Appendix A: AP Server Communication Workflow
With the 18.0 release, the Access Point (AP) and CV-CUE Server (previously called Wireless Manager Server or WM Server) connectivity for on-premises and cloud deployments have been updated with additional security and improved security posture of AP-Server communication.
For cloud deployments, APs connect to the CV-CUE Server via a redirector proxy server hosted in Arista Cloud. Establishing connections via a proxy server ensures additional security, eliminates direct access to the CV-CUE Server, and uplifts the security posture of AP-Server communication.
In the new communication workflow, the CV-CUE Server will generate a random communication key for new customers, and only authenticated and authorized APs can connect to it. In such cases, Administrators must enable the onboarding window from the CV-CUE UI for APs to connect to the CV-CUE Server. The details are described later in this article.
Important! Before 18.0 release, Access Points deployed in the customer’s network communicated to Arista Redirector via port 443/TCP or port 3851/UDP. The Arista Redirector provided the Access Point with the URL of the CV-CUE Server, and the AP directly communicated with the Wireless Manager hosted in the cloud through port 3851/UDP.
From 18.0 release onwards, all APs must communicate with the CV-CUE Server through the Arista Redirector Proxy (which shares the same URL/domain name as the Arista Redirector) for better monitoring, scalability, and security. As part of this change, the range of IP addresses hosting the Arista Redirector has also been extended. Traffic from the Access Point must now be allowed to all the IP addresses or FQDN of the Arista Redirector on ports 443/TCP and 3851/UDP. Trusted Platform Module (TPM) APs will connect with the CV-CUE Server in Arista Cloud exclusively using 443/TCP instead of 3851/UDP.
Note the following scenarios and make the necessary changes to the firewall rules:
-
If you have allowed communication from the AP to the individual IP addresses of Arista Redirector and Arista Wireless Manager over port 443/TCP, you must modify the firewall rule also to allow communication from the Access Point to the new IP addresses listed later in this article (in addition to the existing IP addresses) on port 443/TCP.
-
If you have allowed communication from the AP to the FQDN of the Arista Redirector (redirector.online.spectraguard.net) over port 443/TCP, no action is required (as long as your firewall can automatically allow all the IP addresses that can resolve to the FQDN)
-
If you have allowed communication from the AP to all the individual IP addresses of Arista Redirector and Arista Wireless Manager only on port 3851/UDP, you must modify the firewall rule also to allow communication from the Access Point to the new IP addresses listed later in this article (in addition to the existing IP addresses) on ports 443/TCP and 3851/UDP.
-
If you have allowed communication from AP to the FQDN of Arista Cloud Redirector (redirector.online.spectraguard.net) only on port 3851/UDP, you must modify the firewall rule also to allow communication from Access Point to the FQDN of Arista Cloud Redirector (redirector.online.spectraguard.net) on port 443/TCP.
-
Clarification: Only the Inside-to-Outside traffic from Access Points to Arista Redirector (IP address / FQDN) on ports 443/TCP and 3851/UDP needs to be allowed.
-
Other services related to Arista Wi-Fi, such as CIP (cloud Integration Point) and image repository, will continue to operate on their current prescribed ports.
-
These changes will improve the security posture of Arista APs and Cloud Communication, and move towards using TLS-based encryption as the primary method for authentication and communication with the Cloud.
The following list provides the IP addresses/URLs of the Redirector that you must enable for the AP-Server communication workflow to work:
URL: redirector.online.spectraguard.net
New IP Addresses:
-
35.209.220.35
-
35.208.54.203
-
35.208.115.139
-
35.206.94.152
-
35.208.235.177
-
35.209.160.80
-
35.208.144.161
-
35.208.5.204
-
35.207.108.103
-
35.207.79.102
-
35.214.29.19
-
35.214.13.105
-
35.213.241.166
-
35.213.201.253
-
35.207.206.240
-
35.207.229.20
-
35.213.96.138
-
35.213.55.222
Existing IP Addresses:
-
52.199.251.150
-
13.113.247.134
-
35.154.33.182
-
15.206.10.168
-
3.106.40.11
-
52.64.207.242
-
52.58.63.144
-
52.29.194.192
-
52.56.61.130
-
3.11.192.175
-
52.200.63.237
-
34.194.204.153
-
52.203.51.183
-
3.228.242.60
-
52.8.155.239
-
13.52.28.201
Server Discovery by TPM Vs. Non-TPM AP
Arista has TPM (Trusted Platform Module) and non-TPM APs.
- TPM APs: C-200, C-230, C-230E, C-330, C-360, C-460, C-460E, W-318, O-235, O-235E
- Non-TPM APs: C-250, C-260, Wave 2 APs (1xx series of APs)
Depending on TPM or non-TPM APs, the process of server discovery differs.
Cloud Deployments
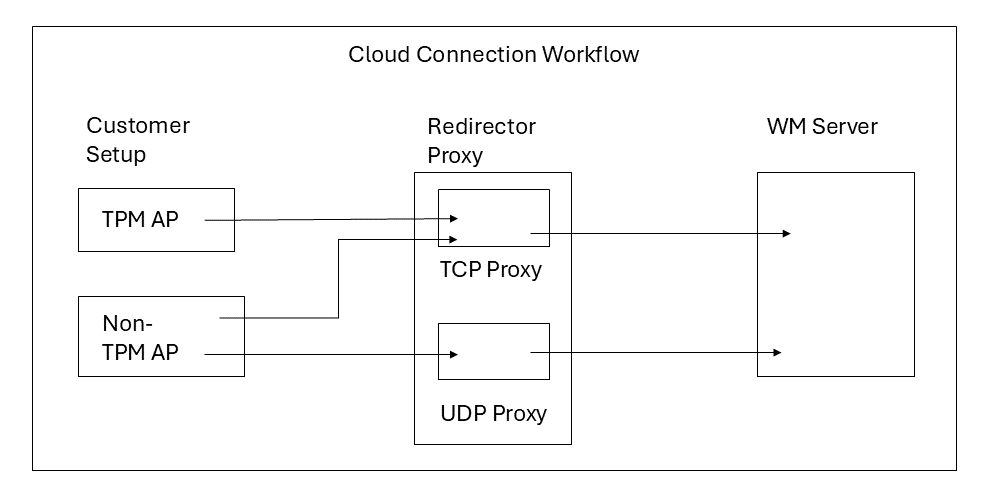
TPM AP-Server Communication Workflow:
All TPM APs are mandated to connect to the CV-CUE Server via a TCP Proxy.
AP certificate (pre-loaded) is mandatory for authenticating and onboarding TPM APs.
TPM APs must be on Version 11.0 or higher.
Non-TPM AP-Server Communication Workflow:
Non-TPM APs connect to the CV-CUE Server via a proxy server. They connect to the proxy using UDP 3851; if UDP is unreachable, they connect using TCP 443.
Administrators must enable the Non-TPM AP onboarding window from CloudVision CUE (CV-CUE) when the APs connect to the CV-CUE Server for the first time.
On-Premises Deployments
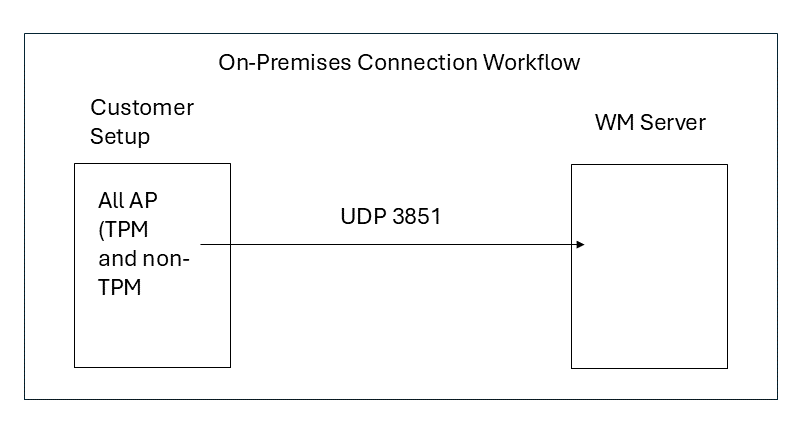
APs connect to the CV-CUE Server over UDP on port 3851.
Administrators must enable the onboarding window from the CV-CUE UI when the APs connect to the CV-CUE Server for the first time.
Ensure Seamless ZTP for APs
To ensure that all existing and new APs connect seamlessly and maintain Zero Touch Provisioning (ZTP), the CV-CUE Server maintains three communication keys.
Three AP-Server communication keys:
-
Communication Key: This is the current communication key for the AP and CV-CUE Server communication. The Administrator configures it from CV-CUE.
-
Default Communication Key: The default communication key is flashed on every AP during manufacturing.
-
Old Communication Key: The previous communication key that was used before the Administrator changed it to the current communication key.
Note that there is no option to restore the Default communication key.
AP Server Communication Scenarios
Consider these scenarios for AP-Server communication workflow when upgrading to the latest release.
Cloud Deployments
As a prerequisite for the Cloud-based deployment scenarios, ensure that you have made all the firewall changes mentioned in the Introduction section.
Scenario 1: Customers Upgrade the Version But Don’t Change the Communication Key
Customers have AP version 11.0 or higher, and Arista upgraded the CV-CUE Server to version 18.0. Customers do not change the AP-Server communication key after the upgrade. This upgrade is like any other upgrade, with no network disruptions.
However, we highly recommend that customers change the communication key after the upgrade.
Scenario 2: Customers Upgrade the Version and Change the Communication Key
Customers have AP version 11.0 or higher, and Arista upgraded the CV-CUE Server to version 18.0. After the upgrade, customers change the communication key.
All connected APs (TPM and non-TPM) can connect seamlessly after upgrading the CV-CUE Server to Version 18.0 and changing the communication key. The CV-CUE Server pushes the new communication key automatically to the connected APs. There will not be any disruption in the AP-Server communication. For APs that were not connected or inactive when the communication key was being pushed from the CV-CUE Server:
- TPM APs will be able to connect automatically with the old communication key and get the new communication key from the CV-CUE Server for future connections.
- For non-TPM APs, Administrators must enable the onboarding window from CV-CUE. Afterward, the non-TPM APs can connect to the CV-CUE Server seamlessly within the time specified in the onboarding window. Enabling the onboarding window from CV-CUE is a one-time activity for the non-TMP APs. After they are connected to the CV-CUE Server, the Server automatically pushes the new key to such APs.
Scenario 3: Customers Upgrade the Version and Change the Communication Key. Then they Purchase New Arista APs.
Customers have AP version 11.0 or higher, and Arista upgraded the CV-CUE Server to version 18.0. After the upgrade, customers change the communication key. Then, they purchase some more new Arista APs.
This scenario is the same as Scenario 2 for existing APs. For the newly purchased APs, TPM APs will connect seamlessly with the CV-CUE Server.
For non-TPM APs, Administrators must enable the onboarding window from CV-CUE. Afterward, the non-TPM APs can connect to the CV-CUE Server seamlessly within the time specified in the onboarding window. Enabling the onboarding window from CV-CUE is a one-time activity for the non-TMP APs. After they are connected to the CV-CUE Server, the Server automatically pushes the new key to such APs.
Scenario 4: New Customers Purchase Arista APs.
New customers associate with Arista and purchase APs.
TPM APs will connect seamlessly with the server. For non-TPM APs, Administrators must enable the onboarding window from CV-CUE. Afterward, the non-TPM APs can connect to the CV-CUE Server seamlessly within the time specified in the onboarding window. Enabling the onboarding window from CV-CUE is a one-time activity for the non-TMP APs. After they are connected to the CV-CUE Server, the server automatically pushes the new key to such APs.
On-Premises Deployments
Scenario 1: Customers Upgrade the Version But Don’t Change the Communication Key
Customers upgrade the CV-CUE Server to version 18.0 and do not change the AP-Server communication key after the upgrade. This upgrade is like any other upgrade, with no network disruptions.
However, we highly recommend that customers change the communication key after the upgrade.
Scenario 2: Customers Upgrade the Version and Change the Communication Key
Customers have AP version 11.0 or higher, and they upgraded the CV-CUE Server to version 18.0. After the upgrade, they change the communication key.
The CV-CUE Server pushes the new communication key automatically to the connected APs. There will not be any disruption in the AP-Server communication. For APs that were not connected or inactive when the communication key was being pushed from the CV-CUE Server, Administrators must enable the onboarding window from CV-CUE. Afterward, the APs can connect to the CV-CUE Server seamlessly within the time specified in the onboarding window. Enabling the onboarding window from CV-CUE is a one-time activity for the existing APs. After they are connected to the CV-CUE Server, the Server automatically pushes the new key to such APs.
Scenario 3: Customers Upgrade the Version and Change the Communication Key. Then they Purchase New Arista APs.
Customers have AP version 11.0 or higher, and they upgraded the server to version 18.0. After the upgrade, they change the communication key. Then, they purchase some more new Arista APs.
This scenario is the same as Scenario 2 for existing APs. For newly purchased APs, Administrators must again enable the onboarding window from CV-CUE so the APs can connect to the CV-CUE Server.
Scenario 4: New Customers Purchase Arista APs.
When new customers associate with Arista and purchase APs, Administrators must enable the onboarding window from CV-CUE. Afterward, the APs can connect to the CV-CUE Server seamlessly within the time specified in the onboarding window. Enabling the onboarding window from CV-CUE is a one-time activity for the APs. After they are connected to the CV-CUE Server, the Server automatically pushes the new key to such APs.
How Will Users Know if APs Fail to Connect Due to Incorrect Key
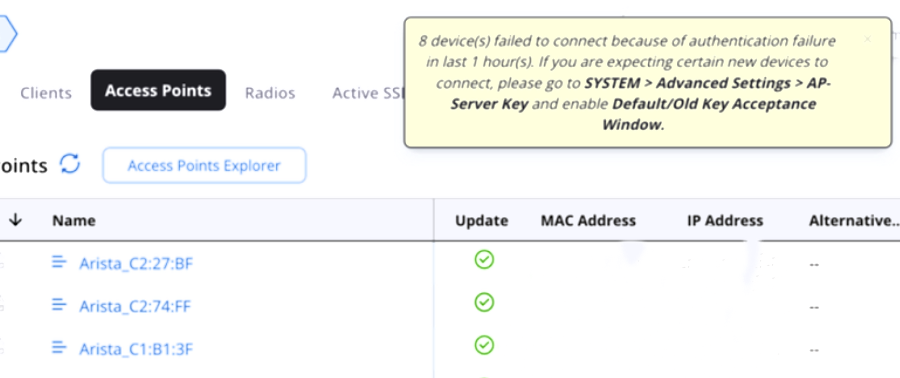
Change the Default AP-Server Communication Key
- Go to
- Select Change Communication Keyand change your default communication key.
- Save the settings.
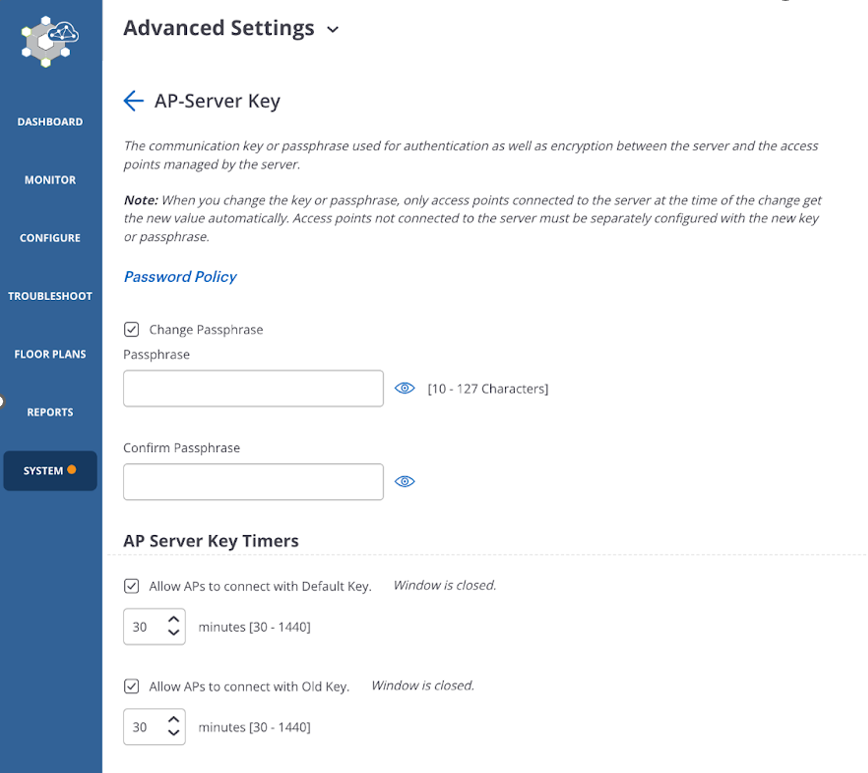
Enable the AP-Server Communication Key Timers for the Onboarding Window
AP-Server communication key timers give you control over which APs (having an old or default communication key) can connect to the CV-CUE Server and for how long the timer is available. The timer controls the duration of the onboarding window within which APs need to connect to the Server.
To enable the timers:
- Select SYSTEM > Advanced Settings > AP-Server Key.
- Enable the following checkboxes in AP-Server Key Timers and provide your time in
minutes.
- Default Communication Key: The default key is flashed on every AP during manufacturing.
- Old Communication Key: The previous communication key that was used before the Administrator changed it to the current communication key.
- Save the settings.
The APs can connect to the CV-CUE Server within the specified time using the default or old communication key.
