NG Firewall Protect Apps
Firewall
Firewall provides traditional firewall functionality, blocking and/or flagging traffic based on rules.

The term "Firewall" has grown to encompass many functionalities and has a wide array of meanings. The "firewall" is often use interchangeably with router, gateway and Unified Threat Management (UTM) or . Even the NG Firewall is a "next-gen" "firewall." There are also host-based "firewalls" that run on the local host computer.
The "Firewall" app is a traditional firewall used to block and/or flag TCP and UDP sessions passing through NG Firewall using rules. The Firewall app provides the same functionality as the traditional "firewall" - the ability to use rules to control which computers and communicate on a network.
Settings
This section reviews the different settings and configuration options available for Firewall.
Status

Rules
The Rules tab allows you to specify rules to Block, Pass or Flag traffic that crosses the NG Firewall.
The Rules documentation describes how rules work and how they are configured. Firewall uses rules to determine to block/pass the specific session and if the sessions is flagged. Flagging a session marks it in the logs for reviewing in the event logs or reports, but has no direct effect on the network traffic.
Typically NG Firewall is installed as a NAT/gateway device, or behind another NAT/gateway device in bridge mode. In this scenario all inbound sessions are blocked by NAT except those explicitly allowed with port forwards. Because of this, the Firewall does not block anything by default. It is up to you to decide the best fit for your network, whether you only want to block specific ports or you want to block everything and allow only a few services.
- Pass: Allows the traffic that matches the rule to flow.
- Block: Blocks the traffic that matches the rule.

Reports
The Reports tab provides a view of all reports and events for all traffic handled by Firewall.
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Firewall Summary | A summary of firewall actions. |
| Scanned Sessions | The amount of scanned, flagged, and blocked sessions over time. |
| Top Scanned Hostnames | The number of scanned session grouped by hostname. |
| Top Flagged Hostnames | The number of flagged session grouped by hostname. |
| Top Blocked Hostnames | The number of blocked sessions grouped by hostname. |
| Top Scanned Clients | The number of scanned session grouped by client. |
| zTop Flagged Clients | The number of flagged session grouped by client. |
| Top Blocked Clients | The number of blocked session grouped by client. |
| Top Scanned Usernames | The number of scanned session grouped by username. |
| Top Flagged Usernames | The number of flagged session grouped by username. |
| Top Blocked Usernames | The number of blocked session grouped by username. |
| Top Scanned Server Ports | The number of scanned session grouped by server (destination) port. |
| Top Flagged Server Ports | The number of flagged session grouped by server (destination) port. |
| Top Blocked Server Ports | The number of blocked session grouped by server (destination) port. |
| All Events | All events are scanned by Firewall App. |
| Flagged Events | Events flagged by Firewall App. |
| Blocked Events | Events are blocked by Firewall App. |
Related Topics
Firewall Reports
The Reports tab provides a view of all reports and events for all traffic handled by Firewall.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
| Report Entry | Description |
|---|---|
| Firewall Summary | A summary of firewall actions. |
| Scanned Sessions | The amount of scanned, flagged, and blocked sessions over time. |
| Top Scanned Hostnames | The number of scanned session grouped by hostname. |
| Top Flagged Hostnames | The number of flagged session grouped by hostname. |
| Top Blocked Hostnames | The number of blocked sessions grouped by hostname. |
| Top Scanned Clients | The number of scanned session grouped by client. |
| Top Flagged Clients | The number of flagged session grouped by client. |
| Top Blocked Clients | The number of blocked session grouped by client. |
| Top Scanned Usernames | The number of scanned session grouped by username. |
| Top Flagged Usernames | The number of flagged session grouped by username. |
| Top Blocked Usernames | The number of blocked session grouped by username. |
| Top Scanned Server Ports | The number of scanned session grouped by server (destination) port. |
| Top Flagged Server Ports | The number of flagged session grouped by server (destination) port. |
| Top Blocked Server Ports | The number of blocked session grouped by server (destination) port. |
| All Events | All events scanned by Firewall App. |
| Flagged Events | Events flagged by Firewall App. |
| Blocked Events | Events blocked by Firewall App. |
The tables queried to render these reports:
Related Topics
Intrusion Prevention
Intrusion Prevention is an Intrusion Detection system that detects malicious activity on your network.

To detect malicious activity, Intrusion Prevention uses signatures, a method that draws upon a database of known attack patterns. If a session matches a signature, its enabled action directs Intrusion Prevention to Log (records the incident but does not stop the activity) or Block (records the incident and does stop the activity).
There is tremendous diversity between networks,and it is possible for a signature to correctly identify malicious activity on one network and incorrectly match legitimate traffic on another. Logging all matching signatures can make it difficult to effectively monitor Intrusion Prevention, and blocking can disrupt legitimate traffic, causing your network to appear broken. Therefore, it is perfectly legitimate for there to be many signatures set as disabled or not active in Intrusion Prevention. In fact, it is advised that you use the Recommended actions as specified by the signature database providers.
The database contains over 40,000 signatures, making it difficult to manage signatures directly. Rules are used to configure groups of signatures on matching various attributes. A condition can match an attribute such as classtype. For all signatures that match they are configured in Intrusion Prevention according to the rule action. Any signature not matched by a rule is Disabled. A default set of rules based on system memory is enabled by default.
The signature database is automatically updated several times a week. New and updated rules will be configured as determined by rules.
All detected activity for enabled signatures is recorded in the Intrusion Prevention All Events log. You should review this log on a daily basis.
Note: Intrusion Prevention installs but is off by default.
Note: Intrusion Prevention can be memory intensive and requires at least 2GB of RAM. The amount used is a combination of the number of enabled signatures and the amount of traffic that goes through your system.
Settings
When To Scan
Intrusion Prevention can be run before or after other network processing. Which option depends largely on your reasons for using Intrusion Prevention.
When Before other Network Processing is selected (the default), IPS sees all traffic, even if it will subsequently be dropped by the firewall. This means IPS will see much malicious activity like port scans intrusion attempts on the public IP addresses on almost all networks, even though that traffic will ultimately just be dropped. The advantage of this approach is that Intrusion Prevention sees and logs everything, providing the most complete picture. The disadvantage is that it usually logs so much that the Intrusion Prevention event log quickly becomes ignored because it logs thousands of events per day and this is completely normal and expected.
When After other Network Processing is selected, IPS will only scan traffic that will pass through the firewall. Most networks where an NG Firewall is running with a Public IP and doing NAT and only port forwarding select or no traffic at all, this will be extremely different from scanning "prerouting". The advantage of this mode is that IPS will only scan/log on traffic that is entering your network and, therefore, ignores a lot of the standard "noise" from incoming port scans and vulnerability scans that just get dropped at the firewall and logs only on traffic that should potentially concern the administrator. Another advantage is that it fully allows bypass traffic to work as expected. The disadvantage of this mode is that it provides a less complete picture of activity on the public interface it now no longer logs attempts that just get dropped.
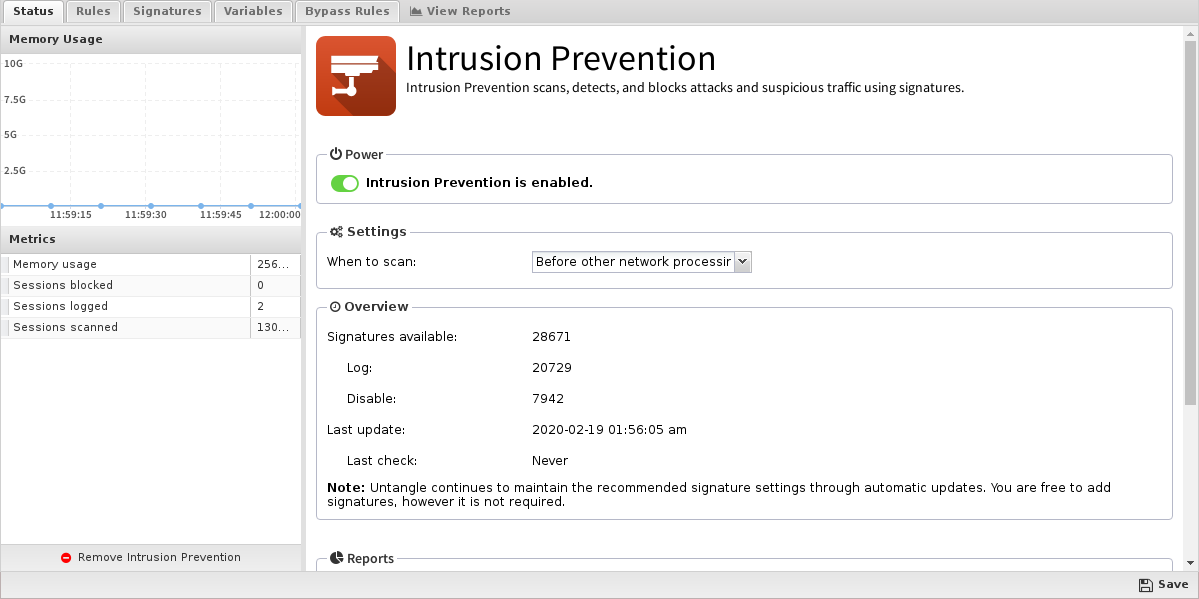
Status
- Memory Usage: The amount of system memory the IPS engine is using compared to your installed system memory.
- Metrics: The number of blocked, logged, and scanned sessions.
- Overview: Signatures and Signature Updates.
- Signatures: Total number of signatures available and the number set for Log, Block, Disabled.
- Updates: The last time the signature database was updated and the last time a check was performed. Database updates do not occur on each check.
Figure 3. Apps Intrusion-Prevention Status
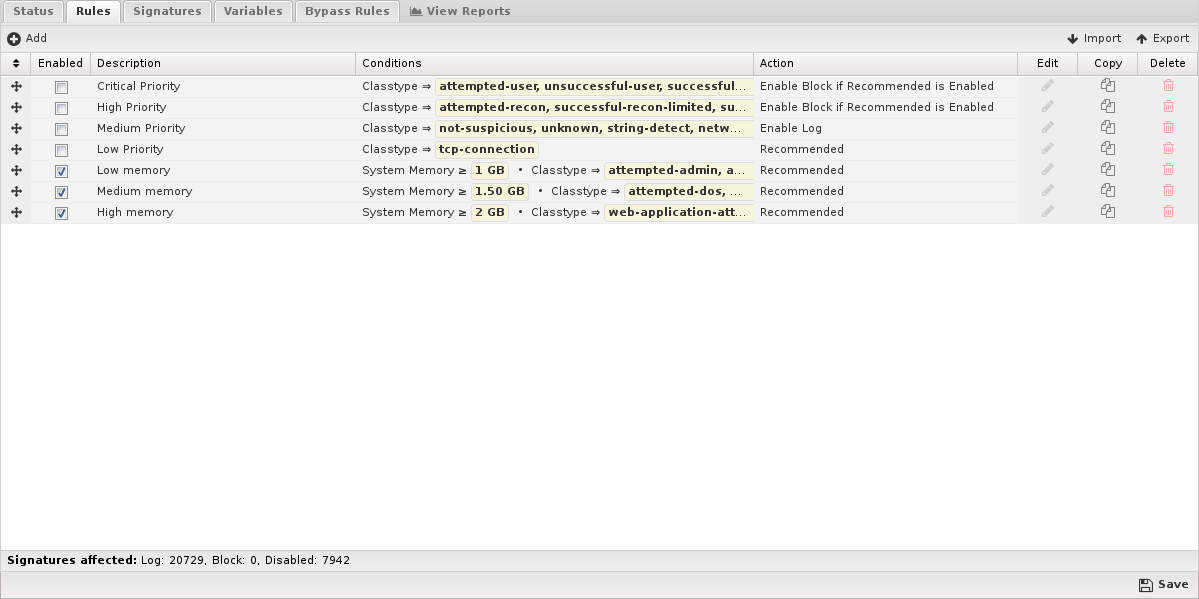
Rules
Rules allow you to control which signatures are enabled (and their actions) or disabled. For each signature, the rules are evaluated in order, and the action from the first matching rule is used to determine the status of that signature. The Intrusion Prevention rules are the mechanism to determine which signatures are enabled and their associated actions. These rules have no impact on network traffic and are not evaluated against packets, sessions, or network traffic in any manner.
Any signature not matched by any rule is disabled.
The Rules documentation describes how rules generally work and how they are configured. The major difference for Intrusion Prevention is the Conditions List.
At the bottom of the tab, a stats bar indicates how many signatures are affected by the currently defined rules.
Rule Conditions
Conditions define which signatures will match the rule. If and only all conditions match, the rule is considered a match.
| Name | Syntax | Function |
|---|---|---|
| Signature identifier | Numeric | Matches if the value matches the exact or partial signature identifier. |
| Group identifier | Numeric | Matches if the value matches the exact or partial group identifier. |
| Category | Checkbox | Matches if the value is in one of the checked categories. |
| Classtype | Checkbox | Matches if the value is in one of the checked classtypes. |
| Message | Text | Matches if the value matches the exact or partial signature subject message. |
| Protocol | Checkbox | Matches if the value is in one of the checked protocols. |
| Source Address | Text | Matches if the value matches the exact or partial source address. |
| Source Port | Text | Matches if the value matches the exact or partial source port. |
| Destination Address | Text | Matches if the value matches the exact or partial destination address. |
| Destination Port | Text | Matches if the value matches the exact or partial destination port. |
| Signature | Text | Matches if the value matches the exact or any part of the entire signature. |
| Custom | Boolean | Matches if the value is a custom signature. |
| Recommended Action | Select | Matches if the value is a signature's recommended action. |
| System Memory | Numeric | Matches if system memory matches this value. |
Rule Actions
| Action | Function |
|---|---|
| Recommended | Each signature will use its specific Recommended Action. If that Recommended Action is disabled, it will not be enabled. |
| Enable Log | Each signature will be enabled to log. |
| Enable Block if Recommended is Enabled | Only if the signature's Recommended Action is Log will the signature be configured for Block. Use this for "wide" condition matches like classtype. |
| Enable Block | Each signature will be enabled to block. Use this for "narrow" matches like sid and gid. |
| Disable | Each signature will be disabled and not used by Intrusion Prevention. |
| Whitelist | Each signature's Source and/or Destination networks will be modified to exclude networks defined by the selected variables. |
Signatures
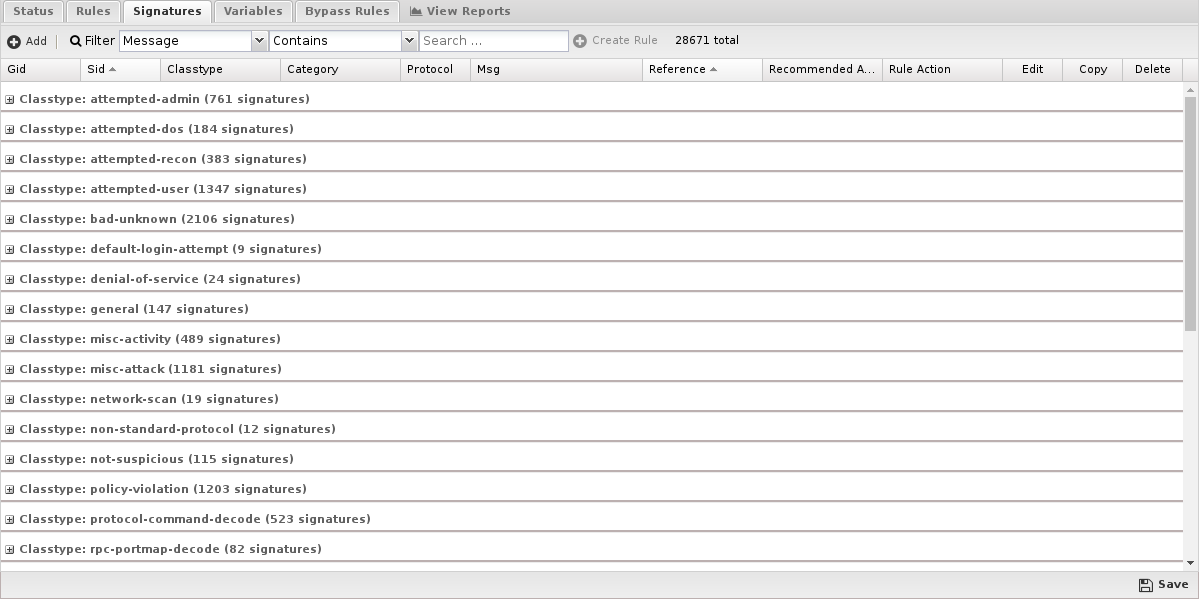
Navigation
By default, signatures are grouped by classtype, and you can expand the groups to view the individual signatures.
To better find specific signatures, you can use the Filter to select signature fields and the match you're looking for. The grid view will change to show those signatures matching the filter.
If your filter returned one or more matches, you can create a rule from the filter by clicking Create Rule.
Mousing over a grid cell will show appropriate information related to that cell. For example, if you mouse over the Rule Action cell, you'll see which rule is affecting this signature.
Custom Signatures
You may create and maintain your signatures, but most use the default database.
If you want to add custom signatures you can do so either by clicking Add.
Variables
This tab provides administrators access to Suricata variables. These variables are used in rules to specify criteria for the source and destination of a packet.
Suricata's most important variable is $HOME_NET. $HOME_NET defines the network or networks you are trying to protect - it is computer automatically based on your network configuration - it includes all local networks (including aliases). Under nearly every circumstance, you will want to leave these values as-is.
Bypass Rules
Updates
The signature database is checked automatically every night. Updates are typically released 2-3 times a week. The signature database does not affect custom signatures. New signatures will be integrated into Intrusion Prevention according to defined rules.
Reports
The Reports tab provides a view of all reports and events for all traffic handled by Intrusion Prevention.
This application's reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
| Report Entry | Description |
|---|---|
| Intrusion Prevention Summary | A summary of intrusion detection and prevention actions. |
| Intrusion Detection (all) | The amount of detected and blocked intrusions over time. |
| Intrusion Detection (logged) | The amount of detected intrusions over time. |
| Intrusion Detection (blocked) | The amount of blocked intrusions over time. |
| Top Rules (all) | The number of intrusions detevted by the rule. |
| Top Rules (logged) | The number of intrusions logged by rule. |
| Top Rules (blocked) | The number of intrusions blocked by rule. |
| Top Signatures (all) | The number of intrusions detected by signature. |
| Top Signatures (logged) | The number of intrusions logged by signature. |
| Top Signatures (blocked) | The number of intrusions blocked by signature. |
| Top Classtypes (all) | The number of intrusions detected by classtype. |
| Top Classtypes (logged) | The number of intrusions logged by classtype. |
| Top Classtypes (blocked) | The number of intrusions blocked by classtype. |
| Top Categories (all) | The number of intrusions detected by category. |
| Top Categories (logged) | The number of intrusions logged by category. |
| Top Categories (blocked) | The number of intrusions blocked by category. |
| Top Source IP Addresses (all) | The number of intrusions detected by source IP address. |
| Top Source IP Addresses (logged) | The number of intrusions logged by source IP address. |
| Top Source IP Addresses (blocked) | The number of intrusions blocked by source IP address. |
| Top Source Ports (all) | The number of intrusions detected by source port. |
| Top Source Ports (logged) | The number of intrusions logged by source port. |
| Top Source Ports (blocked) | The number of intrusions blocked by source port. |
| Top Destination IP Addresses (all) | The number of intrusions detected by the destination IP address. |
| Top Destination IP Addresses (logged) | The number of intrusions logged by the destination IP address. |
| Top Destination IP Addresses (blocked) | The number of intrusions blocked by destination IP address. |
| Top Destination Ports (all) | The number of intrusions detected by destination port. |
| Top Destination Ports (logged) | The number of intrusions logged by destination port. |
| Top Destination Ports (blocked) | The number of intrusions blocked by destination port. |
| Top Protocols (all) | The number of intrusions detected by protocol. |
| Top Protocols (logged) | The number of intrusions logged by protocol. |
| Top Protocols (blocked) | The number of intrusions blocked by protocol. |
| All Events | All sessions scanned by Intrusion Prevention. |
| Logged Events | All sessions match Intrusion Prevention signatures and are logged. |
| Blocked Events | All sessions matching Intrusion Prevention signatures are blocked. |
The tables queried to render these reports:
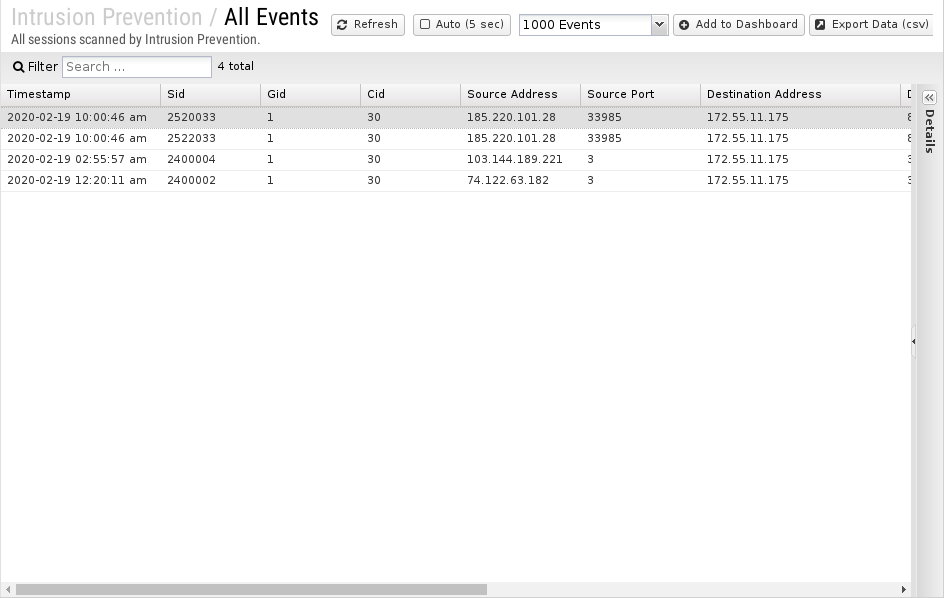
All Events
The All Events report shows all enabled signature matches found by Intrusion Prevention.
Related Topics
- Intrusion Prevention Systems
- Suricata - Writing Suricata Signatures
Intrusion Prevention Reports
The Reports tab provides a view of all reports and events for all traffic handled by Intrusion Prevention.
Reports
This application's reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
| Report Entry | Description |
|---|---|
| Intrusion Prevention Summary | A summary of intrusion detection and prevention actions. |
| Intrusion Detection (all) | The amount of detected and blocked intrusions over time. |
| Intrusion Detection (logged) | The amount of detected intrusions over time. |
| Intrusion Detection (blocked) |
The amount of blocked intrusions over time. |
| Top Rules (all) | The number of intrusions detevted by rule. |
| Top Rules (logged) | The number of intrusions logged by rule. |
| Top Rules (blocked) | The number of intrusions blocked by rule. |
| Top Signatures (all) | The number of intrusions detected by signature. |
| Top Signatures (logged) | The number of intrusions logged by signature. |
| Top Signatures (blocked) | The number of intrusions blocked by signature. |
| Top Classtypes (all) | The number of intrusions detected by classtype. |
| Top Classtypes (logged) | The number of intrusions logged by classtype. |
| Top Classtypes (blocked) | The number of intrusions blocked by classtype. |
| Top Categories (all) | The number of intrusions detected by category. |
| Top Categories (logged) | The number of intrusions logged by category. |
| Top Categories (blocked) | The number of intrusions blocked by category. |
| Top Source IP Addresses (all) | The number of intrusions detected by source IP address. |
| Top Source IP Addresses (logged) | The number of intrusions logged by source IP address. |
| Top Source IP Addresses (blocked) | The number of intrusions blocked by source IP address. |
| Top Source Ports (all) | The number of intrusions detected by source port. |
| Top Source Ports (logged) | The number of intrusions logged by source port. |
| Top Source Ports (blocked) | The number of intrusions blocked by source port. |
| Top Destination IP Addresses (all) | The number of intrusions detected by destination IP address. |
| Top Destination IP Addresses (logged) | The number of intrusions logged by destination IP address. |
| Top Destination IP Addresses (blocked) | The number of intrusions blocked by destination IP address. |
| Top Destination Ports (all) | The number of intrusions detected by destination port. |
| Top Destination Ports (logged) | The number of intrusions logged by destination port. |
| Top Destination Ports (blocked) | The number of intrusions blocked by destination port. |
| Top Protocols (all) | The number of intrusions detected by protocol. |
| Top Protocols (logged) | The number of intrusions logged by protocol. |
| Top Protocols (blocked) | The number of intrusions blocked by protocol. |
| All Events | All sessions scanned by Intrusion Prevention. |
| Logged Events | All sessions matching Intrusion Prevention signatures and logged. |
| Blocked Events | All sessions matching Intrusion Prevention signatures are blocked. |
The tables queried to render these reports:
Related Topics
Phish Blocker
Phish Blocker protects users from phishing attacks over email (SMTP). It inspects email for fraudulent emails, also known as phish. A phishing email attempts to acquire sensitive information such as passwords and credit card details by masquerading as a trustworthy person or business in an apparently official electronic communication, such as an email.

Settings
This section reviews the different settings and configuration options available for Phish Blocker.
Status
- Scan SMTP: This enables or disables SMTP scanning.
- Action: The action taken on the message if the Spam Score is high enough.

Reports
The Reports tab provides a view of all reports and events for all traffic handled by Phish Blocker.
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
| Report Entry | Description |
|---|---|
| Phish Blocker Summary | A summary of phish blocking actions for email activity. |
| Email Usage (all) | The amount of scanned, clean, and phish email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (clean) | The amount of clean email over time. |
| Email Usage (phish) | The amount of phish email over time. |
| Phish Ratio | The ratio of phish (true) to ham (false) |
| Top Phish Recipients | The number of email addresses with phish. |
| Top Phish Sender Addresses | The number of IP addresses sending phish. |
| All Email Events | All email sessions are scanned by Phish Blocker. |
| All Phish Events | All email sessions are detected as phishing attempts. |
| Quarantined Events | All email sessions are detected as phishing attempts and quarantined. |
Related Topics
Phish Blocker Reports
The Reports tab provides a view of all reports and events for all traffic handled by Phish Blocker.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
| Report Entry | Description |
|---|---|
| Phish Blocker Summary | A summary of phish blocking actions for email activity. |
| Email Usage (all) | The amount of scanned, clean, and phish email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (clean) | The amount of clean email over time. |
| Email Usage (phish) | The amount of phish email over time. |
| Phish Ratio | The ratio of phish (true) to ham (false) |
| Top Phish Recipients | The number of email addresses with phish. |
| Top Phish Sender Addresses | The number of IP addresses sending phish. |
| All Email Events | All email sessions are scanned by Phish Blocker. |
| All Phish Events | All email sessions are detected as phishing attempts. |
| Quarantined Events | All email sessions are detected as phishing attempts and quarantined. |
Related Topics
Threat Prevention
Threat Prevention blocks potentially harmful traffic from entering or exiting the network. This app can prevent cyber attacks on your servers (e.g. web, VoIP, and email). It is also useful to prevent data loss in case users mistakenly try to connect to a phishing site or other type of malicious host.

- Spam Sources - IP addresses involved in tunneling spam messages through proxy, anomalous SMTP activities, and forum spam activities.
- Windows Exploits - IP addresses participating in the distribution of malware, shell code, rootkits, worms or viruses for Windows platforms.
- Web Attacks - IP addresses using cross site scripting, iFrame injection, SQL injection, cross domain injection, or domain password brute force attacks to target vulnerabilities on a web server.
- Botnets - IP addresses acting as Botnet Command and Control (C&C) centers and infected zombie machines controlled by the C&C servers.
- Denial of Service - The Denial of Service category includes DOS, DDOS, anomalous sync flood, and anomalous traffic detection.
- Scanners - IP addresses involved in unauthorized reconnaissance activities such as probing, host scanning, port scanning and brute force login attempts.
- Phishing - IP addresses hosting phishing sites and sites related to other kinds of fraudulent activities.
- TOR Proxy - IP addresses acting as exit nodes for the TOR Network. Exit nodes are the last point along the proxy chain and make a direct connection to the originator’s intended destination.
- Proxy - IP addresses providing proxy services, including both VPN and open web proxy services.
- Mobile Threats - Denial of service, packet sniffing, address impersonation, and session hijacking
Settings
This section reviews the different settings and configuration options available for Threat Prevention.
Status
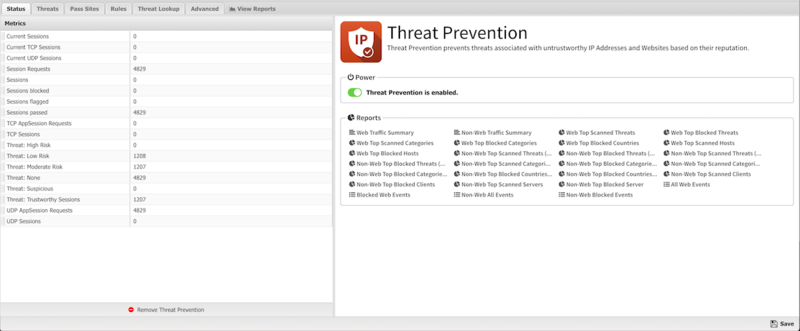
Threats

Pass Sites
Rules
The Rules tab allows you to specify rules to Block, Pass or Flag traffic that crosses the NG Firewall.
The Rules describes how rules work and how they are configured. Threat Prevention uses rules to determine to block/pass the specific session, and if the sessions is flagged. Flagging a session marks it in the logs for reviewing in the event logs or reports, but has no direct effect on the network traffic.
In addition to all the common rule types, there are four that are unique to Threat Prevention, and these can be useful for making exceptions to the general *Reputation Threshold* setting.
Client address reputation: The reputation value of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network.
Server address reputation: The reputation value of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network.
Client address category: The reputation category of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network.
Server address category: The reputation category of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network.
Rule Actions
- Pass: Allows the traffic that matches the rule to flow.
- Block: Blocks the traffic that matches the rule.
Threat Lookup
Threat Results
| Result | Description |
|---|---|
| Address/URL | The IP Address or URL you requested to search. |
| Country | The country where the IP Address or URL originates. |
| Popularity | The popularity of the IP Address or URL is based on the volume of lookups. |
| Recent Threat Count | The amount of recent occurrences that the IP Address or URL has been associated to a threat. |
| Age | The amount of time since the IP Address or URL was first noticed. |
| Reputation | The reputation of the IP Address or URL as determined by the Webroot BrightCloud reputation service. |
| Details | A description of the Reputation value. |
Advanced
The Advanced section enables you to configure additional Threat Prevention options.
Custom block page URL: Set an external location where to redirect users when they are denied access to a web site by Threat Prevention. This is useful if you want to use your own server to process the denial in a different way than the built-in denial options.
Enabling this option will only redirect internal/outbound traffic to your custom page. It will not function to redirect external/inbound traffic (such as Port Forwarded traffic).

Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the ConditionsConditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Web Traffic Summary | A summary of web Threat Prevention actions. |
| Non-Web Traffic Summary | A summary of non-web Threat Prevention actions. |
| Web Top Scanned Threats | The number of web scanned sessions to servers grouped by threat reputation. |
| Web Top Blocked Threats | The number of web blocked sessions to servers grouped by threats reputation. |
| Web Top Scanned Categories | The number of other scanned sessions to servers grouped by threat. |
| Web Top Blocked Categories | The number of web sessions blocked grouped by threat. |
| Web Top Blocked Countries | Top blocked web sessions to servers grouped by country. |
| Web Top Scanned Hosts | The number of web scanned sessions grouped by server. |
| Web Top Blocked Hosts | The number of web blocked session grouped by client. |
| Non-Web Top Scanned Threats (by client) | The number of non-web scanned sessions from clients grouped by threat reputation. |
| Non-Web Top Blocked Threats (by client) | The number of non-web blocked sessions from clients grouped by threat reputation. |
| Non-Web Top Scanned Threats (by server) | The number of non-web scanned sessions to servers grouped by threat reputation. |
| Non-Web Top Blocked Threats (by server) | The number of non-web blocked sessions to servers grouped by threat reputation. |
| Non-Web Top Scanned Categories (by client) | The number of non-web scanned sessions from clients grouped by threat. |
| Non-Web Top Blocked Categories (by client) | The number of non-web blocked sessions from clients grouped by threat. |
| Non-Web Top Scanned Categories (by server) | The number of non-web scanned sessions to servers grouped by threat. |
| Non-Web Top Blocked Categories (by server) | The number of non-web blocked sessions to servers grouped by threat. |
| Non-Web Top Blocked Countries (by client) | Top non-web blocked sessions from clients grouped by country. |
| Non-Web Top Blocked Countries (by server) | Top non-web blocked sessions to servers grouped by threat. |
| Non-Web Top Scanned Clients | The number of non-web scanned session grouped by client. |
| Non-Web Top Blocked Clients | The number of non-web blocked session grouped by client. |
| Non-Web Top Scanned Servers | The number of non-web scanned sessions grouped by server. |
| Non-Web Top Blocked Server | The number of non-web blocked session grouped by client. |
| All Web Events | Shows all scanned web requests. |
| Blocked Web Events | Shows all blocked web requests. |
| Non-Web All Events | All non-web events scanned by Threat Prevention. |
| Non-Web Blocked Events | Non-web events blocked by Threat Prevention. |
Threat Prevention Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports
Reports can be searched and further defined using the time selectors and the Condition window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Web Traffic Summary | A summary of web Threat Prevention actions. |
| Non-Web Traffic Summary | A summary of non-web Threat Prevention actions. |
| Web Top Scanned Threats | The number of web scanned sessions to servers grouped by threat reputation. |
| Web Top Blocked Threats | The number of web blocked sessions to servers grouped by threats reputation. |
| Web Top Scanned Categories | The number of other scanned sessions to servers grouped by threat. |
| Web Top Blocked Categories | The number of web sessions blocked grouped by threat. |
| Web Top Blocked Countries | Top blocked web sessions to servers grouped by country. |
| Web Top Scanned Hosts | The number of web scanned sessions grouped by server. |
| Web Top Blocked Hosts | The number of web blocked session grouped by client. |
| Non-Web Top Scanned Threats (by client) | The number of non-web scanned sessions from clients grouped by threat reputation. |
| Non-Web Top Blocked Threats (by client) | The number of non-web blocked sessions from clients grouped by threat reputation. |
| Non-Web Top Scanned Threats (by server) | The number of non-web scanned sessions to servers grouped by threat reputation. |
| Non-Web Top Blocked Threats (by server) | The number of non-web blocked sessions to servers grouped by threat reputation. |
| Non-Web Top Scanned Categories (by client) | The number of non-web scanned sessions from clients grouped by threat. |
| Non-Web Top Blocked Categories (by client) | The number of non-web blocked sessions from clients grouped by threat. |
| Non-Web Top Scanned Categories (by server) | The number of non-web scanned sessions to servers grouped by threat. |
| Non-Web Top Blocked Categories (by server) | The number of non-web blocked sessions to servers grouped by threat. |
| Non-Web Top Blocked Countries (by client) | Top non-web blocked sessions from clients grouped by country. |
| Non-Web Top Blocked Countries (by server) | Top non-web blocked sessions to servers grouped by threat. |
| Non-Web Top Scanned Clients | The number of non-web scanned session grouped by client. |
| Non-Web Top Blocked Clients | The number of non-web blocked session grouped by client. |
| Non-Web Top Scanned Servers | The number of non-web scanned sessions grouped by server. |
| Non-Web Top Blocked Server | The number of non-web blocked session grouped by client. |
| All Web Events | Shows all scanned web requests. |
| Blocked Web Events | Shows all blocked web requests. |
| Non-Web All Events | All non-web events are scanned by Threat Prevention. |
| Non-Web Blocked Events | Non-web events are blocked by Threat Prevention. |
Virus Blocker
Virus Blocker transparently scans your HTTP, FTP, and SMTP traffic to protect your network from viruses, trojans, and other malware. It scans within archives such as zip, rar, tar, gzip, bzip2 (and more).

As files are downloaded onto the network, Virus Blocker scans downloads using many technologies. Firstly, it will collect metadata about the file and query the NG Firewall threat intelligence database for information about the file based on its fingerprint. Secondly, a local scan using Bitdefender's signature database will be run on the server while the cloud lookup is being performed. Thirdly, a heuristic scan is performed to look for suspicious patterns in executable files. Lastly, dynamic analysis is performed by evaluating code in an emulator and looking for malicious activity. If the download fails any of the above tests, it is considered malware, and the download is blocked.
Settings
This section reviews the different settings and configuration options available for the virus scanners.
Status
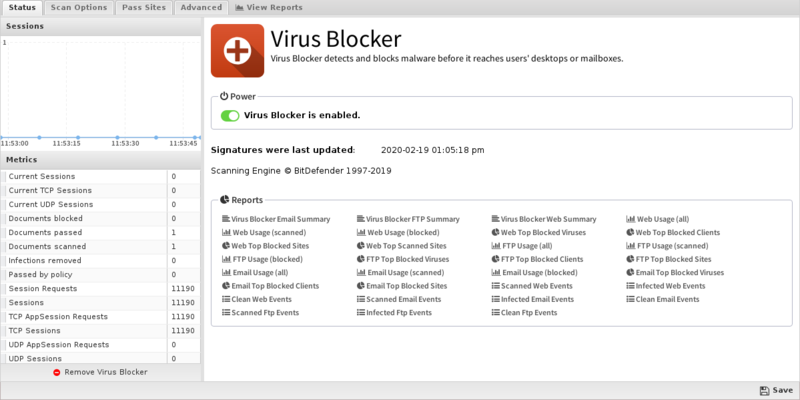
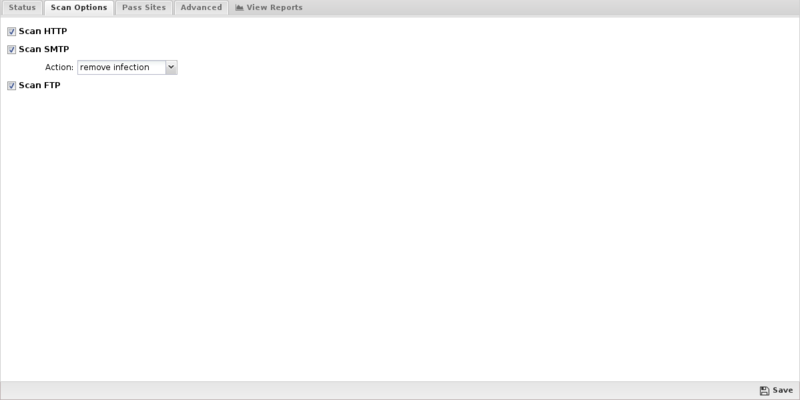
Scan Options
- Scan HTTP: This enables or disables HTTP scanning.
- Scan SMTP: This option enables the scanning of SMTP message attachments.
- Action: The selected action will be taken on a message if a virus is found.
- Setting Action to Remove Infection will remove the infected attachment and wrap the original email for delivery to the intended recipient. If set to Pass Message, the original message will be wrapped and delivered with the attachment intact. In both cases, the subject line is prepended with "[VIRUS]". Block will block the message from being delivered.
- Scan FTP: This enables or disables scanning of FTP downloads.
Figure 16. Virus Blocker Scan Options
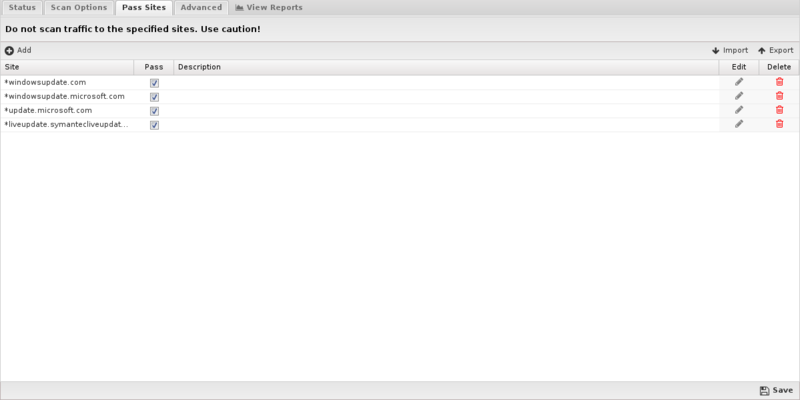
Pass Sites
- HTTP: Match the HTTP Host header.
- FTP: Match the server IP address or domain address (if a reverse DNS address exists).
- Email: Match the client or server IP address or domain address (if a reverse DNS address exists).
Figure 17. Virus Blocker Pass Sites
Advanced
Advanced settings can tune specific behavior of virus blockers.
The first option can enable/disable certain scanners. When a file is scanned by a virus blocker, it is scanned by multiple engines, a local antivirus engine, and the cloud ScoutIQ™ engine.
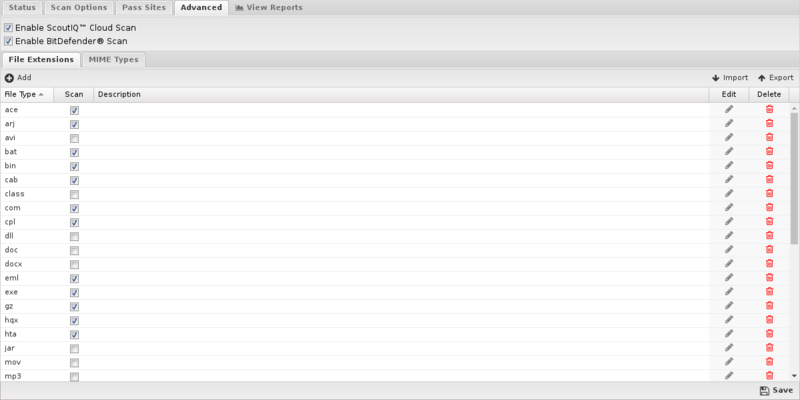
File Extensions
File extensions configure which HTTP files will be scanned. The defaults are the recommended values. However, in some cases, you may want to add or remove certain file extensions.
An understanding of security tradeoffs and pragmatism is essential before changing these settings. Unlike the other URL-based scanning of other apps like Web Filter, Virus Blocker runs in depth analysis of the file, including signatures, heuristics, and emulation. Unlike host-based antivirus, the gateway is a unique resource shared among the whole network, and it has no ability to scan-on-exec as it has no knowledge of what the client plans to execute, unlike host-based antivirus. Scanning is expensive, and turning on certain extensions (like .png files) can cripple the network. Analyzing reports to see how many scans are being done and if those resources are being spent on worthwhile scan resources is a good exercise. It is not uncommon to see millions of scans of some application's update.
MIME Types
Similar to file extensions, this lists the MIME types to be scanned, regardless of extension. The same logic and warnings apply here as well.
Reports
The Reportstab provides a view of all reports and events for all traffic handled by Virus Blocker.
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Virus Blocker Web Summary | A summary of virus blocking actions for web activity. |
| Virus Blocker FTP Summary | A summary of virus blocking actions for FTP activity. |
| Virus Blocker Email Summary | A summary of virus blocking actions for Email activity. |
| Web Usage (all) | The amount of scanned and blocked web requests over time. |
| Web Usage (scanned) | The amount of scanned web requests over time. |
| Web Usage (blocked) | The amount of blocked web requests over time. |
| Web Top Blocked Viruses | The top web virus is blocked. |
| Web Top Blocked Clients | The top web clients by blocked virus count. |
| Web Top Blocked Sites | The top web sites by blocked virus count. |
| Web Top Scanned Sites | The top web sites by scan count. |
| FTP Usage (all) | The amount of scanned and blocked FTP requests over time. |
| FTP Usage (scanned) | The amount of scanned FTP requests over time. |
| FTP Usage (blocked) | The amount of blocked FTP requests over time. |
| FTP Top Blocked Viruses | The number of blocked viruses by FTP activity. |
| FTP Top Blocked Clients | The number of clients with blocked viruses by FTP activity. |
| FTP Top Blocked Sites | The number of clients with blocked viruses by FTP activity. |
| Email Usage (all) | The amount of scanned and blocked email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (blocked) | The amount of blocked email over time. |
| Email Top Blocked Viruses | The number of blocked viruses by Email activity. |
| Email Top Blocked Clients | The number of clients with blocked viruses by Email activity. |
| Email Top Blocked Sites | The number of clients with blocked viruses by Email activity. |
| Scanned Web Events | All HTTP sessions are scanned by Virus Blocker. |
| Infected Web Events | Infected HTTP sessions blocked by Virus Blocker. |
| Clean Web Events | Scanned HTTP sessions marked clean. |
| Scanned Email Events | All email sessions are scanned by Virus Blocker. |
| Infected Email Events | Infected email sessions blocked by Virus Blocker. |
| Clean Email Events | Scanned email sessions are marked clean. |
| Scanned FTP Events | All FTP sessions are scanned by Virus Blocker. |
| Infected FTP Events | Infected FTP sessions are blocked by Virus Blocker. |
| Clean FTP Events | Scanned FTP sessions are marked clean. |
Related Topics
Virus Blocker Reports
The Reports tab provides a view of all reports and events for all traffic handled by Virus Blocker.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Virus Blocker Web Summary | A summary of virus blocking actions for web activity. |
| Virus Blocker FTP Summary | A summary of virus blocking actions for FTP activity. |
| Virus Blocker Email Summary | A summary of virus blocking actions for Email activity. |
| Web Usage (all) | The amount of scanned and blocked web requests over time. |
| Web Usage (scanned) | The amount of scanned web requests over time. |
| Web Usage (blocked) | The amount of blocked web requests over time. |
| Web Top Blocked Viruses | The top web virus is blocked. |
| Web Top Blocked Clients | The top web clients by blocked virus count. |
| Web Top Blocked Sites | The top web sites by blocked virus count. |
| Web Top Scanned Sites | The top web sites by scan count. |
| FTP Usage (all) | The amount of scanned and blocked FTP requests over time. |
| FTP Usage (scanned) | The amount of scanned FTP requests over time. |
| FTP Usage (blocked) | The amount of blocked FTP requests over time. |
| FTP Top Blocked Viruses | The number of blocked viruses by FTP activity. |
| FTP Top Blocked Clients | The number of clients with blocked viruses by FTP activity. |
| FTP Top Blocked Sites | The number of clients with blocked viruses by FTP activity. |
| Email Usage (all) | The amount of scanned and blocked email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (blocked) | The amount of blocked email over time. |
| Email Top Blocked Viruses | The number of blocked viruses by Email activity. |
| Email Top Blocked Clients | The number of clients with blocked viruses by Email activity. |
| Email Top Blocked Sites | The number of clients with blocked viruses by Email activity. |
| Scanned Web Events | All HTTP sessions scanned by Virus Blocker. |
| Infected Web Events | Infected HTTP sessions are blocked by Virus Blocker. |
| Clean Web Events | Scanned HTTP sessions are marked clean. |
| Scanned Email Events | All email sessions scanned by Virus Blocker. |
| Infected Email Events | Infected email sessions are blocked by Virus Blocker. |
| Clean Email Events | Scanned email sessions are marked clean. |
| Scanned FTP Events | All FTP sessions scanned by Virus Blocker. |
| Infected FTP Events | Infected FTP sessions are blocked by Virus Blocker. |
| Clean FTP Events | Scanned FTP sessions are marked clean. |
Related Topics
Virus Blocker Lite
Virus Blocker Lite transparently scans your HTTP, FTP, and SMTP traffic to protect your network from viruses, trojans, and other malware. It scans within archives such as zip, rar, tar, gzip, bzip2 (and more).
Virus Blocker Lite is based on an open-source virus scanner, Clam AV. Clam AV is well-known for its speed and accuracy.
Settings
This section reviews the different settings and configuration options available for the virus scanners.
Status
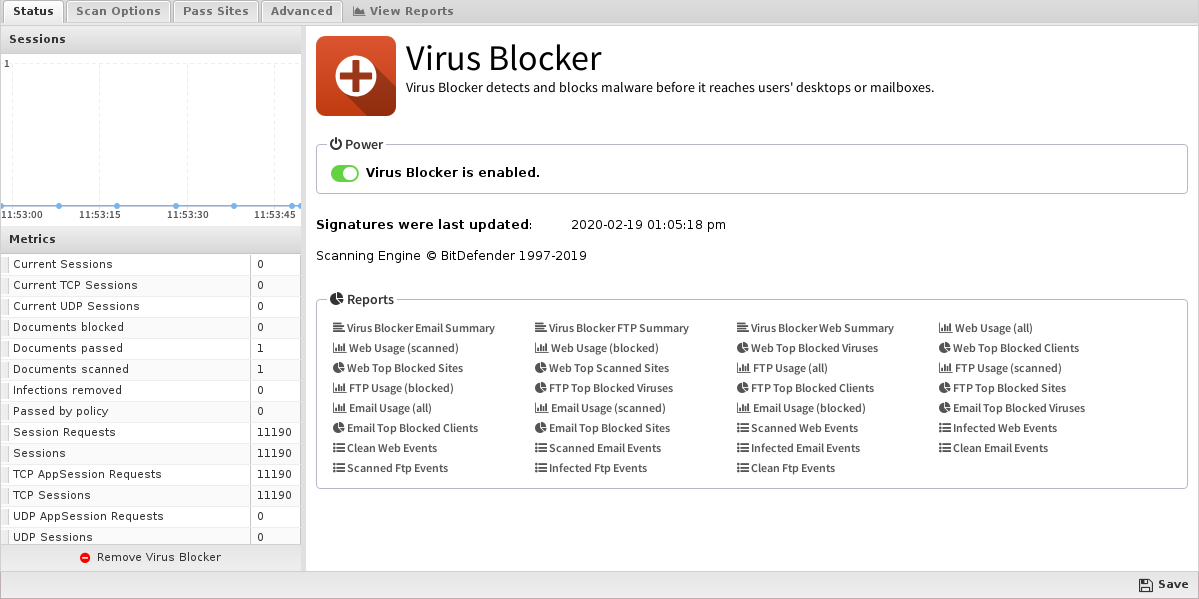
Scan Options
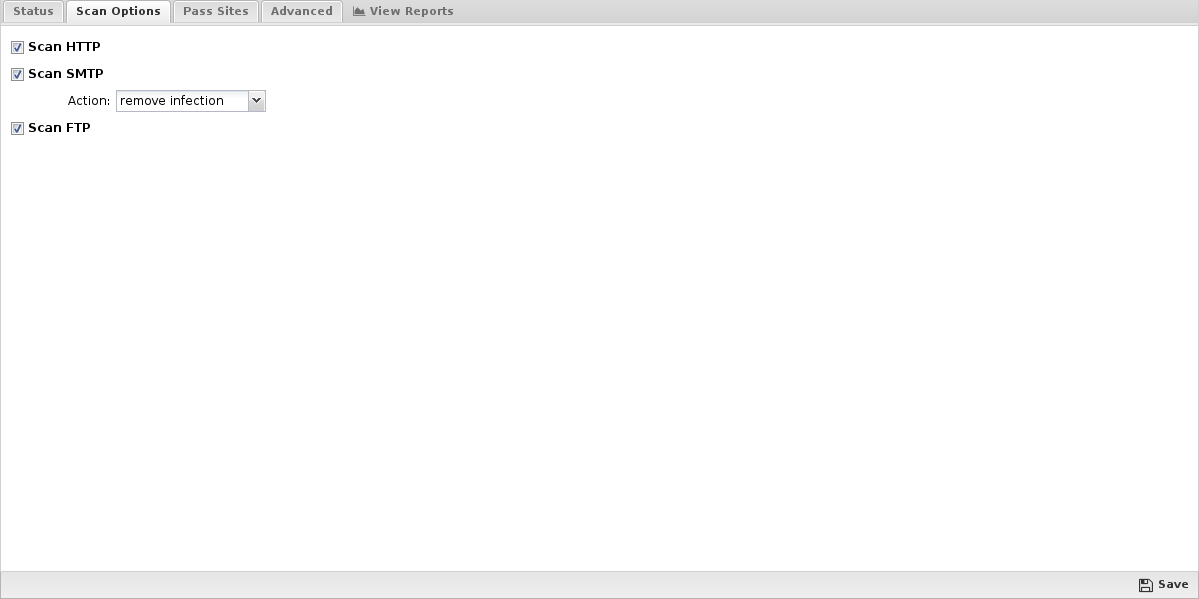
- Scan HTTP: This enables or disables HTTP scanning.
- Scan SMTP: This option enables the scanning of SMTP message attachments.
- Action: The selected action will be taken on a message if a virus is found.
- Setting Action to Remove Infection will remove the infected attachment and wrap the original email for delivery to the intended recipient.
- If set to Pass Message, the original message will be wrapped and delivered with the attachment intact.
Note: In both cases, the subject line is prepended with [VIRUS].
- Block will block the message from being delivered.
- Scan FTP: This enables or disables scanning of FTP downloads.
Pass Sites
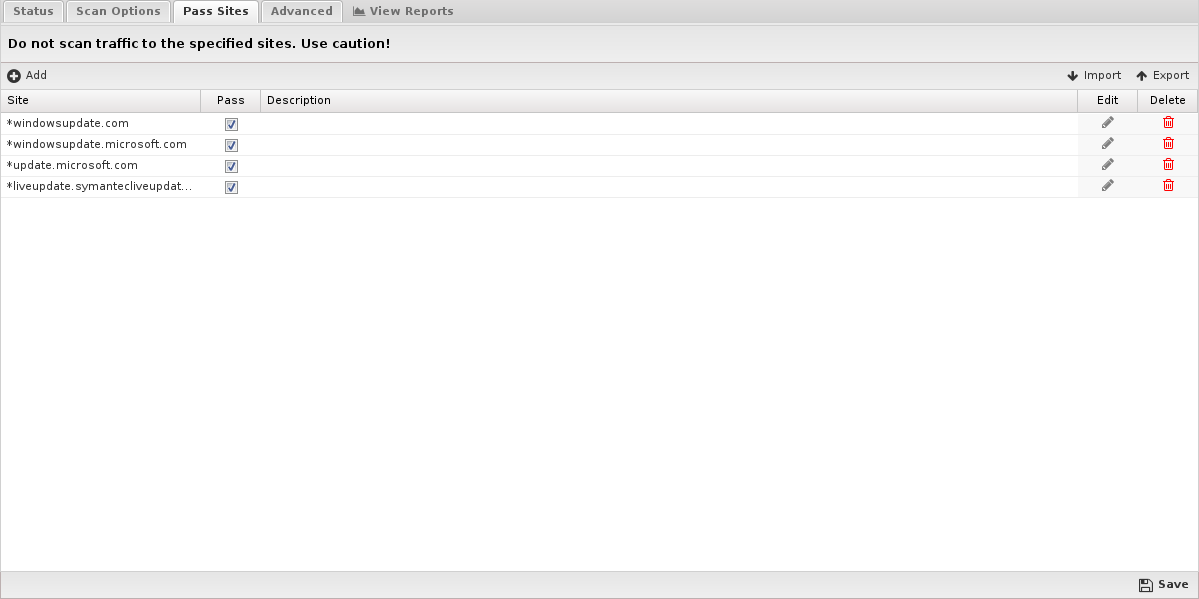
- HTTP: Match the HTTP Host header.
- FTP:Match the server IP address or domain address (if a reverse DNS address exists).
- Email: Match the client or server IP address or domain address (if a reverse DNS address exists).
Advanced
Advanced settings can tune specific behavior of virus blockers.The first option can enable/disable certain scanners. When a file is scanned by a virus blocker, it is scanned by multiple engines, a local antivirus engine, and the cloud ScoutIQ™ engine.

File Extensions
File extensions configure which HTTP files will be scanned. The defaults are the recommended values. However, in some cases, you may want to add or remove certain file extensions.
An understanding of security tradeoffs and pragmatism is essential before changing these settings. Unlike the other URL-based scanning of other apps like Web Filter, Virus Blocker runs in depth analysis of the file, including signatures, heuristics, and emulation. Unlike host-based antivirus, the gateway is a unique resource shared among the whole network. Furthermore, it has no ability to scan-on-exec as it has no knowledge of what the client plans to execute, unlike host-based antivirus. Scanning is expensive, and turning on certain extensions (like .png files) can cripple the network. Analyzing reports to see how many scans are being done and if those resources are being spent on worthwhile scan resources is a good exercise. It is not uncommon to see millions of scans of some application's update.
MIME Types
Similar to file extensions, but this lists the MIME types to be scanned, regardless of extension. The same logic and warnings apply here as well.
Reports
The Reports tab provides a view of all reports and events for all traffic handled by Virus Blocker Lite.
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Virus Blocker Lite Web Summary | A summary of virus blocking actions for web activity. |
| Virus Blocker Lite FTP Summary | A summary of virus blocking actions for FTP activity. |
| Virus Blocker Lite Email Summary | A summary of virus blocking actions for Email activity. |
| Web Usage (all) | The amount of scanned and blocked web requests over time. |
| Web Usage (scanned) | The amount of scanned web requests over time. |
| Web Usage (blocked) | The amount of blocked web requests over time. |
| Web Top Blocked Viruses | The top web virus is blocked. |
| Web Top Blocked Clients | The top web clients by blocked virus count. |
| Web Top Blocked Sites | The top web sites by blocked virus count. |
| Web Top Scanned Sites | The top web sites by scan count. |
| FTP Usage (all) | The amount of scanned and blocked FTP requests over time. |
| FTP Usage (scanned) | The amount of scanned FTP requests over time. |
| FTP Usage (blocked) | The amount of blocked FTP requests over time. |
| FTP Top Blocked Viruses | The number of blocked viruses by FTP activity. |
| FTP Top Blocked Clients | The number of clients with blocked viruses by FTP activity. |
| FTP Top Blocked Sites | The number of clients with blocked viruses by FTP activity. |
| Email Usage (all) | The amount of scanned and blocked email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (blocked) | The amount of blocked email over time. |
| Email Top Blocked Viruses | The number of blocked viruses by Email activity. |
| Email Top Blocked Clients | The number of clients with blocked viruses by Email activity. |
| Email Top Blocked Sites | The number of clients with blocked viruses by Email activity. |
| Scanned Web Events | All HTTP sessions are scanned by Virus Blocker Lite. |
| Infected Web Events | Infected HTTP sessions are blocked by Virus Blocker Lite. |
| Clean Web Events | Scanned HTTP sessions are marked clean. |
| Scanned Email Events | All email sessions are scanned by Virus Blocker Lite. |
| Infected Email Events | Infected email sessions blocked by Virus Blocker Lite. |
| Clean Email Events | Scanned email sessions marked clean. |
| Scanned FTP Events | All FTP sessions scanned by Virus Blocker Lite. |
| Infected FTP Events | Infected FTP sessions blocked by Virus Blocker Lite. |
| Clean FTP Events | Scanned FTP sessions marked clean. |
The tables queried to render these reports:
Related Topics
Virus Blocker Lite Reports
The Reports tab provides a view of all reports and events for all traffic handled by Virus Blocker Lite.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
| Report Entry | Description |
|---|---|
| Virus Blocker Lite Web Summary | A summary of virus blocking actions for web activity. |
| Virus Blocker Lite FTP Summary | A summary of virus blocking actions for FTP activity. |
| Virus Blocker Lite Email Summary | A summary of virus blocking actions for Email activity. |
| Web Usage (all) | The amount of scanned and blocked web requests over time. |
| Web Usage (scanned) | The amount of scanned web requests over time. |
| Web Usage (blocked) | The amount of blocked web requests over time. |
| Web Top Blocked Viruses | The top web virus is blocked. |
| Web Top Blocked Clients | The top web clients by blocked virus count. |
| Web Top Blocked Sites | The top web sites by blocked virus count. |
| Web Top Scanned Sites | The top web sites by scan count. |
| FTP Usage (all) | The amount of scanned and blocked FTP requests over time. |
| FTP Usage (scanned) | The amount of scanned FTP requests over time. |
| FTP Usage (blocked) | The amount of blocked FTP requests over time. |
| FTP Top Blocked Viruses | The number of clients with blocked viruses by FTP activity. |
| FTP Top Blocked Clients | The number of clients with blocked viruses by FTP activity. |
| FTP Top Blocked Sites | The number of clients with blocked viruses by FTP activity. |
| Email Usage (all) | The amount of scanned and blocked email over time. |
| Email Usage (scanned) | The amount of scanned email over time. |
| Email Usage (blocked) | The amount of blocked email over time. |
| Email Top Blocked Viruses | The number of blocked viruses by Email activity. |
| Email Top Blocked Clients | The number of clients with blocked viruses by Email activity. |
| Email Top Blocked Sites | The number of clients with blocked viruses by Email activity. |
| Scanned Web Events | All HTTP sessions are scanned by Virus Blocker Lite. |
| Infected Web Events | Infected HTTP sessions are blocked by Virus Blocker Lite. |
| Clean Web Events | Scanned HTTP sessions are marked clean. |
| Scanned Email Events | All email sessions are scanned by Virus Blocker Lite. |
| Infected Email Events | Infected email sessions are blocked by Virus Blocker Lite. |
| Clean Email Events | Scanned email sessions are marked clean. |
| Scanned FTP Events | All FTP sessions are scanned by Virus Blocker Lite. |
| Infected FTP Events | Infected FTP sessions are blocked by Virus Blocker Lite. |
| Clean FTP Events | Scanned FTP sessions are marked clean. |
The tables queried to render these reports:
Related Topics
Virus Blockers Common
This section reviews the different settings and configuration options available for the virus scanners.
Status
This displays the current status and some statistics.

Scan Options
Scan options configure what network traffic and content to scan.
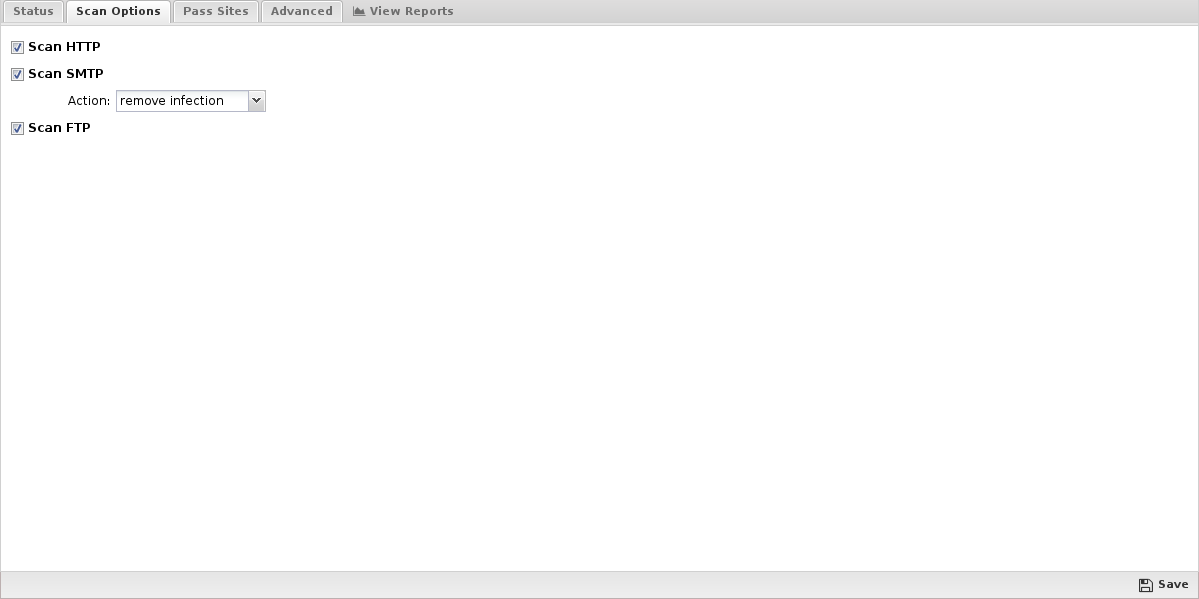
- Scan HTTP: This enables or disables HTTP scanning.
- Scan SMTP: This option enables the scanning of SMTP message attachments.
- Action: The selected action will be taken on a message if a virus is found.
Setting Action to Remove Infection will remove the infected attachment and wrap the original email for delivery to the intended recipient. If set to Pass Message, the original message will be wrapped and delivered with the attachment intact. In both cases, the subject line is prepended with "[VIRUS]". Block will block the message from being delivered.
- Scan FTP: This enables or disables scanning of FTP downloads.
Pass Sites
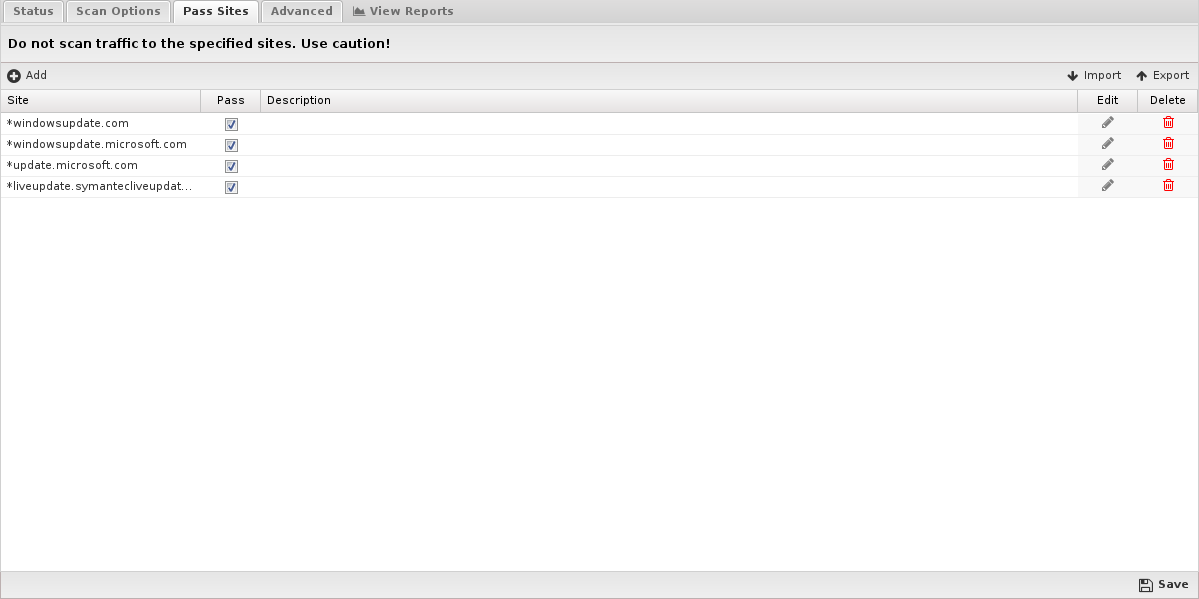
For each protocol, the behavior is as follows:
- HTTP: Match the HTTP Host header.
- FTP: Match the server IP address or domain address (if a reverse DNS address exists).
- Email: Match the client or server IP address or domain address (if a reverse DNS address exists).
Advanced
Advanced settings can tune specific behavior of virus blockers.
The first option can enable/disable certain scanners. When a file is scanned by a virus blocker, it is scanned by multiple engines, a local antivirus engine, and the cloud ScoutIQ™ engine.
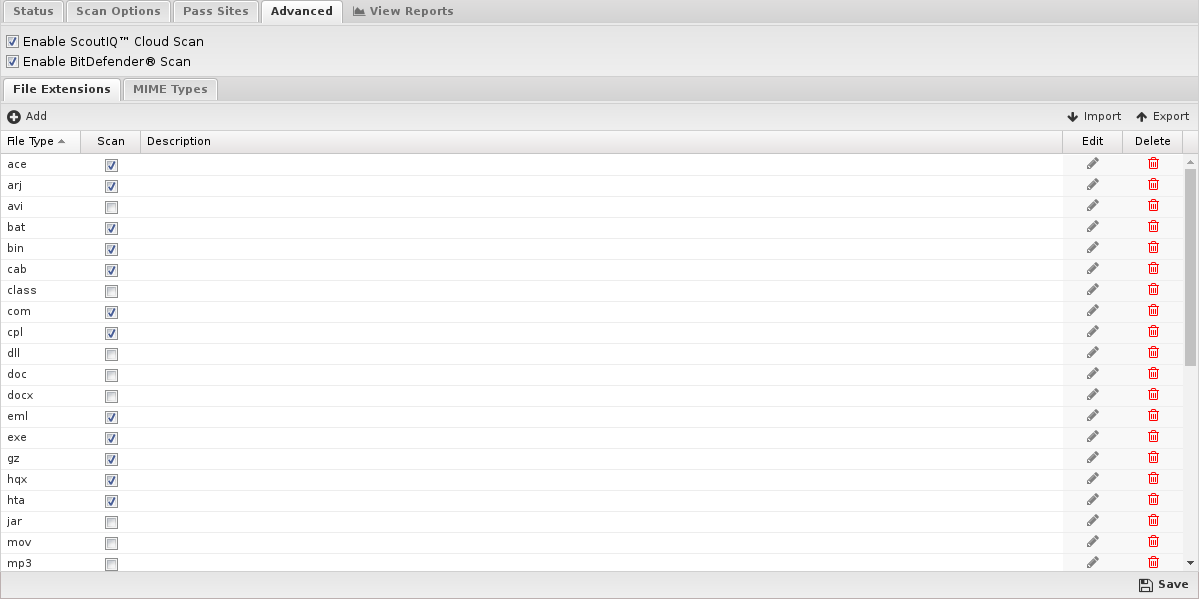
File Extensions
File extensions configure which HTTP files will be scanned. The defaults are the recommended values. However, in some cases, you may want to add or remove certain file extensions.
An understanding of security tradeoffs and pragmatism is essential before changing these settings. Unlike the other URL-based scanning of other apps like Web Filter, Virus Blocker runs in depth analysis of the file, including signatures, heuristics, and emulation. Unlike host-based antivirus, the gateway is a unique resource shared among the whole network, andit has no ability to scan-on-exec as it has no knowledge of what the client plans to execute, unlike host-based antivirus. Scanning is expensive, and turning on certain extensions (like .png files) can cripple the network. Analyzing reports to see how many scans are being done and if those resources are being spent on worthwhile scan resources is a good exercise. It is not uncommon to see millions of scans of some application's update.
MIME Types
Similar to file extensions, but this lists the MIME types to be scanned, regardless of extension. The same logic and warnings apply here as well.
