Reference Material
Event Definitions
All event data is stored in the Mail messages in a relational database. As Arista and applications process traffic, they create Event objects that add and modify content in the database. Each event has it's class/object with certain fields that modify the database in a certain way.
The list below shows the classes used in the event logging and the attributes of each event object. These can add alerts in Reports or other event handling within Arista.
SpamLogEvent
These events are created by Spam Blocker, and the Database Schema table is updated when an email is scanned.
| Attribute Name | Type | Description getAction |
|---|---|---|
| action | SpamMessageAction | The action getClass |
| class | Class | The class name getClientAddr |
| clientAddr | InetAddress | The client address getClientPort |
| clientPort | int | The client port getMessageId |
| messageId | Long | The message ID getPartitionTablePostfix getReceiver |
| receiver | String | The receiver getScore |
| score | float | The score getSender |
| sender | String | The sender getServerAddr |
| serverAddr | InetAddress | The server address getServerPort |
| serverPort | int | The server port getSmtpMessageEvent |
| smtpMessageEvent | SmtpMessageEvent | The parent SMTP message event isSpam |
| isSpam | boolean | True if spam, false otherwise getSubject |
| subject | String | The subject getTag getTestsString |
| testsString | String | The tests string from the spam engine getTimeStamp |
| timeStamp | Timestamp | The timestamp getVendorName |
| vendorName | String | The application name |
SpamSmtpTarpitEvent
These events are created by Spam Blocker and inserted into the Database Schema table when a session is tarpitted.
| Attribute Name | Type | Description getIPAddr |
|---|---|---|
| IPAddr | InetAddress | The IP address getClass |
| class | Class | The class name getHostname |
| hostname | String | The host name getPartitionTablePostfix getSessionEvent |
| sessionEvent | SessionEvent | The session event getSessionId |
| sessionId | Long | The session ID getTag getTimeStamp |
| timeStamp | Timestamp | The time stamp getVendorName |
| vendorName | String | The application name |
PrioritizeEvent
The Bandwidth ControlDatabase Schema creates these events and updates the table when a session is prioritized.
| Attribute Name | Type | Description getClass |
|---|---|---|
| class | Class | The class name getPartitionTablePostfix getPriority |
| priority | int | The priority getRuleId |
| ruleId | int | The rule ID getSessionEvent |
| sessionEvent | SessionEvent | The session event getTag getTimeStamp |
| timeStamp | Timestamp | The timestamp |
VirusFtpEvent
Virus Blocker creates these events and updates the Database Schema table when Virus Blocker scans an FTP transfer.
| Attribute Name | Type | Description getAppName |
|---|---|---|
| appName | String | The name of the application getClass |
| class | Class | The class name getClean |
| clean | boolean | True if clean, false otherwise getPartitionTablePostfix getSessionEvent |
| sessionEvent | SessionEvent | The session event getTag getTimeStamp |
| timeStamp | Timestamp | The timestamp getUri |
| uri | String | The URI getVirusName |
| virusName | String | The virus name, if not clean |
VirusHttpEvent
These events are created by Virus Blocker and update the Database Schema table when Virus Blocker scans an HTTP transfer.
| Attribute Name | Type | Description getAppName |
|---|---|---|
| appName | String | The name of the application getClass |
| class | Class | The class name getClean |
| clean | boolean | True if clean, false otherwise getPartitionTablePostfix getRequestLine |
| requestLine | RequestLine | The request line getSessionEvent |
| sessionEvent | SessionEvent | The session event getTag getTimeStamp |
| timeStamp | Timestamp | The timestamp getVirusName |
| virusName | String | The virus name, if not clean |
VirusSmtpEvent
Virus Blocker creates these events and updates the Database Schema table when Virus Blocker scans an email.
| Attribute Name | Type | Description getAction |
|---|---|---|
| action | String | The action getAppName |
| appName | String | The name of the application getClass |
| class | Class | The class name getClean |
| clean | boolean | True if clean, false otherwise getMessageId |
| messageId | Long | The message ID getPartitionTablePostfix getTag getTimeStamp |
| timeStamp | Timestamp | The timestamp getVirusName |
| virusName | String | The virus name, if not clean |
FirewallEvent
Firewall creates these events, and the Database Schema table is updated when a firewall rule matches a session.
| Attribute Name | Type | Description getBlocked |
|---|---|---|
| blocked | boolean | True if blocked, false otherwise getClass |
| class | Class | The class name getFlagged |
| flagged | boolean | True if flagged, false otherwise getPartitionTablePostfix getRuleId |
| ruleId | long | The rule ID getSessionId |
| sessionId | Long | The session ID getTag getTimeStamp |
| timeStamp | Timestamp | The timestamp |
Day of Week Matcher
A "Day of Week" matcher syntax describes days of the week.
A Day of Week Matcher can be any of the following syntax:
| Name | Example | Description |
|---|---|---|
| Any Matcher | "any" | matches all days of the week |
| Single Day (English name) | "tuesday" | matches Tuesday only |
| Single Day (Digit 1-7) | "1" | matches Sunday only |
| List of Time of Day Matchers | "monday,2,wednesday" | matches Monday, Tuesday, and Wednesday |
Group Matcher
Group Matcher syntax describes an user or set of users. This can be used, for example, in Policy Manager or Bandwidth Control rules to match against certain traffic.
Group Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Matcher | [any] | matches all groups |
| None Matcher | [none] | matches no groups |
| Groupname | mygroup | matches the "mygroup" group |
| Glob Matcher | m*p | matches the "mygroup" group |
| List of Group Matchers | mygroup1,mygroup2 | matches "mygroup1" and "mygroup2" |
Glob Matcher
A Glob is a common way to match strings of characters against rules. An Arista glob is similar to the syntax commonly used on Microsoft OSs to match filenames (example: "rm *.exe").
A glob matcher has two special characters: "*" means 0 or more of any characters (excluding return charater) and "?" means exactly 1 of any character (excluding return character).Globs are often used in rules like URL rules and filename rules to match various strings. The left and rights side are implicitly anchored. If you wish to match if a string contains the match you will need to use "*foo*".
| Example | String | Description |
|---|---|---|
| String | XYZ | matches "XYZ" but NOT "xYZ" and NOT "XYZZ" |
| String with * | X*Z | matches "XZ" and "XYZ" and "XYYZ" and "XyyyabcZ" but NOT "xYZ" and NOT "XYZA" |
| String with * | X*Z* | matches "XZ" and "XYZ" and "XYYZ" and "XyyyabcZ" and "XYZA" but NOT "xYZ" |
| String with ? | X?Z | matches "XYZ" and "XyZ" but NOT match "XZ" or "XYYZ" |
| List of Globs | X,Z | matches "X" and "Z" but NOT match "Y" or "X,Z" |
- replace "." with "\." to escape the special meaning of "." in regular expressions.
- replace "?" with "." to match any character.
- replace "*" with ".*" to match zero or more characters.
Note:
- "*" matches all values except null/unset.
- "" matches null and nothing else.
- All glob matching is case insensitive for domains but case sensitive for all other matches.
Int Matcher
Int Matcher syntax describes a integer or set of integers.
This can be used, for example, in firewall or Policy manager rules to match against certain traffic destination ports.
Port Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any | any | matches all |
| Single | 80 | matches that single integer |
| Greater Than | >1234 | matches all values greater than 1234 |
| Less Than | <1234 | matches all values less than 1234 |
| Range | 1024-65535 | matches all values within the range (inclusive) |
| List of Int Matchers | 80,443,8080-8088 | matches all 80, 443, and 8080 through 8088 |
IP Matcher
IP Matcher syntax is a that describes an IP address or set of IP addresses. This can be used, for example, in Firewall or Policy Manager rules to match against certain traffic.
IP Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Matcher | any | matches all addresses |
| Single IP | 1.2.3.4 | matches the single IP address |
| Range of IPs | 1.2.3.4 - 1.2.3.100 | matches all the IPs in the range |
| CIDR range | 192.168.1.0/24 | matches all the IPs in that subnet |
| List of IP Matchers | 1.2.3.4, 1.2.3.5, 1.2.3.10, 1.2.3.15 | matches all the IPs in the list and in that range |
User Matcher
User Matcher syntax describes an user or set of users.
This can be used, for example, in Policy Manager or Application Control rules to match against certain traffic.
User Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Authenticated User | [authenticated] | matches all identified or authenticated users (excluding null) |
| Unauthenticated User | [unauthenticated] | matches all unidentified or unauthenticated users (including null) |
| Username | myuser | matches the "myuser" user |
| Glob Matcher | m*r | matches the "myuser" user |
| List of User Matchers | myuser1,myuser2 | matches "myuser1" and "myuser2" |
URL Matcher
The URL Matcher Syntax describes all or part of a website.
| Example | Matches | Does not Match |
|---|---|---|
| example.com | http://example.com/, http://www.example.com/, http://example.com/foo | http://example.net |
| example.com/bar | http://example.com/bar/test.html, http://www.example.com/bar | http://example.com/foo |
| *porn* | http://pornsite.com/ | http://foobar.com |
| example???.com/ | http://example123.com | http://example1.com |
| example.com/foo | http://example.com/foo, http://abc.example.com/foobar | http://example.com/ |
URL Matchers use globs which are describe more in depth in the Glob Matcher.
- The left side of the rule is anchored with the regular expression "^([a-zA-Z_0-9-]*\.)*". "foo.com" will match only "foo.com" and "abc.foo.com" but not "afoo.com".
- The right side of the rule is anchored with the regular expression ".*$". "foo.com" will match "foo.com/test.html" because it is actually "foo.com.*$". "foo.com/bar" is "foo.com/bar.*$" which will match "foo.com/bar/baz" and "foo.com/bar2". Also "foo" becomes "foo.*" which will match "foobar.com" and "foo.com".
- "http://" and "https://" are stripped from the rule.
- URIs are case-sensitive, but domains are not. The URL Matcher is case sensitive, but domains are converted to lowercase before evaluation because they should not be case sensitive. Any part of the matcher that should match against the domain should be lower case in the rule.
- "www." is automatically stripped from the rule. This is to prevent the frequent misconfiguration of users adding a block rule for something like "www.pornsite.com" which blocks "www.pornsite.com" but not just "pornsite.com." If you truly desire to only match www.pornsite.com and not pornsite.com then use "*www.pornsite.com" because the "*" will match zero or more characters.
- Similarly "*." is stripped from the rule for the same reason as above. If you truly want all sub-domains but not the main domain matched, you can accomplish this by doing "*?.foo.com".
Port Forward Troubleshooting Guide
- Read the What is "Destined Local?".
- Verify that the destination host on the inside is using the Untangle as its default gateway. If not, the reply packets won't find their way back to Arista.
- Verify that the destination service is reachable from the inside on the IP and port specified in your port forward rule.
- Test your (TCP) port forward using 'telnet.' In windows you can run and then you can type telnet 1.2.3.4 123 where 1.2.3.4 is your external IP and 123 is the port your port forward rule matches. If it connects and hangs then the port forward is working. If it fails to connect then your port forward is not working.
- Test your rule from the outside. Port forwarding back inside the network has extra complications. First, verify that it works from the outside.
- Verify there is a session shown in .
- Verify that Arista can connect to the final destination. Use the Connection Test in Troubleshooting' or open the console on Arista and type 'telnet 192.168.1.10 123' where 192.168.1.10 is the internal server you are forwarding to, and 123 is the port. If it connects then Arista can reach the server. If it fails to connect Arista can't reach the server and the port forward will probably not function until this part is working.
- For testing, turn off the Firewall and Captive Portal applications if you have them installed. Port forwarded sessions will not connect if they are blocked by an application. If you have many policies, verify which policy is processing the session and make sure you disable the correct apps.
- Simplify your port forward rule. Remove extra qualifiers and make it contain as few as possible. For example specify just what port to forward and "Destined Local" and then which server to forward it to. If that works then add the extra qualifiers back one at a time testing each time.
- If you are port forwarding port 443 (HTTPS), try moving Untangle administration to another port so port 443 is available to be forwarded.
- Remove any Source Address and Source Interface qualifiers - 99% of the time these are misused.
- For advanced users, use tcpdump or the Packet Test in troubleshooting to debug and watch the packets. To test with tcpdump run these commands: tcpdump -i eth0 -n "port 123" and tcpdump -i eth1 -n "port 123" - assuming eth0 is your outside interface and eth1 is your inside interface.
- Still not working? Post a screenshot of your port forward rule to the forums along with the results from the above tests and ask for help.
Port Forwarding FAQs
- Can I specify multiple ports/IPs in one rule?
- My port forward isn't working. Why?
- I setup a port forward for HTTPS (port 443) and it is not working. Why?
- I setup a port forward to my FTP server and it is working but transfers fail. Why?
- Can I port forward traffic destined to a specific hostname like 'mywebserver.com' to a specific server?
- Does Untangle support 1:1 (One to One) NAT?
- What is "Destined Local?"
Can I specify multiple ports/IPs in one rule?
Absolutely. You can use comma-separated values or hyphen-separated ranges. In the case of IPs you can even use CIDR notation to cover a network space. Keep in mind that NGFW's Debian base limits rules to a maximum of 15 unique values per rule, and that hyphen-separated values count as two values.
My port forward isn't working. Why?
Follow the Port Forward Troubleshooting Guide to see if you can discover the issue.
I setup a port forward for HTTPS (port 443) and it is not working. Why?
Arista and many of the applications use port 443. In order to forward port 443 you need to move Arista off of port 443 to a different port. This can be done in .
I setup a port forward to my FTP server and it is working but transfers fail. Why?
- Configure your server to use a range of ports for a transfer, passive ports (i.e., 10000-20000) and configure Arista to forward all of these ports to the FTP server.
- Use 1:1 NAT
Can I port forward traffic destined to a specific hostname like 'mywebserver.com' to a specific server?
No. Packets are destined to IPs not hostnames. When a new packet of a new session arrives from 1.2.3.4 port 1234 to 5.6.7.8 port 5678, the port forward rules must decide if and where to forward that session based on the information present in that packet. This decision can only be made using the information known at this time. If the session is forwarded and its an HTTP or HTTPS session and later it successfully connects, the client may request "mywebserver.com/index.html". At this point in theory the hostname is known, however the port forwards must decide where to forward the session long before the hostname is known. Port forwards rules can not see into the future and know which hostname the client may request at the time the client is trying to initiate the session.
However, This can be accomplished for HTTP and HTTPS traffic using | apache as a reverse proxy. This mechanism will accept all HTTP requests and forward/proxy based on the information in the request and proxy all responses from the final server.
Does Untangle support 1:1 (One to One) NAT?
Yes, Read more about how to setup 1:1 NAT.
What is "Destined Local?"
Destined Local is a flag for port forward rules. It matches on traffic destined to the local Arista machine and one of its IPs. This flag is usually used when you want to redirect a port on the Arista Server (and all of its IPs) to another server.
Database Schema
- Database Tables
- Configuration backup events
- HTTP events
- Intrusion prevention events
- SMPT tarpit events
- IPsec user events
- IPsec VPN events
- IPsec tunnel stats
- HTTP query events
- Admin logins
- Sessions
- Session minutes
- Quotas
- Host table updates
- Device table updates
- User table updates
- Alerts
- Settings changes
- Web cache stats
- Server events
- Interface stat events
- Mail messages
- Mail addresses
- FTP events
- Tunnel VPN events
- Tunnel VPN stats
- WAN failover test events
- WAN failover action events
- Directory connector login events
- Captive portal user events
- OpenVPN stats
- OpenVPN events
Database Tables
Configuration Backup Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| success | Success | boolean | The result of the backup (true if the backup succeeded, false otherwise) |
| description | Text detail of the event | text | Text detail of the event |
| destination | Destination | text | The location of the backup |
| event_id | Event ID | bigint | The unique event ID |
HTTP Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| request_id | Request ID | bigint | The HTTP request ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| session_id | Session ID | bigint | The session |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| client_country | Client Country | text | The client Country |
| client_latitude | Client Latitude | real | The client Latitude |
| client_longitude | Client Longitude | real | The client Longitude |
| server_country | Server Country | text | The server Country |
| server_latitude | Server Latitude | real | The server Latitude |
| server_longitude | Server Longitude | real | The server Longitude |
| policy_id | Policy ID | smallint | The policy |
| username | Username | text | The username associated with this session |
| hostname | Hostname | text | The hostname of the local address |
| method | Method | character(1) | The HTTP method |
| uri | URI | text | The HTTP URI |
| host | Host | text | The HTTP host |
| domain | Domain | text | The HTTP domain (shortened host) |
| referer | Referer | text | The Referer URL |
| c2s_content_length | Client-to-server Content Length | bigint | The client-to-server content length |
| s2c_content_length | Server-to-client Content Length | bigint | The server-to-client content length |
| s2c_content_type | Server-to-client Content Type | text | The server-to-client content type |
| s2c_content_filename | Server-to-client Content Disposition Filename | text | The server-to-client content disposition filename |
| ad_blocker_cookie_ident | Ad Blocker Cookie | text | This name of cookie blocked by Ad Blocker |
| ad_blocker_action | Ad Blocker Action | character(1) | This action of Ad Blocker on this request |
| web_filter_reason | Reason for action (Web Filter) | character(1) | This reason Web Filter blocked/flagged this request |
| web_filter_category_id | Web Category (Web Filter) | smallint | This numeric category according to Web Filter |
| web_filter_rule_id | Web Rule (Web Filter) | smallint | This numeric rule according to Web Filter |
| web_filter_blocked | Blocked (Web Filter) | boolean | If Web Filter blocked this request |
| web_filter_flagged | Flagged (Web Filter) | boolean | If Web Filter flagged this request |
| virus_blocker_lite_clean | Virus Blocker Lite Clean | boolean | The cleanliness of the file according to Virus Blocker Lite |
| virus_blocker_lite_name | Virus Blocker Lite Name | text | The name of the malware according to Virus Blocker Lite |
| virus_blocker_clean | Virus Blocker Clean | boolean | The cleanliness of the file according to Virus Blocker |
| virus_blocker_name | Virus Blocker Name | text | The name of the malware according to Virus Blocker |
| threat_prevention_blocked | Threat Prevention Blocked | boolean | If Threat Prevention blocked this request |
| threat_prevention_flagged | Threat Prevention Flagged | boolean | If Threat Prevention flagged this request |
| threat_prevention_rule_id | Threat Prevention Rule Id | integer | This numeric rule according to Threat Prevention |
| threat_prevention_reputation | Threat Prevention Reputation | smallint | This numeric threat reputation |
| threat_prevention_categories | Threat Prevention Categories | integer | This bitmask of threat categories |
Intrusion Prevention Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| sig_id | Signature ID | bigint | This ID of the rule |
| gen_id | Grouping ID | bigint | The grouping ID for the rule, The gen_id + sig_id specify the rule's unique identifier |
| class_id | Classtype ID | bigint | The numeric ID for the classtype |
| source_addr | Source Address | inet | The source IP address of the packet |
| source_port | Source Port | integer | The source port of the packet (if applicable) |
| dest_addr | Destination Address | inet | The destination IP address of the packet |
| dest_port | Destination Port | integer | The destination port of the packet (if applicable) |
| protocol | Protocol | integer | The protocol of the packet |
| blocked | Blocked | boolean | If the packet was blocked/dropped |
| category | Category | text | The application specific grouping for the signature |
| classtype | Classtype | text | The generalized threat signature grouping (unrelated to gen_id) |
| msg | Message | text | The "title" or "description" of the signature |
| rid | Rule ID | text | The rule id |
| rule_id | Rule ID | text | The rule id |
SMPT Tarpit Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| ipaddr | Client Address | inet | The client IP address |
| hostname | Hostname | text | The hostname of the local address |
| policy_id | Policy ID | bigint | The policy |
| vendor_name | Vendor Name | character varying(255) | The "vendor name" of the app that logged the event |
| event_id | Event ID | bigint | The unique event ID |
IPsec User Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| event_id | Event ID | bigint | The unique event ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| connect_stamp | Connect Time | timestamp without time zone | The time the connection started |
| goodbye_stamp | End Time | timestamp without time zone | The time the connection ended |
| client_address | Client Address | text | The remote IP address of the client |
| client_protocol | Client Protocol | text | The protocol the client used to connect |
| client_username | Client Username | text | The username of the client |
| net_process | Net Process | text | The PID of the PPP process for L2TP connections or the connection ID for Xauth connections |
| net_interface | Net Interface | text | The PPP interface for L2TP connections or the client interface for Xauth connections |
| elapsed_time | Elapsed Time | text | The total time the client was connected |
| rx_bytes | Bytes Received | bigint | The number of bytes received from the client in this connection |
| tx_bytes | Bytes Sent | bigint | The number of bytes sent to the client in this connection |
IPsec VPN Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| event_id | Event ID | bigint | The unique event ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| local_address | Local Address | text | The local address of the tunnel |
| remote_address | Remote Address | text | The remote address of the tunnel |
| tunnel_description | Tunnel Description | text | The description of the tunnel |
| event_type | Event Type | text | The type of the event (CONNECT,DISCONNECT) |
IPsec Tunnel Stats
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| tunnel_name | Tunnel Name | text | The name of the IPsec tunnel |
| in_bytes | In Bytes | bigint | The number of bytes received during this time frame |
| out_bytes | Out Bytes | bigint | The number of bytes transmitted during this time frame |
| event_id | Event ID | bigint | The unique event ID |
HTTP Query Events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| event_id | Event ID | bigint | The unique event ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| session_id | Session ID | bigint | The session |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| policy_id | Policy ID | bigint | The policy |
| username | Username | text | The username associated with this session |
| hostname | Hostname | text | The hostname of the local address |
| request_id | Request ID | bigint | The HTTP request ID |
| method | Method | character(1) | The HTTP method |
| uri | URI | text | The HTTP URI |
| term | Search Term | text | The search term |
| host | Host | text | The HTTP host |
| c2s_content_length | Client-to-server Content Length | bigint | The client-to-server content length |
| s2c_content_length | Server-to-client Content Length | bigint | The server-to-client content length |
| s2c_content_type | Server-to-client Content Type | text | The server-to-client content type |
| blocked | Blocked | boolean | If Web Filter blocked this search term |
| flagged | Flagged | boolean | If Web Filter flagged this search term |
Admin Logins
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| login | Login | text | The login name |
| local | Local | boolean | True if it is a login attempt through a local process |
| client_addr | Client Address | inet | The client IP address |
| succeeded | Succeeded | boolean | True if the login succeeded, false otherwise |
| reason | Reason | character(1) | The reason for the login (if applicable) |
Sessions
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| session_id | Session ID | bigint | The session |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| end_time | End Time | timestamp without time zone | The time the session ended |
| bypassed | Bypassed | boolean | True if the session was bypassed, false otherwise |
| entitled | Entitled | boolean | True if the session is entitled to premium functionality |
| protocol | Protocol | smallint | The IP protocol of session |
| icmp_type | ICMP Type | smallint | The ICMP type of session if ICMP |
| hostname | Hostname | text | The hostname of the local address |
| username | Username | text | The username associated with this session |
| policy_id | Policy ID | smallint | The policy |
| policy_rule_id | Policy Rule ID | smallint | The ID of the matching policy rule (0 means none) |
| local_addr | Local Address | inet | The IP address of the local participant |
| remote_addr | Remote Address | inet | The IP address of the remote participant |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| client_country | Client Country | text | The client Country |
| client_latitude | Client Latitude | real | The client Latitude |
| client_longitude | Client Longitude | real | The client Longitude |
| server_country | Server Country | text | The server Country |
| server_latitude | Server Latitude | real | The server Latitude |
| server_longitude | Server Longitude | real | The server Longitude |
| c2p_bytes | From-Client Bytes | bigint | The number of bytes the client sent to Arista (client-to-pipeline) |
| p2c_bytes | To-Client Bytes | bigint | The number of bytesArista sent to client (pipeline-to-client) |
| s2p_bytes | From-Server Bytes | bigint | The number of bytes the server sent to Arista (client-to-pipeline) |
| p2s_bytes | To-Server Bytes | bigint | The number of bytes Arista sent to server (pipeline-to-client) |
| filter_prefix | Filter Block | text | The network filter that blocked the connection (filter,shield,invalid) |
| firewall_blocked | Firewall Blocked | boolean | True if Firewall blocked the session, false otherwise |
| firewall_flagged | Firewall Flagged | boolean | True if Firewall flagged the session, false otherwise |
| firewall_rule_index | Firewall Rule ID | integer | The matching rule in Firewall (if any) |
| threat_prevention_blocked | Threat Prevention Blocked | boolean | If Threat Prevention blocked |
| threat_prevention_flagged | Threat Prevention Flagged | boolean | If Threat Prevention flagged |
| threat_prevention_reason | Threat Prevention Reason | character(1) | Threat Prevention reason |
| threat_prevention_rule_id | Threat Prevention Rule Id | integer | Numeric rule id of Threat Prevention |
| threat_prevention_client_reputation | Threat Prevention Client Reputation | smallint | Numeric client reputation of Threat Prevention |
| threat_prevention_client_categories | Threat Prevention Client Categories | integer | Bitmask client categories of Threat Prevention |
| threat_prevention_server_reputation | Threat Prevention Server Reputation | smallint | Numeric server reputation of Threat Prevention |
| threat_prevention_server_categories | Threat Prevention Server Categories | integer | Bitmask server categories of Threat Prevention |
| application_control_lite_protocol | Application Control Lite Protocol | text | The application protocol according to Application Control Lite |
| application_control_lite_blocked | Application Control Lite Blocked | boolean | True if Application Control Lite blocked the session |
| captive_portal_blocked | Captive Portal Blocked | boolean | True if Captive Portal blocked the session |
| captive_portal_rule_index | Captive Portal Rule ID | integer | The matching rule in Captive Portal (if any) |
| application_control_application | Application Control Application | text | The application according to Application Control |
| application_control_protochain | Application Control Protochain | text | The protochain according to Application Control |
| application_control_category | Application Control Category | text | The category according to Application Control |
| application_control_blocked | Application Control Blocked | boolean | True if Application Control blocked the session |
| application_control_flagged | Application Control Flagged | boolean | True if Application Control flagged the session |
| application_control_confidence | Application Control Confidence | integer | True if Application Control confidence of this session's identification |
| application_control_ruleid | Application Control Rule ID | integer | The matching rule in Application Control (if any) |
| application_control_detail | Application Control Detail | text | The text detail from the Application Control engine |
| bandwidth_control_priority | Bandwidth Control Priority | integer | The priority given to this session |
| bandwidth_control_rule | Bandwidth Control Rule ID | integer | The matching rule in Bandwidth Control rule (if any) |
| ssl_inspector_ruleid | SSL Inspector Rule ID | integer | The matching rule in SSL Inspector rule (if any) |
| ssl_inspector_status | SSL Inspector Status | text | The status/action of the SSL session (INSPECTED, IGNORED, BLOCKED, UNTRUSTED, ABANDONED) |
| ssl_inspector_detail | SSL Inspector Detail | text | Additional text detail about the SSL connection (SNI, IP Address) |
| tags | Tags | text | The tags on this session |
Session Minutes
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| session_id | Session ID | bigint | The session |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| c2s_bytes | From-Client Bytes | bigint | The number of bytes the client sent |
| s2c_bytes | From-Server Bytes | bigint | The number of bytes the server sent |
| start_time | Start Time | timestamp without time zone | The start time of the session |
| end_time | End Time | timestamp without time zone | The time the session ended |
| bypassed | Bypassed | boolean | True if the session was bypassed, false otherwise |
| entitled | Entitled | boolean | True if the session is entitled to premium functionality |
| protocol | Protocol | smallint | The IP protocol of session |
| icmp_type | ICMP Type | smallint | The ICMP type of session if ICMP |
| hostname | Hostname | text | The hostname of the local address |
| username | Username | text | The username associated with this session |
| policy_id | Policy ID | smallint | The policy |
| policy_rule_id | Policy Rule ID | smallint | The ID of the matching policy rule (0 means none) |
| local_addr | Local Address | inet | The IP address of the local participant |
| remote_addr | Remote Address | inet | The IP address of the remote participant |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| client_country | Client Country | text | The client Country |
| client_latitude | Client Latitude | real | The client Latitude |
| client_longitude | Client Longitude | real | The client Longitude |
| server_country | Server Country | text | The server Country |
| server_latitude | Server Latitude | real | The server Latitude |
| server_longitude | Server Longitude | real | The server Longitude |
| filter_prefix | Filter Block | text | The network filter that blocked the connection (filter,shield,invalid) |
| firewall_blocked | Firewall Blocked | boolean | True if Firewall blocked the session, false otherwise |
| firewall_flagged | Firewall Flagged | boolean | True if Firewall flagged the session, false otherwise |
| firewall_rule_index | Firewall Rule ID | integer | The matching rule in Firewall (if any) |
| threat_prevention_blocked | Threat Prevention Blocked | boolean | If Threat Prevention blocked |
| threat_prevention_flagged | Threat Prevention Flagged | boolean | If Threat Prevention flagged |
| threat_prevention_reason | Threat Prevention Reason | character(1) | Threat Prevention reason |
| threat_prevention_rule_id | Threat Prevention Rule Id | integer | Numeric rule id of Threat Prevention |
| threat_prevention_client_reputation | Threat Prevention Client Reputation | smallint | Numeric client reputation of Threat Prevention |
| threat_prevention_client_categories | Threat Prevention Client Categories | integer | Bitmask client categories of Threat Prevention |
| threat_prevention_server_reputation | Threat Prevention Server Reputation | smallint | Numeric server reputation of Threat Prevention |
| threat_prevention_server_categories | Threat Prevention Server Categories | integer | Bitmask server categories of Threat Prevention |
| application_control_lite_protocol | Application Control Lite Protocol | text | The application protocol according to Application Control Lite |
| application_control_lite_blocked | Application Control Lite Blocked | boolean | True if Application Control Lite blocked the session |
| captive_portal_blocked | Captive Portal Blocked | boolean | True if Captive Portal blocked the session |
| captive_portal_rule_index | Captive Portal Rule ID | integer | The matching rule in Captive Portal (if any) |
| application_control_application | Application Control Application | text | The application according to Application Control |
| application_control_protochain | Application Control Protochain | text | The protochain according to Application Control |
| application_control_category | Application Control Category | text | The category according to Application Control |
| application_control_blocked | Application Control Blocked | boolean | True if Application Control blocked the session |
| application_control_flagged | Application Control Flagged | boolean | True if Application Control flagged the session |
| application_control_confidence | Application Control Confidence | integer | True if Application Control confidence of this session's identification |
| application_control_ruleid | Application Control Rule ID | integer | The matching rule in Application Control (if any) |
| application_control_detail | Application Control Detail | text | The text detail from the Application Control engine |
| bandwidth_control_priority | Bandwidth Control Priority | integer | The priority given to this session |
| bandwidth_control_rule | Bandwidth Control Rule ID | integer | The matching rule in Bandwidth Control rule (if any) |
| ssl_inspector_ruleid | SSL Inspector Rule ID | integer | The matching rule in SSL Inspector rule (if any) |
| ssl_inspector_status | SSL Inspector Status | text | The status/action of the SSL session (INSPECTED, IGNORED, BLOCKED, UNTRUSTED, ABANDONED) |
| ssl_inspector_detail | SSL Inspector Detail | text | Additional text detail about the SSL connection (SNI, IP Address) |
| tags | Tags | text | The tags on this session |
Quotas
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| entity | Entity | text | The IP entity given the quota (address/username) |
| action | Action | integer | The action (1=Quota Given, 2=Quota Exceeded) |
| size | Size | bigint | The size of the quota |
| reason | Reason | text | The reason for the action |
Host Table Updates
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| address | Address | inet | The IP address of the host |
| key | Key | text | The key being updated |
| value | Value | text | The new value for the key |
| old_value | Old Value | text | The old value for the key |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
Device Table Updates
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| mac_address | MAC Address | text | The MAC address of the device |
| key | Key | text | The key being updated |
| value | Value | text | The new value for the key |
| old_value | Old Value | text | The old value for the key |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
User Table Updates
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| username | Username | text | The username |
| key | Key | text | The key being updated |
| value | Value | text | The new value for the key |
| old_value | Old Value | text | The old value for the key |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
Alerts
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| description | Text detail of the event | text | The description from the alert rule. |
| summary_text | Summary Text | text | The summary text of the alert |
| json | JSON Text | text | The summary JSON representation of the event causing the alert |
Settings Changes
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| settings_file | Settings File | text | The name of the file changed |
| username | Username | text | The username logged in at the time of the change |
| hostname | Hostname | text | The remote hostname |
Web cache stats
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| hits | Hits | bigint | The number of cache hits during this time frame |
| misses | Misses | bigint | The number of cache misses during this time frame |
| bypasses | Bypasses | bigint | The number of cache user bypasses during this time frame |
| systems | System bypasses | bigint | The number of cache system bypasses during this time frame |
| hit_bytes | Hit Bytes | bigint | The number of bytes saved from cache hits |
| miss_bytes | Miss Bytes | bigint | The number of bytes not saved from cache misses |
| event_id | Event ID | bigint | The unique event ID |
Server events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| load_1 | CPU load (1-min) | numeric(6,2) | The 1-minute CPU load |
| load_5 | CPU load (5-min) | numeric(6,2) | The 5-minute CPU load |
| load_15 | CPU load (15-min) | numeric(6,2) | The 15-minute CPU load |
| cpu_user | CPU User Utilization | numeric(6,3) | The user CPU percent utilization |
| cpu_system | CPU System Utilization | numeric(6,3) | The system CPU percent utilization |
| mem_total | Total Memory | bigint | The total bytes of memory |
| mem_free | Memory Free | bigint | The number of free bytes of memory |
| disk_total | Disk Size | bigint | The total disk size in bytes |
| disk_free | Disk Free | bigint | The free disk space in bytes |
| swap_total | Swap Size | bigint | The total swap size in bytes |
| swap_free | Swap Free | bigint | The free disk swap in bytes |
| active_hosts | Active Hosts | integer | The number of active hosts |
Interface stat events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| interface_id | Interface ID | integer | The interface ID |
| rx_rate | Rx Rate | double precision | The RX rate (bytes/s) |
| rx_bytes | Bytes Received | bigint | The number of bytes received from the client in this connection |
| tx_rate | Tx Rate | double precision | The TX rate (bytes/s) |
| tx_bytes | Bytes Sent | bigint | The number of bytes sent to the client in this connection |
Mail messages
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| session_id | Session ID | bigint | The session |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| policy_id | Policy ID | bigint | The policy |
| username | Username | text | The username associated with this session |
| msg_id | Message ID | bigint | The message ID |
| subject | Subject | text | The email subject |
| hostname | Hostname | text | The hostname of the local address |
| event_id | Event ID | bigint | The unique event ID |
| sender | Sender | text | The address of the sender |
| receiver | Receiver | text | The address of the receiver |
| virus_blocker_lite_clean | Virus Blocker Lite Clean | boolean | The cleanliness of the file according to Virus Blocker Lite |
| virus_blocker_lite_name | Virus Blocker Lite Name | text | The name of the malware according to Virus Blocker Lite |
| virus_blocker_clean | Virus Blocker Clean | boolean | The cleanliness of the file according to Virus Blocker |
| virus_blocker_name | Virus Blocker Name | text | The name of the malware according to Virus Blocker |
| spam_blocker_lite_score | Spam Blocker Lite Score | real | The score of the email according to Spam Blocker Lite |
| spam_blocker_lite_is_spam | Spam Blocker Lite Spam | boolean | The spam status of the email according to Spam Blocker Lite |
| spam_blocker_lite_tests_string | Spam Blocker Lite Tests | text | The tess results for Spam Blocker Lite |
| spam_blocker_lite_action | Spam Blocker Lite Action | character(1) | The action taken by Spam Blocker Lite |
| spam_blocker_score | Spam Blocker Score | real | The score of the email according to Spam Blocker |
| spam_blocker_is_spam | Spam Blocker Spam | boolean | The spam status of the email according to Spam Blocker |
| spam_blocker_tests_string | Spam Blocker Tests | text | The tess results for Spam Blocker |
| spam_blocker_action | Spam Blocker Action | character(1) | The action taken by Spam Blocker |
| phish_blocker_score | Phish Blocker Score | real | The score of the email according to Phish Blocker |
| phish_blocker_is_spam | Phish Blocker Phish | boolean | The phish status of the email according to Phish Blocker |
| phish_blocker_tests_string | Phish Blocker Tests | text | The tess results for Phish Blocker |
| phish_blocker_action | Phish Blocker Action | character(1) | The action taken by Phish Blocker |
Mail addresses
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| session_id | Session ID | bigint | The session |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| c_client_port | Client-side Client Port | integer | The client-side client port |
| s_client_port | Server-side Client Port | integer | The server-side client port |
| c_server_port | Client-side Server Port | integer | The client-side server port |
| s_server_port | Server-side Server Port | integer | The server-side server port |
| policy_id | Policy ID | bigint | The policy |
| username | Username | text | The username associated with this session |
| msg_id | Message ID | bigint | The message ID |
| subject | Subject | text | The email subject |
| addr | Address | text | The address of this event |
| addr_name | Address Name | text | The name for this address |
| addr_kind | Address Kind | character(1) | The type for this address (F=From, T=To, C=CC, G=Envelope From, B=Envelope To, X=Unknown) |
| hostname | Hostname | text | The hostname of the local address |
| event_id | Event ID | bigint | The unique event ID |
| sender | Sender | text | The address of the sender |
| virus_blocker_lite_clean | Virus Blocker Lite Clean | boolean | The cleanliness of the file according to Virus Blocker Lite |
| virus_blocker_lite_name | Virus Blocker Lite Name | text | The name of the malware according to Virus Blocker Lite |
| virus_blocker_clean | Virus Blocker Clean | boolean | The cleanliness of the file according to Virus Blocker |
| virus_blocker_name | Virus Blocker Name | text | The name of the malware according to Virus Blocker |
| spam_blocker_lite_score | Spam Blocker Lite Score | real | The score of the email according to Spam Blocker Lite |
| spam_blocker_lite_is_spam | Spam Blocker Lite Spam | boolean | The spam status of the email according to Spam Blocker Lite |
| spam_blocker_lite_action | Spam Blocker Lite Action | character(1) | The action taken by Spam Blocker Lite |
| spam_blocker_lite_tests_string | Spam Blocker Lite Tests | text | The tess results for Spam Blocker Lite |
| spam_blocker_score | Spam Blocker Score | real | The score of the email according to Spam Blocker |
| spam_blocker_is_spam | Spam Blocker Spam | boolean | The spam status of the email according to Spam Blocker |
| spam_blocker_action | Spam Blocker Action | character(1) | The action taken by Spam Blocker |
| spam_blocker_tests_string | Spam Blocker Tests | text | The tess results for Spam Blocker |
| phish_blocker_score | Phish Blocker Score | real | The score of the email according to Phish Blocker |
| phish_blocker_is_spam | Phish Blocker Phish | boolean | The phish status of the email according to Phish Blocker |
| phish_blocker_tests_string | Phish Blocker Tests | text | The tess results for Phish Blocker |
| phish_blocker_action | Phish Blocker Action | character(1) | The action taken by Phish Blocker |
FTP events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| event_id | Event ID | bigint | The unique event ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| session_id | Session ID | bigint | The session |
| client_intf | Client Interface | smallint | The client interface |
| server_intf | Server Interface | smallint | The server interface |
| c_client_addr | Client-side Client Address | inet | The client-side client IP address |
| s_client_addr | Server-side Client Address | inet | The server-side client IP address |
| c_server_addr | Client-side Server Address | inet | The client-side server IP address |
| s_server_addr | Server-side Server Address | inet | The server-side server IP address |
| policy_id | Policy ID | bigint | The policy |
| username | Username | text | The username associated with this session |
| hostname | Hostname | text | The hostname of the local address |
| request_id | Request ID | bigint | The FTP request ID |
| method | Method | character(1) | The FTP method |
| uri | URI | text | The FTP URI |
| virus_blocker_lite_clean | Virus Blocker Lite Clean | boolean | The cleanliness of the file according to Virus Blocker Lite |
| virus_blocker_lite_name | Virus Blocker Lite Name | text | The name of the malware according to Virus Blocker Lite |
| virus_blocker_clean | Virus Blocker Clean | boolean | The cleanliness of the file according to Virus Blocker |
| virus_blocker_name | Virus Blocker Name | text | The name of the malware according to Virus Blocker |
Tunnel VPN events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| event_id | Event ID | bigint | The unique event ID |
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| tunnel_name | Tunnel Name | text | The name the tunnel |
| server_address | Server IP Address | text | The address of the remote server |
| local_address | Local Address | text | The local address assigned the client |
| event_type | Event Type | text | The type of the event (CONNECT,DISCONNECT) |
Tunnel VPN stats
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| tunnel_name | Tunnel Name | text | The name of the Tunnel VPN tunnel |
| in_bytes | In Bytes | bigint | The number of bytes received during this time frame |
| out_bytes | Out Bytes | bigint | The number of bytes transmitted during this time frame |
| event_id | Event ID | bigint | The unique event ID |
WAN failover test events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| interface_id | Interface ID | integer | This interface ID |
| name | Interface Name | text | This name of the interface |
| description | Text detail of the event | text | The description from the test rule |
| success | Success | boolean | The result of the test (true if the test succeeded, false otherwise) |
| event_id | Event ID | bigint | The unique event ID |
WAN failover action events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| interface_id | Interface ID | integer | This interface ID |
| action | Action | text | This action (CONNECTED,DISCONNECTED) |
| os_name | Interface O/S Name | text | This O/S name of the interface |
| name | Interface Name | text | This name of the interface |
| event_id | Event ID | bigint | The unique event ID |
Directory connector login events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| login_name | Login Name | text | The login name |
| domain | Domain | text | The AD domain |
| type | Type | text | The type of event (I=Login,U=Update,O=Logout) |
| client_addr | Client Address | inet | The client IP address |
| login_type | Login Type | text | The login type |
Captive portal user events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| policy_id | Policy ID | bigint | The policy |
| event_id | Event ID | bigint | The unique event ID |
| login_name | Login Name | text | The login username |
| event_info | Event Type | text | The type of event (LOGIN, FAILED, TIMEOUT, INACTIVE, USER_LOGOUT, ADMIN_LOGOUT) |
| auth_type | Authorization Type | text | The authorization type for this event |
| client_addr | Client Address | text | The remote IP address of the client |
OpenVPN stats
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| start_time | Start Time | timestamp without time zone | The time the OpenVPN session started |
| end_time | End Time | timestamp without time zone | The time the OpenVPN session ended |
| rx_bytes | Bytes Received | bigint | The total bytes received from the client during this session |
| tx_bytes | Bytes Sent | bigint | The total bytes sent to the client during this session |
| remote_address | Remote Address | inet | The remote IP address of the client |
| pool_address | Pool Address | inet | The pool IP address of the client |
| remote_port | Remote Port | integer | The remote port of the client |
| client_name | Client Name | text | The name of the client |
| event_id | Event ID | bigint | The unique event ID |
OpenVPN events
| Column Name | Human Name | Type | Description |
|---|---|---|---|
| time_stamp | Timestamp | timestamp without time zone | The time of the event |
| remote_address | Remote Address | inet | The remote IP address of the client |
| pool_address | Pool Address | inet | The pool IP address of the client |
| client_name | Client Name | text | The name of the client |
| type | Type | text | The type of the event (CONNECT,DISCONNECT) |
Rules
Rules are used frequently in Arista and many other firewalls. Rules are very powerful, but can sometimes be difficult to configure.
This documentation discusses how rules work and gives some basic examples and some common mistakes to avoid. Many applications use rules like NG Firewall Rule Syntax, Captive Portal, Bandwidth Control, etc. All of these rules essentially share the same logic.
Basics
Rules are configured by the user to categorize and act upon traffic. For example,NG Firewall Rule Syntax uses rules to determine whether to block or pass traffic.Bandwidth Control uses rules to determine how to prioritize a session.
Rules are evaluated in order from top to bottom against sessions (not packets!). If a rule matches then the action from that rule is performed and no more rules are evaluated. If no matching rule is found the behavior is defined by the application, which is usually doing nothing.
This is similar to other firewalls. Arista rules are quick rules which means the first match is always used. Unlike some other firewalls, Arista evaluates against sessions, not packets. This means that the Source Address will be the initiator of the session and the Destination Address will be the server address the client is connecting to, and the same is true for Source Port and Destination Port.
- An enable checkbox
- A name/description
- A set of conditions
- An action or set of actions
Rule Anatomy
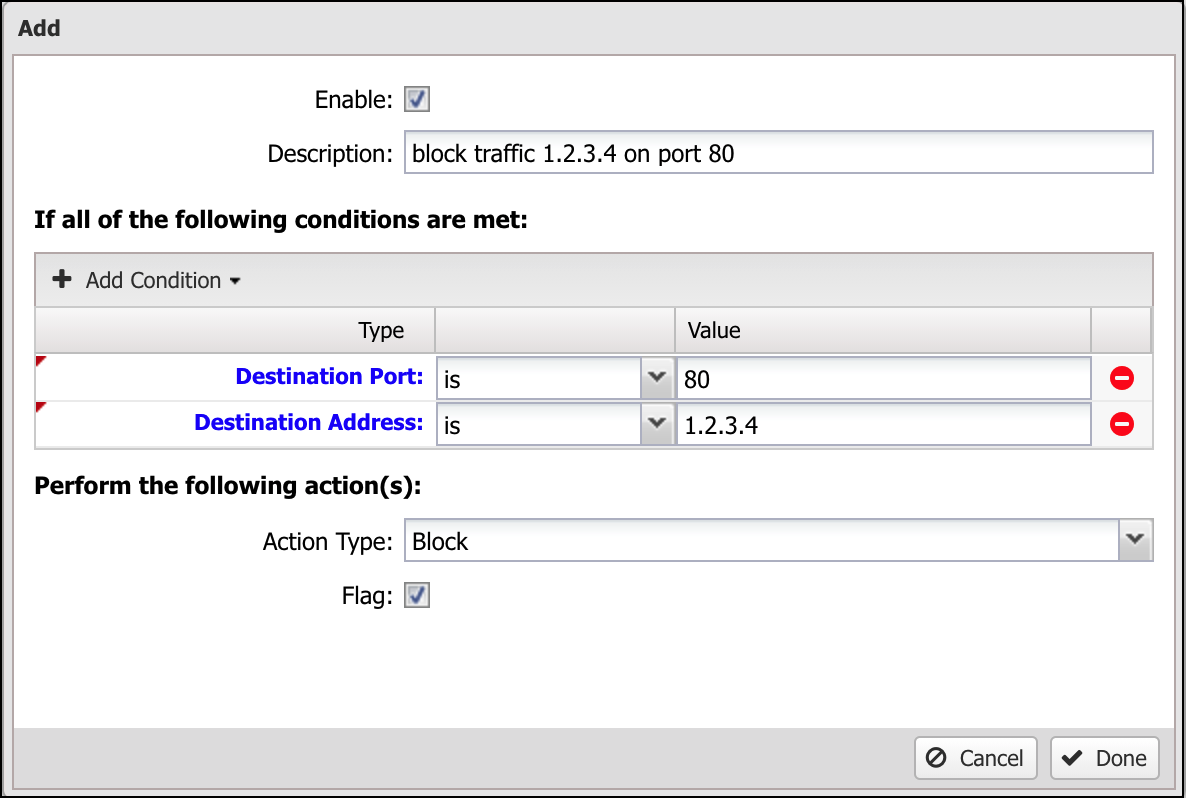
The enable checkbox determines if the rule is evaluated. If the enable checkbox is not checked, the rule is simply skipped.
The description is for the user to document what the rule does. It is highly suggested to give the rule a meaningful name. Trying to troubleshoot a set of rules all named "[no description]" can be extremely difficult.
The set of conditions is the description of the traffic that should match the rule. If all of the conditions are true for the given session then the rules matches. This is discussed in more details in the next section.
The action or set of actions configures what action is performed if the rule matches. This is dependent on the application. For example, in NG Firewall User Guide it determines whether to block or pass the session and additionally if it should be flagged.
Conditions
Conditions define which sessions will match the rule. If and only if all of the conditions match, the rule is considered a match. Conditions can also be inverted by selecting "is NOT" in the dropdown, effectively inverting when it matches. Destination Port "is NOT" "80" matches on all ports except port 80.
- Protocol is TCP
- Destination Address is 1.2.3.4 (The IP address of the server)
- Destination Port is 80
Finally, set the action to block and flag, and click Done and Apply. Since all conditions must be true this rule will block TCP traffic to 1.2.3.4 port 80 only and nothing else.
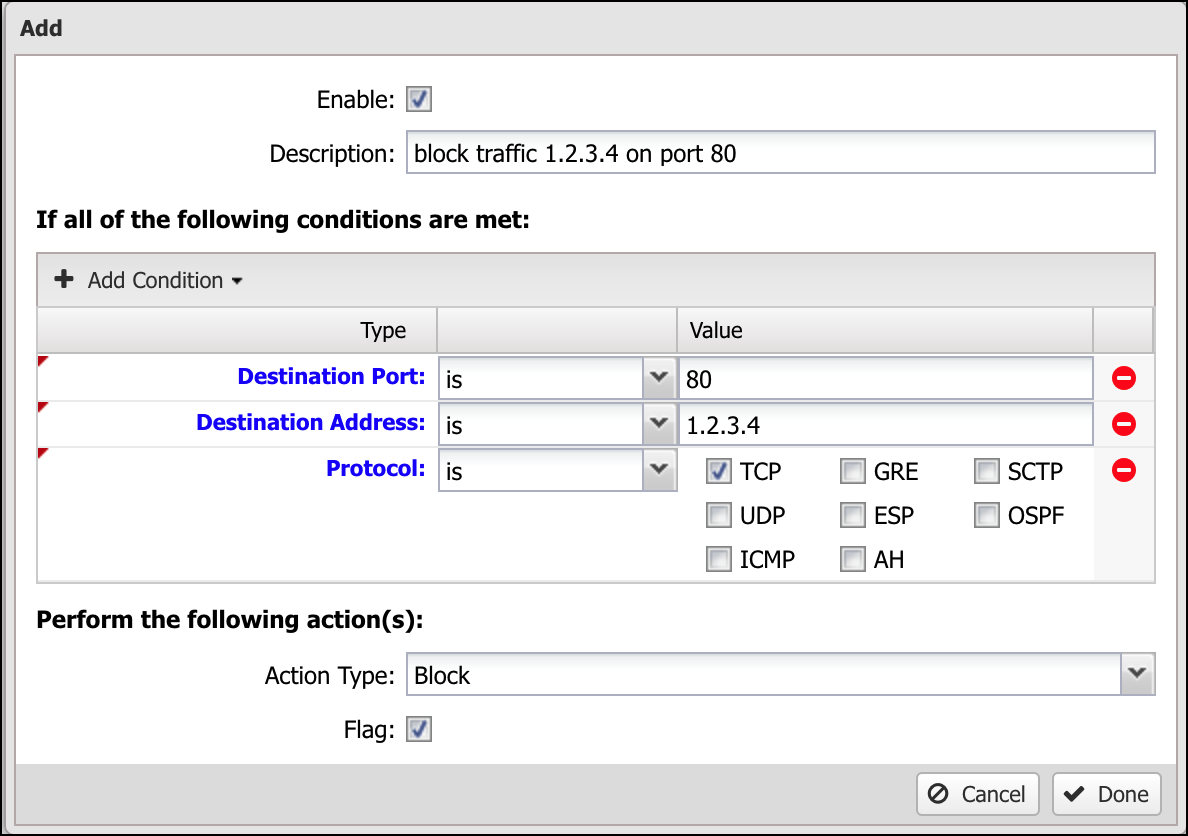
There are many conditions available to carefully define precise sets of traffic. The following table defines the list of conditions.
- Name - The Name of the condition.
- Syntax - The accepted Syntax of the condition. If editing through the UI, some conditions have custom editors to help you craft conditions, others are just a text field.
- Availability - The Availability is the availability of that matcher at various times. Some conditions, like Destination Address, are always known and can always be used to match. Other conditions, like Application Control: Application, are only known after the session is created and some data flows and Application Control is able to identify the application. These type conditions are 'deep session' conditions because they are not able to be evaluated at session creation time, only after some data flows. As such they are not available in rules that are evaluated at session creation time, like NG Firewall User Guide and Captive Portal.
- Reliability - The Reliability is a "reliability" of that condition. True means it is 100% reliable. False means it is 99% or less reliable. For example, some conditions, like Destination Port, are always known and thus matching on Destination Port is 100% reliable. Other conditions, like Client Hostname, only match if the hostname for the client hostname is known. Hostname is determined through many ways, including DNS and DHCP. If all of these methods fail then it is entirely possible that the hostname of a server is "foo" but Arista has not been able to determine this and as such a Client Hostname is "foo" condition will not match. This column is there purely as a warning that users in these cases must be aware of when conditions might deliver false negatives.
Table 1. Condition List Name Syntax Function Availability Reliability Destination Address IP Matcher Matches if value matches the Destination/Server Address of the session. (after NAT/port forwarding) all True Destination Port Int Matcher Matches if value matches the Destination/Server Port of the session. (after NAT/port forwarding) all True Destination Interface checkboxes Matches if value matches the Destination/Server Interface of the session. (after routing/port forwarding) all True Destined Local boolean Matches if the session is destined to one ofArista's IP addresses. all True Source Address IP Matcher Matches if value matches the Source/Client Address of the session. (before NAT/port forwarding) all True Source Port NG Firewall Rule Syntax Matches if value matches the Source/Client Port of the session. (before NAT/port forwarding) hidden True Source Interface checkboxes Matches if value matches the Source/Client Interface of the session. (before routing/port forwarding) all True Protocol checkboxes Matches if value matches the Protocol of the session. all True Tagged Glob Matcher Matches if session is tagged with matching tag all True Client Tagged Glob Matcher Matches if client of the session is tagged with matching tag all True Server Tagged Glob Matcher Matches if server of the session is tagged with matching tag all True Username User Matcher Matches if value matches the username associated with the Client IP in the Host table. all False Host Hostname Glob Matcher Matches if value matches the hostname associated with the Local Address in the Host table. all False Client Hostname Glob Matcher Matches if value matches the hostname associated with the Client IP in the Host table. all False Server Hostname Glob Matcher Matches if value matches the hostname associated with the Server IP in the Host table. all False Client MAC Address Glob Matcher Matches if value matches the MAC address associated with the Client IP in the ARP table. all False Server MAC Address Glob Matcher Matches if value matches the MAC address associated with the Server IP in the ARP table. all False Client MAC Vendor Glob Matcher Matches if value matches the device manufacturer. This is identified using the Client IP's MAC address in the ARP table and OUI Lookup. all False Server MAC Vendor Glob Matcher Matches if value matches the device manufacturer. This is identified using the Server IP's MAC address in the ARP table and OUI Lookup. all False Host has no Quota boolean Matches if the local address has no quota all True User has no Quota boolean Matches if the username has no quota all True Client has no Quota boolean Matches if the client has no quota hidden True Server has no Quota boolean Matches if the server has no quota hidden True Host has Exceeded Quota boolean Matches if the local address has exceeded their quota all True User has Exceeded Quota boolean Matches if the user has exceeded their quota all True Client has Exceeded Quota boolean Matches if the client has exceeded their quota hidden True Server has Exceeded Quota boolean Matches if the server has exceeded their quota hidden True Host Quota Attainment Int Matcher Matches the local address quota used to quota size ratio (">1" means over quota, ">.5" means over 50% used, etc) all True User Quota Attainment Int Matcher Matches the username quota used to quota size ratio (">1" means over quota, ">.5" means over 50% used, etc) all True Client Quota Attainment Int Matcher Matches the client quota used to quota size ratio (">1" means over quota, ">.5" means over 50% used, etc) hidden True Server Quota Attainment Int Matcher Matches the server quota used to quota size ratio (">1" means over quota, ">.5" means over 50% used. etc) hidden True HTTP: Hostname Glob Matcher Matches if the value matches the hostname specified in the HTTP session deep sessions False HTTP: Referrer Glob Matcher Matches if the value matches the referrer string specified in the HTTP header deep sessions False HTTP: URI Glob Matcher Matches if the value matches the latest URI specified in the HTTP session deep sessions False HTTP: URL URL Matcher Matches if the value matches the latest URL (hostname+URI) specified in the HTTP session deep sessions False HTTP: Content Type Glob Matcher Matches the content-type of the latest content in the HTTP session deep sessions False HTTP: Content Length Int Matcher Matches if Int Matcher matches the content length specified in the latest HTTP response deep sessions False HTTP: Request Method Glob Matcher Matches if the value matches the HTTP request method of the requested URL. Standard request methods include GET, POST, HEAD, OPTIONS, PUT, DELETE, TRACE, and CONNECT. deep sessions False HTTP: Request File Path Glob Matcher Matches if the value matches the entire file path of the requested URL. This is everything including and after the first slash character following the host name or address. (e.g. /some/location/mypage.html) deep sessions False HTTP: Request File Name Glob Matcher Matches if the value matches the file name of the requested URL. This is everything after the final slash character of the request. (e.g. mypage.html) deep sessions False HTTP: Request File Extension Glob Matcher Matches if the value matches the file extension of the requested URL. This is everything after following the dot after the final slash character of the request. (e.g. html) deep sessions False HTTP: Response Content Type Glob Matcher Matches if the value matches the content or MIME type reported in the server response. deep sessions False HTTP: Response File Name Glob Matcher Matches if the value matches the file name returned in the server response. deep sessions False HTTP: Response File Extension Glob Matcher Matches if the value matches the file extension returned in the server response. This is everything after (but not including) the final dot of the file name. deep sessions False HTTP: Client User Agent Glob Matcher Matches if the value matches the User Agent string for the client in the Host table all False Application Control: Application Glob Matcher Matches if the value matches the Application determined by Application Control deep sessions False Application Control: Category Glob Matcher Matches if the value matches the Category of the Application determined by Application Control deep sessions False Application Control: Protochain Glob Matcher Matches if the value matches the Protochain determined by Application Control deep sessions False Application Control: Detail Glob Matcher Matches if the value matches the Detail of the Application determined by Application Control deep sessions False Application Control: Confidence Int Matcher Matches if Int Matcher matches the confidence rating determined by Application Control deep sessions False Application Control: Productivity Int Matcher Matches if Int Matcher matches the productivity rating determined by Application Control deep sessions False Application Control: Risk Int Matcher Matches if Int Matcher matches the risk rating determined by Application Control deep sessions False Application Control Lite: Signature Glob Matcher Matches if the value matches the Signature determined by Application Control Lite deep sessions False Application Control Lite: Category Glob Matcher Matches if the value matches the Category of the Signature determined by Application Control Lite deep sessions False Application Control Lite: Description Glob Matcher Matches if the value matches the Description of the Signature determined by Application Control Lite deep sessions False Web Filter: Category Glob Matcher Matches if the value matches the Category determined by Web Filter deep sessions False Web Filter: Category Description Glob Matcher Matches if the value matches the Description of the Category determined by Web Filter deep sessions False Web Filter: Site is Flagged boolean Matches if the latest request in this session was flagged by Web Filter deep sessions False Directory Connector: User in Group Group Matcher Matches if the username associated with the client in the Host Table is in the specified group(s) all False SSL Inspector: SNI Host Name Glob Matcher Matches if the value matches the Server Name Indication (SNI) host name included by the client in the initial session request. deep sessions False SSL Inspector: Certificate Subject Glob Matcher Matches if the value matches the Subject DN in the SSL certificate received from the external server. all False SSL Inspector: Certificate Issuer Glob Matcher Matches if the value matches the Issuer DN in the SSL certificate received from the external server. all False Time of Day Time and Date Formatting Matches times of day. all True Day of Week Day of Week Matcher Matches days of the week. all True Remote Host Country Glob Matcher Matches if value matches the country associated with the remote IP. all False Client Country Glob Matcher Matches if value matches the country associated with the Client IP. all False Server Country Glob Matcher Matches if value matches the country associated with the Server IP. all False
Order
As discussed above, the order of rules is very important. Often users want to do very complex tasks that can be difficult or impossible with a single rule. In these cases, multiple rules is useful. For example, assume you want to use Firewall to block all traffic to a server (1.2.3.4) except port 80 traffic or from the admin IP (192.168.1.100) to RDP (port 3389).
Doing this in one rule would be difficult (actually impossible in this case), but it is quite easy using several rules: First, create a rule to just block all traffic to the server IP, 1.2.3.4. Above that rule create a rule that passes all traffic from the admin IP, 192.168.1.100, to the server IP where Destination Port == "3389", and another rule that passes all traffic to 1.2.3.4 with Destination Port == "80." This set of three rules does exactly what we describe above and effects no other traffic.
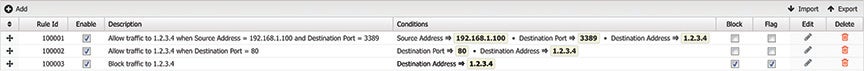
Common Mistakes
- Conditions must ALL match
In order for a rule to match, ALL conditions must match. In some cases you may want to add a rule that just passes all traffic to and from an IP. Users sometimes will create a pass rule with two conditions:
- Destination Address is "1.2.3.4"
- Source Address is "1.2.3.4"
This rule will never match anything because it will only match traffic where the destination address is 1.2.3.4 AND the source address is 1.2.3.4 (a session destined to itself). If you want to match when the destination address is 1.2.3.4 OR the source address is 1.2.3.4, then you must create two separate rules, one for the destination address and one for the source address.
- Rule Order
Occasionally, you will add a rule and not understand why it is not working as intended. Often we find that there was a rule above that was matching the session before the desired rule. For example, just adding a rule to the bottom often isn't sufficient, you must find the appropriate place in your ruleset to place the new rule.
To do so simply logically evaluate the rules in your head starting at the top to find the appropriate place for your rule. Also use the event log to run several tests to see how the session was handled in the event log and adjust your ruleset accordingly.
NG Firewall Rule Syntax
About NG Firewall Rule Syntax
Throughout the NG Firewall Server Administrative Interface, Administrators must enter information about their network and web locations. In some cases the values entered can be exact, and in others the text entered indicates a range of values.
The following describe common syntaxes to describe IPs, ports, strings, URLs, etc. The Policy Manager documentation describes which syntax is used for which fields.
IP Matcher
IP Matcher syntax is a that describes an IP address or set of IP addresses. This can be used, for example, in NG Firewall User Guide or Policy Manager rules to match against certain traffic.
IP Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Matcher | any | matches all addresses |
| Single IP | 1.2.3.4 | matches the single IP address |
| Range of IPs | 1.2.3.4-1.2.3.100 | matches all the IPs in the range |
| CIDR range | 192.168.1.0/24 | matches all the IPs in that subnet |
| List of IP Matchers | 1.2.3.4, 1.2.3.5, 1.2.3.10 - 1.2.3.15 | matches all the IPs in the list and in that range |
Port Matcher
Int Matcher syntax is a that describes a integer or set of integers. This can be used, for example, in NG Firewall User Guide or Policy Manager rules to match against certain traffic destination ports.
Port Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any | any | matches all |
| Single | 80 | matches that single integer |
| Greater Than | >1234 | matches all values greater than 1234 |
| Less Than | <1234 | matches all values less than 1234 |
| Range | 1024-65535 | matches all values within the range (inclusive) |
| List of Int Matchers | 80, 443, 8080-8088 | matches all 80, 443, and 8080 through 8088 |
URL Matcher
The URL Matcher Syntax describes all or part of a website.
| Example | Matches | Does not Match |
|---|---|---|
| example.com | http://example.com/, http://www.example.com/, http://example.com/foo | http://example.net |
| example.com/bar | http://example.com/bar/test.html, http://www.example.com/bar | http://example.com/foo |
| *porn* | http://pornsite.com/ | http://foobar.com |
| example???.com/ | http://example123.com | http://example1.com |
| example.com/foo | http://example.com/foo, http://abc.example.com/foobar | http://example.com/ |
URL Matchers use globs which are describe more in depth in the Glob Matcher.
- The left side of the rule is anchored with the regular expression "^([a-zA-Z_0-9-]*\.)*". "foo.com" will match only "foo.com" and "abc.foo.com" but not "afoo.com".
- The right side of the rule is anchored with the regular expression ".*$". "foo.com" will match "foo.com/test.html" because it is actually "foo.com.*$". "foo.com/bar" is "foo.com/bar.*$" which will match "foo.com/bar/baz" and "foo.com/bar2". Also "foo" becomes "foo.*" which will match "foobar.com" and "foo.com"
- "http://" and "https://" are stripped from the rule.
- URIs are case-sensitive, but domains are not. The URL Matcher is case sensitive, but domains are converted to lowercase before evaluation because they should not be case sensitive. Any part of the matcher that should match against the domain should be lower case in the rule.
- "www." is automatically stripped from the rule. This is to prevent the frequent misconfiguration of users adding a block rule for something like "www.pornsite.com" which blocks "www.pornsite.com" but not just "pornsite.com." If you truly desire to only match www.pornsite.com and not pornsite.com then use "*www.pornsite.com" because the "*" will match zero or more characters.
- Similarly "*." is stripped from the rule for the same reason as above. If you truly want all sub-domains but not the main domain matched, you can accomplish this by doing "*?.foo.com".
User Matcher
User Matcher syntax describes an user or set of users. This can be used, for example, in Policy Manager or About Bandwidth Control rules to match against certain traffic.
User Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Authenticated User | [authenticated] | matches all identified or authenticated users (excluding null) |
| Unauthenticated User | [unauthenticated] | matches all unidentified or unauthenticated users (including null) |
| Username | myuser | matches the "myuser" user |
| Glob Matcher | m*r | matches the "myuser" user |
| List of User Matchers | myuser1,myuser2 | matches "myuser1" and "myuser2" |
Group Matcher
Group Matcher syntax is a that describes an user or set of users. This can be used, for example, in Policy Manager or Bandwidth Control rules to match against certain traffic.
Group Matcher can be any of the following:
| Name | Example | Description |
|---|---|---|
| Any Matcher | [any] | matches all groups |
| None Matcher | [none] | matches no groups |
| Groupname | mygroup | matches the "mygroup" group |
| Glob Matcher | m*p | matches the "mygroup" group |
| List of Group Matchers | mygroup1,mygroup2 | matches "mygroup1" and "mygroup2" |
Glob Matcher
A Glob is a common way to match strings of characters against rules. An Arista glob is similar to the syntax commonly used on Microsoft OSs to match filenames (example: "rm *.exe").
A glob matcher has two special characters: "*" means 0 or more of any characters (excluding return character) and "?" means exactly 1 of any character (excluding return character).
| Example | String | Description |
|---|---|---|
| String | XYZ | matches "XYZ" but NOT "xYZ" and NOT "XYZZ" |
| String with * | X*Z | matches "XZ" and "XYZ" and "XYYZ" and "XyyyabcZ" but NOT "xYZ" and NOT "XYZA" |
| String with * | X*Z* | matches "XZ" and "XYZ" and "XYYZ" and "XyyyabcZ" and "XYZA" but NOT "xYZ" |
| String with ? | X?Z | matches "XYZ" and "XyZ" but NOT match "XZ" or "XYYZ" |
| List of Globs | X,Z | matches "X" and "Z" but NOT match "Y" or "X,Z" |
Globs are often used in rules like URL rules and filename rules to match various strings. The left and rights side are implicitly anchored. If you wish to match if a string contains the match you will need to use "*foo*".
- replace "." with "\." to escape the special meaning of "." in regular expressions.
- replace "?" with "." to match any character.
- replace "*" with ".*" to match zero or more characters.
- "*" matches all values except null/unset.
- "" matches null and nothing else.
- All glob matching is case insensitive for domains but case sensitive for all other matches.
Time of Day Matcher
Day of Week Matcher
A "Day of Week" matcher is a syntax used to describe days of the week.
A Day of Week Matcher can be any of the following syntax:
| Name | Example | Description |
|---|---|---|
| Any Matcher | "any" | matches all days of the week |
| Single Day (English name) | "tuesday" | matches Tuesday only |
| Single Day (Digit 1-7) | "1" | matches Sunday only |
| List of Time of Day Matchers | "monday, 2, wednesday" | matches Monday, Tuesday, and Wednesday |
Time and Date Formatting
| Format | Description | Example |
|---|---|---|
| d | Day of the month, 2 digits with leading zeros | 01 to 31 |
| D | A short textual representation of the day of the week | Mon to Sun |
| j | Day of the month without leading zeros | 1 to 31 |
| l | A full textual representation of the day of the week | Sunday to Saturday |
| N | ISO-8601 numeric representation of the day of the week | 1 (for Monday) through 7 (for Sunday) |
| S | English ordinal suffix for the day of the month, 2 characters. Works well with j | st, nd, rd or th |
| w | Numeric representation of the day of the week | 0 (for Sunday) to 6 (for Saturday) |
| z | The day of the year (starting from 0) | 0 to 364 (365 in leap years) |
| W | ISO-8601 week number of year, weeks starting on Monday | 01 to 53 |
| F | A full textual representation of a month, such as January or March | January to December |
| m | Numeric representation of a month, with leading zeros | 01 to 12 |
| M | A short textual representation of a month | Jan to Dec |
| n | Numeric representation of a month, without leading zeros | 1 to 12 |
| t | Number of days in the given month | 28 to 31 |
| L | Whether it's a leap year | 1 if it is a leap year, 0 otherwise. |
| o | ISO-8601 year number (identical to (Y), but if the ISO week number (W) belongs to the previous or next year, that year is used instead) | Examples: 1998 or 2004 |
| Y | A full numeric representation of a year, 4 digits | Examples: 1999 or 2003 |
| y | A two digit representation of a year | Examples: 99 or 03 |
| a | Lowercase Ante meridiem and Post meridiem | am or pm |
| A | Uppercase Ante meridiem and Post meridiem | AM or PM |
| g | 12-hour format of an hour without leading zeros | 1 to 12 |
| G | 24-hour format of an hour without leading zeros | 0 to 23 |
| h | 12-hour format of an hour with leading zeros | 01 to 12 |
| H | 24-hour format of an hour with leading zeros | 00 to 23 |
| i | Minutes, with leading zeros | 00 to 59 |
| s | Seconds, with leading zeros | 00 to 59 |
| u | Decimal fraction of a second | Examples:(minimum 1 digit, arbitrary number of digits allowed) 001 (i.e. 0.001s) or 100 (i.e. 0.100s) or 999 (i.e. 0.999s) or 999876543210 (i.e. 0.999876543210s) |
| O | Difference to Greenwich time (GMT) in hours and minutes | Example: +1030 |
| P | Difference to Greenwich time (GMT) with colon between hours and minutes | Example: -08:00 |
| T | Timezone abbreviation of the machine running the code | Examples: EST, MDT, PDT ... |
| Z | Timezone offset in seconds (negative if west of UTC, positive if east) | -43200 to 50400 |
| c | ISO 8601 date represented as the local time with an offset to UTC appended.
Note:
|
Examples:1991 or 1992-10 or 1993-09-20 or 1994-08-19T16:20+01:00 or 1995-07-18T17:21:28-02:00 or 1996-06-17T18:22:29.98765+03:00 or 1997-05-16T19:23:30,12345-0400 or 1998-04-15T20:24:31.2468Z or 1999-03-14T20:24:32Z or 2000-02-13T21:25:33 2001-01-12 22:26:34 |
| C | An ISO date string as implemented by the native Date object's Date to ISO String method. This outputs the numeric part with *UTC* hour and minute values, and indicates this by appending the `'Z'` timezone identifier. | 1962-06-17T09:21:34.125Z |
| U | Seconds since the Unix Epoch (January 1 1970 00:00:00 GMT) | 1193432466 or -2138434463 |
| MS | Microsoft AJAX serialized dates | \/Date(1238606590509)\/ (i.e. UTC milliseconds since epoch) or \/Date(1238606590509+0800)\/ |
| time | A javascript millisecond timestamp | 1350024476440 |
| timestamp | A UNIX timestamp (same as U) | 1350024866 |
