NG Firewall Connect Apps
Captive Portal
Captive Portal allows administrators to require network users to log in or accept a network usage policy before accessing the internet.

Captive Portal can authenticate users against NG Firewall's built-in Local Directory, Active Directory (if Directory Connector is installed), or RADIUS. It can also be used to set up policies (for Policy Manager) by username (or group name if using Active Directory) rather than IP. While Captive Portal is running, captured machines will be forced to authenticate (or press OK) on the Captive Portal page before they can access the Internet.
Captive Portal is a common technique used to identify network users as described in Users.
Getting Started with Captive Portal
After installing Captive Portal, complete the following steps to get it working:
- Define which machines will be captured and required to complete the Captive Portal process before accessing the Internet. Enabling the first example rule in the Capture Rules table will force all machines on the internal interface to use the Captive Portal.
- Enter any IPs that unauthenticated machines will need to access. These can be entered in the Pass Listed Server Addresses section of the Passed Hosts tab.
- Enter any IPs that always need access to the Internet—these can be entered in the Pass Listed Client Addresses section of the Passed Hosts tab.
- On the Captive Page tab, customize the Captive Portal page. If Basic Login is chosen, set the appropriate authentication method for users on the User Authentication tab.
- Turn on the Captive Portal.
At this point, Captive Portal will evaluate your Capture Rules, and any traffic that matches will be stopped until that user has completed the Captive Portal process.
Settings
This section reviews the different settings and configuration options available for Captive Portal.
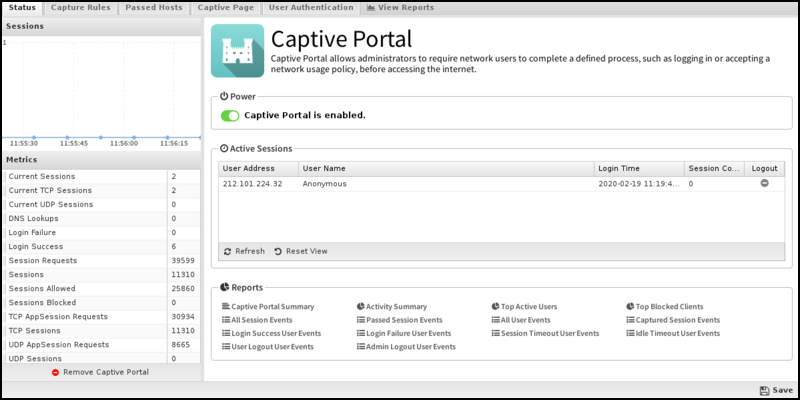
Status
This tab shows the current status of the Captive Portal. You can see information about current captured IPs, such as the username and other session information, and you can also log out of any active session.
Capture Rules
The Capture Rules tab allows you to specify rules to Capture or Pass traffic that crosses the NG Firewall.
The Rules describe how rules work and how they are configured. Captive Portal uses rules to determine whether to capture or pass each network session. The rules are evaluated in order, and the configured action will be applied on the first match. If no rules match, the traffic is allowed by default.
- If the client is authenticated, the session is passed.
- If the client is not authenticated, the protocol is TCP, and the destination port is 80, a redirect to the captive portal page is sent.
- If the client is not authenticated, the protocol is TCP, and the destination port = 443, then a redirect to the captive portal page is sent. (The certificate will not match as the captive portal is not the requested server)
- If the client is not authenticated and the destination port is 53, a DNS response is sent after it is validated as a valid DNS request.
- If the client is not authenticated and the session has a destination port != 53,80,443, then the session is blocked.
Figure 2. Capture Rules Tab

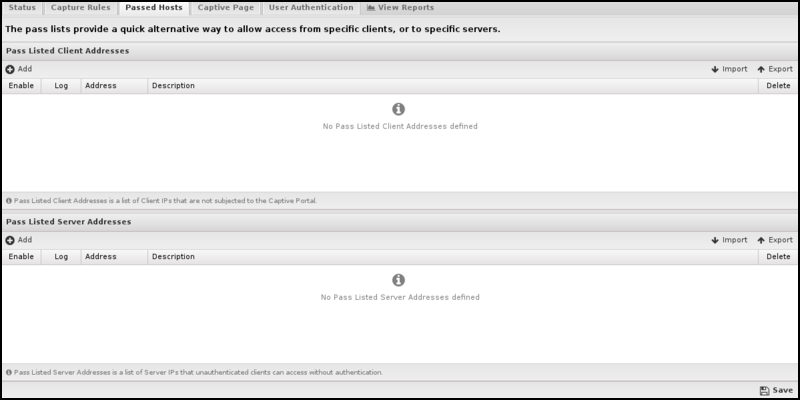
Passed Hosts
The Pass Hosts tab allows you to specify machines that either a) should not be affected by Captive Portal or b) servers that machines behind Captive Portal should be able to access even if unauthenticated.
- Pass Listed Client Addresses: Captive Portal will not affect these machines. This is useful for servers and devices without browsers.
- Pass Listed Server Addresses: Machines behind the Captive Portal can access these servers whether or not they have been authenticated through the Captive Portal. Typically, these will be any DNS or DHCP servers separated from their clients by the NG Firewall. This is unnecessary if the NG Firewall is handling DHCP or DNS.
Figure 3. Passed Hosts Tab
Captive Page
This tab controls the type of Captive Portal page displayed to unauthenticated users. Please note that you can use HTML in the Captive Portal page fields; however, invalid HTML will prevent the page from rendering properly.
- Basic Message: Select this option if users should see (or accept) a message before being allowed to the internet. It has several tunable properties such as Page Title, Welcome Text, Message Text, and Lower Text. If Agree Checkbox is enabled, users must check a checkbox (labeled with the Agree Text) before continuing.
- Basic Login: Select this option if users should see a page that requires them to log in. Similar to Basic Message, it has several properties that can be configured. When the login/continue button on the page is clicked, the user will be authenticated. You must also set your authentication method on the User Authentication tab.
- Custom: Select this option if you would like to upload a custom Captive Portal page. This is for experienced web developers who are comfortable with HTML, Python, and JavaScript. The Edge Threat Management Support department can not help develop or troubleshoot custom Captive Portal pages. If Custom is selected, it is advised to turn off automatic upgrades—newer versions of NG Firewall may be incompatible with any custom captive page
Note: Select 'Basic Message' when using "Any OAuth provider" for User Authentication. All the "Page Configuration" options except the agree checkbox and text will be used when generating the OAuth provider selection page.
Figure 4. Captive Page Tab

HTTPS/Root Certificate Detection
- Disable Certificate Detection: No checking for the root certificate.
- Check Certificate. Show a warning when it is not detected: Check the root certificate. If not found, display a warning with instructions on how to install the certificate.
- Require Certificate. Login is prohibited when not detected: The connection is blocked if it is not found, and the client is instructed to install the certificate.
The Preview Captive Portal Page button can be used to view what the configured captive page looks like. This button only works when Captive Portal is on.
Session Redirect- Block instead of capture and redirect unauthenticated HTTPS connections: The browser redirecting from an HTTPS URL to the captive page will show a certificate error as the captive page is not requested. To avoid this error message, block the traffic and show nothing instead of showing the captive login page.
- Use hostname instead of IP address for the capture page redirect: Create the browser redirect using the hostname instead of the server's IP address.
Warning:If enabled, the admin must ensure that the hostname properly resolves to the internal IP of the NG Firewall on all internal networks. If internal hosts use the NG Firewall for DNS, this is automatic. If using another internal DNS server, the administrator must configure DNS to properly resolve the correct internal IP on all internal networks. If this is not configured properly, the Captive Portal will not function properly, as clients cannot reach the Captive Portal page. The host will NOT be able to reach the captive portal page if the hostname is resolved to the external IP of the NG Firewall.
This option is useful for organizations with valid certificates on the NG Firewall server who want to avoid the cert warning on the capture page.
Note: This has nothing to do with the first warning caused by serving/spoofing the 301 redirect from a website to the capture page. - Always use HTTPS for the capture page redirect: When using the Captive Portal, always redirect to the HTTPS version of the login page.
- Redirect URL: Users will be rerouted to this site after successful authentication. If the Redirect URL is blank, they will be sent to the original destination. Make sure to enter a complete URL (e.g., http://edge.arista.com), or this setting will not properly operate.
Custom Pages
You can create a custom.html file and place it, along with any supporting image files, etc., into a zip file and then upload it via the administrative interface. This allows you to customize the look and layout of the page while leveraging the existing code and application settings. To use this model, you must be familiar with HTML and forms.
Customized Captive Portal pages are "used at your own risk." The Edge Threat Management Support department cannot assist you in creating, updating, or troubleshooting Custom captive pages.
User Authentication
- None: Is used in cases where no login is required.
- Local Directory: Use the NG Firewall's built-in Local Directory () to authenticate users.
- RADIUS: Use an external RADIUS server to authenticate users. This option requires that the Directory Connector be installed, enabled, and configured.
- Active Directory: This option can be used if the user should be authenticated against an Active Directory server. It requires the Directory Connector to be installed, enabled, and configured.
- Any Directory Connector: This option allows users to authenticate against any configured and enabled Directory Connector methods. It requires the Directory Connector to be installed, enabled, and configured.
- Google Account: Can be used to allow users to authenticate via OAuth using a Google account.
- Facebook Account: This can be used to allow users to authenticate via OAuth using a Facebook account.
- Microsoft Account: can be used to allow users to authenticate via OAuth using a Microsoft account.
- Any OAuth Provider: This option allows users to select and authenticate using any supported OAuth providers. When this option is selected, unauthenticated users will first encounter the OAuth selection page, where they will click the icon or link corresponding to the provider account they want to use.
- Idle Timeout: This option controls the time before a host is automatically logged out if no traffic is seen. While a machine may be idle, it is still active on the network level. In this case, Idle means the Captive Portal sees no new TCP or UDP connections.
- Important: It is recommended to leave this at zero (not enabled).
- Timeout: This option controls the time before a computer is automatically logged out. After this, the user must log in again through the Captive Portal. Timeouts greater than 1440 minutes (1 day) are not recommended. The authenticated table is stored in memory and will be flushed on reboot/upgrade. Additionally, the logout time should be shorter than your DHCP lease time to ensure IPs don't change before the Captive Portal timeout.
- Allow Concurrent Logins: This option controls whether multiple machines can use the same login credentials simultaneously. If enabled, two or more users can log in with the same username/password at the same time.
- Allow Cookie-based authentication: When enabled, a cookie is added to the user's browser and used to authenticate the user in future sessions. Cookies must be allowed by the browser and not cleared when closing the browser or by other security programs. When the Cookie timeout is reached, the user must re-authenticate (regardless of activity). The default is 24 hours.
- Track logins using MAC address: When enabled, Captive Portal will use the MAC address instead of the IP address to identify the client machine. If the MAC address for a given IP address is unknown, it will revert to using an IP address. This option is useful on smaller flat networks where the NG Firewall is on the same network segment as all the hosts, and you have a very long timeout period such that a client's IP address might change.
Figure 5. User Authentication Tab

Captive Portal Reports
The Reports tab provides a view of all reports and events for all traffic handled by the Captive Portal.
Reports
This application's reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports and custom reports created will be listed.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries:
| Report Entry | Description |
|---|---|
| Captive Portal Summary | A summary of Captive Portal actions. |
| Activity Summary | A summary of Captive Portal activity. |
| Top Active Users | The top active users that logged in to Captive Portal. |
| Top Blocked Clients | The top clients were blocked by Captive Portal because they were not logged in. |
| All Session Events | All sessions are processed by the Captive Portal. |
| Passed Session Events | Sessions matching passed hosts. |
| Captured Session Events | Sessions matching capture rules. |
| All User Events | All user sessions are processed by the Captive Portal. |
| Login Success User Events | Successful logins to Captive Portal. |
| Login Failure User Events | Failed logins to Captive Portal. |
| Session Timeout User Events | Sessions that reached the session timeout. |
| Idle Timeout User Events | Sessions that reached the idle timeout. |
| User Logout User Events | All user logout events. |
| Admin Logout User Events | Sessions logged off by the admin. |
Related Topics
IPsec VPN
The IPsec VPN service provides secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session.
Settings
This section reviews the different settings and configuration options available for IPsec VPN.
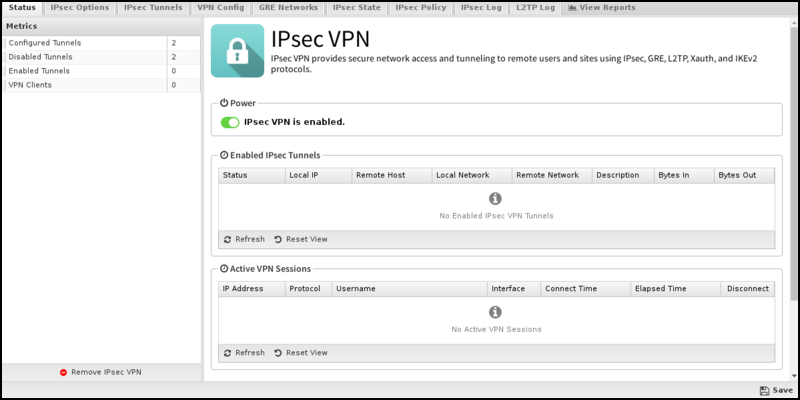
Status
- Enabled IPsec Tunnels
- This section shows a list of all IPsec tunnels that have been created and enabled. For tunnels that are active, the status will display the connection details reported by the IPsec subsystem. For active tunnels, the status will display the connection details reported by the IPsec subsystem. For inactive tunnels, the configuration information will be displayed.
- Active VPN Sessions
- This section shows a list of all active L2TP and Xauth connections. In addition to the connection details, a Disconnect column can forcefully disconnect an active session. Please note that there is no confirmation when you click the Disconnect icon. The corresponding session will be immediately terminated.
- Bypass all IPsec traffic
- When this checkbox is enabled, traffic from IPsec tunnels will bypass all applications and services on the NG Firewall server. This was the only behavior available in previous versions of NG Firewall, so this option is enabled by default to maintain equivalent functionality on upgrade. If you disable this checkbox, traffic from IPsec tunnels can now be filtered through all active applications and services. Also, note that this only applies to plain IPsec tunnels. Traffic from L2TP and Xauth VPN clients will always pass through all active applications and services.

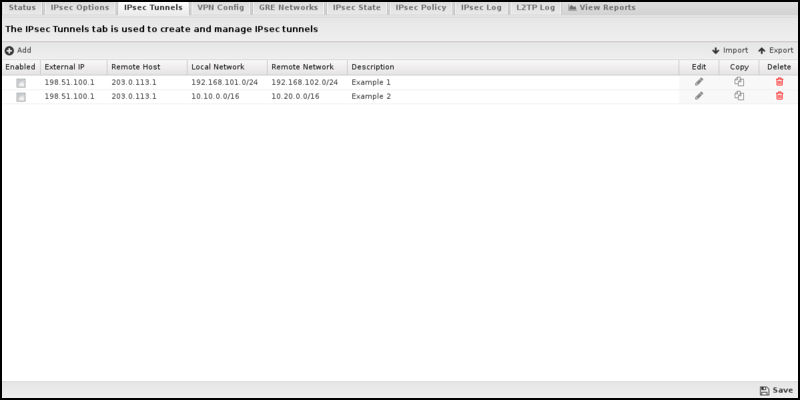
IPsec Tunnels
The IPsec Tunnels tab is where you create and manage the IPsec VPN configuration. The main tab display shows a summary of all IPsec tunnels that have been created.
Tunnel Editor When you create a new tunnel or edit and existing tunnel, the tunnel editor screen will appear with the following configurable settings:
| Name | Description |
|---|---|
| Enabled | This checkbox allows you to set a tunnel to enabled or disabled. |
| Description | This field should contain a short name or description. |
| Connection Type | This field allows you to set the connection type to any of the following:
|
| IKE Version | The IKE version should use either version 1 or version 2. Both endpoints must use the same IKE version. |
| Connect Mode | This field controls how IPsec manages the corresponding tunnel when the IPsec process restarts:
|
| Interface | This field allows you to select the network interface associated with the IPsec tunnel on the NG Firewall server. For most situations, choose Active WAN to bind to the active Internet interface. This allows the VPN tunnel to reconnect using a secondary WAN interface in case of Internet failover. The Active WAN option is available when using the WAN Failover app. Alternatively, you can select a specific interface, or you can manually configure an IP address using the Custom option and manually inputting the IP address. |
| Any remote host | Enabling this option allows the VPN Server to accept tunnel connections from any IP Address. This option enables the remote side of the tunnel to connect from a dynamic IP address or via a secondary WAN link. This option switches the Connect Mode to On Demand and removes the Remote Host field, as these options are not used when allowing connections from any remote host. |
| Remote Host | This field should contain the host's public IP address to which the GRE tunnel will be connected.
Warning: Using host names with IPsec tunnels can often cause problems, especially if you have enabled the L2TP/Xauth VPN server. We strongly recommend the use of IP addresses in the Remote Host field.
|
| Local Identifier | This field is used to configure the local identifier used for authentication. When this field is blank, the value in the *External IP* field will be used. |
| Remote Identifier | This field is used to configure the remote identifier used for authentication. When this field is blank, the value in the Remote Host field will be used.
Important: If the remote host is located behind any kind of NAT device, you may need to use the value % in this field for a connection to be successfully established.
|
| Local Network | This field configures the local network that will be reachable from hosts on the other side of the IPsec VPN. |
| Remote Network | This field configures the remote network that will be reachable from hosts on the local side of the IPsec VPN. |
| Shared Secret | This field should contain the shared secret or PSK (pre-shared key) used to authenticate the connection and must be the same on both sides of the tunnel for the connection to be successful. Because the PSK is used as the encryption key for the session, using long strings of a random nature will provide the highest level of security. |
| DPD Interval | The number of seconds between R_U_THERE messages. Enter 0 to disable this feature. |
| DPD Timeout | The number of seconds for a dead peer tunnel to be restarted. |
| Ping Address | The IP address of a host on the remote network to ping for verifying that the tunnel is connected and routed. Leave blank to disable. |
| Ping Interval | The time in minutes between ping attempts of the ping address. Leave as 0 to disable. The recommended value is 1 when using a Ping address. |
| Authentication and SA/Key Exchange | If you leave the Phase 1 and Phase 2 manual configuration checkboxes disabled, IPsec will automatically attempt to negotiate the encryption protocol with the remote peer when creating the Tunnel. Given the number of different IPsec implementations and versions and the overall complexity of the protocol, best results can often be achieved by enabling manual configuration of these two options and selecting Encryption, Hash, DH Key Group, and Lifetime values that exactly match the settings configured on the peer device. |
VPN Config
| Name | Description |
|---|---|
| Enable L2TP/Xauth/IKEv2 Server | Use this checkbox to enable or disable the L2TP/Xauth/IKEv2 server. |
| L2TP Address Pool | This field configures the pool of IP addresses assigned to L2TP clients while connected to the server. The default 198.18.0.0/16 is a private network generally reserved for internal network testing. It was chosen as the default because it is used less frequently than other RFC-1918 address blocks and, thus, is less likely to conflict with existing address assignments on your network. |
| Xauth Address Pool | This field configures the pool of IP addresses assigned to Xauth clients while connected to the server. The default 198.19.0.0/16 is a private network generally reserved for internal network testing. It was chosen as the default because it is used less frequently than other RFC-1918 address blocks, and thus, is less likely to conflict with existing address assignments on your network. |
| Custom DNS Servers | Leave both fields blank to have L2TP and Xauth clients use the NG Firewall server for all DNS resolution. Alternatively, if you have other DNS servers you want clients to use, you can enter IP addresses in these fields. |
| IPsec Secret | This is the shared secret that will be used between the client and server to establish the IPsec channel that will secure all L2TP and Xauth communications. |
| Allow Concurrent Logins | If enabled, the same credentials can be authenticated simultaneously from multiple devices. |
| User Authentication | In addition to the IPsec Secret configured above, VPN clients must authenticate with a username and password. To use the Local Directory, select this option and click the Configure Local Directory button to manage use credentials. Alternatively, you can use an external RADIUS server for authentication by selecting the RADIUS option and clicking the Configure RADIUS button to configure the RADIUS server options. |
| Server Listen Addresses | This list configures one or more of your server IP addresses to listen for inbound VPN connection requests from remote clients. Clicking the Add button will insert a new line, allowing the entry of another server IP address. |
GRE Networks
The GRE Networks tab is where you create and manage connections to remote GRE servers. Generic Routing Encapsulation (GRE) is a tunneling protocol that can encapsulate a wide variety of network layer protocols inside virtual point-to-point links over an Internet Protocol network.
GRE Address Pool
This field configures the pool of IP addresses assigned to interfaces created and associated with tunnels added on the GRE Networks tab. The default 198.51.100.0/24 is a private network generally reserved for internal network testing. It was chosen as the default because it is used less frequently than other RFC-1918 address blocks and, thus, is less likely to conflict with existing address assignments on your network. If you use GRE to connect multiple NG Firewall servers, you need to configure a different, unused pool on each server.
The main tab display shows a summary of all GRE Networks that have been created.
Network Editor
When you create a new GRE Network or edit and existing network, the network editor screen will appear with the following configurable settings:
| Name | Description |
|---|---|
| Enable | This checkbox allows you to set a network to either enabled or disabled. |
| Description | This field should contain a short name or description. |
| Interface | This field allows you to select the network interface that should be associated with the GRE Network on the NG Firewall server. When you select a valid interface, the Local IP field (see below) will automatically be configured with the corresponding IP address. If, for some reason, you want to configure an IP address that is not currently active manually, you can set the Interface to Custom and manually input the IP address below. |
| External IP | Use this field to configure the IP address associated with the GRE Network on the NG Firewall server. Normally, this field will be read-only and automatically populated based on the Interface selected earlier. If you select Custom as the interface, you can manually enter the local IP address. |
| Remote Host | This field should contain the host's public IP address to which the GRE tunnel will be connected. |
| Remote Networks | This field configures the list of remote network traffic that should be routed across this GRE tunnel. Networks should be entered after per line in CIDR (192.168.123.0/24) format.
Note: The subnets in Remote Networks must not conflict with your GRE Address Pool.
|
IPsec State
The IPsec State tab allows you to see the status of all established IPsec connections. There will typically be two entries per tunnel, one with details about the local side of the connection and another with details about the remote side.
IPsec Policy
The IPsec Policy tab allows you to see the routing table rules associated with each active IPsec VPN.
IPsec Log
The IPsec Log tab lets you see the low-level status messages the underlying IPsec protocol components generate. This information can be very helpful when diagnosing connection problems or other IPsec issues.
L2TP Log
The L2TP Log tab lets you see the low-level status messages generated by the underlying L2TP protocol daemon. This information can be very helpful when diagnosing connection problems or other L2TP issues.
Reporting
The Reports tab provides a view of all reports and events for all connections handled by IPsec VPN.
Related Topics
IPsec VPN Reports
The Reports tab provides a view of all reports and events for all connections handled by IPsec VPN.
Reports
This application's reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries:
| Report Entry | Description |
|---|---|
| IPsec VPN Summary | A summary of IPsec VPN actions. |
| Hourly Tunnel Traffic | The amount of IPsec tunnel traffic over time. |
| Top Tunnel Traffic | The amount of traffic for each IPsec tunnel. |
| Top Active Users | The top IPsec VPN users by number of sessions. |
| Top Download Users | The top IPsec users are grouped by the amount of data downloaded. |
| Top Upload Users | The top IPsec users are grouped by the amount of data uploaded. |
| Top Protocols | The top IPsec VPN connections by protocol. |
| L2TP/Xauth Events | Shows all user L2TP/Xauth events. |
| Tunnel Connection Events | Shows all IPsec VPN tunnel connection events. |
| Tunnel Traffic Events | Shows all IPsec tunnel traffic statistics events. |
OpenVPN
OpenVPN enables you to create an SSL-based VPN (virtual private network) that supports both site-to-site and client-to-site tunnels. This allows your road warrior users to connect to local resources as if they were in the office or connect the networks of several geographically distant offices - all with the added security of encryption protecting your data. OpenVPN supports any operating system with an OpenVPN-compatible VPN client (which is almost every OS), even smartphones! The OpenVPN application can run as a server, allowing remote clients to connect to the NG Firewall server, and the OpenVPN application can connect to other remote NG Firewall servers as a client. The VPN Overview article provides general guidance on which VPN technology may best fit different scenarios.
The Remote Clients sub-tab configures all the Remote Clients that can connect to this OpenVPN server. A Remote Client is any entity that connects to this OpenVPN server as a client. This includes remote desktops, laptops, devices, road warriors, etc., as well as remote OpenVPNs and remote NG Firewall networks.
Initially, no clients are allowed to connect, and a unique entry must be created for each remote client you want to allow to connect to this server.
- Enabled—If checked, this client is enabled. If unchecked, it is disabled and can not connect.
- Client Name - A unique name for the client. (alphanumerics only)
- Group - The group for this client. More information is below.
- Type - The type of this client. An individual client for a single host is like a remote desktop or laptop. Network for an entire remote network that the server should also be able to reach.
- Remote Networks - The remote network in CIDR notation if this remote client is of type Network. For example, 192.168.1.0/24 means that the 192.168.1.* The network lives behind the remote client and should be reachable from the server. A comma-separated list of CIDR networks can be used if multiple networks are reachable through this remote client. These networks are automatically exported so hosts on the main network and other remote clients can reach these networks.
- Click here to download this client's configuration zip file for other OSs (Apple/Linux/etc).
- This file provides a zip file with the OpenVPN client configuration files. This file can configure various OpenVPN clients for various OSs, like Linux, Apple, and even some phones/tablets/devices.
- Click here to download this client's configuration file for remote OpenVPN clients.
- This file provides a zip file with the OpenVPN client configuration for setting up a remote OpenVPN application to connect as a client to this server.
- Click here to download this client's configuration ONC file for Chromebook.
- This file provides an ONC file that can be used to configure your Chromebook as a client to connect to the NG Firewall OpenVPN server. On the target device, browse to chrome://net-internals and use the Import ONC file.
First, you must install the OpenVPN client on the client system. You can download the client from here: https://openvpn.net/download-open-vpn/. After installing the OpenVPN client on the remote client, you can import the OpenVPN profile into the client.
Groups
Groups are a convenient feature for "group" clients; some settings can be applied to that entire group. By default, there will be a Default Group. Each group has the following settings:
| Setting | Description |
|---|---|
| Full Tunnel | If checked, remote clients will send ALL traffic bound to the internet through the VPN. This allows NG Firewall to filter ALL internet traffic for connected clients by "proxying" it through the VPN and then out through NG Firewall's internet connection. This will have no effect on remote OpenVPN clients. If unchecked, only traffic destined to the local network is subject to filtering. |
| Push DNS | If enabled, OpenVPN will "push" some DNS configuration to the remote clients when they connect. This is useful if you want some local names and services to resolve via DNS that would not be publicly resolved properly. |
| Push DNS Server | If set to OpenVPN Server, the IP of the NG Firewall server itself will be pushed to the remote clients, and all remote clients will use the NG Firewall for all DNS lookups. If Custom is selected, one or two DNS entries can be specified that will be used for DNS resolution. |
| Push DNS Custom 1 | If Push DNS Server is set to Custom, this IP will be pushed to remote clients to use for DNS resolution. It is important to export this address if traffic should travel through the VPN tunnel. If this value is blank, nothing will be pushed. |
| Push DNS Custom 2 | This is just like Push DNS Custom 1, except it sets the secondary DNS value. If blank, no secondary DNS will be pushed. |
| Push DNS Domain | If set, this domain will be pushed to remote clients to extend their domain search path during DNS resolution. |
These settings will apply to all clients belonging to that group. Many sites will only have one group because all clients need the same settings. However, some clients have some Full Tunnel remote clients and some Split Tunnel remote clients. In this case, you need two groups where each client belongs to the appropriate group.
Exported Networks
Exported Networks is a list of networks reachable through the OpenVPN server for remote clients. These routes are pushed to remote clients when they connect, telling remote clients to reach the specified network through the OpenVPN server.
For example, exporting 1.2.3.4/24 will result in all 1.2.3. traffic going through the OpenVPN server.
- This network will be exported/pushed to connect remote clients if Enabled is checked.
- Export Name is a name that is purely used for documentation purposes.
- The network is the network in CIDR notation.
Settings
The Status tab lists open connections, the time the tunnels were created, and transmits statistics.
Status
The Status tab shows you a list of open connections, the time the tunnels were created, and transmit statistics.
Connected Remote Clients
This table shows the currently connected remote clients connected to this OpenVPN (if the server is enabled.)
| Name | Description |
|---|---|
| Address | The IP of the remote client. |
| Client | The OpenVPN client name. |
| Start Time | The time that the client connected. |
| Rx Data | The amount of data received from this client in this session. |
| Tx Data | The amount of data sent to this client in this session. |
Remote Server Status
This table shows the remote servers this OpenVPN is connects to as a client.
| Name | Description |
|---|---|
| Name | The name of the remote server. |
| Connected | The current connection status |
| Rx Data | The amount of data received from this client in this session. |
| Tx Data | The amount of data sent to this client in this session. |
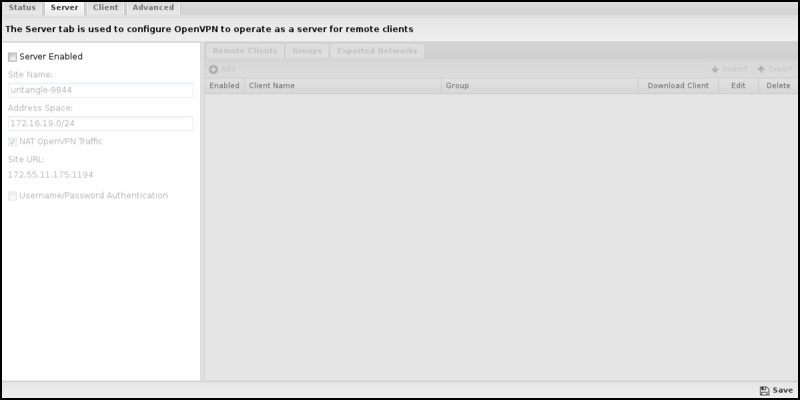
Server
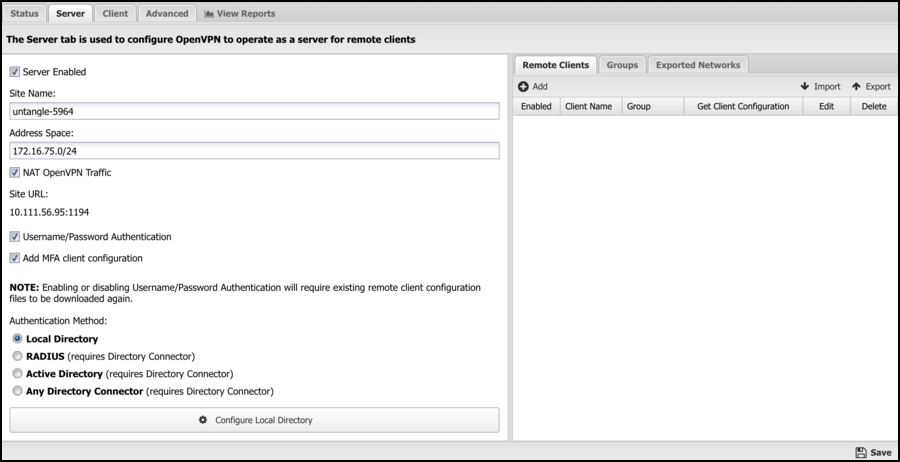
The Server tab includes all the configuration for OpenVPN's server functionality.
Site Name is the name of this OpenVPN site. A random name is chosen so that it is unique. A new name can be given, but it should be unique across all NG Firewall sites in the organization. For example, if the company name is "MyCompany," then "mycompany" is a bad site name if you have multiple NG Firewalls deployed, as it might be used elsewhere. The Site Name must be unique.
The site URL shows the URL remote clients will use to connect to this server. This is just for reference. Verify that this address will be resolved and publicly accessible from remote networks. This URL can be configured in.
If Server Enabled is checked, the OpenVPN server will run and accept connections from configured Remote Clients. If unchecked, the OpenVPN server will not run, and no server services will be provided.
Address Space defines an IP network/space for the VPN to use internally. The Address Space must be unique and separate from all existing networks and other address spaces on other OpenVPNs. A default will be chosen that does not conflict with the existing configuration.
NAT OpenVPN Traffic will NAT all traffic from remote networks to local networks to a local address. This helps solve routing and host-based firewall issues. The default and recommended values are enabled.
Username/Password Authentication can be enabled to activate two-factor authentication, requiring clients to provide a username and password when connecting.
Add MFA client configuration can be enabled to activate multi-factor authentication using a TOTP app. This feature uses the Local Directory users and requires each user to be configured with multi-factor authentication and paired with a TOTP app.
Authentication Method is used to select the authentication method for clients when Username/Password authentication is enabled.
Remote Clients
Client
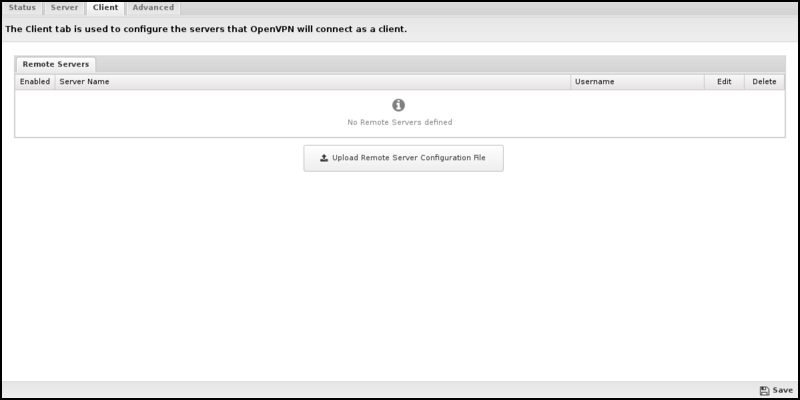
The Client tab configures which remote servers this OpenVPN will connect to as a client.
Remote Servers
The Remote Servers table lists the currently configured remote servers that OpenVPN is configured to connect.
- Return to this OpenVPN and click the Browse button below the Remote Servers table.
- Select the zip file downloaded from the OpenVPN server computer and select OK.
- Press the Submit button to upload the zip file to OpenVPN, adding a new entry into the Remote Servers grid based on the configuration in the submitted zip file.
Suppose the remote server requires authentication using a username or password. In that case, you must edit the configuration, enable the Username/Password authentication checkbox, and enter the username and password to be used when establishing the connection.
After connected to a remote server, you can reach their exported networks. They will also be able to reach the networks on this server, specified as the remote network configuration.
Advanced
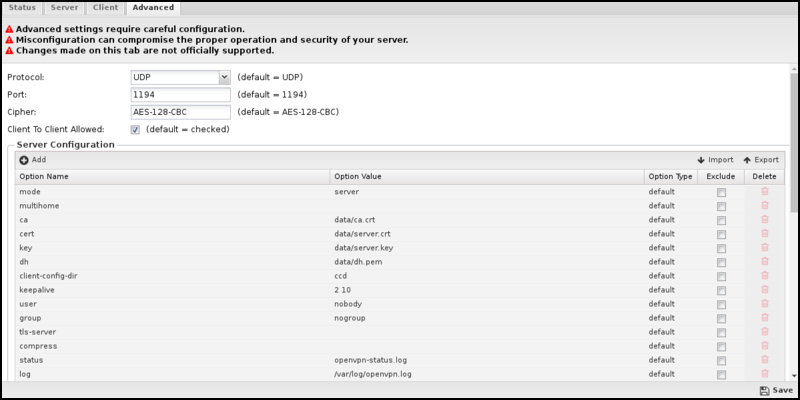
The Advanced tab is provided for advanced users with detailed knowledge and understanding of OpenVPN who need specific configuration changes to address unique or unusual situations. It is possible to break your OpenVPN configuration completely with a single wrong character, misplaced space, or by changing a configuration option that probably shouldn't be changed. Changes you make on this page could compromise your server's security and proper operation and are not officially supported.
Common Settings
At the top of the Advanced page are the Protocol, Port, and Cipher options. These must be the same on the client and server for connections to work. Since they are the options most frequently modified, they can be easily configured here and will apply to both the client and server.
The Client to Client Allowed checkbox turns traffic on or off, passing between OpenVPN clients. When enabled, all clients will have full network access to each other when connected. If disabled, traffic will not be allowed to flow between connected clients.
Server Configuration and Client Configuration
Suppose you require changes to other low-level parameters. In that case, the Server and Client Configuration grids allow you to control the generated OpenVPN configuration file effectively. Both grids work similarly, with each configuration applied to the corresponding server or client openvpn.conf file, respectively.
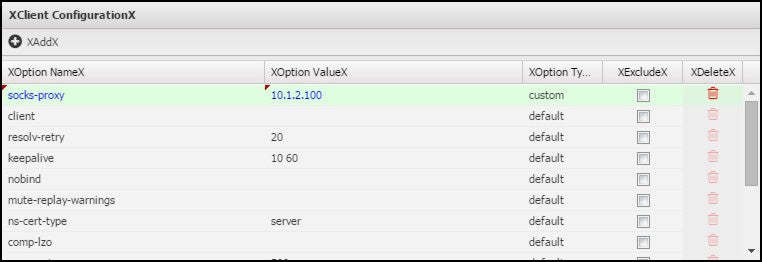
Both lists contain config items comprised of an Option Name and Option Value pair. By default, all items in both configuration grids are read-only. The lists represent the default configuration settings used for the server and client configuration files. The default items cannot be modified or deleted; they can only be excluded. When you exclude an item, it is effectively removed from the resulting configuration file. To change one of the default items, add a new item with the same Option Name and input the Option Value that you want to be used. This will effectively override the default. The same method can also be used to add configuration items not included in the default list.
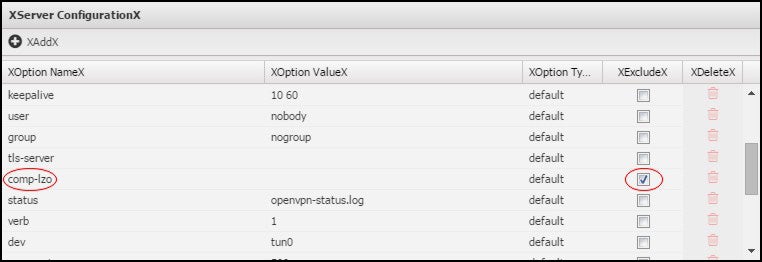
Exclude Default Configuration Item
This example shows how to disable the comp-lzo option in the server configuration file to turn off compression:
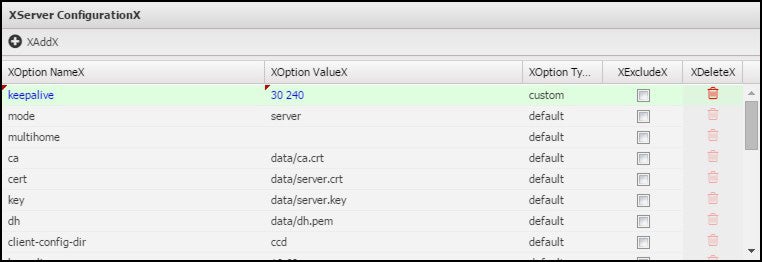
Modify Default Configuration Item
This example shows how to change the default keepalive setting in the server configuration file:
Add New Configuration Item
This example shows how to add a socks-proxy setting to the client configuration file:
OpenVPN Reports
The Reports tab provides a view of all reports and events for all connections handled by OpenVPN.
Reports
You can access the applications reports via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries:
| Report Entry | Description |
|---|---|
| OpenVPN Summary | A summary of OpenVPN actions. |
| OpenVPN Bandwidth Usage | The approximate amount of data transferred over openvpn connections. |
| OpenVPN Events | The number of login and logout events over time. |
| OpenVPN Sessions | The amount of openvpn sessions over time. |
| Top Clients (by usage) | The number of bytes transferred grouped by remote client. |
| Connection Events | OpenVPN client connection events. |
| Statistic Events | Shows all OpenVPN connection traffic statistics events. |
Tunnel VPN
The Tunnel VPN service app provides secure tunnels to remote servers and services and determines which traffic on the network goes through these tunnels.
Use Cases
Tunnel VPN is used in a wide variety of configurations. Some common scenarios are described below.
Branch Offices
Organizations with one or more small branch offices can use Tunnel VPN to send all internet-bound traffic at the remote small branch through the central site for security and filtering. This alleviates the need to actively manage the security and filtering configuration at the branch offices and allows for easier management at the central site and centralized monitoring and reporting.
Remote Security Services
Many cloud-based security services, or Cloud Access Security Brokers (CASB), enforce policy and security network traffic as it transits from the local infrastructure to the Internet.
Tunnel VPN can be configured to send traffic, either in total or selectively, to the desired cloud services. For example, Tunnel VPN can send all port 25 (SMTP) through a specific tunnel to a cloud email archiving service. Alternatively, you could send DNS, web, or all traffic through dedicated cloud services.
SD-WAN
SD-WAN (software-defined networking) type deployments often need to maintain several tunnels to dedicated CASBs or internet "exit" points. Tunnel VPN allows you to maintain connections to several cloud exit points and prioritize the tunnels such that if one tunnel goes down, the next available tunnel will be leveraged.
Combined with WAN Failover and WAN Balancer, this provides an easy way to ensure the network is always online and the best possible tunnel is being used for connectivity, regardless of cloud services going up or down or individual ISPs or internet connections being up or down.
Privacy
Tunnel VPN can connect to other NG Firewall services or most Privacy VPN services (like NordVPN, ExpressVPN, Private Internet Access, and so on).
Many countries have imposed limits or monitored "forbidden" content. This can range from content expressing certain political views to information on historical events, region-locked content, unapproved types of entertainment, or copyrighted material. Also, many locations do not have access to ISPs (or governments) that respect net neutrality.
For these locations, Tunnel VPN can provide safe encrypted passage to a location that supports freer internet and net neutrality. Rules can either statically determine what traffic goes through a tunnel (specific hosts or ports) or can dynamically shift which traffic uses the tunnel using tags. For example, a host can be switched to using a tunnel once Skype or Bittorrent usage is detected.
Settings
This section discusses the different settings and configuration options available for Tunnel VPN.
Status
The Status tab shows the on/off status of Tunnel VPN.
Tunnels
The Tunnels tab configures the encrypted tunnels to remote servers/services.
- Enabled—If checked, this tunnel is enabled. If not enabled, it will not connect and will not be active.
- Tunnel Name - A unique name for the tunnel.
- Provider - this is the remote service/provider. Select the appropriate option for the remote service.
- Arista - this is for connecting to a remote NG Firewall server.
- NordVPN - this is for connecting to NordVPN at [nordvpn.com].
- ExpressVPN - this is for connecting to ExpressVPN at [expressvpn.com].
- Any remote service that supplies a zip file with an OpenVPN configuration inside uses a custom zip file.
- Custom zip file with username/password - used for any remote service that supplies a zip file with an OpenVPN configuration inside and requires a valid username and password.
- Custom Ovpn file - used for any remote service that supplies an Ovpn file.
- Custom Ovpn file with username/password - used for any remote service that supplies an Ovpn file, which also requires a valid username and password.
- A custom conf file is used for any remote service that supplies an OpenVPN conf file.
- Custom conf file with username/password - used for any remote service that supplies an OpenVPN conf file and requires a valid username and password.
- Select the VPN Config File button to upload the zip/conf/ovpn file.
- The username specifies the username (if required).
- Password specifies the password (if required).
First, provide a name and choose the remote provider type. After choosing the provider type, the instructions describe configuring the rest of the fields.
All enabled tunnels will attempt to connect to the remote services on save. The log can be viewed on the Log tab.
Rules
Rules control what traffic is routed through the tunnels. The Tunnel VPN rules are run before any WAN Balancer rules are evaluated, and the routing table is consulted. If a Tunnel VPN rule matches and the tunnel is active, the traffic will exit through the tunnel regardless of the WAN Balancer or routing configuration. In other words, Tunnel VPN takes precedence over any other routing configuration.
The Rules describe how rules work and how they are configured. As with all rules, rules are evaluated in order, and the action is taken from the first matching rule.
Example: Static Rules
- If the following conditions are met:
- Destination Port is 25
- Perform the following action(s):
- Destination Tunnel: tunnel-1
This will route all port 25 traffic through tunnel-1. If tunnel-1 is offline, traffic will be routed normally.
Example: Preference Order
- Rule 1: Always (no conditions) perform the following action, Destination Tunnel: 'tunnel-1'
- Rule 2: Always (no conditions) perform the following action, Destination Tunnel: 'tunnel-2'
- Rule 3: Always (no conditions) perform the following action, Destination Tunnel: 'tunnel-3'
Then traffic will always route to tunnel-1. If tunnel-1 is not available it will route to tunnel-2. If tunnel-2 is not available, it will be routed to tunnel-3. If tunnel-3 is not available, it will normally route.
Example: Dynamic Rules
Unlike most solutions, the NG Firewall also allows for automatic dynamic adjustment of traffic through the tunnel using tags. Hosts can be tagged manually by tagging the appropriate device or username associated with a host or automatically using trigger rules Events.
- If allow of the following conditions are met:
- Client Tagged is bittorrent-use.
- Perform the following action(s):
- Destination Tunnel: tunnel-1.
This will route any hosts tagged bittorrent-use through tunnel-1. The trigger rule will ensure that any host detected using BitTorrent will automatically be tagged so that each session after the detection will go through the tunnel.
Example: Multiple Triggers
- If the host uses Skype, the tag host tunnel expires in 10 minutes.
- If the host is accessing Craigslist, the tag host tunnel expires in 10 minutes.
- If the host is accessing Gaming category website, tag host tunnel expires in 10 minutes.
Then add the following Tunnel VPN Rule:
- If allow of the following conditions are met:
- Client Tagged is a tunnel.
- Perform the following action(s):
- Destination Tunnel: tunnel-1.
If a host does any of that action, it will automatically be switched to the tunnel (until the tag expires, 10 minutes after the specified activity stops).
Log
This shows the raw OpenVPN log file.
This is useful for debugging issues if the tunnels are not initializing correctly to the service providers.
Related Topics
Tunnel VPN Reports
There are currently no specific reports for Tunnel VPN. However, all traffic is logged using the appropriate tunnel set as the destination interface.
All reports (Application Control, Web Filter, etc.) can be viewed and filtered per tunnel by adding a Destination Interface condition where the value equals the tunnel ID.
WireGuard VPN
The WireGuard VPN service provides virtual private networking via Wireguard VPN, an open-source lightweight VPN application and protocol designed to be fast, secure, and easy to configure.
Settings
This section reviews the different settings and configuration options available for WireGuard VPN.
Status
The Status tab shows the status of the WireGuard VPN service:
- Local Service Information
This section displays information about the local WireGuard service, such as the public key, endpoint address and port, peer address, and the list of local networks.
- Enabled Tunnels
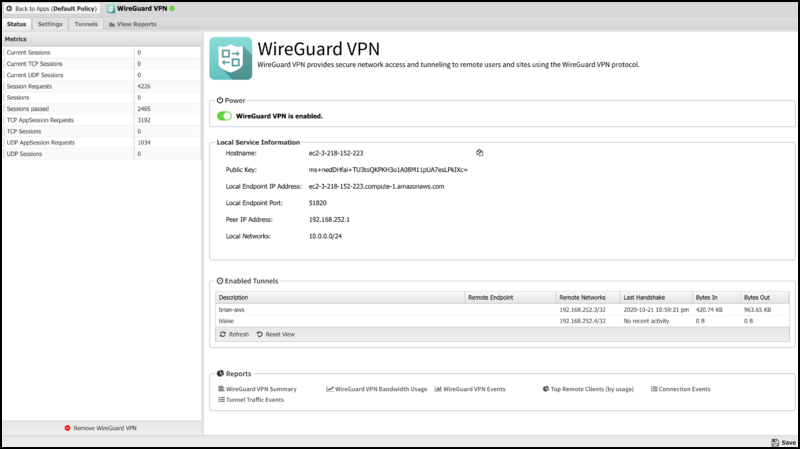
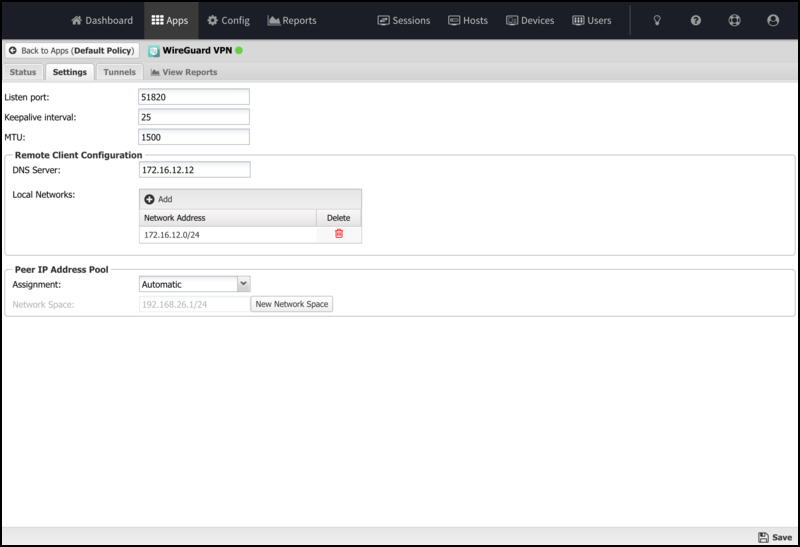
Table 3. Settings Listen port Sets the port where the WireGuard server will listen for inbound tunnel connections from peers. Keepalive interval Sets the passive keepalive interval, which ensures that sessions stay active and allows both peers to determine if a connection has failed or been disconnected passively. MTU Sets the MTU size for WireGuard tunnels.
Remote Client Configuration
These fields are used when generating the Remote Client configuration.
| Field | Description |
|---|---|
| DNS Server | The IP address of the local DNS server will be added to the client configuration. It is initially populated using the first defined DHCP DNS Server Override address is used it found. If not, the IP address of your first non-WAN interface is used. |
| Networks | These are networks added to the client's allowed IP list. It is initially populated with all known local networks discovered from non-WAN interfaces (and their aliases) and static routes. |
| Peer IP Address Pool | |
| Assignment | They were used to select the method for address pool assignment. It can be set automatically to allow the system to select an unused network space or be self-assigned to configure a user-entered network space. |
| Network Space | Shows the automatically assigned networks space or allows editing the self-assigned network space. |
| New Network Space | Click when using Automatic Assignment to select a new random network space. |
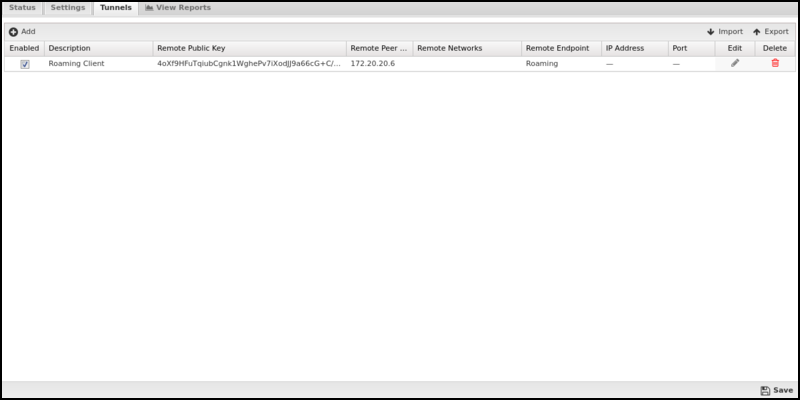
Tunnels
The Tunnels tab is where you create and manage WireGuard VPN tunnels. Each tunnel in the table can view the client configuration or edit the tunnel.
- Remote Client
- Clicking this icon will display a window showing the recommended client configuration in both Quick Reference (QR) Code, which many WireGuard mobile apps can scan with the device's camera, and import a text file suitable for copying and pasting into the remote client.
- Tunnel Editor
- When you add a tunnel or edit and existing tunnel, the tunnel editor screen will appear with the following configurable settings:
Note: You can copy the configuration from a remote NG Firewall peer and paste it into any configurable field. The screen automatically populates all of the relevant fields from the remote side. This simplifies the configuration of tunnels and is recommended to avoid misconfiguration.
Name Description Enabled This checkbox allows you to set a tunnel to enabled or disabled. Description This field should contain a short name or description. Remote Public Key This field is for the public key of the tunnel peer. Remote Endpoint Type This field controls the endpoint type for the peer. - Select Roaming if the remote endpoint is a mobile device using the WireGuard app or if the remote network is used for client access only and does not host any resources.
- Select Static for a traditional site-to-site tunnel configuration where each network hosts resources that must be accessible through the virtual private network.
Remote Endpoint IP Address Sets the IP address for a static endpoint. Remote Endpoint Port Sets the port for a static endpoint. Remote Peer IP Address This field sets the IP address that will be used by the remote peer. Remote Networks This field configures the list of remote networks that should be routed across this WireGuard tunnel. Networks should be entered per line in CIDR (192.168.123.0/24) format. Monitor Ping IP Address The IP address of a host on the remote network to ping for verifying that the tunnel is connected. Leave blank to disable. Monitor Ping Interval The time in seconds between attempts to ping the configured ping monitor address. Monitor Alert on Tunnel Up/Down When enabled, CONNECT and DISCONNECT alerts will be generated when the configured ping monitor transitions from reachable to unreachable and unreachable to reachable. Monitor Alert on Ping Unreachable When enabled, UNREACHABLE alerts will be generated for each monitor ping that fails when the target is unreachable. Local Service Information This section includes information from the Status tab useful when copying/pasting configurations between peers.
WireGuard VPN Client
The WireGuard Virtual Private Network client app is available for download on various mobile devices and desktop operating systems, including iOS, macOS, Android, Windows, and Linux. The download links for each supported OS are available from the WireGuard Website.
For a step-by-step setup guide, refer to the KB article Setting up WireGuard VPN on mobile devices and desktops.
Related Topics
WireGuard VPN Reports
The Reports tab provides a view of all reports and events for all connections handled by WireGuard VPN.
Reports
You can access the applications' reports via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries:
| Report Entry | Description |
|---|---|
| WireGuard VPN Summary | A summary of WireGuard VPN traffic. |
| WireGuard VPN Bandwidth Usage | The amount of traffic processed by the WireGuard service. |
| WireGuard VPN Events | Time chart of WireGuard VPN connection events. |
| Top Remove Clients (by usage) | The top WireGuard VPN peers by traffic usage. |
| Connection Events | Shows all WireGuard VPN tunnel monitoring events. |
| Tunnel Traffic Events | Shows all WireGuard tunnel traffic statistics events. |
