Configure Alerts
CV-CUE allows you to configure the behavior of each alert under You can define the severity level of an alert, select what means are used to notify administrators of an alert, and—in the case of System and WIPS alerts—decide whether or not an alert affects the security status of your network.
Like many other policies, the configuration of alerts is a location-based policy, i.e., an alert defined at a location is inherited by its child locations. You can customize the alert configuration at a child location to break the inheritance from the parent location. An alert is raised at the location of the device that triggers the alert.You can also Download Alerts as a ".tsv" file.
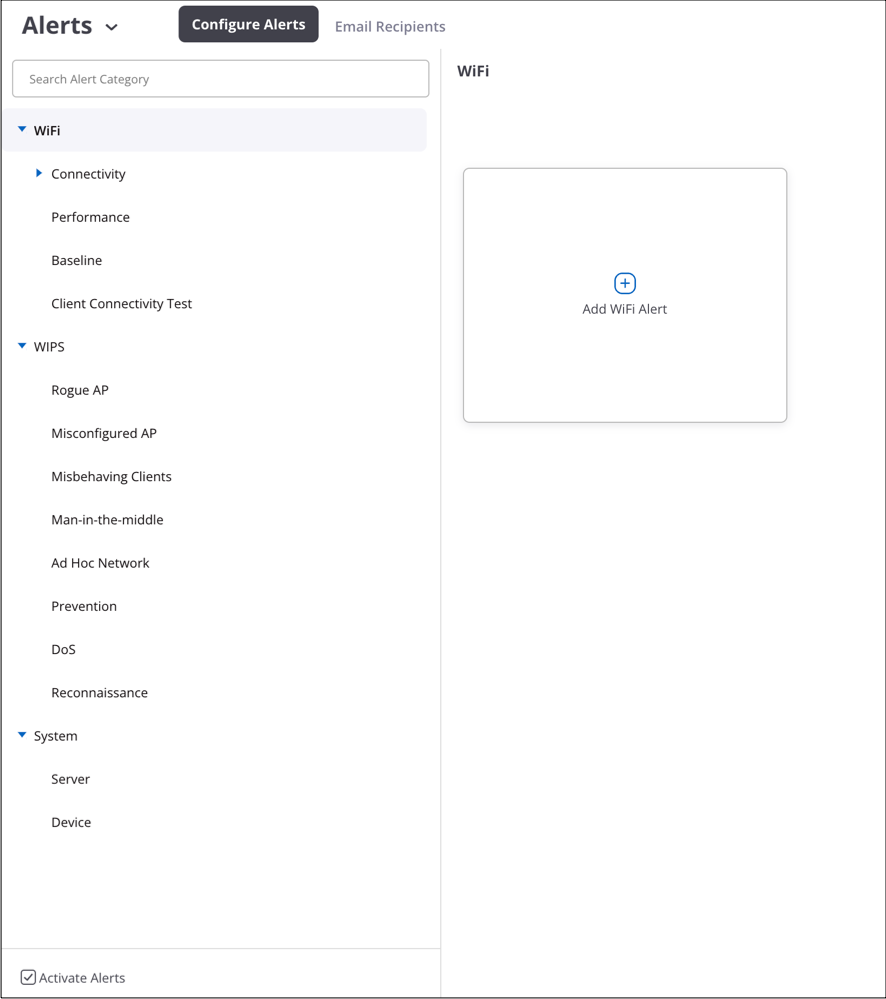
Configure Wi-Fi Alerts
You can define when Wi-Fi alerts occur and how a network administrator is notified. Certain alerts can only be enabled or disabled, e.g., an alert for a client connectivity test failure, while others additionally have configurable thresholds. By defining thresholds, an administrator can configure alerts for events that cross these thresholds and need attention. An alert is raised when the actual value exceeds the configured threshold, e.g., an alert based on the number of clients associated with an access point exceeding the configured threshold. You can also configure how alerts should be communicated: on the UI or sent via email, Syslog messages, or SNMP traps.
Let's discuss two examples of how Wi-Fi alerts can be configured.
Example 1: Poor Client Performance Alert
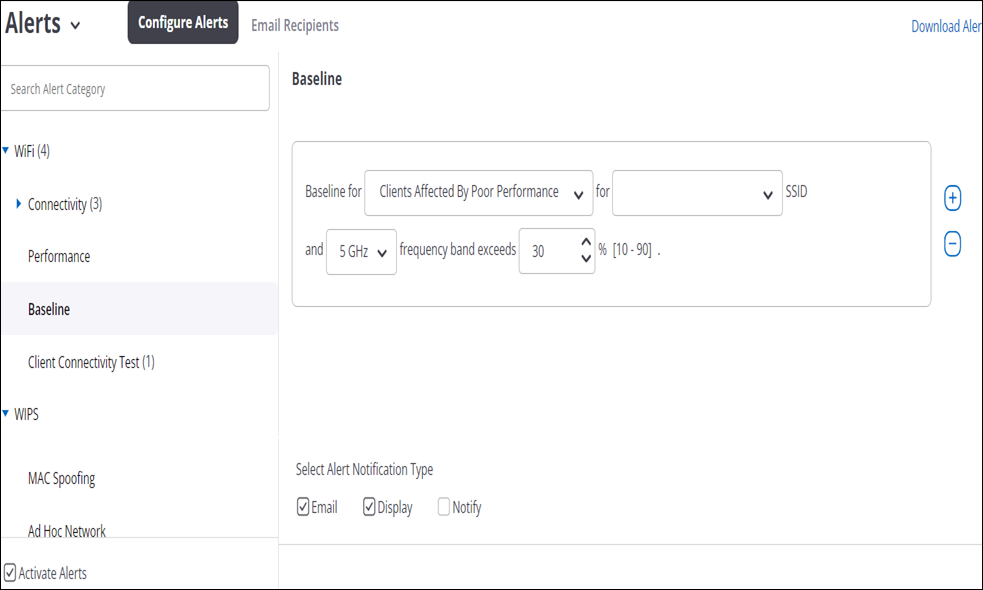
- Select Baseline alerts under Wi-Fi.
- Select "Clients Affected by Poor Performance" as the metric.
- Select "Any" SSID and the "5 GHz" band.
- Define the threshold in terms of the percentage value above which you want an alert to be raised.
- Select "Email" and "Display" to send an email to the administrator and show the alert on the UI.
Example 2: DHCP Latency Alert
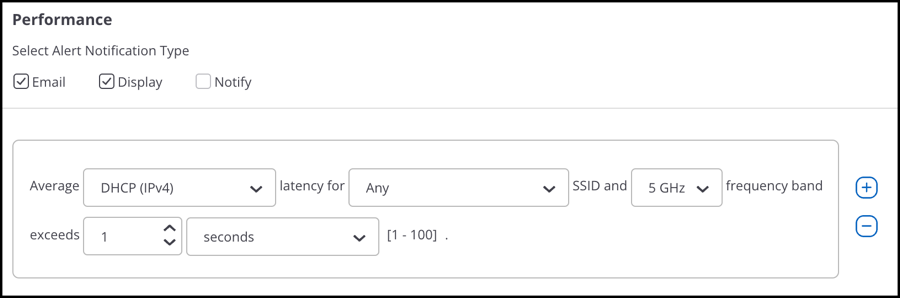
Suppose that you want CV-CUE to raise an alert if the DHCP latency for a particular SSID exceeds a threshold, and you want to notify a Syslog/SNMP server of this alert. As shown in the figure above, you can configure such an alert as follows:
- Select Performance alerts under Wi-Fi.
- Select "DHCP" as the component for which latency triggers the alert.
- Select the SSID and "Any" band.
- Define the latency threshold above which you want an alert to be raised.
- Select all the notification types for the alert.
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify |
|---|---|---|---|
| Connection Failure |
Connection Failure Alerts are triggered when clients experiencing connectivity issues exceed a certain number. You can configure an alert for the following connectivity issues:
To set a threshold for all connectivity issues, select Any from the drop-down menu. |
Investigate the reason behind respective connection failures from Client Event Logs. | Disabled | Disabled | Disabled |
| Associated Clients by Location or Access Point (AP) |
This alert is raised when the number of associations on AP exceeds the set threshold or the number of associations on location exceeds the set threshold. |
Increase the number of APs at the location | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify |
|---|---|---|---|
| Average Latency Exceeded | This alert is raised when the average latency for a particular SSID and frequency band exceeds the set threshold. | Check for network issues and take corrective actions according to the alert details. | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify |
|---|---|---|---|
| Baseline Threshold Exceeded | This alert is raised when the Wi-Fi baseline for an SSID and frequency band exceeds the set threshold. | Take corrective actions according to the alert details. | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify |
|---|---|---|---|
| Client Connectivity Test Fail | This alert is raised when a scheduled client connectivity test fails. | Investigate the result behind the client connectivity failed test. | Disabled | Disabled | Disabled |
Configure WIPS Alerts
WIPS alerts are related to Wi-Fi vulnerabilities and attacks that may pose a security threat to your network.
Let us look at an example WIPS alert configuration.
Example: Banned AP Active

If a banned AP becomes active, it could pose a serious threat to your network. As shown in the figure above, you can configure the "Banned AP active" alert as follows:
- Set the Severity of the alert to "High".
- Have this alert displayed on the UI under Monitor > Alerts > WIPS .
- Send an email to an administrator and notify an external entity such as a Syslog server about this alert.
- Have the alert affect the security status of your network.
WIPS Alert Types
| WIPS Alert Type | Description |
|---|---|
| Rogue AP | Alerts for any potentially rogue APs. Examples: Unauthorized AP connected to the enterprise wired network, Banned AP, Unauthorized AP on non-allowed channels. |
| Misconfigured APs | Alerts for any AP
behavior that deviates from the authorized Wi-Fi policy. Examples: Change in an authorized AP's SSID, No encryption on an authorized AP. |
| Misbehaving Clients | Alerts for any
client behavior that could compromise network security. Examples: Authorized client association with an external AP, Unauthorized client association with an authorized AP. |
| Man-in-the-middle | Alerts for
potential man-in-the-middle type attacks. Examples: Honeypot/evil twin active, PS-poll attack. |
| MAC Spoofing | Alerts for AP and client MAC spoofing. |
| Ad-hoc Network | Alerts for an authorized client participating in an ad-hoc network. |
| Prevention | Intrusion
prevention related alerts. Examples: Device reached maximum prevention capacity, AP/client needs to be prevented. |
| DoS | Alerts for
potential DoS type attacks. Examples: Disassociation flood attacks, Deauthentication flood attacks. |
WIPS Alerts
The following sections describe the various WIPS alerts and the actions you can take to mitigate or counter them:
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Banned AP active | This alert is raised when a banned AP gets active. | Locate the banned AP and remove it from the network. You can use the location tracking feature to locate this device. You can configure Intrusion Prevention to automatically prevent banned APs. You can also manually prevent an AP from the list of monitored APs. | Disabled | Disabled | Disabled | Disabled |
| Rogue AP active | This alert is raised when a rogue AP gets active. This is a serious security violation. Unauthorized users can gain access to the network if they are within the radio coverage of this AP. | You can use the location tracking feature to locate this AP on the floor map. If you have enabled the corresponding setting in the Intrusion Prevention Policy, WIPS will automatically prevent rogue APs. You can also manually prevent the AP from the list of monitored APs. However, note that prevention is not a permanent solution. | Enabled | Enabled | Enabled | Enabled |
| Offline mode: Rogue AP detected | This alert is raised when a Rogue AP is detected in the offline mode operation of an Arista device. This AP is not one of your authorized APs and is plugged into the network. This AP could have been used to gain unauthorized access to the network. | As mitigation against this threat, configure the policies to automatically prevent Rogue APs. | Enabled | Disabled | Disabled | Disabled |
| Indeterminate AP active | This alert is raised when an indeterminate AP becomes active. | WIPS cannot determine if this AP is connected to your network. If you know this AP, mark it authorized or external as appropriate. Otherwise, locate the AP and investigate if it poses a security threat to your network. You can use the location tracking feature to locate this AP on the floor map. You can configure Intrusion Prevention to automatically prevent either authorized or all clients from connecting to indeterminate APs. You can also manually prevent an AP from the list of monitored APs. However, note that prevention is not a permanent solution. | Disabled | Disabled | Disabled | Disabled |
| Unauthorized AP operating on non-allowed channel | This alert is rasied when an unauthorized AP starts operating on an non-allowed channel. | Operation on non-allowed channels amounts to a violation of the country's wireless communication laws. You can use the location tracking feature to locate the device. | Enabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Client MAC Spoofing | This alert is raised when the spoofing of MAC address of an authorized client is in progress. With MAC spoofing, an attacker imitates an authorized client by advertising the same identity as the latter. This is a serious security violation. | Locate the attacker client and remove it immediately from the network. You can also manually prevent the client from the list of monitored clients. However, note that prevention is not a permanent solution. | Disabled | Disabled | Disabled | Disabled |
| AP MAC Spoofing | This alert is raised when spoofing of the MAC address of an authorized AP is in progress. The same MAC is visible to two devices. With MAC spoofing, an attacker AP imitates an authorized AP by advertising the same identity as the latter. This is a serious security violation. | Locate the fake AP and remove it from the network.If you have enabled the corresponding Intrusion Prevention setting, WIPS will automatically prevent APs with the same MAC address. You can also manually prevent the AP from the list of monitored APs. However, note that prevention is not a permanent solution. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Offline mode: Authorized client association with rogue AP detected | This alert is raised when an authorized client association with rogue AP is detected. Authorized Client connecting to Rogue AP may be due to misconfiguration of the Client. | Rogue APs must be located and removed. As mitigation against this threat, configure Intrusion Prevention to automatically quarantine rogue APs. | Disabled | Disabled | Disabled | Disabled |
| Offline mode: Authorized client association with external AP detected | This alert is raised when an authorized client association with an external AP is detected. Such associations pose a security threat to the client and the network. | Configure authorized clients to prevent such associations. For example, ensure that the client connects to only those APs that advertise your corporate network SSID. As mitigation, configure Intrusion Prevention to automatically prevent authorized clients that connect to APs categorized as external. | Disabled | Disabled | Disabled | Disabled |
| Offline mode: Authorized client association with Honeypot AP detected |
This alert is raised when an authorized client association with Honeypot AP is detected. This can happen if Intrusion Prevention has not been configured to automatically prevent authorized clients from associating with Honeypot/Even Twin APs. It can also happen if a managed WiFi device is unable to prevent the association due to overload or limited visibility. Such connections pose a security threat as Authorized Clients may unwittingly provide confidential information (e.g. passwords) to the External AP over these connections. The External AP can also insert itself as a man-in-the-middle for authorized communications using this connection. It can also perform port scanning on the Client to discover its vulnerabilities.", |
Locate and remove such APs. If this cannot be done, change the SSIDs of your authorized APs. As mitigation against this threat, configure Intrusion Prevention to prevent authorized clients from associating with Honeypot/Evil Twin APs. | Disabled | Disabled | Disabled | Disabled |
| Offline mode: Unauthorized/Uncategorized client association with authorized AP detected | This alert is raised when unauthorized or uncategorized client association with authorized AP is detected. Such associations pose a security threat to the network. | Use either WPA or 802.11i on authorized APs. Also, use SSIDs different from those used by neighboring networks. As mitigation, configure Intrusion Prevention to prevent Unauthorized/Uncategorized clients from associating with authorized APs. | Disabled | Disabled | Disabled | Disabled |
| Offline mode: Unauthorized/Uncategorized client association with rogue AP detected | This alert is raised when unauthorized or uncategorized client association with rogue AP is detected. Such associations allow unauthorized clients to access your network. This is a serious security violation. | Locate and remove the rogue AP. As mitigation against this threat, configure Intrusion Prevention to automatically prevent rogue APs. | Disabled | Disabled | Disabled | Disabled |
| Offline mode: Soft AP detected | This alert is raised when a wireless client is operating as a Soft AP. A Soft AP is a wireless client operating as an access point. If this client is connected to the enterprise network (over the Ethernet, for example), unauthorized users can access the network through it. | Recommended action: Locate the client and shut it down. | Disabled | Disabled | Disabled | Disabled |
| Authorized client connection to guest SSID of authorized AP | This alert is raised when an authorized client gets connected to the guest SSID of an authorized AP. Guest SSIDs provide wireless access to guests. They are usually less secure than enterprise SSIDs. Authorized clients should not be connecting to guest SSIDs. | Remove SSID of Guest AP from the wireless profiles in the client. Instruct Authorized users to not connect to Guest APs. You can also configure layer-2 encryption such as static WEP on Guest APs to prevent accidental connection of Authorized Clients to Guest APs. | Enabled | Disabled | Enabled | Enabled |
| Banned client active | This alert is raised when a banned client gets active. | Locate the banned client and remove it from the network. You can use the location tracking feature to locate this device. You can configure Intrusion Prevention to automatically prevent banned clients from connecting to your APs. You can also manually prevent a client from the list of monitored clients. | Enabled | Enabled | Enabled | Enabled |
| Client in Bridging/ICS configuration | This alert is raised when a client is bridging its wireless interface and other network interface(s). If the other network interface(s) is connected to your enterprise network, the enterprise network will become accessible to unauthorized users via the wireless interface of this client. | Check the client configuration and disable the bridging or Internet Connection Sharing (ICS) option. Until then, if you have enabled the corresponding Intrusion Prevention setting, WIPS will automatically prevent such devices from engaging in wireless communication. | Disabled | Disabled | Disabled | Disabled |
| Rogue client active |
This alert is raised when a rogue client is active. A client is
marked as rogue if it falls under any of the following
conditions:
|
The rogue client will be automatically disrupted if the relevant Intrusion Prevention setting is enabled. Locate the rogue client using the location tracking feature. If this is a client connecting to a rogue AP or an external/Uncategorized client connecting to an authorized AP, shut the client down. If this client is bridging its wireless interface to the enterprise wired network, correct its wireless configuration settings. | Disabled | Disabled | Disabled | Disabled |
| Guest client mis-association | This alert is raised when a guest client gets connected to an unauthorized AP. The AP may not be malicious but such connections pose a security threat to the client and the network. | Configure the guest client to avoid such connections. For example, ensure that the client connects only to APs broadcasting your guest or corporate network SSID. If you enable the corresponding Intrusion Prevention setting, WIPS can prevent such connections. | Disabled | Disabled | Disabled | Disabled |
| Unauthorized client connection to guest SSID | This alert is raised when an unauthorized client gets connected to a guest SSID. Such connections can degrade the performance of your guest clients as they have to share the guest network bandwidth. | Ensure that you do not use commonly used SSIDs as your Guest SSID or the Guest SSID is not the same as one of your neighbors' SSIDs. Also, consider setting up WEP or WPA/WPA2 with PSK authentication on your guest network to prevent such associations. You can also set up an intrusion prevention policy to automatically disrupt such associations. | Disabled | Disabled | Disabled | Disabled |
| Authorized client mis-association | This alert is raised when an authorized client gets connected to an unauthorized AP. The AP may not be malicious but such connections pose a security threat to the client and the network. | Configure authorized clients to avoid such connections. For example, ensure that authorized clients connect only to APs broadcasting your corporate network SSID. You can enable the corresponding Intrusion Prevention settings to disallow authorized client mis-associations. | Enabled | Disabled | Enabled | Enabled |
| Soft Mobile Hotspot AP or Windows 7 Virtual AP Active | This alert is raised when a soft Mobile Hotspot AP or Windows 7 Virtual AP gets detected on a client. Clients running the Soft Mobile Hotspot AP or Windows 7 Virtual AP pose a serious security threat to the enterprise. If such a Client is also connected to the wired network, it can expose the Enterprise network to anyone who connects to the Soft Mobile Hotspot AP or Windows 7 Virtual AP. | Locate such clients and change their settings to stop this AP. Operating Systems like Windows 7 make it easy for users to create such APs. Several smart mobile device platforms such as Apple iOS and Android also natively provide hotspot AP features. Hence users must also be educated about the security threats from such settings. | Disabled | Disabled | Disabled | Disabled |
| Client authenticated using a non-compliant authentication type | This alert is raised when a client associated with an authorized AP uses the non-compliant authentication type instead of the allowed authentication type. | Ensure that the authentication server, the AP, and the WLAN infrastructure policy are all correctly configured. Use the location of the event and the details of the participating AP device to reach the AP to check its settings. | Disabled | Disabled | Disabled | Disabled |
| Unauthorized client connection to authorized AP | This alert is raised when an unauthorized client gets connected to an authorized AP. Such connections pose a security threat to the network. | Ensure that your network is not using an SSID being used on neighboring networks. Enforce an authentication policy between authorized APs and authorized clients. Until then, if you have enabled the corresponding Intrusion Prevention settings, WIPS will automatically prevent unauthorized clients. You can manually prevent the client from the list of monitored clients. Note: You might be preventing a client on a neighboring network. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Honeypot/Evil Twin active | This alert is raised when a Honeypot/Evil Twin AP is active. A potentially external AP is advertising an SSID used in your authorized WiFi Policy. This can lure your authorized clients into connecting to the external AP. Such connections pose a security threat because authorized clients may unwittingly provide confidential information (e.g. passwords) to the external AP. The external AP can also insert itself as a man-in-the-middle for authorized communications using this connection. It can also perform port scanning on the client to discover its vulnerabilities. | Locate the Honeypot AP and remove it from the vicinity of your network. Until then, if you have enabled the corresponding Intrusion Prevention setting, WIPS will prevent authorized clients from connecting to Honeypot APs. You can use the location tracking feature to locate this AP. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Enabled | Enabled | Enabled | Enabled |
| Offline Mode: Honeypot AP detected | This alert is raised when a Honeypot AP is detected. The AP is advertising an SSID used in your WiFi network. This may lure your authorized clients into connecting to the AP. | Locate and remove the AP. If this cannot be done, change the SSIDs of your authorized APs. As mitigation against this threat, configure Intrusion Prevention to prevent authorized clients from associating with Honeypot/Evil Twin APs. | Enabled | Disabled | Disabled | Disabled |
| PS-Poll attack in progress | This alert is raised when a PS-Poll attack is in progress against an authorized AP and client. In a PS-Poll attack, an attacker sends spoofed PS-Poll messages to the AP in order to steal the victim client's data. A flood of PS-Poll packets can even be used to starve a client when the client is in power-saving mode. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to locate the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Client MAC Spoofing | This alert is raised when the spoofing of MAC address of an authorized client is in progress. With MAC spoofing, an attacker imitates an authorized client by advertising the same identity as the latter. This is a serious security violation. | Locate the attacker client and remove it immediately from the network. You can also manually prevent the client from the list of monitored clients. However, note that prevention is not a permanent solution. | Disabled | Disabled | Disabled | Disabled |
| AP MAC Spoofing | This alert is raised when spoofing of the MAC address of an authorized AP is in progress. The same MAC is visible to two devices. With MAC spoofing, an attacker AP imitates an authorized AP by advertising the same identity as the latter. This is a serious security violation. | Locate the fake AP and remove it from the network.If you have enabled the corresponding Intrusion Prevention setting, WIPS will automatically prevent APs with the same MAC address. You can also manually prevent the AP from the list of monitored APs. However, note that prevention is not a permanent solution. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Offline mode: Authorized client detected in ad-hoc connection mode | This alert is raised when an authorized client is detected in an ad-hoc connection. Ad-hoc connections pose a security threat because unauthorized wireless clients can connect to authorized clients in ad-hoc mode. | Reconfigure such clients to not advertise or participate in ad-hoc networks. As mitigation, configure Intrusion Prevention to automatically prevent authorized clients that participate in any ad-hoc network. | Disabled | Disabled | Disabled | Disabled |
| Authorized client participating in ad-hoc network | This alert is raised when an ad-hoc network involving one or more authorized clients is active. Ad-hoc connections pose a security threat. Unauthorized clients can launch attacks on authorized clients via ad-hoc connections. Ad-hoc connections among authorized clients are also undesirable because enterprise security policies cannot be enforced on these connections. | See the sub-events of this event for information on clients participating in this ad-hoc network. Locate the authorized client(s) involved in the ad-hoc network and configure these clients to not use ad-hoc connections. You can use the location tracking feature to locate these clients on the floor map. Until then, if you have enabled the corresponding Intrusion Prevention settings, WIPS will prevent authorized clients from communicating over ad-hoc connections. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| AP reached maximum prevention capacity | WIPS raises this alert when AP reaches the maximum prevention capacity.This access point will no longer be able to prevent unwanted communication on a new channel. The Intrusion Prevention Level is a trade-off between prevention strength and the number of channels prevented simultaneously. | If you want to configure the AP to simultaneously quarantine on more channels, you must reduce the Intrusion Prevention Level. However, doing so will weaken the prevention and some packets might go through. | Enabled | Disabled | Disabled | Disabled |
| AP needs to be prevented | This alert is raised when an AP needs to be prevented. | Identify the reason for AP prevention. See the sub-events and the help for details. If the necessary conditions are satisfied (for example, the device is operating on a legal channel, and resources are available for prevention), then this AP will be prevented. Eliminate the condition that caused WIPS to prevent this AP. | Enabled | Disabled | Disabled | Disabled |
| Client needs to be prevented | This alert is raised when a client needs to be prevented. | Identify the reason for client prevention. See the sub-events and the help for details. If the necessary conditions are satisfied (for example, the device is operating on a legal channel, resources are available for prevention), then this client will be prevented. | Enabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Offline mode: DoS attack detected | This alert is raised when WIPS detects a DoS attack on a device. DoS attacks try to disrupt authorized communication. | Locate the device and shut it down or disconnect it from the network. | Disabled | Disabled | Disabled | Disabled |
| Disassociation flood attack in progress | This alert is raised when a disassociation flood attack is in progress against an authorized AP and client. A disassociation flood attack is a DoS attack wherein an attacker sends spoofed disassociation messages to break or prevent a connection between the victim AP and a client. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. | Disabled | Disabled | Disabled | Disabled |
| Disassociation broadcast attack in progress | This alert is raised when a disassociation broadcast attack is in progress against an authorized AP. A disassociation broadcast attack is a DoS attack wherein an attacker sends spoofed broadcast disassociation messages to break or prevent all client connections to the victim AP. While this attack is in progress, no client will be able to connect to the AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. | Disabled | Disabled | Disabled | Disabled |
| Association flood attack in progress | This alert is raised when an association flood attack is in progress against an authorized AP. An association flood attack is a DoS attack wherein an attacker overwhelms the victim AP with connection requests (usually with spoofed source MAC addresses in them). This can quickly fill up the association table of an AP and prevent it from accepting any new connection requests from legitimate clients. | Locate the attacker device and shut it down immediately. Then reset the AP so that its association table frees up. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. | Disabled | Disabled | Disabled | Disabled |
| Association table overflow |
This alert is raised when WIPS detects an overflown association table at an authorized AP. The association table keeps track of successful associations to the authorized AP. Association table overflow happens when the number of successful associations exceeds 127 clients as a result of the AP receiving a large number of connection requests in a short period of time. This could happen due to a large number of legitimate connection requests or due to a DoS attack such as an association flood attack in which the attacker deliberately generates a large number of connection requests. The AP cannot accept new connection requests when its association table is full. |
If you suspect that a DoS attack is in progress, locate the attacker device and shut it down immediately. If there is no DoS attack in progress, then the table could have overflowed due to high client density in this area. In any case, reset the AP so that its association table frees up. If the client density remains high in this area, then consider adding more APs. | Disabled | Disabled | Disabled | Disabled |
| Fake client detected | This alert is raised when WIPS detects the use of a fake client tool near an AP. Fake client tool generates a large number of bogus Probe Requests with different MAC addresses. This can fill up the databases of WiFi security and management systems with bogus client records. | Locate the device running the fake client tool and shut it down immediately or disconnect it from the network. | Disabled | Disabled | Disabled | Disabled |
| Deauthentication flood attack in progress | This alert is raised when a de-authentication flood attack is in progress against an authorized AP and client. A de-authentication flood attack is a DoS attack wherein the attacker sends spoofed de-authentication messages to break or prevent a connection between the victim AP and a client. While this attack is in progress, the client cannot connect to the AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to locate the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| Deauthentication broadcast attack in progress | This alert is raised when a de-authentication broadcast attack is in progress against an authorized AP. A deauthentication broadcast attack is a DoS attack wherein the attacker sends spoofed broadcast de-authentication messages to break or prevent all client connections to the victim AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. | Disabled | Disabled | Disabled | Disabled |
| Authentication flood attack in progress | This alert is raised when an authentication flood attack is in progress against an authorized AP. An authentication flood attack is a DoS attack wherein the attacker overwhelms the victim AP with connection requests, usually with spoofed source MAC addresses in them. This can quickly fill up the connection table of an AP and prevent it from accepting any new connection requests from legitimate clients. | Locate the attacker device and shut it down immediately. Then reset the AP so that its connection table frees up. This event could be accompanied by another DoS attack that actively disconnects clients from APs. This is because some clients aggressively try to reconnect to the AP and flood the wireless medium with Authentication Requests. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. | Disabled | Disabled | Disabled | Disabled |
| EAPOL Logoff flood attack in progress | This alert is raised when a EAPOL Logoff flood attack is in progress against an authorized AP and client. EAPOL Logoff flood attack is a DoS attack wherein an attacker sends spoofed EAPOL Logoff messages to an AP to break the connection between the AP and its client. While this attack is in progress, the client cannot connect to the AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| EAPOL Start flood attack in progress | This alert is raised when an EAPOL Start flood attack is in progress against an authorized AP. EAPOL Start flood attack is a DoS attack wherein an attacker overwhelms an AP with EAPOL Start requests (usually with spoofed source MAC addresses in them). This can quickly fill up the association table of the AP and prevent it from accepting any new connection requests from legitimate clients. An EAPOL Start flood is always accompanied by an Authentication flood and an Association flood because authentication and association are prerequisites for an EAPOL Start request. | Locate the attacker device and shut it down immediately. Then reset the AP. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| Premature EAP Success attack in progress | This alert is raised when a Premature EAP Success attack is in progress against an authorized AP and client. Premature EAP Success attack is a DoS attack wherein the attacker sends spoofed EAP Success messages to a client to confuse its EAP state machine. This can result in repeated restarting of the client’s EAP state machine, preventing the client from connecting to an AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| Premature EAP Failure attack in progress | This alert is raised when a Premature EAP Failure attack is in progress against an authorized AP and client. Premature EAP Failure attack is a DoS attack wherein the attacker sends spoofed EAP Failure messages to a client to confuse its EAP state machine. This can result in repeated restarting of the client’s EAP state machine, preventing the client from connecting to an AP. | Locate the attacker device and shut it down immediately. You can use the event location tracking feature to determine the physical location of the attacker on the floor map. Note: Location tracking might be inaccurate if the attacker is not on your premises. | Disabled | Disabled | Disabled | Disabled |
| Fake AP detected | This alert is raised when WIPS detects the use of fake AP tool. The Fake AP tool generates a large number of bogus beacon frames with different MAC addresses. This confuses wireless clients. It can also fill up the databases of WiFi security and management systems with bogus AP records. | Locate the device running the fake AP tool and shut it down immediately or disconnect it from the network. | Disabled | Disabled | Disabled | Disabled |
| RTS/CTS flood | This alert is raised when WIPS detects an RTS/CTS flood on a particular channel near an AP. RTS/CTS flooding is a DoS attack wherein an attacker sends requests to reserve the wireless channel for large durations (usually with spoofed source MAC addresses in them). These requests can block legitimate devices operating on that channel from accessing the wireless medium. | Locate the attacker device and shut it down immediately. | Disabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Cellular activity detected | This alert is raised when WIPS detects cellular activity near one or more managed Wi-Fi devices. One or more cellular connections are active within 40 feet of the device. | Move the cellular device away from the Wi-Fi device. | Disabled | Disabled | Disabled | Disabled |
| Excessive NULL probes detected | This alert is raised when WIPS detects Excessive NULL Probe Requests detected near an access point. Typically, NULL probes come from a harmless Windows/Linux laptop when it is not able to associate with an AP in its vicinity. However, the NULL probes could be from a client running a network scanning tool such as Netstumbler, Wellenreiter. Such tools gather information about the wireless network. | Track the location of the client and check if this client is able to associate to any AP in the vicinity. If the Client is not engaged in network scanning or malicious activity, no action is required. | Disabled | Disabled | Disabled | Disabled |
Configure System Alerts
System alerts are triggered by events related to the Wi-Fi server (e.g., the active server switches to the standby server) or the AP/Sensor (for example, a new network is detected or the memory utilization exceeded a certain threshold). You can define the severity of a system alert and choose how to notify a user. You can also select if the alert affects the security status of your network; for example, when a server stops, some WIPS functionality is lost, which could make your network vulnerable.
Example: New network detected

When a new network is detected, CV-CUE generates an alert as shown in the figure above. You can configure this alert as follows:
- Set the Severity of the alert to "Low".
- Display this alert on the UI.
- Do not send an email to an administrator.
- Notify an external entity such as a Syslog server about this alert.
- Do not have the alert affect the security status of your network.
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| Server started | This is an informational alert raised when a server instance starts or boots up. | This is an information alert. No action is required. | Enabled | Disabled | Disabled | Disabled |
| Server stopped | This is an informational alert raised when a server instance stops. | If this is not a planned shutdown, investigate why the server stopped. | Enabled | Disabled | Disabled | Enabled |
| Database backup result | This alert is raised when the server takes a backup of the database. This alert captures the remote server IP address and the remote file details. |
If the database backup failed, verify the following:
|
Enabled | Disabled | Disabled | Disabled |
| Database restore result | This alert is raised when the server restores the database. | If the restore operation is successful, the current server database is overwritten with the restored database. This is an informational alert. Ensure that this action was performed by authorized personnel. | Enabled | Disabled | Disabled | Disabled |
| Automatic deletion done | This alert is raised when a scheduled automatic deletion job is completed on a server. This job deletes old and inactive access points, clients, unmonitored networks, device prevention history, old events, and user action logs. | This is an information alert. No action is required. | Enabled | Disabled | Disabled | Disabled |
| Device connection rejected; licensed limit reached | This alert is raised when you attempt to connect a device to a server after the number of devices connected has already reached the number of devices per your license. | To connect more devices, apply for a new license allowing more devices. Contact Technical Support for information on procuring the license. | Enabled | Disabled | Enabled | Disabled |
| High Avaibility Server Switch | This alert is raised when the server switches to standby server. After the HA failover, the server that was on standby becomes the Active server. When the server that was the Active one before the failover recovers, it becomes the Standby server. |
If this event is raised when Failover mode is set to Automatic, the Active server may be down or its connectivity with the Standby server over the network interface may be down. Unless both appliances are ON and connected, the HA feature will not work. | Enabled | Disabled | Disabled | Enabled |
| Data synchronization link is up | This alert is raised when The connection between the Active and Standby servers is done. Active and Standby servers are now connected | This is an information alert. No action is required. | Enabled | Disabled | Disabled | Disabled |
| Data synchronization link is down | This affects server availability because the Standby server is no longer connected to the Active server. Data synchronization with the Active server is essential in case the Standby server needs to take over from the Active server. | Restore the link between the Active and Standby servers. | Enabled | Enabled | Enabled | Enabled |
| Data synchronization is lagging | This alert is raised when database synchronization between Active and Standby servers is slow. | Check the Data Sync link between the two servers. If it is up, then the lag may be temporary. Wait for few minutes and then check if 'Data Synchronization State' is 'Complete' in the 'get ha' CLI. If it is not 'Complete', contact Technical Support. | Enabled | Enabled | Enabled | Disabled |
| Inactive Clients Detected | This alert is raised when server detects inactive clients that are eligible for deletion. | Enable Auto Deletion for Inactive Clients. To enable Auto Deletion, go to Monitor>WIPS>Clients, and click Auto Deletion.. | Enabled | Disabled | Disabled | Disabled |
| Alert | Alert Description | Recommended Action | Default Setting Display | Email | Notify | Affects Severity Status |
|---|---|---|---|
| CPU utilization exceeds X for X minutes | This alert is raised when the AP’s CPU utilization exceeds your configured threshold for the configured time duration. | Configure optimal utilization threshold values. | Enabled | Enabled | Enabled| Disabled |
| Memory utilization exceeds X for X minutes | This alert is raised when the AP’s memory utilization exceeds the configured threshold for the configured time duration. | Configure optimal memory utilization threshold values. | Enabled | Enabled | Enabled| Disabled |
| Access point is not reachable by the server for at least X minutes | This alert is raised when the AP is not reachable by the server since the last configuration time duration. | Investigate why the AP device is not reachable by the server. It could be due to network issues, power issues with the device, or a planned disconnection of the device from the network. | Enabled | Enabled | Disabled| Disabled |
| The number of access points with failed firmware update exceeds X | This alert is raised when a certain number of APs with failed firmware update exceeds the configured threshold. | Check for network connectivity issues. Contact Technical Support if the problem persists. | Disabled | Disabled | Disabled | Disabled |
| Authorized AP inactive | This alert is raised when an authorized AP becomes inactive. Clients cannot connect to an inactive AP and it can create a coverage gap in your Wi-Fi network. |
If this is not a planned shutdown, investigate why the AP was shut down. Restart the AP. |
Disabled | Disabled | Disabled | Disabled |
| Authorized AP disconnected from network | This alert is raised when an authorized AP gets disconnected from the network. A disconnected AP can create a gap in the WLAN coverage of your Wi-Fi network as it prevents authorized clients from accessing the network. how | Investigate why the disconnection happened. It could be due to a physical disconnection or due to failure of the AP's wire side interface. Connect the AP back to the network. | Disabled | Disabled | Disabled | Disabled |
| Access Point Reboot | An alert is raised when the AP gets rebooted. | No action is required if the reboot was because of a configuration change or an upgrade. Otherwise, check the AP power source and port connectivity, and the configuration of the AP. For details, check the AP logs for problems that might have caused the reboot. | Enabled | Disabled | Enabled | Disabled |
| VAPs down for network profile | This alert is raised when VAPs for a Network Profile are down because both tunnel interfaces are unreachable. | Investigate and fix any network connectivity issues between the device and the tunnel endpoints. | Enabled | Enabled | Enabled | Disabled |
| VAPs up for network profile | This alert is raised when VAPs for Network Profile are brought up because the tunnel interface, primary or secondary, becomes reachable. | This is an informational alert. No action is required. | Disabled | Disabled | Disabled | Disabled |
| Authentication RADIUS server switched | This alert is raised when the authentication RADIUS server is switched. | Investigate and fix any network connectivity issues between the device and the RADIUS server. | Enabled | Enabled | Enabled | Disabled |
| RADIUS server not responding | This alert is raised when the RADIUS server stops responding. | Investigate and fix any network connectivity issues between the device and the RADIUS server. | Enabled | Enabled | Enabled | Disabled |
| Tunnel endpoint down (Applicable to AP build 13.0 and higher) | This alert is raised when the tunnel endpoint is down for a particular network profile. | Investigate and fix any network connectivity issues between the device and the tunnel endpoint. | Enabled | Enabled | Enabled | Disabled |
| Tunnel endpoint down (Applicable to AP build lower than 13.0) | This alert is raised when the tunnel endpoint is down for a particular network profile. | Investigate and fix any network connectivity issues between the device and the tunnel endpoint. | Enabled | Enabled | Enabled | Disabled |
| Tunnel endpoint switched | This alert is raised when the tunnel endpoint is switched. | Investigate and fix any network connectivity issues between the device and the tunnel endpoint. | Enabled | Enabled | Enabled | Disabled |
| Device firmware version unavailable | This alert is raised when an attempted scheduled update or auto-update of a device fails because the firmware version is not available. | Change the scheduled update or auto-update policy and configure an available version. | Enabled | Disabled | Enabled | Disabled |
| Device firmware update failed | This alert is raised when an attempted firmware update of a device fails. This could be because of network connectivity problems between the device and the server. | Investigate and fix any network connectivity issues between the device and the server, and then re-attempt the firmware update. Contact Technical Support if the problem persists. | Enabled | Disabled | Enabled | Disabled |
| Device with old firmware version detected | This alert is raised when the device firmware is lower than the latest available firmware version This device may not have some of the features from the latest version. | Update the device firmware. Arista recommends that you upgrade the device firmware to the latest version. Contact Technical Support if you have any questions.. | Disabled | Disabled | Disabled | Disabled |
| Device disconnected from server | This alert is raised when a device gets disconnected from the server. | The device can get disconnected when it is rebooting, which takes a few minutes. If the device stays disconnected for more than 10 minutes, investigate the reason. | Enabled | Enabled | Enabled | Enabled |
| New device connected to server | This alert is raised when a new device gets connected to the server. | Move the device from the staging area to your required location. | Disabled | Disabled | Disabled | Disabled |
| Device operating in fail-safe mode | This alert is raised when a device starts operating in fail-safe Mode. This could be because of configuration changes or a firmware update on the device. | Undo any recent configuration changes and reboot the device from the UI. If the issue persists, try upgrading the device or contact Technical Support. | Enabled | Enabled | Enabled | Disabled |
| Authentication failed for managed WiFi device | This alert is raised when a managed Wi-Fi device fails authentication. | This alert provides the reason behind failed authentication. If the communication key on the device does not match the one on the server, log in to the device and set the correct communication key. If the device uses legacy authentication, turn on the legacy authentication method on the server and upgrade the device. After the upgrade, the device will connect to the server if the server is using the factory default communication key. If you have changed the communication key on the server, log into the device and set the correct key. | Enabled | Enabled | Enabled | Disabled |
| AP with incompatible version detected | This alert is raised when an AP is running an incompatible version. An AP with an incompatible version cannot connect to the server. | Upgrade the AP to the recommended version. | Enabled | Enabled | Enabled | Disabled |
| New network detected | This alert is raised when a device detects a new network. You can configure the SSID (under the authorized WiFi Policy) to ensure that the SSID to network/VLAN mappings are enforced. A managed WiFi device in WIPS mode can then detect APs connected to its own network. | Review the authorized WiFi Policy to ensure that the SSIDs are configured with the correct SSID to network/VLAN mapping. | Disabled | Disabled | Disabled | Disabled |
| Authentication failed for access point uplink port | This alert is raised when a device fails to authenticate its uplink port. | Investigate the device. | Enabled | Enabled | Enabled | Disabled |
| Maximum VLAN limit reached | This alert is rasied when the AP reaches Maximum VLAN limit. | This is an informational alert. | Enabled | Enabled | Enabled | Disabled |
| Access Point with non-compliant firmware version detected | This alert is raised when the current version of the access points do not match with the compliant version configured for the selected location | Upgrade your AP builds to the complaint versions. You can upgrade the access point from Monitor > WiFi > Access Points or Monitor > WIPS > Managed WiFi Devices | Enabled | Enabled | Enabled | Enabled |
| Local Authentication |
This alert is raised when a BSSID enters Local Authentication mode. |
Investigate and fix any network connectivity issues between the device and the RADIUS server. | Enabled | Disabled | Disabled | Disabled |
Alerts Auto-Deletion
You can specify the duration to retain alerts on the server. After the specified duration, the alerts are automatically deleted.
- Got to .
- In the Configure Alerts tab, click Auto Deletion.
- From the Auto Deletion right panel, specify the number of
security and system alerts that you want to retain.
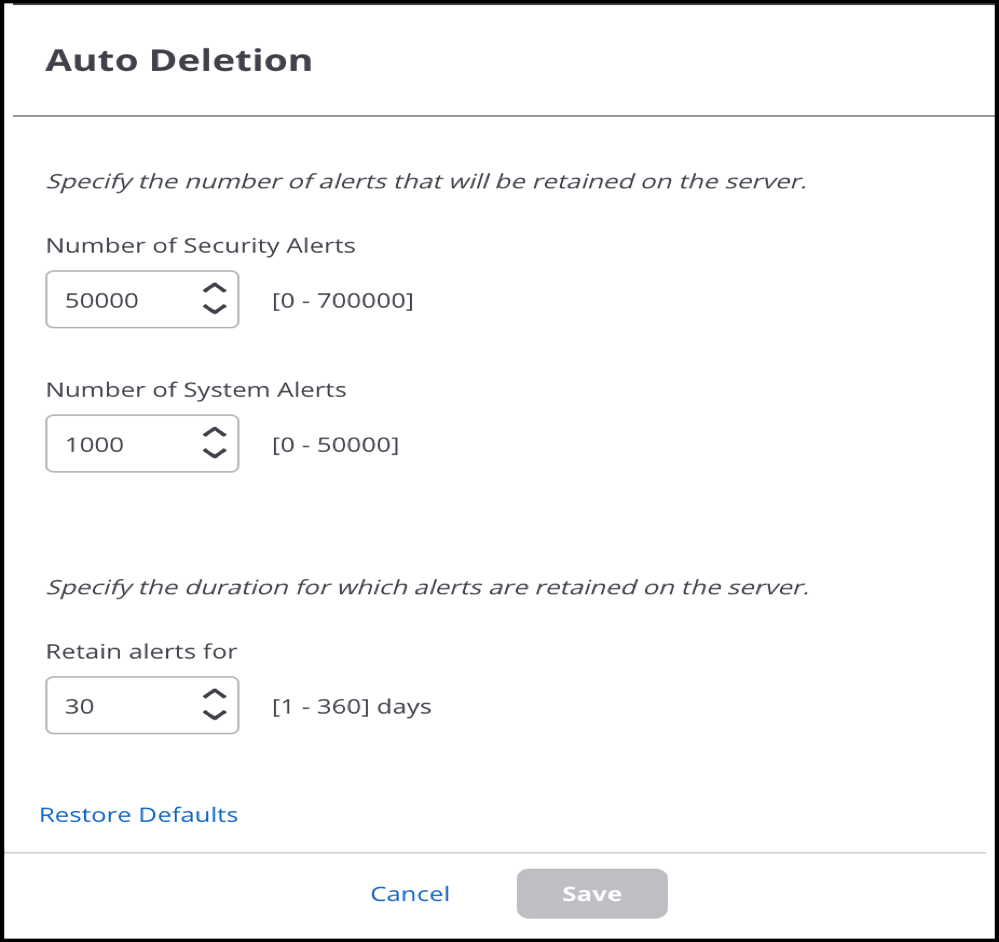
- Specify the duration to retain alerts.
- Save the settings.
