(config-pmap-t-policy_1)# class t-class_1 switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-grp id-tag 444 switch(config-pmap-c-t-policy_1-t-class_1)# exit switch(config-pmap-t-policy_1)# exit switch(config)# policy-map type tapagg t-policy_1 switch(config-pmap-t-policy_1)# show active policy-map type tapagg t-policy_1 10 class t-class_1 set aggregation-group t-group id-tag 444 switch(config-pmap-t-policy_1)#The match (policy-map (tapagg)) command adds a match rule to the configuration-mode TAP aggregation policy map.
- This command enters policy-map configuration mode for
t-policy_1, then creates a match rule for the
policy map that filters OSPF packets and replicates them as specified by
t-grp TAP aggregation
group.
switch(config-pmap-t-policy_1)# match ip ospf any any set aggregation-group t-grp switch(config-pmap-t-policy_1)#
Applying Policy Maps to an Interface
The service-policy type tapagg (Interface mode) command applies a specified policy map to the configuration-mode interface.
Example
switch(config)# interface ethernet 17
switch(config-if-Et17)# service-policy type tapagg input tpolicy_1
switch(config-if-Et17)#Stripping VLAN Tags
The traffic-steering policies in tap aggregation mode allows steering traffic from tap ports to tool ports using set (policy-map-class (tapagg)) command, while the ‘set id-tag’ tags the traffic with the specified VLAN ID in the dot1q format. The class (policy-map (tapagg)) command allows removing VLAN tags from the steered traffic. It supports all traffic types that the traffic steering policies support such as IPv4, IPv6, and MAC.
A tap port is an interface that receives a data stream where two network ports exchange.
A tool port is an interface that replicates data streams received by one or more tap ports. Tool ports connect to the devices that process monitored data streams.
Example
These commands place the switch in policy-map-class to add the t-class_1 class map to the t-policy_1 policy map. The first, second, or both of the two outer-most VLAN tags are stripped.
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# class t-class_1
switch(config-pmap-t-policy_1t-class_1)# set aggregation-group t-group remove dot1q outer 1-2
switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group id-tag 10
switch(config-pmap-c-t-policy_1-t-class_1)# set id-tag 10 remove dot1q outer 1
switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group
switch(config-pmap-c-t-policy_1-t-class_1)# set id-tag 10
switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group id-tag 10 remove dot1q outer 1-2Traffic Steering to Match Inner Header Fields
This feature allows matching the inner header fields (either IPv4 or IPv6 inner fields) of encapsulated traffic.
The following convention is adopted when describing an encapsulated traffic: <inner-protocol>-over-<outer-protocol>. For example, the IPv4-over-IPv6 packet indicates that the inner fields belong to IPv4 protocol and the outer fields belong to IPv6 protocol.
Supported Packet Types and Inner Header Fields
- IP-over-IP traffic
- IP-over-GRE traffic, with the following packet format
supported:
- [ Eth | IPv4 or IPv6 | GRE | Inner IPv4 or IPv6 ]
- [ Eth | IPv4 | GRE | Inner Eth | Inner IPv4 ], which will be referred to as L2-GRE packet.
- IP-over-GTP traffic (only in DCS-7280R3 and DCS-7500R3
series), with the following packet format
supported
- [ Eth | IPv4 | GTP | Inner IPv4 or IPv6 ]
- [ Eth | IPv6 | GTP | Inner IPv4 or IPv6 ]
The following inner header fields are supported:
- inner source IP address.
- inner destination IP address.
- inner TCP/UDP protocol.
- inner source port number.
- inner destination port number.
Configuring Traffic Steering to Match Inner Header Fields
To enable traffic steering with an ACL rule that matches the inner IP addresses, a user-defined TCAM profile must be configured for each type of IP protocol to which the inner IP addresses belong. For example, to match the inner IPv4 addresses of an IPv4 packet (i.e. IPv4-over-IPv4 traffic) or the inner IPv4 addresses of an IPv6 packet (i.e. IPv4-over-IPv6 traffic), one user-defined TCAM profile must be configured. A different user-defined TCAM profile is needed if matching the inner IPv6 addresses of an IPv4 packet or the inner IPv6 addresses of an IPv6 packet is desired.
The following commands show how to configure different TCAM profiles needed to enable support for matching inner IP headers, depending on the desired inner IP version, and inner IP header fields to be matched. These TCAM profiles are referred to as user-defined TCAM profiles and created based on the existing TCAM profile tap-aggregation-extended.
TCAM Profile to Match Inner IPv4 Header Fields
Match inner IPv4 addresses only.
The following commands configure the TCAM profile for matching only the inner source and destination IP addresses of IPv4 traffic based on the existing TCAM profile tap-aggregation-extended.
Example
switch(config)# hardware tcam
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip4 copy tap-aggregation-extended
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# no key field src-ip dst-ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# key field inner-src-ip-high inner-src-ip-low inner-dst-ip-high inner-dst-ip-low
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# no key field src-ipv6 src-ipv6-high dst-ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# key field inner-src-ip-high inner-src-ip-low inner-dst-ip-high inner-dst-ip-low
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# exitMatch inner IPv4 addresses, inner TCP/UDP protocol and inner port numbers for IP-over-IP and IP-over-GRE traffic.
In addition to matching inner IPv4 addresses, the previous user-defined TCAM profile can also be configured to match the inner TCP/UDP protocol and their corresponding port numbers. The commands to configure these inner fields are shown below.
Note that, due to hardware limitation, the feature “tapagg mac” is disabled in this TCAM profile to make room for matching additional inner header fields.
Example
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip4
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# no feature tapagg mac
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# no key field outer-vlan-id inner-vlan-id l4-src-port l4-dst-port udf-16b-1 udf-16b-2 udf-16b-3 udf-16b-4 udf-32b-1 udf-32b-2
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# key field inner-ip-protocol inner-l4-src-port inner-l4-dst-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# no key field l4-src-port l4-dst-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# key field inner-ip-protocol inner-l4-src-port inner-l4-dst-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ipv6)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# exitMatch inner IPv4 addresses, inner TCP/UDP protocol and inner port numbers for L2-GRE packets.
The same user-defined TCAM profile can be updated to support traffic steering that matches on inner header fields for L2-GRE packets, simply by adding a new packet type.
Example
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip4
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# packet ipv4 eth ipv4 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-port)# packet ipv4 eth ipv4 forwarding bridgedMatch inner IPv4 addresses, inner TCP/UDP protocol and inner port numbers for IP-over-GTP packets.
We can re-use the same user-defined TCAM profile and update it to support traffic steering that matches on inner header fields for IP-over-GTP packets, simply by adding a new packet type.
Example
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip4
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# no packet ipv4 eth ipv4 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-ip)# packet ipv4 gtpv1 ipv4 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-port)# no packet ipv4 eth ipv4 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-port)# packet ipv4 gtpv1 ipv4 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip4-feature-tapagg-port)# packet ipv6 gtpv1 ipv4 forwarding bridgedMatch inner and outer IPv4 addresses.
If matching a combination of inner and outer IP header fields is desired, the user-defined TCAM profile must be updated to include the desired fields. For example, instead of matching both inner source and inner destination IPv4 addresses as illustrated by this TCAM profile, if users would like to match outer source IPv4 address and inner destination IPv4 address only (and ignoring outer destination and inner source IPv4 addresses). The following commands show how to configure a TCAM profile for such filtering.
Example
switch(config)# hardware tcam
switch(config-hw-tcam)# profile tap-aggregation-user-outer-inner-ip4 copy tap-aggregation-extended
switch(config-hw-tcam-profile-tap-aggregation-user-outer-inner-ip4)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-outer-inner-ip4-feature-tapagg-ip)# no key field dst-ip
switch(config-hw-tcam-profile-tap-aggregation-user-outer-inner-ip4-feature-tapagg-ip)# key field inner-src-ip-high inner-src-ip-low
switch(config-hw-tcam-profile-tap-aggregation-user-outer-inner-ip4-feature-tapagg-ip)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-outer-inner-ip4)# exitTCAM Profile to Match Inner IPv6 Header Fields
Match inner IPv6 addresses only.
These commands are to configure a TCAM profile that can match inner IP addresses of IPv6 traffic are as follows:
Example
switch(config)# hardware tcam
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip6 copy tap-aggregation-extended
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# no key field dst-ip src-ip udf-16b-1 udf-16b-2 udf-16b-3 udf-16b-4 udf-32b-1 udf-32b-2 outer-vlan-id inner-vlan-id l4-src-port l4-dst-port l4-ops
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# key field inner-src-ipv6-high-high-32b inner-src-ipv6-high-low-32b inner-src-ipv6-low-high-32b inner-src-ipv6-low-low-32b
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# key field inner-dst-ipv6-high-high-32b inner-dst-ipv6-high-low-32b inner-dst-ipv6-low-high-32b inner-dst-ipv6-low-low-32b
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# no key field src-ipv6 src-ipv6-high dst-ipv6 l4-dst-port l4-src-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# key field inner-src-ipv6-high-high-32b inner-src-ipv6-high-low-32b inner-src-ipv6-low-high-32b inner-src-ipv6-low-low-32b
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# key field inner-dst-ipv6-high-high-32b inner-dst-ipv6-high-low-32b inner-dst-ipv6-low-high-32b inner-dst-ipv6-low-low-32b
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# exitMatch inner IPv6 addresses, inner TCP/UDP protocol and inner port numbers.
In addition to matching inner IPv6 addresses, the previous user-defined TCAM profile can also be configured to match the inner TCP/UDP protocol and their corresponding port numbers. The commands to configure these inner fields are shown below.
Note that, due to hardware limitation, the feature tapagg mac is disabled in this TCAM profile to make room for matching additional inner header fields.
Example
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# no feature tapagg mac
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# key field inner-ipv6-next-header inner-l4-src-port inner-l4-dst-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# key field inner-ipv6-next-header inner-l4-src-port inner-l4-dst-port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ipv6)# exit
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# exitMatch inner IPv6 addresses, inner TCP/UDP protocol and inner port numbers for IP-over-GTP packets.
We can re-use the same user-defined TCAM profile and update it to support traffic steering that matches on inner header fields for IP-over-GTP packets, simply by adding a new packet type.
switch(config-hw-tcam)# profile tap-aggregation-user-inner-ip6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg ip
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-ip)# packet ipv4 gtpv1 ipv6 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg port
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-port)# packet ipv4 gtpv1 ipv6 forwarding bridged
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6)# feature tapagg ipv6
switch(config-hw-tcam-profile-tap-aggregation-user-inner-ip6-feature-tapagg-port)# packet ipv6 gtpv1 ipv6 forwarding bridgedApply TCAM Profile
To apply the newly-defined TCAM profile use tap-aggregation-user-inner-ip4 or tap-aggregation-user-inner-ip6 command.
switch(config)# tap aggregation
switch(config-tap-agg)# mode exclusive profile tap-aggregation-user-inner-ip4For modular systems
switch(config)# tap aggregation
switch(config-tap-agg)# mode mixed module Linecard <linecard number> profile tap-aggregation-user-inner-ip4Set-Up ACL Rules for Matching Inner Header Fields
In order to apply traffic steering for particular packets based on their inner header fields, ACL rules that can filter such traffic must be created, as shown in the example.
- ACL rule for filtering an IPv4-over-IPv4 traffic based
on the inner
addresses.
switch(config)# ip access-list acl1 switch(config-acl-acl1)# permit ip any any inner ip host 1.2.3.4 host 5.6.7.8 - ACL rule for filtering an IPv4-over-IPv4 traffic based
on the outer source and inner destination
addresses.
switch(config)# ip access-list acl1 switch(config-acl-acl1)# permit ip host 1.2.3.4 any inner ip host any host 5.6.7.8 - ACL rule for filtering an IPv6-over-IPv4 traffic based
on the inner
addresses.
switch(config)# ip access-list acl2 switch(config-acl-acl2)# permit ip any any inner ipv6 host 1001::abcd host 2002::cafe - ACL rule for filtering an IPv4-over-IPv6 traffic based
on the inner addresses, inner TCP/UDP protocol,
and inner TCP/UDP
ports.
switch(config)# ipv6 access-list acl3 switch(config-ipv6-acl-acl3)# permit ipv6 any any inner ip tcp host 10.11.12.13 eq 9999 host 20.22.24.26 eq 8888 - ACL rule for filtering an IPv6-over-GRE(IPv4) traffic
based on the inner addresses, inner TCP/UDP
protocol, and inner TCP/UDP
ports.
switch(config)# ip access-list acl4 switch(config-acl-acl4)# permit gre any any inner ipv6 udp host 2019::baba eq 9999 host 1986::deca eq 8888 - ACL rule for filtering an IPv4-over-GTP traffic based on
the inner
addresses.
switch(config)# ip access-list acl5 switch(config-acl-acl5)# permit gtp any any version 1 protocol gtp-u inner ip host 1.2.3.4 host 5.6.7.8
Limitations
- Only IP (IPv4 and IPv6), GRE and GTP outer protocols are supported.
- Other outer protocols are not supported.
- Only IP (IPv4 and IPv6), TCP and UDP inner protocols are supported.
- Other inner protocols are not supported.
- To configure support for matching inner IPv4 addresses (for either IPv4 or IPv6 outer packets), a custom user-defined TCAM profile is required. A different user-defined TCAM profile is needed if matching inner IPv6 addresses is desired.
- The total size of fields to match must not exceed the TCAM key size limitation (which is 320 bit if tap-aggregation-extended system profile is used as the base profile, or 160 bit for tap-aggregation-default system profile). For example, it is not possible to create a user-defined TCAM profile that matches both outer and inner source/destination address pairs for an IPv6-over-IPv6 packet. This is because each IPv6 address is 128 bit, requiring at least 512 bit to match all 4 addresses, and the TCAM key size is limited to 320 bit.
TAP Aggregation GUI
The switch provides a Graphical User Interface (GUI) for creating and viewing a TAP aggregation configuration and displaying LANZ traffic statistics.
All commands available on the GUI are accessible through the CLI. The TAP aggregation configuration created through either the CLI or the GUI can be viewed and modified through either medium.
This section provides a brief description of the TAP aggregation GUI.
Accessing the TAP Aggregation GUI
The URL for the TAP aggregation GUI is: //hostname/apps/TapAgg/index.html where the hostname is the switch’s configured hostname. The TAP Aggregation GUI Initial Panel displays the initial TAP aggregation GUI panel for the switch with the hostname ro402.
-
The configuration section displays the TAP aggregation configuration, including the TAP interfaces, tool interfaces, and aggregation groups. Links are displayed to indicate interface group membership.
-
The component section displays information and control buttons for the active configuration entity. When an entity is not selected, the section displays information for the switch (device).
The configuration section displays TAP aggregation components only when the switch is in TAP aggregation mode. To enter TAP aggregation mode, click the TAP Aggregation icon in the component section for the device. The icon is a toggle mechanism; clicking it again disables TAP aggregation mode.
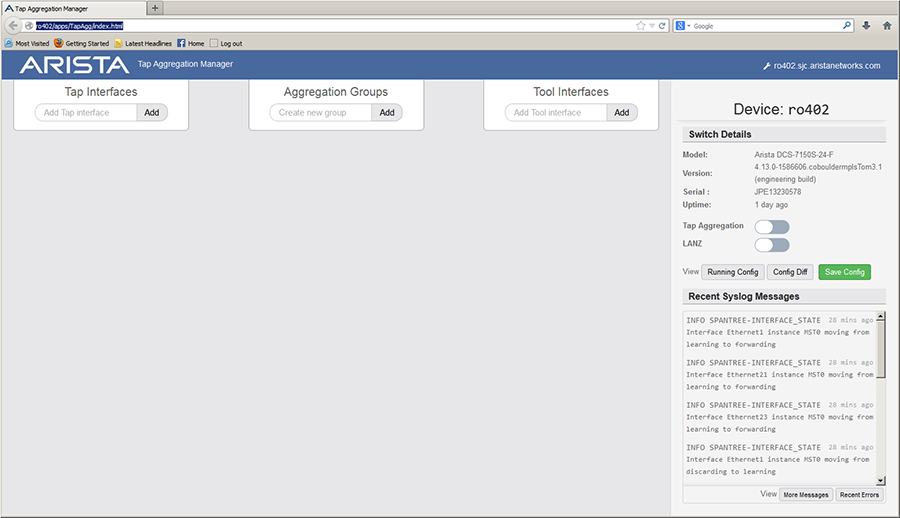
Viewing TAP Aggregation Component Details
TAP Aggregation GUI Panel with TAP Aggregation Mode Enabled displays the TAP aggregation panel when the switch is in TAP aggregation mode. The configuration section indicates that the TAP aggregation configuration consists of three tool interfaces, one TAP interface, and four aggregation groups. Ethernet port 10 is the active component; configuration control and traffic information for this interface is available in the component section.
The active component is changed by clicking on the desired component in the configuration section. To display device (switch) information, click on any configuration section outside of any component.
Modifying a TAP Aggregation Configuration
- adding a TAP or tool interface: begin typing the interface name in the desired add-interface data entry area to access a drop-down list of available interfaces. Select the desired interface and press the Add button.
- removing an interface from the configuration: select the desired interface in the configuration section and click the deconfigure button in that interface’s component section.
- adding an aggregation group: type the desired name of the new group in the data entry area and press the Add button. The TAP aggregation group name can consist of alphanumeric characters and specific special characters (- _ [ ] { } :) only.
- adding an interface to an aggregation group: select the desired interface in the configuration section, then press the icon of the group in the group membership area of the interface’s component section.
Group icons are toggle buttons; clicking the icon of a group to which the interface belongs removes that interface from the group.
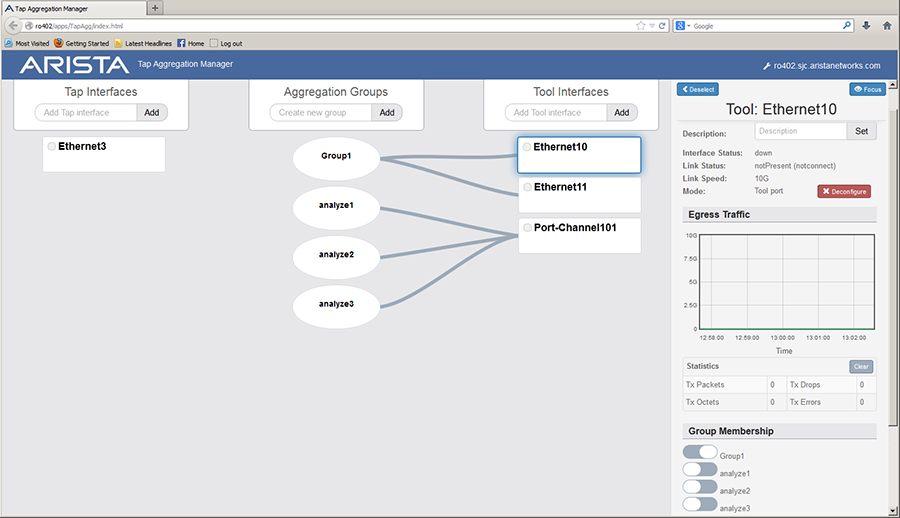
TAP Aggregation Keyframe and Timestamp Configuration
TAP Aggregation Keyframe Generation
Keyframes contain routable IP packets that provide information to relate timestamps with the complete ASIC counter and absolute UTC time. The switch supports a maximum of ten keyframes, which are distinguished by their name label. Each keyframe can egress from every Ethernet port.
- the platform fm6000 keyframe rate command configures the keyframe’s transmission rate.
- the platform fm6000 keyframe source command configures the
source IP address that is placed in each keyframe’s header. The management interface IP
address is the default source address.
The source MAC address is the MAC address of the egress interface transmitting the keyframe
- the platform fm6000 keyframe device command configures the 16-bit number that keyframes list as the device ID in their payload.
- the platform fm6000 keyframe fields skew command enables the inclusion of clock skew fields in the keyframe.
- the show platform fm6000 keyframe command displays keyframe configuration information.
- This command enables the generation of a keyframe named
key-1 and configures it to egress from interfaces ethernet
11 through 15 with a source IP
address of 10.21.1.4 and a MAC address of
10.4E21.9F11.
switch(config)# platform fm6000 keyframe key-1 interface ethernet 11-15 10.21.1.4 10.4E21.9F11 switch(config)# - This command configures the generation rate for the
keyframe of 10 frames per second on each of the five
interfaces that it is configured to
egress.
switch(config)# platform fm6000 keyframe key-1 rate 10 switch(config)# - This command enables the generation of a keyframe named
key-1 and configures 100 as the
value that is placed in the keyframe’s device ID
field.
switch(config)# platform fm6000 keyframe key-1 device 100 switch(config)# - This command enables the inclusion of clock skew fields
in the keyframe named
key-1.
switch(config)# platform fm6000 keyframe key-1 fields skew switch(config)# - This command displays configuration information for
keyframe
key-1.
switch(config)# show platform fm6000 keyframe Keyframe key-1 ------------------------ Egress Interface(s): Ethernet11, Ethernet12, Ethernet13, Ethernet14, Ethernet15 Source IP: 172.22.30.142 Destination IP: 10.21.1.4 Destination MAC: 00:10:4e:21:9f:11 Device ID: 100 Rate: 10 packet(s) per second switch(config)#
Enabling Timestamp Insertion on an Interface
EOS bases timestamps on a frame’s ingress time and applies them to frames sent on egress ports, ensuring that timestamps on monitored traffic reflect ingress timing of the original frames. Time-stamping is configured on the egress port where the timestamp is applied to the frame.
When timestamping is enabled on an egress interface, packets leave the interface with timestamps that were applied in hardware when the packet arrived at the switch. This is facilitated by applying a hardware timestamp to all frames arriving on all interfaces when timestamping is enabled on any interface, then removing timestamps on packets egressing interfaces where timestamping is not enabled.
- before-fcs: the switch discards the original FCS, appends the ingress timestamp at the end of the frame data, recalculates a new FCS based on the appended timestamp, then appends the new FCS to the end of the frame. This creates a valid Ethernet frame but does not update headers of any nested protocols.
- replace-fcs: the switch replaces the original FCS with the timestamp. This mode maintains the size of the original frame without any latency impact, but the FCS is not valid.
- These commands enable timestamping in before-fcs mode on
interface ethernet 44 on a 7150
platform.
switch(config)# interface ethernet 44 switch(config-if-Et44)# mac timestamp before-fcs switch(config-if-Et44)# show active interface Ethernet44 mac timestamp before-fcs switch(config-if-Et44)# - These commands disable timestamping on interface ethernet
44 on a 7150
platform..
switch(config-if-Et44)# no mac timestamp switch(config-if-Et44)# show active interface Ethernet44 switch(config-if-Et44)#
TapAgg GRE Tunnel Termination
The TapAgg GRE Tunnel Termination feature terminates the GRE packets on a TapAgg switch by stripping the GRE header and then letting the decapped packets go through the normal TapAgg path. With this feature, we can use an L3 GRE tunnel to transit tapped traffic to the TapAgg switch over an L3 network. That would widely extend the available use cases for TapAgg.
- Support IPv4 GRE tunnel interfaces only.
- Support the following GRE types: IPoGRE, L2GRE, GREenSPAN, ERSPAN Type I, ERSPAN Type II, and GREenTAP.
- Do packet forwarding/steering on the decapped packets. Not routing.
- Packets can be forwarded to a set of tool ports.
- Have a command to configure for not stripping the GRE header, so that the TapAgg side may use the information present in the GRE metadata.
Configuring TapAgg GRE Tunnel Termination
The TapAgg GRE Tunnel Termination is allowed to be configured in the following two modes:
- TapAgg Exclusive Mode
- TapAgg Mixed Mode
TapAgg Exclusive Mode
In Tapagg Exclusive mode, GRE tunnel termination is enabled on a selected tap ports through CLI. When traffic comes into those tap ports, the matched GRE packets is decapped and forwarded to the tap port's default forwarding destinations or the steering destinations if it matches the policy ACLs applied.
Adding the TCAM Feature
switch# configure
switch(config)# hardware tcam
switch(config-tcam)# profile tap-aggregation-gre copy tap-aggregation-profile
switch(config-tcam-profile-tap-aggregation-gre)# feature tapagg tunnel termination copy system-feature-source-profile
switch(config-tcam-feature-tapagg-tunnel-termination)# exit
switch(config-tcam-profile-tap-aggregation-gre)# exit
Saving new profile 'tap-aggregation-gre'
switch(config-tcam)# exit
switch(config)#switch(config)# show hardware tcam profile tap-aggregation-gre
Features enabled in TCAM profile tap-aggregation-gre:
mpls
acl port ipv6
tapagg port
tapagg mac
tapagg ip
tapagg ipv6
tapagg tunnel termination
acl port ip
tunnel VXLAN
acl port mac
forwarding-destination mplsChange Hardware Forwarding Profile
On DCS-7280R3, DCS-7500R3 and DCS-7800R3 systems, the hardware forwarding profile needs to be set to system-profile-tap-aggregation on all linecards.
Enable GRE Termination on a Tap Port
Use switchport tap encapsulation gre [tunnel destination <dst IP address> [source <src IP address> ]] strip to enable GRE termination on a tap port. The command allows specification of tunnel endpoints, to support termination on a specific tunnel.
switch(config-if-Et7/1)# switchport tap encapsulation gre destination <dst-ip> source <src-ip> stripWithout the specification of tunnel endpoints, it will terminate GRE packets for all tunnels. If only the destination endpoint is specified, then any GRE packet that matches this destination is terminated.
Example
switch(config-if-Et7/1)# switchport mode tap
switch(config-if-Et7/1)# switchport tap default group tool1
switch(config-if-Et7/1)# switchport tap encapsulation gre stripGRE Termination into Traffic Steering
If the matched GRE packet also hits the policy map that is applied on the tap port, after stripping the GRE header, the packets are forwarded to the steering destination configured for the policy map. In the example below, a policy map named ‘pm’ is applied on the tap port which has gre strip enabled on it. Then the GRE packets with an outer destination IP dst-ip and source IP src-ip, matching the permit rule in the policy map, is forwarded to the tool group tool2 aftering stripping the GRE header.
switch(config)# show policy-map type tapagg
Service policy pm
Configured on:
Applied on:
10: Class-map: cm (match-any)
Match: 10 IP Access List testAcl
10 permit ip host 1.1.1.1 host 2.2.2.2
Configured actions: set group tool2
switch(config-if-Et7/1)#show active
interface Ethernet7/1
service-policy type tapagg input pm
switchport mode tap
switchport tap encapsulation gre strip
switchport tap default group tool1GRE Termination with Ingress/Egress Truncation
When there is truncation enabled, either on the tap port that has GRE termination configured or on the tool port that is configured to egress out the decapped packets, the GRE header is stripped from the truncated packets. In other words, the GRE header stripping occurs after truncation. That means the size of the egress packet will be less than the original expectation. For example, if we have configured to truncate packets to a size of 178 bytes, after enabling GRE termination, the egress out packet for a GREenSpan will have a size of 136. It is 178 minus 42 (the total bytes stripped for GREenSpan).
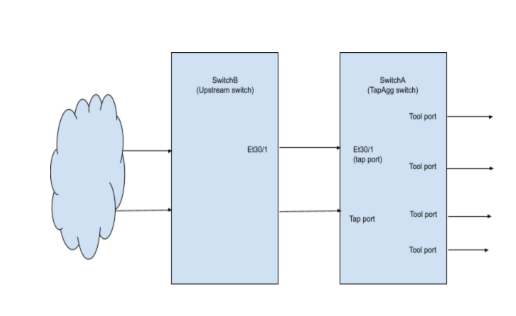
Configuring the Upstream Switch
In TapAgg exclusive mode, the routing protocols are not running so TapAgg Switch will rely on its upstream switch which has routing protocol enabled to forward the GRE packets to it. Tap ports which are selected to receive the GRE packets should be connected to the upstream switch. The upstream switch needs to configure a static route to forward the GRE packets to the link.
Example
switchB(config-if-Et30/1)# show active
interface Ethernet30/1
speed forced 100gfull
no switchport
ip address 10.10.10.1/24
SwitchB(config-if-Et30/1)# ip route 40.1.1.2/32 ethernet 30/1switchB# show ip route
VRF: default
Codes: C - connected, S - static, K - kernel,
O - OSPF, IA - OSPF inter area, E1 - OSPF external type 1,
E2 - OSPF external type 2, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type2, B - BGP, B I - iBGP, B E - eBGP,
R - RIP, I L1 - IS-IS level 1, I L2 - IS-IS level 2,
O3 - OSPFv3, A B - BGP Aggregate, A O - OSPF Summary,
NG - Nexthop Group Static Route, V - VXLAN Control Service,
DH - DHCP client installed default route, M - Martian,
DP - Dynamic Policy Route, L - VRF Leaked,
RC - Route Cache Route
Gateway of last resort is not set
C 10.10.10.0/24 is directly connected, Ethernet30/1
S 10.80.0.0/13 [1/0] via 10.240.25.1, Management1
S 10.95.0.0/16 [1/0] via 10.240.25.1, Management1
C 10.240.25.0/25 is directly connected, Management1
S 10.240.0.0/15 [1/0] via 10.240.25.1, Management1
S 10.242.0.0/15 [1/0] via 10.240.25.1, Management1
S 40.1.1.2/32 is directly connected, Ethernet30/1
S 172.16.0.0/12 [1/0] via 10.240.25.1, Management1switchB(config)# arp 40.1.1.2 44:4c:a8:be:35:e9 arpaswitchB# show arp
Address HWtype HWaddress Flags Mask Iface
10.240.25.1 ether 28:99:3a:67:7f:93 C ma1
40.1.1.2 ether 44:4c:a8:be:35:e9 CM et30_1With the above configurations, the upstream Switch B can forward the GRE packets to TapAgg Switch A.
TapAgg Mixed Mode
For a modular system, such as the DCS-7500R or DCS-7500R2, routed ports on a non-TapAgg linecard is used to receive GRE packets. In order to use the tap tunnel termination feature, dbTapTunnelTermination must be added to the TCAM profile for the non-TapAgg linecards.
Adding the TCAM Feature
switch(config)# hardware tcam
switch(config-tcam)# profile default-with-tap-gre copy default
switch(config-tcam-profile-default-with-tap-gre)# feature tapagg tunnel termination copy system-feature-source-profile
switch(config-tcam-feature-tapagg-tunnel-termination)# exit
switch(config-tcam-profile-default-with-tap-gre)# exit
Saving new profile 'default-with-tap-gre'
switch(config-tcam)# exitswitch(config)# hardware tcam
switch(config-tcam)# system profile default-with-tap-greswitch(config)# tap agg
switch(config-tap-agg)# mode mixed module linecard 3,4,5
! Changing modes may affect available functionality. Unsupported configuration elements will be ignored.
switch(config)#show hardware tcam profile
Configuration Status
Linecard3 tap-aggregation-default* tap-aggregation-default
Linecard4 tap-aggregation-default* tap-aggregation-default
Linecard5 tap-aggregation-default* tap-aggregation-default
Linecard6 default-with-tap-gre default-with-tap-gre
* configuration overridden by TapAggThere could be some cases where we need to remove some features from the TCAM profile in order to have room to fit the feature tapagg tunnel termination in. This kind of ‘tradeoff’ is needed when we want this feature to be with a specific user-defined tcam profile.
switch(config)# tap agg
switch(config-tap-agg)# mode mixed module linecard 3,4,5
! Changing modes may affect available functionality. Unsupported configuration elements will be ignored.
switch(config)# show hardware tcam profile
Configuration Status
Linecard3 tap-aggregation-default* tap-aggregation-default
Linecard4 tap-aggregation-default* tap-aggregation-default
Linecard5 tap-aggregation-default* tap-aggregation-default
Linecard6 default-with-tap-gre ERROR
* configuration overridden by TapAgg
switch(config)# hardware tcam
switch(config-tcam)# profile default-with-tap-gre
switch(config-tcam-profile-default-with-tap-gre)# no feature mirror ip
switch(config-tcam-profile-default-with-tap-gre)# no feature pbr ip
switch(config-tcam-profile-default-with-tap-gre)# exit
switch(config-tcam)# show hardware tcam profile
Configuration Status
Linecard3 tap-aggregation-default* tap-aggregation-default
Linecard4 tap-aggregation-default* tap-aggregation-default
Linecard5 tap-aggregation-default* tap-aggregation-default
Linecard6 default-with-tap-gre default-with-tap-gre
* configuration overridden by TapAggChange Hardware Forwarding Profile
On DCS-7280R3, DCS-7500R3 and DCS-7800R3 systems, the hardware forwarding profile needs to be set to system-profile-tap-aggregation on all tap agg linecards. Detailed instructions on how to set it can be found in the Resources section.
Configure GRE Tunnel Interface
Configure the GRE tunnel interface that we want the packets it received to be terminated and redirected.
switch(config)# interface tunnel 1
switch(config-if-Tu1)# tunnel mode gre
switch(config-if-Tu1)# tunnel source 40.1.1.1
switch(config-if-Tu1)# tunnel destination 40.1.1.2switch(config-if-Tu1)# show active
tunnel mode gre
tunnel source 40.1.1.1
tap default group gr1
tap default interface Ethernet3/1switch(config-if-Tu1)# show active
tunnel mode gre
tap default group gr1
tap default interface Ethernet3/1switch(config)# interface tunnel 1
switch(config-if-Tu1)# tap default group gr1
switch(config-if-Tu1)# tap default interface ethernet 3/1
switch(config-if-Tu1)#switch(config)# interface tunnel 1
switch(config-if-Tu1)# tap encapsulation gre preserve
switch(config-if-Tu1)#switch(config)# show interfaces tunnel 1
Tunnel1 is up, line protocol is up (connected)
Hardware is Tunnel, address is 2801.0102.0800
Tunnel source 40.1.1.2, destination 40.1.1.1
Tunnel protocol/transport GRE/IP
Hardware forwarding enabled
Tunnel transport MTU 1476 bytes (default)
Up 35 minutes, 57 secondsEnable Tap Tunnel Termination on TapAgg Linecards in Mixed Mode
If you do want to enable GRE Termination on a specific tap port in TapAgg mixed mode,follow the TapAgg exclusive mode section and refer to configuring TCAM profile and GRE termination for the TapAgg linecard.
Tap Aggregation Hardware Forwarding Profile
Configuring Tap Aggregation Hardware Forwarding Profile
- The default hardware forwarding profile can be set globally with the
hardware forwarding system profile
command:
switch(config)# hardware forwarding system profile system-profile-tap-aggregation - When not in Tap Aggregation mode the default hardware forwarding profile should be
returned to the default system profile with the same
command:
switch(config)# hardware forwarding system profile system-profile-default - For a modular system the system default profile can also be overridden on a per line
card basis with the
command:
switch(config)# hardware forwarding module Linecard3 profile system-profile-tap-aggregationNote: If this command is used to set the hardware forwarding profile of a specific line card then changing the system default profile with the hardware forwarding system profile command will not affect that line card until the line card specific configuration is removed.
Show Commands
(config)# show hardware forwarding profile
Linecard Configured Profile
----------------- ------------------------------
FixedSystem system-profile-tap-aggregation
System default profile: system-profile-tap-aggregation(config)# show hardware forwarding profile
Linecard Configured Profile
--------------- ------------------------------
Linecard3 system-profile-default
Linecard4 system-profile-tap-aggregation
Linecard5 system-profile-tap-aggregation
System default profile: system-profile-defaultLimitations
TAP Aggregation MPLS Pop
Configuring MPLS Pop
- On DCS-7280R/R2, DCS-7500R/R2, and DCS-7020R MPLS pop is configurable at the tap port
using the switchport
command:
switch(config-if-Et1)# [no] switchport tap mpls pop all - On DCS-7280R3, DCS-7500R3, and DCS7800R3 MPLS pop is configurable at the tool port
using the switchport command. As the commands suggest, all MPLS labels will be
popped.
switch(config-if-Et1)# [no] switchport tool mpls pop all - On DCS-7280R3, DCS-7500R3, and DCS7800R3 the hardware forwarding profile must also be
set before MPLS pop can be used. This is done globally by the
command:
switch(config)# hardware forwarding system profile system-profile-tap-aggregation - The system profile can also be overridden on a per line card basis with the
command:
switch(config)# hardware forwarding module Linecard3 profile system-profile-tap-aggregation
Limitations
R/R2 series MPLS pop has the following limitations:
- New L2 Header on Egress
- Always inserts a tap port Identity VLAN ID, even if not configured. Default Identity VID is 1.
- Destination / source MAC addresses are not configurable.
- Tool Port / Egress VLAN Filtering
- Because the incoming L2 header is discarded, the tool port does not have access to the original VLAN ID.
- Tap ports can still filter on VLAN ID.
- ACL-Based Tap Aggregation
- Matching IP headers contained inside an MPLS header is only supported since EOS-4.20.5F.
On both R/R2 series and R3 series some Tap Aggregation features do not work when forwarding MPLS-encapsulated traffic:
- Non-IP over MPLS
-
If the incoming L3 header is not recognized as IPv4 or IPv6 the MPLS pop feature is bypassed and the packet is not stripped.
-
TAP Aggregation 802.1br EVN Tag Stripping
Configuring 802.1br-E/VN Tag Stripping
By default, Arista switches do not strip BR-E/VN tags from ingress packets.
- To enable BR E-Tag stripping add the following
configuration:
switch(config)# tap aggregation switch(config-tap-agg)# [no] encapsulation dot1br strip - To enable VN-TAG stripping add the following
configuration:
switch(config)# tap aggregation switch(config-tap-agg)# [no] encapsulation vn-tag strip
On DCS-7280R3, DCS-7500R3and DCS7800R3, BR-E/VN tag stripping is configured at the tool port level. When enabled on a tool port, only packets egressing this tool port will have their BR-E/VN tags stripped. The BR-E/VN tag stripping allows a choice of stripping both or either of the tags.
- To activate BR E-Tag stripping on a tool port, add the following
configuration:
switch(config-if-Et1)# [no] switchport tool encapsulation dot1br strip - To activate VN-TAG stripping on a tool port, add the following
configuration:
switch(config-if-Et1)# [no] switchport tool encapsulation vn-tag strip
switch(config)# hardware forwarding system profile system-profile-tap-aggregationswitch(config)# hardware forwarding module Linecard3 profile system-profile-tap-aggregationShow Commands
- On DCS-7280R/R2, DCS-7500R/R2, and
DCS-7020R:
switch(config)# show interfaces tap tunnel Port Configured Status Port Allowed Vlans Native Truncation Mode Identity Vlan Size ---------- ------------------ ------------ --------------- ------------------- ------------- ----------- Et1/1 tap tap 0 All 1 0 Port VN Tag Action BR Tag Action VXLAN Action MPLS Action ----------- ------------------- ------------------- ------------------ ----------- Et1/1 strip none none none - On DCS-7280R3, DCS-7500R3, and
DCS7800R3:
switch(config)# show interface tool tunnel Port Configured Status Id Tag Allowed Vlans Timestamp Mode Mode ------------ ------------------ ------------ ------------ ------------------- ----------- Et1/1 tool tool Off 100 None Port VN Tag Action BR Tag Action MPLS Action ------------ ------------------- ------------------- ----------- Et1/1 strip none none
Feature Interactions
On DCS-7280R/R2, DCS-7500R/R2, and DCS-7020R the following Tap aggregation features are supported with BR-E/VN tagged packets when tag stripping is enabled. Some or all of these features may not work for BR-E/VN tagged packets when tag stripping is not configured.
- MAC, IPv4, IPv6 Traffic Steering
- Tap identity tagging
- MPLS Termination
- Ingress VLAN Membership Filtering
- Egress VLAN Membership Filtering
On DCS-7280R3, DCS-7500R3, and DCS7800R3 the following Tap aggregation features are supported with BR-E/VN tagged packets when tag stripping is enabled.
- MAC, IPv4, IPv6 Traffic Steering
- Tap identity tagging
Limitations
The following lists feature limitations on DCS-7280R/R2, DCS-7500R/R2, and DCS-7020R when BR-E/VN tag stripping is enabled with tagged packets:
- IPv4/IPv6 traffic steering on VLAN IDs is not supported.
- IPv6 traffic steering is not supported on packets with two or more accompanying 802.1Q tags.
- Ingress VLAN membership filtering is scale limited. Only 4096 entries, used for whitelisting or allowing specific port-VLAN pairs, are supported. The default case of allowing all VLANs does not consume any of these entries. For example, a tap interface configured to allow 4093 VLANs will consume all but three entries.
- Ingress VLAN membership filtering on Tap interface LAGs for BR-E/VN tagged packets is not supported. To use Ingress VLAN membership for BR-E/VN tagged packets on a LAG Tap interface the Ingress VLAN membership configuration must be configured on each physical interface of the LAG.
- Time stamping and BR-E/VN tag stripping cannot be configured on the same tool interfaces. Time stamping, if configured, will take precedence over BR-E/VN tag stripping.
- 802.1Q Tag Stripping does not support BR-E/VN tagged packets.
The following lists feature limitations on DCS-7280R3, DCS-7500R3, and DCS7800R3 when BR-E/VN tag stripping is enabled with tagged packets:
- IPv4/IPv6/MAC traffic steering on VLAN IDs is not supported.
- MPLS pop and BR-E/VN tag stripping can not be used simultaneously on a tool port. If MPLS pop and BR-E/VN tag stripping are both configured on the same tool port, MPLS pop will take precedence and BR-E/VN tags will not be stripped.
- Ingress and Egress VLAN Membership filtering of BR-E/VN tagged packets is not supported in EOS-4.25.2F.
- 802.1Q Tag Stripping does not support BR-E/VN tagged packets.
TAP Aggregation Commands
Global Configuration Commands
- hardware forwarding system-profile-tap-aggregation
- platform fm6000 keyframe
- platform fm6000 keyframe device
- platform fm6000 keyframe fields skew
- platform fm6000 keyframe rate
- platform fm6000 keyframe source
- platform sand multicast replication default
- platform sand multicast replication ingress maximum
- tap aggregation
Interface Configuration Commands
- mac timestamp
- switchport mpls pop all
- switchport tap allowed vlan
- switchport tap default group
- switchport tap identity
- switchport tap native vlan
- switchport tap truncation
- switchport tool allowed vlan
- switchport tool encapsulation
- switchport tool group
- switchport tool identity
- switchport tool truncation
Tap Aggregation Configuration Mode
Tap Aggregation Traffic Steering
Display Commands EXEC Mode
class (policy-map (tapagg))
The class (policy-map (tapagg)) command places the switch in the policy-map-class (TAPagg) configuration mode, which is a group-change mode that defines a TAP aggregation class by associating the class’s eponymous class-map to a set statement. Upon exiting the policy-map-class mode, the class is placed in the policy-map as specified by an assigned sequence number.
- The class map identifies a data stream by using an ordered list of ACLs. Class maps are configured in class-map (tapagg) configuration mode. Data packets are managed by commands of the highest priority class or rule that matches the packet.
- set commands specify the replication method of filtered data packets, either through an associated aggregation group or identity VLAN tagging.
- Sequence numbers specify the class’s priority within the policy map. Lower sequence numbers denote higher priority.
The exit command returns the switch to policy-map configuration mode. However, saving policymap-class changes also requires an exit from policy-map mode. This saves all pending policy map and policy-map-class changes to running-config and returns the switch to global configuration mode. The abort command discards pending changes and returns the switch to global configuration mode.
The no class and default class commands remove the class assignment from the configuration mode policy map by deleting the corresponding class configuration from running-config.
Command Mode
Policy-Map (tapagg) Configuration accessed through class (policy-map (tapagg))
Command Syntax
[SEQ_NUM] class class_name
default [SEQ_NUM] class class_name
no [SEQ_NUM] class class_name
- SEQ_NUM priority of the class within the policy map. Lower numbers denote higher priority.
- no parameter number is derived by adding 10 to number of the map’s last class or rule.
- 1 to 4294967295 number assigned to class.
- class_name name of the class.
Guidelines
When a class is not associated with a set (policy-map-class (tapagg)) command, the filtered traffic is managed as specified by the TAP port’s default aggregation group.
- set (policy-map-class (tapagg)) assigns VLAN identity tag or tap aggregation group to class.
- exit returns the switch to parent policy map configuration mode.
- abort discards pending class map changes, then returns the switch to global configuration mode.
- class (policy-map (tapagg)) places the switch in the policy-map (tapagg) configuration mode.
- match (policy-map (tapagg)) assigns a match rule to a TAP aggregation policy map.
- These commands place the switch in policy-map-class and add the
t-class_1 class map to the
tpolicy_1 policy map. Packets filtered by the
class map are identity tagged with VLAN
444.
switch(config)# policy-map type tapagg t-policy_1 switch(config-pmap-t-policy_1)# class t-class_1 switch(config-pmap-c-t-policy_1-t-class_1)# set id-tag 444 switch(config-pmap-c-t-policy_1-t-class_1)# exit switch(config-pmap-t-policy_1)# exit switch(config)# policy-map type tapagg t-policy_1 switch(config-pmap-t-policy_1)# show active policy-map type tapagg t-policy_1 10 class t-class_1 set id-tag 444 switch(config-pmap-t-policy_1)# - These commands place the switch in policy-map-class to add the
t-class_1 class map to the
t-policy_1 policy map. The first, second, or
both of the two outer-most VLAN tags are
stripped.
switch(config)# policy-map type tapagg t-policy_1 switch(config-pmap-t-policy_1)# class t-class_1 switch(config-pmap-t-policy_1t-class_1)# set aggregation-group t-group remove dot1q outer 1-2 switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group id-tag 10 switch(config-pmap-c-t-policy_1-t-class_1)# set id-tag 10 remove dot1q outer 1 switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group switch(config-pmap-c-t-policy_1-t-class_1)# set id-tag 10 switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group id-tag 10 remove dot1q outer 1-2
class-map type tapagg
The class-map type tapagg command places the switch in class-map (tapagg) configuration mode, which is a group change mode that modifies a tapagg class map. A tapagg class map is a data structure that uses Access Control Lists (ACLs) to define a data stream by specifying characteristics of data packets that comprise the stream. Tapagg policy maps use class maps to specify traffic that is managed by policy map criteria.
The exit command saves pending class map changes to running-config, then returns the switch to the global configuration mode. Class map changes are also saved by entering a different configuration mode. The abort command discards pending changes and returns the switch to global configuration mode.
The no class-map type tapagg and default class-map type tapagg commands delete the specified class map by removing the corresponding class-map type qos command and its associated configuration.
Command Mode
Global Configuration
Command Syntax
class-map type tapagg match-any class_name
no class-map type tapagg match-any class_name
default class-map type tapagg match-any class_name
Parameter
class_name name of class map.
Related Commands
Example
switch(config)# class-map type tapagg match-any t-class_1
switch(config-cmap-t-class_1)#encapsulation
The encapsulation command is configured under Tap Aggregation mode to enable the 802.1br-E/VN Tag Stripping the packets ingressing any tap port on DCS-7280R/R2, DCS-7500R/R2, and DCS-7020R.
The no encapsulation or default encapsulation commands disable the 802.1br-E/VN Tag Stripping configuration from the running-config.
Command Mode
Tap Aggregation Configuration Mode
Command Syntax
encapsulation {dot1br | vn-tag} strip
no encapsulation {dot1br | vn-tag} strip
default encapsulation {dot1br | vn-tag} strip
- dot1br strips the 802.1br-E headers.
- vn-tag strips the VN Tag headers.
- To enable BR E-Tag stripping add the following
configuration:
switch(config)# tap aggregation switch(config-tap-agg)# encapsulation dot1br strip - To enable VN-TAG stripping add the following
configuration:
switch(config)# tap aggregation switch(config-tap-agg)# encapsulation vn-tag strip
hardware forwarding system-profile-tap-aggregation
The hardware forwarding system-profile-tap-aggregation command sets the global hardware forwarding system profile on a switch.
The hardware forwarding system-profile-default command returns the switch to the default system profile configurations when not in Tap Aggregation mode.
Command Mode
Global Configuration Mode
Command Syntax
hardware forwarding system profile [system-profile-default | system-profile-tap-aggregation | module]
default hardware forwarding system profile [system-profile-default | system-profile-tap-aggregation | module]
- system-profile-default normal forwarding profile.
- system-profile-tap-aggregation tap aggregation features profile.
- module used to set the tap aggregation features profile on a modular system.
- This command configures the tap aggregation features profile.
switch(config)# hardware forwarding system profile system-profile-tap-aggregation - This command returns the to the default system profile configurations when
not in Tap Aggregation
mode.
switch(config)# hardware forwarding system profile system-profile-default - This command overrides the system default profile on a per line card basis
for a modular
system.
switch(config)# hardware forwarding module Linecard3 profile system-profile-tap-aggregation
mac timestamp
The mac timestamp command enables timestamping on the configuration mode interface.
When timestamping is enabled on an egress interface, packets leave the interface with timestamps that were applied in hardware upon arriving at the switch. This is facilitated by applying a hardware timestamp to all frames arriving on all interfaces when timestamping is enabled on any interface, then removing timestamps on packets egressing interfaces where timestamping is not enabled.
The switch supports two timestamp modes, which differ in managing the egress frame’s 32-bit Frame Check Sequence (FCS):
- before-fcs: the switch discards the original FCS, appends the ingress timestamp at the end of the frame data, recalculates a new FCS based on the appended timestamp, then appends the new FCS to the end of the frame. This creates a valid Ethernet frame but does not update headers of any nested protocols.
- replace-fcs: the switch replaces the original FCS with the timestamp. This mode maintains the size of the original frame without any latency impact, but the FCS is not valid.
The no mac timestamp and default mac timestamp commands restore the default behavior of disabling timestamping on the configuration mode interface by removing the corresponding mac timestamp command from running-config.
Command Mode
Interface-Ethernet Configuration
Command Syntax
mac timestamp TS_PROPERTY
Parameters
- TS_PROPERTY specifies the timestamp
insertion mode. Options include:
- before-fcs the ingress timestamp is appended to the frame and the FCS is recalculated.
- replace-fcs the ingress timestamp replaces the original FCS.
Examples
- These commands enable timestamping in
before-fcs mode on interface
ethernet
44.
switch(config)# interface ethernet 44 switch(config-if-Et44)# mac timestamp before-fcs switch(config-if-Et44)# show active interface Ethernet44 mac timestamp before-fcs switch(config-if-Et44)# - These commands disable timestamping on interface
ethernet
44.
switch(config-if-Et44)# no mac timestamp switch(config-if-Et44)# show active interface Ethernet44 switch(config-if-Et44)#
match (class-map (tapagg))
The match command adds an ACL to the configuration-mode class map and associates a sequence number to the ACL. A class map is an ordered list of ACLs that define a data stream; the sequence number specifies an ACL’s priority within the list. A class map is used by policy maps to filter data packets. Tapagg class maps utilize ACL permit rules to pass packets and deny rules to drop packets.
Class map (tapagg) configuration mode is a group change mode. Match statements are not saved to running-config until the edit session is completed by exiting the mode.
The no match and default match commands remove the specified match statement from the configuration-mode class map by deleting the corresponding match command from running-config.
Command Mode
Class-map (tagagg) Configuration accessed through class-map type tapagg command.
Command Syntax
[SEQ_NUM] match ip access-group list_name
no SEQ_NUM] match ip access-group list_name
default SEQ_NUM] match ip access-group list_name
Parameters
- SEQ_NUM sequence number assigned to the
ACL. Options include:
- no parameter number is derived by adding 10 to the number of the map’s last ACL.
- 1 to 4294967295 number assigned to ACL.
- list_name name of ACL assigned to class map.
Guidelines
match statements accept IPv4 ACLs.
Related Commands
- class-map type tapagg places the switch in Class-Map configuration mode.
- exit saves pending class map changes, then returns the switch to global configuration mode.
- abort discards pending class map changes, then returns the switch to global configuration mode.
- class (policy-map (tapagg)) assigns a class map to a policy map.
Example
switch(config)# class-map type tapagg match-any t-class_1
switch(config-cmap-t-class_1)# match ip access-group tacl-1
switch(config-cmap-t-class_1)# match ip access-group tacl-2
switch(config-cmap-t-class_1)# exit
switch(config)# class-map type tapagg match-any t-class_1
switch(config-cmap-t-class_1)# show active
class-map type tapagg match-any t-class_1
10 match ip access-group tacl-1
20 match ip access-group tacl-2
switch(config-cmap-t-class_1)#match (policy-map (tapagg))
- The filter list identifies a data stream through a set of packet field values.
- The action, (SET_VALUE parameter) specifies the replication method of filtered data packets, either through an associated aggregation group or identity VLAN tagging.
- The sequence number specifies the rule’s priority within the policy map.
The no match and default match commands remove the match rule from the configuration-mode policy by deleting the corresponding statement from running-config.
Command Mode
Policy-Map (tapagg) Configuration accessed through class (policy-map (tapagg)).
Command Syntax
[SEQ_NUM] match [VLAN_TAG] SOURCE_ADDR [SOURCE_PORT] DEST_ADDR [DEST_PORT] [PROTOCOL] [FLAGS] [MESSAGE] [fragments] [tracked] [DSCP_FILTER] [TTL_FILTER] [log] SET_VALUE
no match [VLAN_TAG] SOURCE_ADDR [SOURCE_PORT] DEST_ADDR [DEST_PORT] [PROTOCOL][FLAGS][MESSAGE] [fragments][tracked] [DSCP_FILTER][TTL_FILTER] [log] SET_VALUE
default match [VLAN_TAG] SOURCE_ADDR [SOURCE_PORT] DEST_ADDR [DEST_PORT] [PROTOCOL][FLAGS] [MESSAGE][fragments] [tracked][DSCP_FILTER] [TTL_FILTER][log] SET_VALUE
Parameters
- SEQ_NUM priority of the rule within the
policy map. Lower numbers denote higher priority.
- no parameter number derived by adding 10 to number of the map’s last class or rule.
- 1 to 4294967295 number assigned to class.
- VLAN_TAG VLAN field filter. Options
include:
- no parameter packets are not filtered by VLAN field.
- vlan 1 to 4094 0 to 4095 VLAN ID and mask.
- vlan inner 1 to 4094 0 to 4095 VLAN ID and mask.
- vlan 1 to 4094 0 to 4095 inner 1 to 4094 0 to 4095 VLAN ID and mask.
- PROTOCOL protocol field filter. Values
include:
- no parameter packets are not filtered by host name.
- ahp authentication header protocol (51).
- icmp internet control message protocol (1).
- igmp internet group management protocol (2).
- ip internet protocol IPv4 (4).
- ospf open shortest path first (89).
- pim protocol independent multicast (103).
- tcp transmission control protocol (6).
- udp user datagram protocol (17).
- vrrp virtual router redundancy protocol (112).
- protocol_num integer corresponding to an IP protocol. Values range from 0 to 255.
- SOURCE_ADDR and
DEST_ADDR source and destination address
filters. Options include:
- network_addr subnet address (CIDR or address-mask).
- any packets from all addresses are filtered.
- host
ip_addr IP address (dotted decimal
notation).
Source and destination subnet addresses support discontiguous masks.
- SOURCE_PORT and
DEST_PORT
source and destination port filters. Options include:
- any all ports.
- eq port-1 port-2 ... port-n a list of ports. Maximum list size is 10 ports.
- neq port-1 port-2 ... port-n the set of all ports not listed. Maximum list size is 10 ports.
- gt port the set of ports with larger numbers than the listed port.
- lt port the set of ports with smaller numbers than the listed port.
- range port_1 port_2 the set of ports whose numbers are between the range.
- fragments filters packets with FO bit set (indicates a non-initial fragment packet).
- FLAGS flag bit filters (TCP packets). Use CLI syntax assistance (?) to display options.
- MESSAGE message type filters (ICMP packets). Use CLI syntax assistance (?) to display options.
- tracked rule filters packets in
existing ICMP, UDP, or TCP connections.
- Valid in ACLs applied to the control plane.
- Validity in ACLs applied to data plane varies by switch platform.
- DSCP_FILTER rule filters packet by its
DSCP value. Values include:
- no parameter rule does not use DSCP to filter packets.
- dscp dscp_value packets match if DSCP field in packet is equal to dscp_value.
- TTL_FILTER rule filters packet by its TTL
(time-to-live) value. Values include:
- no parameter rule does not use TTL field to filter packets.
- ttl eq ttl_value packets match if ttle in packet is equal to ttl_value.
- ttl gt ttl_value packets match if ttl in packet is greater than ttl_value.
- ttl lt ttl_value packets match if ttl in packet is less than ttl_value.
- ttl neq ttl_value packets match if ttl in packet is not equal to ttl_value.
- log triggers an informational log
message to the console about the matching packet.
- Valid in ACLs applied to the control plane.
- Validity in ACLs applied to data plane varies by switch platform.
- SET_VALUE specifies the replication
method for filtered packets.
- set aggregation group agg_group peplication specified by aggregation group.
- set id-tag 1 to 4094 packet is identity tagged with specified VLAN number.
- set aggregation group agg_group id-tag 1 to 4094 assigns agg group and identity tag.
- policy-map type tapagg places the switch in the policy-map (tapagg) configuration mode.
- class (policy-map (tapagg)) assigns a class to the configuration-mode policy map.
Example
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# match ip ospf any any set aggregation-group t-group
switch(config-pmap-t-policy_1)# exit
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
10 match ip ospf any any set aggregation-group t-group
switch(config-pmap-t-policy_1)#mode (tap-agg configuration mode)
The mode command configures the switch’s TAP aggregation mode. The mode exclusive command enables TAP aggregation. When TAP aggregation is enabled, TAP and tool ports are enabled, switching mode is disabled, and switching ports are errdisabled. TAP aggregation is disabled by default.
The no mode and default mode commands disable TAP aggregation mode and enable switching mode by removing the mode command from running-config.
Command Mode
TAP Aggregation Configuration
Command Syntax
mode exclusive
no mode exclusive
default mode exclusive
Parameter
exclusive TAP aggregation is enabled.
Related Command
tap aggregation places the switch in the TAP-aggregation configuration mode.
- These commands place the switch in tap aggregation
configuration mode, enable TAP aggregation mode, and display the
results.
switch(config)# tap aggregation switch(config-tap-agg)# mode exclusive switch(config-tap-agg)# show active tap aggregation mode exclusive switch(config-tap-agg)# - These commands disable tap aggregation mode by removing the
mode command from
running-config, then display the
results.
switch(config)# tap aggregation switch(config-tap-agg)# no mode switch(config-tap-agg)# show active switch(config-tap-agg)#
mode exclusive no-errdisable (tap-agg configuration mode)
The mode exclusive no-errdisable command configures the specified interface to remain enabled, regardless of its switchport mode, when TAP aggregation is enabled. This command is used primarily to configure a port to support PTP functions while the switch operates as a TAP aggregator.
Each command configures one Ethernet or port-channel interface. Subsequent mode exclusive no-errdisable commands add to the list of ports that remain enabled when TAP aggregation is enabled.
The no mode exclusive no-errdisable and default mode exclusive no-errdisable commands configure the specified interface to be error-disabled when programmed in access, trunk, or dot1q-tunnel switching mode (when TAP aggregation is enabled) by removing the corresponding mode exclusive no-errdisable command from running-config.
Command Mode
TAP Aggregation Configuration
Command Syntax
mode exclusive no-errdisable INT_NAME
Parameters
- ethernet e_num Ethernet interface specified by e_num.
- port-channel p_num port-channel interface specified by p_num.
- tap aggregation places the switch in TAP-aggregation configuration mode.
- mode (tap-agg configuration mode) configures the switch’s TAP-aggregation mode.
Guidelines
In order for a TAP-aggregation switch to receive PTP traffic, the upstream device to which it is connected should be set to statically send PTP multicast traffic to the connected port on the switch.
Since IGMP snooping is disabled on TAP-aggregation switches and with no configuration to support sending upstream join messages in such a state, the messages are transmitted statically from the upstream device. Once the upstream messages are received, the port will move to the slave state and follow the standard PTP mechanism.
Example
switch(config)# tap aggregation
switch(config-tap-agg)# mode exclusive
switch(config-tap-agg)# mode exclusive no-errdisable ethernet 21/4
switch(config-tap-agg)#platform fm6000 keyframe
The platform fm6000 keyframe command enables keyframe generation for data streams transmitted from specified ethernet interfaces. Keyframes are routable IP packets that the switch inserts into a data stream to provide contextual information that correlate timestamps inserted into data packets with absolute UTC time and the switch’s complete ASIC time counter.
The switch supports a maximum of ten keyframes. The keyframe name is the label that distinguishes different keyframes. Each keyframe can egress from every ethernet port. Command options specify the destination MAC address and IP address in the keyframe’s header. Other keyframe commands specify the transmission rate and the frame’s source.
The no platform fm6000 keyframe and default platform fm6000 keyframe commands disable generation of the specified keyframe by deleting the corresponding platform fm6000 keyframe command from running-config. These command also remove all supporting platform fm6000 keyframe commands for the specified keyframe.
Command Mode
Global Configuration
Command Syntax
platform fm6000 keyframe kf_name interface ethernet e_range ipv4_addr mac_addr
no platform fm6000 keyframe kf_name
default platform fm6000 keyframe kf_name
- kf_name the keyframe’s name.
- e_range Ethernet interface range over which the keyframe egresses. Valid formats include number, range, or comma-delimited list of numbers and ranges.
- ipv4_addr destination IPv4 address inserted into keyframes (dotted decimal notation).
- mac_addr destination MAC address inserted into keyframes (48-bit dotted hex notation).
Guidelines
Subsequent issuance of this command for a specified keyframe replaces the existing command in running-config. Ethernet interfaces are inserted into an existing keyframe only by issuing the complete command that identifies all interfaces through which the keyframe is transmitted.
Example
switch(config)# platform fm6000 keyframe key-1 interface ethernet 11-15 10.21.1.4 10.4E21.9F11
switch(config)#platform fm6000 keyframe device
The platform fm6000 keyframe device command configures the 16-bit number that the specified keyframe lists as the device ID in its payload. By default, the device value placed in the specified keyframes is 0.
The no platform fm6000 keyframe device and default platform fm6000 keyframe device commands restore the default device ID insertion value of 0 for the specified keyframe by removing the corresponding platform fm6000 keyframe device command from running-config. The no platform fm6000 keyframe and default platform fm6000 keyframe command also removes the corresponding platform fm6000 keyframe device command from running-config.
Command Mode
Global Configuration
Command Syntax
platform fm6000 keyframe kf_name device device_id
no platform fm6000 keyframe kf_name device
default platform fm6000 keyframe kf_name device
- kf_name keyframe name.
- device_id value inserted in keyframe’s device ID field. Values range from 0 to 65535. Default is 0.
Example
switch(config)# platform fm6000 keyframe key-1 interface ethernet 11-15 10.21.1.4 10.4E21.9F11
switch(config)# platform fm6000 keyframe key-1 device 100
switch(config)#platform fm6000 keyframe fields skew
Keyframes may optionally include skew numerator and skew denominator fields. These skew fields form a ratio indicating the ASIC clock skew. If the ratio is greater than 1, the clock is skewed fast; if the ratio is less than 1, the clock is skewed slow. Clock skew fields are omitted by default.
The platform fm6000 keyframe fields skew command enables the inclusion of clock skew fields in the keyframe.
The no platform fm6000 keyframe fields skew and default platform fm6000 keyframe fields skew commands remove the clock skew fields from the keyframe.
Command Mode
Global Configuration
Command Syntax
platform fm6000 keyframe kf_name fields skew
Parameter
kf_name keyframe name.
Example
switch(config)# platform fm6000 keyframe key-1 fields skew
switch(config)#platform fm6000 keyframe rate
The platform fm6000 keyframe rate command specifies the transmission rate for the specified keyframe from each interface from which it is configured to egress. By default, one keyframe is sent per second.
The no platform fm6000 keyframe rate and default platform fm6000 keyframe rate commands restore the default transmission rate for the specified keyframe of one per second by removing the corresponding platform fm6000 keyframe rate command from running-config. The no platform fm6000 keyframe and default platform fm6000 keyframe command also removes the corresponding platform fm6000 keyframe rate command from running-config.
Command Mode
Global Configuration
Command Syntax
platform fm6000 keyframe kf_name rate tx_rate
- kf_name the keyframe’s name.
- tx_rate keyframe transmission rate (frames per second). Values range from 1 to 100. Default value is 1.
Example
switch(config)# platform fm6000 keyframe key-1 interface ethernet 11-15 10.21.1.4 10.4E21.9F11
switch(config)# platform fm6000 keyframe key-1 rate 10
switch(config)#platform fm6000 keyframe source
The platform fm6000 keyframe source command configures the source IP address that the specified keyframe lists in its IP header. By default, keyframes use the IP address of the management interface as their source address.
The no platform fm6000 keyframe source and default platform fm6000 keyframe source commands restore the management interface IP address as the specified keyframe’s source IP address by removing the corresponding platform fm6000 keyframe source command from running-config. The no platform fm6000 keyframe and default platform fm6000 keyframe command also removes the corresponding platform fm6000 keyframe source command from running-config.
Command Mode
Global Configuration
Command Syntax
platform fm6000 keyframe kf_name source ip ipv4_addr
no platform fm6000 keyframekf_name source ip
default platform fm6000 keyframe kf_name source ip
Parameters
- kf_name keyframe’s name.
- ipv4_addr keyframe’s source IPv4 address (dotted decimal notation).
Example
switch(config)# platform fm6000 keyframe key-1 interface ethernet 11-15 10.21.1.4 10.4E21.9F11
switch(config)# platform fm6000 keyframe key-1 source 10.1.1.101
switch(config)#platform sand multicast replication default
- The default replication mode on switches with fabric is fabric-egress mode.
- The default replication mode on switches with single Fabric Access Processor (FAP) systems is ingress mode.
- The default replication mode on switches without fabric barring single FAP systems is ingress-egress mode.
- If a tool group with less than 60 LAGs has at least one hardware LAG, then the default replication mode of the tool group is ingress-only mode. Else the default replication mode of the tool group is the one configured across all LAGs in the tool group.
The default platform sand multicast replication default and no platform sand multicast replication default commands revert the current state to the factory default behavior.
Command Mode
Global Configuration
Command Syntax
platform sand multicast replication default {fabric-egress | ingress}
no platform sand multicast replication default
default platform sand multicast replication default
- fabric-egress configures the replication mode to use fabric-egress VoQ buffers.
- ingress configures the replication mode to use ingress VoQ buffers.
Guidelines
This command is supported on Sand platforms only.
Example
switch(config)# platform sand multicast replication default ingress
switch(config)#platform sand multicast replication ingress maximum
The platform sand multicast replication ingress maximum command configures maximum members for ingress-only replication.
The default platform sand multicast replication ingress maximum command reverts the maximum members for ingress-only replication to the default value.
The no platform sand multicast replication ingress maximum command deletes the maximum member value for ingress-only replication.
Command Mode
Global Configuration
Command Syntax
platform sand multicast replication ingress maximum max_value
no platform sand multicast replication ingress maximum
default platform sand multicast replication ingress maximum
Parameters
max_value specifies the maximum number of members for ingress-only replication. Values range from 1 to 64. The default value is 64.
Guidelines
This command is supported on Sand platforms only.
Example
switch(config)# platform sand multicast replication ingress maximum 63
switch(config)#policy-map type tapagg
The policy-map type tapagg command places the switch in policy-map (tapagg) configuration mode, which is a group-change mode that modifies a TAP-aggregation policy map. A TAP-aggregation policy map is a data structure that consists of class maps and match statements that filter a specific data stream. Packets in that data stream are either managed as specified by a TAP aggregation group or modified to add a VLAN identity tag. Policy maps manage traffic when applied to an Ethernet or port-channel interface.
The exit command saves pending policy map changes to running-config and returns the switch to global configuration mode. Policy map changes are also saved by entering a different configuration mode. The abort command discards pending changes, returning the switch to global configuration mode.
The no policy-map type tapagg and default policy-map type tapagg commands delete the specified policy map by removing the corresponding policy-map type tapagg command and the associated policy map statements from running-config.
Command Mode
Global Configuration
Command Syntax
policy-map type tapagg map_name
no policy-map type tapagg map_name
default policy-map type tapagg map_name
Parameter
map_name name of policy map.
Example
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)#resequence (class-map (tapagg))
The resequence command assigns sequence numbers to access control lists (ACLs) in the configuration mode TAP-aggregation class map. Sequence numbers denote an ACL’s priority within the class map. Command parameters specify the number of the first ACL and the numeric interval between consecutive ACLs.
Maximum rule sequence number is 4294967295.
Command Mode
Class-map (tagagg) Configuration
accessed with the class-map type tapagg command
Command Syntax
resequence [start_num [inc_num]]
- start_num sequence number assigned to the first rule. Default is 1.
- inc_num numeric interval between consecutive rules. Default is 1.
Example
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
10 match ip ospf any any set aggregation-group t-group
20 class fred
set aggregation-group t-group id-tag 444
30 class t-class_2
set id-tag 500
40 class t-class_3
set id-tag 600
50 class t-class_4
set id-tag 700
switch(config-pmap-t-policy_1)# resequence 100 20
switch(config-pmap-t-policy_1)# exit
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
100 match ip ospf any any set aggregation-group t-group
120 class fred
set aggregation-group t-group id-tag 444
140 class t-class_2
set id-tag 500
160 class t-class_3
set id-tag 600
180 class t-class_4
set id-tag 700
switch(config-pmap-t-policy_1)#resequence (policy-map (tapagg))
The resequence command assigns sequence numbers to classes and rules in the configuration mode TAP-aggregation policy map. Sequence numbers denote the priority of a class or rule within the policy map. Command parameters specify the number of the first policy map entity and the numeric interval between consecutive entities.
Maximum rule sequence number is 4294967295.
Command Mode
Policy-Map (tapagg) Configuration accessed with the class (policy-map (tapagg)) command
Command Syntax
resequence [start_num [inc_num]]
- start_num sequence number assigned to the first rule. Default is 1.
- inc_num numeric interval between consecutive rules. Default is 1.
Example
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
10 match ip ospf any any set aggregation-group t-group
20 class fred
set aggregation-group t-group id-tag 444
30 class t-class_2
set id-tag 500
40 class t-class_3
set id-tag 600
50 class t-class_4
set id-tag 700
switch(config-pmap-t-policy_1)# resequence 100 20
switch(config-pmap-t-policy_1)# exit
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
100 match ip ospf any any set aggregation-group t-group
120 class fred
set aggregation-group t-group id-tag 444
140 class t-class_2
set id-tag 500
160 class t-class_3
set id-tag 600
180 class t-class_4
set id-tag 700
switch(config-pmap-t-policy_1)#service-policy type tapagg (Interface mode)
The service-policy type tapagg command applies a specified TAP-aggregation policy map to the configuration-mode interface. A policy map is a data structure that identifies data traffic through class maps and match rules, then specifies the method of replicating the traffic. This command is active only when TAP aggregation mode is enabled on the switch.
The no service-policy type tapagg and default service-policy type tapagg commands remove the policy map assignment from the configuration mode interface by deleting the corresponding service-policy tapagg command from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port-Channel Configuration
Command Syntax
service-policy type tapagg input policymap_name
- input policy map applies to inbound packet streams. This is the only option.
- map_name name of policy map.
Guidelines
A policy map that is attached to a port-channel interface takes precedence for member interfaces of the port channel over their individual Ethernet interface configuration. Members that are removed from a port channel revert to the policy-map implementation specified by its Ethernet interface configuration.
Related Commands
class (policy-map (tapagg)) places the switch into the policy-map configuration mode to create a policy map.
Example
switch(config)# interface ethernet 17
switch(config-if-Et17)# service-policy type tapagg input t-policy_1
switch(config-if-Et17)#set (policy-map-class (tapagg))
- specifies an aggregation group.
- specifies a VLAN identity tag for replicated packets.
- specifies an aggregation group and a VLAN identity tag.
The no set and default set commands remove the specified set command data action from the configuration-mode class by deleting the associated set command from running-config.
Command Mode
Policy-map-class (tapagg) Configuration accessed using the class (policy-map (tapagg)) command
Command Syntax
set SET_VALUE
no set SET_VALUE
default set SET_VALUE
Parameters
- aggregation group agg_group replication specified by aggregation group.
- id-tag VLAN_number packet is identity tagged with specified VLAN number. VLAN numbers range from 1 to 4094.
- aggregation group agg_group id-tag VLAN_number assigns aggregation group and identity tag (VLAN number). VLAN numbers range from 1 to 4094.
- policy-map type tapagg places the switch in the policy-map (tapagg) configuration mode.
- class (policy-map (tapagg)) assigns a class to the policy-map configuration mode.
- match (policy-map (tapagg)) assigns a rule to the policy-map configuration mode.
Guidelines
When a class is not associated with a set command, the filtered traffic is managed as specified by the TAP port’s default aggregation group.
Example
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# class t-class_1
switch(config-pmap-c-t-policy_1-t-class_1)# set aggregation-group t-group id-tag 444
switch(config-pmap-c-t-policy_1-t-class_1)# exit
switch(config-pmap-t-policy_1)# exit
switch(config)# policy-map type tapagg t-policy_1
switch(config-pmap-t-policy_1)# show active
policy-map type tapagg t-policy_1
10 class t-class_1
set aggregation-group t-group id-tag 444
switch(config-pmap-t-policy_1)#show hardware tcam profile
Use the show hardware tcam profile command to display The TCAM prifile by configuration and status.
Command Mode
EXEC
Command Syntax
show hardware tcam profile detail
Parameter
detail Displays TCAM profile details.
(config-tap-agg)# show hardware tcam profile
Configuration Status
FixedSystem foo* foo
* configuration overridden by TapAggshow interfaces tap
The show interfaces tap command displays TAP-port configuration information for the specified interfaces.
Command Mode
EXEC
Command Syntax
show interfaces [INTERFACE] tap [INFO_LEVEL]
- INTERFACE interface type and numbers. Options
include:
- no parameter all interfaces.
- ethernet e_range Ethernet interface range specified by e_range.
- management m_range management interface range specified by m_range.
- port-channel p_range port-channel interface range specified by p_range.
- Valid e_range, m_range, and p_range formats include number, number range, or comma-delimited list of numbers and ranges.
- INFO_LEVEL amount of information that is displayed.
Options include:
- no parameter command displays table that summarizes TAP data.
- detail command displays TAP data summary table and a list of ACLS applied to TAP ports.
- This command displays TAP-port configuration information for interface
ethernet 36 through
40.
switch# show interface ethernet 31-35 tap Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et31 tap tap 301 31 0 tag_1 Et32 tap tap 1 132 0 tag_1 Et33 tap tap 303 233 0 tag_1 Et34 tap tap 1 334 0 tag_3 Et35 tap tap 1 345 0 tag_3 switch# - This command displays detailed TAP-port configuration information for
interface ethernet
17.
switch# show interface ethernet 17 tap detail Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et31 tap tap 301 31 0 tag_1 Port ACLs Applied ------------------------------------------------------------------- switch#
show interfaces tool
The show interfaces tool command displays tool port configuration information for the specified interfaces.
Command Mode
EXEC
Command Syntax
show interfaces [INTERFACE] tool
Parameters
- no parameter all interfaces.
- ethernet e_range Ethernet interface range specified by e_range.
- management m_range management interface range specified by m_range.
- port-channel
p_range port-channel interface range specified by
p_range.
Valid e_range, m_range, and p_range formats include number, number range, or comma-delimited list of numbers and ranges.
Example
switch# show interface ethernet 36-40 tool
Port Configured Status Allowed Id Timestamp
Mode Vlans Tag Mode
-----------------------------------------------------------------------
Et36 tool tool 201-205 Off None
Et37 tool tool 201-205 Off None
Et38 tool tool 201-205 Off None
Et39 access errdisabled All Off None
Et40 tool tool All On None
switch#show platform fm6000 keyframe
The show platform fm6000 keyframe command displays configured information for the specified keyframes. Keyframes are routable IP packets that the switch inserts into a data stream to provide contextual information that correlate timestamps inserted into data packets with the absolute UTC time and the switch’s complete ASIC time counter.
Command Mode
Privileged EXEC
Command Syntax
show platform fm6000 keyframe [KEYFRAME_ID]
Parameters
- no parameter command displays all configured keyframes.
- kf_name specifies a single keyframe to display information for.
Example
switch# show platform fm6000 keyframe
Keyframe key-2
------------------------
Egress Interface(s): Ethernet17, Ethernet18, Ethernet19, Ethernet20, Ethernet21
Source IP: 10.22.30.144
Destination IP: 10.21.1.14
Destination MAC: 00:09:00:09:00:09
Device ID: 0
Rate: 5 packet(s) per second
Keyframe key-1
------------------------
Egress Interface(s): Ethernet11, Ethernet12, Ethernet13, Ethernet14, Ethernet15
Source IP: 10.22.30.146
Destination IP: 10.21.1.4
Destination MAC: 00:10:4e:21:9f:11
Device ID: 0
Rate: 2 packet(s) per second
switch#show platform sand mcast capacity
The show platform sand mcast capacity command displays the usage details of hardware resources on Sand platform switches.
Command Mode
EXEC
Command Syntax
show platform sand mcast capacity [threshold threshold_value]
Parameter
threshold threshold_value displays the list of resources whose usage percentage is greater than or equal to the specified threshold value. Values range from 0 to 100. The default value is 100.
Guidelines
This command is supported on Sand platforms only.
Example
switch# show platform sand mcast capacity
Multicast Resources
-------------------
'*' - Applies to all Modules
'-' - Not applicable
TCAM Resources
--------------------------------------------------------------------------
Resource Module Total Used Used%
v4 MC TCAM Linecard3-Jericho3/0 4096 2 0.0
v4 MC TCAM Linecard5-Jericho5/0 4096 506 12.4
Replication Table Resources
--------------------------------------------------------------------------
Resource Module Total Used Used%
Multicast Table Row
Linecard3-Jericho3/0.0 262143 10586 4.0
Linecard3-Jericho3/1.0 262143 10576 4.0
Linecard3-Jericho3/0.1 262143 10586 4.0
Linecard3-Jericho3/1.1 262143 10576 4.0
Linecard6-Jericho6/2.0 262143 10576 4.0
switch#show tap aggregation groups
The show tap aggregation groups command displays the TAP and tool port members of the specified TAP aggregation groups.
Command Mode
EXEC
Command Syntax
show tap aggregation groups [INFO_LEVEL] [GROUP_NAMES]
- INFO_LEVEL port information to display. Options include:
- no parameter displays active TAP and tool ports.
- detail displays all configured TAP and tool ports, including inactive ports.
- GROUP_NAMES TAP aggregation groups. Options include:
- no parameter displays information for all TAP aggregation groups.
- group_list displays information for the
specified TAP aggregation group list.
Valid group_list format is a space-delimited list of one or more TAP aggregation group names.
Example
switch# show tap aggregation groups
Group Name Tool Members
---------------------------------------------------------
analyze2 Po101, Po102
analyze3 Po101, Po103
Group Name Tap Members
---------------------------------------------------------
analyze2 Et41, Et42
analyze3 Et43
switch#switchport mpls pop all
- On DCS-7280R/R2, DCS-7500R/R2, and DCS-7020R MPLS pop is configurable at the tap port using the switchport command.
- On DCS-7280R3, DCS-7500R3, and DCS7800R3 MPLS pop is configurable at the tool port using the switchport command.
- On DCS-7280R3, DCS-7500R3, and DCS7800R3 the hardware forwarding profile must also be set before MPLS pop can be used.
The no switchport mpls pop all command removes the switchport configuration by modifying the corresponding statements in running-config.
Command Mode
Interface-Ethernet Configuration
Command Syntax
switchport [tool | tap] mpls pop all
no switchport [tool | tap] mpls pop all
Parameters
- tool Tool port configuration.
- tap Tap port configuration.
Example
switch(config-if-Et1)# [no] switchport tap mpls pop allswitchport tap allowed vlan
The switchport tap allowed vlan command creates or modifies the list of VLANs for which the configuration mode interface, in TAP mode, handles tagged traffic. By default, interfaces handle tagged traffic for all VLANs. Command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP aggregation mode.
The no switchport tap allowed vlan and default switchport tap allowed vlan commands restore the TAP mode default allowed VLAN setting of all by removing the corresponding switchport tap allowed vlan statement from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tap allowed vlan EDIT_ACTION
Parameters
- v_range creates VLAN list from range of VLANs specified by v_range.
- add v_range adds specified VLANs to current list.
- all VLAN list contains all VLANs.
- except v_range VLAN list contains all VLANs except those specified by v_range.
- none VLAN list is empty (no VLANs).
- remove v_range removes VLANs specified by v_range from current list.
Example
switch(config)# interface ethernet 20
switch(config-if-Et20)# switchport tap allowed vlan 26-30
eswitch(config-if-Et20)# show active
interface Ethernet20
switchport mode tap
switchport tap allowed vlan 26-30
switch(config-if-Et20)#switchport tool encapsulation
The switchport tool encapsulation command is configured under Ethernet Interface configuration mode. When enabled on a tool port, only packets egressing this tool port will have their BR-E/VN tags stripped on DCS-7280R3, DCS-7500R3and DCS7800R3.
The no switchport tool encapsulation or default switchport tool encapsulation commands disables the 802.1br-E/VN Tag Stripping from the running-config.
Command Mode
Interface-Ethernet Configuration Mode
Command Syntax
switchport tool encapsulation {dot1br | vn-tag} strip
no switchport tool encapsulation dot1br | vn-tag} strip
defualt switchport tool encapsulation dot1br | vn-tag} strip
- dot1br strips the 802.1br-E headers.
- vn-tag strips the VN Tag headers.
- To activate BR E-Tag stripping on a tool port, add the following
configuration:
switch(config-if-Et1)# [no] switchport tool encapsulation dot1br strip - To activate VN-TAG stripping on a tool port, add the following
configuration:
switch(config-if-Et1)# [no] switchport tool encapsulation vn-tag strip
switchport tap default group
The switchport tap default group command assigns the configuration-mode interface to the specified tool group as a TAP port member. TAP aggregation groups associate a set of TAP ports with a set of tool ports. Both TAP ports and tool ports may belong to multiple TAP aggregation groups.
The no switchport tap default group and default switchport tap default group commands remove the configuration-mode interface from the TAP aggregation group to which it is assigned by deleting the corresponding switchport tap default group statement from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-port Channel Configuration
Command Syntax
switchport tap default group group_name
no switchport tap default group
default switchport tap default group
Parameter
group_name tool group name.
Restriction
This command is available on FM6000 platform switches only.
Example
switch(config)# interface port-channel 101
switch(config-if-Po101)# switchport tap default group tag-1
switch(config-if-Po101)# show interfaces port-channel 101 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Po101 access notconnect 1 1 0 tag-1
switch(config)#switchport tap identity
The switchport tap identity command associates a VLAN number to the configuration mode TAP interface. Tool ports that are configured to encapsulate packets with an dot1q-style tag enter the number specified by this command as the s-VLAN (tier 1) for packets received from this TAPs port. The default identity value is 1.
The no switchport tap identity and default switchport tap identity commands restore vlan 1 as the configuration-mode ports’s identity VLAN by removing the corresponding switchport tap identity command from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tap identity port_id
no switchport tap identity
default switchport tap identity
Parameter
port_id port’s identity VLAN. Values range from 1 to 4094. Default is 1.
Related Commands
switchport tool identity configures a tool port to encapsulate packets received from TAP ports.
Restriction
This command is available only on FM6000 platform switches.
Example
switch(config)# interface ethernet 17
switch(config-if-Et17)# switchport tap identity 171
switch(config-if-Et17)# show active
interface Ethernet17
switchport tap identity 171
switch(config-if-Et17)# show interfaces ethernet 17 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et17 access connected 1 171 0
switch(config-if-Et17)#switchport tap native vlan
The switchport tap native vlan command specifies the TAP-mode native VLAN for the configuration-mode interface. Interfaces in TAP mode associate untagged frames with the native VLAN. The default native VLAN for all interfaces is vlan 1. Command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP mode.
The no switchport tap native vlan and default switchport tap native vlan commands restore vlan 1 as the TAP-mode native VLAN to the configuration-mode interface by removing the corresponding switchport tap native vlan command from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tap native vlan v_num
no switchport tap native vlan
default switchport tap native vlan
Parameter
v_num TAP-mode native VLAN ID. Values range from 1 to 4094. Default is 1.
Restriction
This command is available only on FM6000 platform switches.
Example
switch(config)# interface ethernet 7
switch(config-if-Et7)# switchport tap native vlan 25
switch(config-if-Et7)# show interface ethernet 7 tap
Port Configured Status Native Id Truncation Default
Mode Vlan Vlan Group
-----------------------------------------------------------------------
Et7 tool connected 25 1 0 ---
switch(config-if-Et7)#switchport tap truncation
The switchport tap truncation command configures the configuration-mode interface, as a TAP port, to truncate inbound packets to the specified packet size. This command is in effect when the port is in TAP mode and the switch is in TAP aggregation mode. Command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP mode. By default, TAP ports do not truncate inbound packets.
The no switchport tap truncation and default switchport tap truncation commands restore the default behavior of not truncating packets received by the configuration-mode interface by removing the corresponding switchport tap truncation command from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tap truncation packet_size
no switchport tap truncation
default switchport tap truncation
Parameter
packet_size size of truncated packets (bytes). Values range from 100 to 9236. Default value of 0 corresponds to not truncating packets.
Restriction
This command is available only on FM6000 platform switches.
Examples
- These commands configure interface ethernet
38 to truncate packets to 150
bytes.
switch(config)# interface ethernet 38 switch(config-if-Et38)# switchport tap truncation 150 switch(config-if-Et38)# show interface ethernet 38 tap Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et38 access notconnect 1 1 150 --- switch(config-if-Et38)# - These commands configure interface ethernet
38 to send complete packets to tool ports in its TAP
aggregation
group.
switch(config-if-Et38)# no switchport tap truncation switch(config-if-Et38)# show interface ethernet 38 tap Port Configured Status Native Id Truncation Default Mode Vlan Vlan Group ----------------------------------------------------------------------- Et38 access notconnect 1 1 0 --- switch(config-if-Et38)#
switchport tool allowed vlan
The switchport tool allowed vlan command creates or modifies the list of VLANs for which the configuration-mode interface, in tool mode, handles tagged traffic. By default, interfaces handle tagged traffic for all VLANs. Command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in TAP aggregation mode.
The no switchport tool allowed vlan and default switchport tool allowed vlan commands restore the tool mode default allowed VLAN setting of all by removing the corresponding switchport tool allowed vlan statement from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tool allowed vlan EDIT_ACTION
Parameters
- v_range creates VLAN list from v_range.
- add v_range adds specified VLANs to current list.
- allVLAN list contains all VLANs.
- except v_range VLAN list contains all VLANs except those specified.
- none VLAN list is empty (no VLANs).
- remove
v_range removes specified VLANs from current
list.
Valid v_range formats include number, range, or comma-delimited list of numbers and ranges.
Example
switch(config)# interface ethernet 38
switch(config-if-Et38)# switchport tool allowed vlan 16-20
switch(config-if-Et38)# show interfaces ethernet 38 tool
Port Configured Status Allowed Id Timestamp
Mode Vlans Tag Mode
-----------------------------------------------------------------------
Et38 access notconnect 16-20 Off None
switch(config-if-Et38)#switchport tool group
- specifying the groups to which the port belongs (supersedes the port’s previous group memberships).
- adding to the list of groups to which the port belongs.
- deleting from the list of groups to which the port belongs.
TAP aggregation groups associate a set of TAP ports with a set of tool ports. A TAP port can belong to a maximum of one default TAP aggregation group.
The no switchport tool default group and default switchport tool default group commands remove the configuration-mode interface from all TAP aggregation groups to which it is assigned as a tool port by modifying the corresponding statements in running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tool group EDIT_ACTION
Parameters
- add group_list specifies additional groups to which the port belongs.
- remove group_list removes interface as a tool port member from specified groups.
- set
group_list specifies groups to which interface
belongs as a tool port.
Valid group_list format is a space-delimited list of one or more TAP aggregation group names.
Restriction
This command is available only on FM6000 platform switches.
- These commands associate interface ethernet 40
with three TAP aggregation
groups.
switch(config)# interface ethernet 40 switch(config-if-Et40)# switchport tool group set tag-1 tag-2 tag-3 switch(config-if-Et40)# show active interface Ethernet40 switchport tool group set tag-3 tag-2 tag-1 switch(config-if-Et40)# - These commands add tag-7 to the tap aggregation
groups to which interface ethernet 40
belongs.
switch(config-if-Et40)# switchport tool group add tag-7 switch(config-if-Et40)# show active interface Ethernet40 switchport tool group set tag-3 tag-7 tag-2 tag-1 switch(config-if-Et40)# - These commands specify tag-9 as the only group to
which interface ethernet
40belongs.
switch(config-if-Et40)# switchport tool group set tag-9 switch(config-if-Et40)# show active interface Ethernet40 switchport tool group set tag-9 switch(config-if-Et40)#
switchport tool identity
The switchport tool identity command configures the configuration-mode interface to add a tier-1 VLAN tag (dot1q) to packets it receives from TAP ports. The VLAN number on the dot1q tag is specified by the switchport tap identity command configured for the TAP port that supplies the packets. By default, tool ports do not encapsulate packets with the tier-1 VLAN tag.
The no switchport tool identity and default switchport tool identity commands restore the default VLAN handling method for the configuration-mode interface by removing the corresponding switchport tool identity statement from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tool identity dot1q
no switchport tool identity dot1q
default switchport tool identity dot1q
Restriction
This command is available only on FM6000 platform switches.
Example
switch(config)# interface ethernet 40
switch(config-if-Et40)# switchport tool identity dot1q
switch(config-if-Et40)# show active
interface Ethernet40
switchport mode tool
switchport tool identity dot1q
switchport tool group set tag-9
switch(config-if-Et40)#switchport tool truncation
The switchport tool truncation command configures the configuration-mode interface, as a tool port, to truncate outbound packets to 160 bytes. This command is in effect when the port is in tool mode and the switch is in TAP aggregation mode. Command settings persist in running-config without taking effect when the switch is not in TAP aggregation mode or the interface is not in tool mode. By default, tool ports do not truncate outbound packets.
The no switchport tool truncation and default switchport tool truncation commands restore the default behavior (not truncating packets that exit the configuration mode interface) by removing the corresponding switchport tool truncation command from running-config.
Command Mode
Interface-Ethernet Configuration
Interface-Port Channel Configuration
Command Syntax
switchport tool truncation packet_size
no switchport tool truncation
default switchport tool truncation
Parameter
packet_size size of truncated packets in bytes. The only permitted value is 160.
- These commands configure interface ethernet 38, as
a tool port, to truncate packets on egress to 160
bytes.
switch(config)# interface ethernet 38 switch(config-if-Et38)# switchport mode tool switch(config-if-Et38)# switchport tool truncation 160 switch(config-if-Et38)# - These commands configure interface ethernet 38 to
send complete
packets.
switch(config)# interface ethernet 38 switch(config-if-Et38)# no switchport tool truncation switch(config-if-Et38)#
tap aggregation
The tap aggregation command places the switch in TAP-aggregation configuration mode. The switch’s TAP aggregation mode is enabled or disabled by the mode (tap-agg configuration mode) command in TAP-aggregation configuration mode.
When TAP aggregation mode is enabled, normal switching and routing operations are disabled. A port’s switchport status depends on the switch’s TAP aggregation mode and the port’s switchport mode:
- TAP aggregation mode enabled: TAP and tool ports are enabled. Switching ports are errdisabled.
- TAP aggregation mode disabled: TAP and tool ports are errdisabled. Switching ports are enabled.
The no tap aggregation and default tap aggregation commands disable tap aggregation mode on the switch by removing all TAP-aggregation configuration mode commands from running-config.
TAP-aggregation configuration mode is not a group-change mode; running-config is changed immediately upon entering commands. Exiting TAP-aggregation configuration mode does not affect running-config. The exit command returns the switch to global configuration mode.
Command Mode
Global Configuration
Command Syntax
tap aggregation
no tap aggregation
default tap aggregation
Commands Available in TAP-aggregation Configuration Mode
mode (tap-agg configuration mode)
Related Command
Examples
- These commands place the switch in TAP-aggregation configuration mode and enable
TAP
aggregation.
switch(config)# tap aggregation switch(config-tap-agg)# mode exclusive switch(config-tap-agg)# show active tap aggregation mode exclusive switch(config-tap-agg)# - This command disables TAP aggregation and removes all TAP-aggregation
configuration mode commands from
running-config.
switch(config)# no tap aggregation switch(config)#
