SSID Settings
You can configure SSID settings on the Configure > WiFi > SSID tab.
SSID Configuration Tabs
For each SSID, there are nine functional settings: Basic, Security, Network, Access Control, Analytics, Captive Portal, RF Optimization, SSID Scheduling, and Traffic Shaping and QoS.
Of these, the first three — Basic, Security, and Network — are essential to an SSID, i.e., you must configure these settings before you can save an SSID and turn it on. You can configure the remaining tabs if you need to, otherwise they assume default values.
You can add up to 8 SSIDs on the 2.4GHz band and up to 8 SSIDs on the 5GHz band in each folder.
Add New SSID
To add an SSID, go to and click Add SSID. Enter the details in each tab sequentially. You must configure at least the Basic, Security, and Network tabs before you can save the SSID. To configure any of the other SSID tabs, click the three-dot menu next, which is typically next to the Network tab, and select the tab you want to configure.
- SSID Basic Settings
- SSID Security Settings
- SSID Network Settings
- SSID Access Control
- SSID Analytics
- SSID Captive Portal
- SSID RF Optimization
- SSID WiFi 7 Setting - Multi-Link Operation
- SSID Traffic Shaping and QoS
- Hotspot 2.0
- SSID Scheduling
- Managing SSID
- Location Based VLAN Mapping
- Customize SSID Attributes for Location-Specific Overrides
SSID Basic Settings
The Basic tab is the first of the three mandatory SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it on.
- SSID Profile Name: Typically, this is the same as the SSID Name. It is primarily meant to distinguish between duplicate SSIDs. So, duplicate SSIDs at the same location have different profile names. For example, if you duplicate "ABC Corp" at the same location, then the new SSID name will be "ABC Corp" but its profile name will be "Copy of ABC Corp(1)". You can modify the profile name.
- SSID Type: This could be a Public or a Guest SSID. If you select Guest, then on the UI you can see the Captive Portal tab next to the Network tab, since Guest SSIDs typically use captive portal logins.
- Hide SSID: If you select this, the SSID will be hidden, i.e., it will not be broadcast on the wireless link.
- Include AP Name in Beacon: Select this option to include the name of the access point (AP) in the beacon.
Configure SSID Basic Settings
The Basic tab is the first of the three SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it ON.
- Enter the name you want to assign the SSID in Enter SSID Name.The Enter Profile Name field gets populated automatically with the SSID name, except if this is a duplicate SSID at the same location as the original.
- Select if you want this to be a Private SSID or a Guest SSID.
- Select Hide SSID if you do not want this SSID to be broadcast.
- The next step depends on whether you are adding a new SSID or updating an existing one:
- If you are adding a new SSID, click Next to move to the Security tab.
- If you are updating an existing SSID, click Save or Save & Turn SSID On. In this case, an "SSID updated successfully" message appears.
SSID Security Settings
The Security tab is the second of the three SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it on.
Select Security Level for Associations
- Open: Open means no security settings are to be applied. This is the default security setting.
- Enhanced Open (OWE): OWE (Enhanced Open), as the name suggests, is an enhancement to open networks. It provides data security for open networks. Open SSID networks are widely used in coffee shops, shopping malls, airport lounges, and enterprise guest networks, and OWE offers data security to your clients with encrypted sessions.
- WPA2: The WPA2 security protocol was created to fix the vulnerabilities of WPA and therefore it is more robust than WPA. It fully implements the IEEE 802.11i standard. You can use WPA2 with PSK (Pre-Shared Key), UPSK(Unique PSKs), Group PSKs, or 802.1x, i.e., RADIUS-based authentication.
- WPA / WPA2 Mixed Mode: This stands for a mix of the WPA and WPA2 protocols. You can use WPA with PSK (Pre-Shared Key), UPSK(Unique PSKs), Group PSKs or 802.1x, i.e., RADIUS-based authentication.
- WPA3: The WPA3 security protocol mitigates the vulnerabilities of WPA2. You can use WPA3 Personal or WPA3 Enterprise.
WPA3 Personal is typically meant for home users. Its robust password-based authentication and 128-bit data AES encryption provides stronger security and protection than WPA2. WPA3 Personal provides protection against attacks such as offline dictionary attacks that attempt to guess passwords. WPA3 Enterprise has an option to use 192-bit encryption and it is meant for enterprises and office networks where the need for data security and protection is higher.
Management Frame Protection is mandatory for both WPA3 Enterprise and WPA3 Personal.
- WPA2/WPA3 Mixed Mode: This stands for a mix of WPA2 and WPA3 protocols. If your SSID operates in WPA2/WPA3 Mixed Mode, then WPA2-only clients can also connect with the same SSID along with WPA3-supported clients. In this mode, WPA3 clients use WPA3 Personal.
Note: 802.11w and 802.11r are supported in WPA2, WPA3, and WPA2/WPA3 Mixed Mode. WPA/WPA2 Mixed Mode does not support 802.11w and 802.11r.
RADIUS Settings
See 802.1X or RADIUS Settings for details.
Deny Locally-Administered MAC Addresses
You can prevent clients using locally-administered MAC addresses from accessing your network. You can ensure that only clients using their device’s globally unique MAC addresses are able to connect to the network. By making sure that only devices with globally unique MAC addresses connect to the network, you can mitigate potential security threats associated with spoofing or unauthorized access by having control over device identification.
802.11w
802.11w offers Management Frame Protection (MFP). MFP is an additional security mechanism that protects the De-authentication, Disassociation and Robust Action management frames and prevents some spoofing attacks. The Integrity Group Temporal Key (IGTK) is used to provide integrity check for multicast management action frames, while the Pairwise Transient Key (PTK) is used to encrypt and protect unicast management action frames. The Group Management Cipher Suite is the combination of security and encryption algorithms used to protect mangement frames. Arista uses the AES-128-CMAC algorithm, so that is what is selected by default.
Association frames are not protected as they need to be open for a client to establish an association with an AP. To make sure that a client Association Request is not spoofed, the AP sends a Security Association (SA) query to a client requesting association. A genuine client responds to the protected frames. The SA Query Max Timeout is the time, in seconds, for which the AP waits for a client to respond to an SA query. If the AP receives no response within this period, it ignores the client. Since clients that spoof Association Requests don't respond, the AP rejects them. The SA Query Retry Timeout is the time, in milliseconds, for which a client can request to associate with the AP after the SA Query max timeout.
Configure SSID Security Settings
The Security tab is the second of the three SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it ON.
- Go to the Security tab under
- Select Security Level for Associations for this SSID.
- If you select Open, there is nothing more you need to do for security. Click Next to move to the Network tab if you are adding a new SSID, or click Save or Save and Turn SSID On if you are updating an existing SSID.
- If you select OWE (Enhanced Open), there is nothing more you need to do for security. Click Next to move to the Network tab if you are adding a new SSID, or click Save or Save and Turn SSID On if you are updating an existing SSID.
- If you select WPA2, you need to select either PSK, UPSK, or 802.1X.
- If you selected WPA2 and PSK, Enter a Passphrase. You can also enable Group PSK. For information on Group PSKs, refer to Group PSKs.
- If you select WPA2 and 802.1X or WPA2 and UPSK, you need to enter the RADIUS Settings. RADIUS settings include:
- The RADIUS servers you want to use as Authentication Server and Accounting Server. You can add up to four RADIUS servers. One is the primary server and the other three are fallback or additional servers. If the Primary server is not reachable, the AP tries to reach the second server defined on the UI. If the second RADIUS server is not reachable, then the AP tries to reach the third server and so on. The AP follows the same order of hierarchy for the additional RADIUS servers that you define on the UI.
Note: If you have not yet defined a RADIUS profile to choose as your Authentication or Accounting server, you can do so by clicking Add / Edit. This opens a RADIUS Profile window on the right pane. You can create the RADIUS profile and return to security settings. See Configure RADIUS Profile for details.
- Enable Send DHCP Options and HTTP User Agent if you want the AP to send client profiling attributes such as DHCP Options 12, 15, and 60, and HTTP User Agent to the RADIUS server in the RADIUS accounting packets.
- The Called Station / NAS ID, IDs that the AP or a Network Access Server (NAS) send the RADIUS server.
Note: No two SSIDs on the same AP should use the same NAS ID.
- The Retry Parameters that control how often the AP attempts to authenticate with RADIUS.
- Fast Handoff Support which saves clients some authentication time when the roam from one AP to another.
- Dynamic VLANs to enable RADIUS-based assignment of VLANs. Select VLAN IDs and manually enter the RADIUS VLANs. Select Auto VLAN to dynamically assign VLANS to clients and send the VLAN to the access point (AP) when the client connects. For more information on creating dynamic VLANs from RADIUS server, refer to Create Dynamic VLANS from RADIUS Server.
- Change of Authorization (CoA) to change a client's authorization. For example, you can use CoA to assign VLANs to a user or to assign roles to a user when implementing Role-Based Access Control.
Note: For CoA, open Port 3799 on your firewall from the RADIUS server to the AP.
- Enable Prefer Primary RADIUS Server if you want the authentication to fall back to the primary RADIUS server once it comes back up after a failover. This helps if, for example, your secondary RADIUS servers have lower capacity than the primary servers. Another example where this helps is when enterprises use two data centers, each one configured as the “secondary” of the other. You would then want the authentication to fall back to the primary or “home” data center RADIUS server once it comes back up.
Once an AP detects a failover to the secondary RADIUS server, it waits for the Dead Time interval before falling back to the primary. This ensures that fallback does not happen too soon, allowing time for the primary server to stabilize if it had been flapping.
- Select the type of Framed IPv6 Address that you want the RADIUS Accounting message to report to an authenticated Wi-Fi client. The choice depends on whether your network uses solicited IPv6 addresses or unsolicited ones obtained via SLAAC (Stateless Address Autoconfiguration). For solicited IPv6 addresses, select Report Full IPv6 Address; for the unsolicited case, select Report Only IPv6 Prefix.
- Enable Prefer Primary RADIUS Server if you want the authentication to fall back to the primary RADIUS server once it comes back up after a failover. This helps if, for example, your secondary RADIUS servers have lower capacity than the primary servers. Another example where this helps is when enterprises use two data centers, each one configured as the “secondary” of the other. You would then want the authentication to fall back to the primary or “home” data center RADIUS server once it comes back up.
Once an AP detects a failover to the secondary RADIUS server, it waits for the Dead Time interval before falling back to the primary. This ensures that fallback does not happen too soon, allowing time for the primary server to stabilize if it had been flapping.
- The RADIUS servers you want to use as Authentication Server and Accounting Server. You can add up to four RADIUS servers. One is the primary server and the other three are fallback or additional servers. If the Primary server is not reachable, the AP tries to reach the second server defined on the UI. If the second RADIUS server is not reachable, then the AP tries to reach the third server and so on. The AP follows the same order of hierarchy for the additional RADIUS servers that you define on the UI.
- If you select WPA2, you can configure 802.11w for Management Frame Protection (MFP). If you select PSK, you can enable Group PSK. To enable Group PSK, select Group PSK and enter the passphrase. If you select UPSK, you must configure the RADIUS server.
Note: 802.11w is not supported in Open, OWE, and WPA/WPA2 Mixed Mode security levels.
- If you select WPA/WPA2 Mixed Mode, you need to select PSK, UPSK, or 802.1X. If you select PSK, you can enable Group PSK. To enable Group PSK, select Group PSK and enter the passphrase. You can then proceed in exactly the same manner as when you select WPA2.
- If you select WPA3, you need to select either WPA3 Personal, UPSK, or WPA3 Enterprise. WPA3 Personal uses Simultaneous Authentication of Equals (SAE) to secure data and it is meant for home users. WPA3 Enterprise is meant for organizations as it includes an option to add 192-bit security for data security. If you select WPA3 or WPA3 Transition Mode, you can select one of the following SAE Mechanism for PWE Derivation:
- Hunting-and-Pecking only
- Hash-to-Element only
- Hunting-and-Pecking and Hash-to-Element
- Select Deny Locally-Administered MAC Addresses to prevent clients using locally-administered MAC addresses from accessing your network.
- The next step depends on whether you are adding a new SSID or updating an existing one:
- If you are adding a new SSID, click Next to move to the Network tab.
- If you are updating an existing SSID, click Save or Save & Turn SSID On. In this case, an "SSID updated successfully" message appears.
Group PSKs
- An enterprise might require IoT devices to connect to the Wi-Fi network. Network administrators often want to use the same SSID for different client device categories, but assign different VLANs or access lists to them—for example, they might want to map printers and video cameras to separate VLANs. IoT devices typically do not support 802.1X-based authentication methods that enterprises use to segment clients into separate VLANs. With Group PSKs, you can configure the same SSID with different PSKs: one PSK for printers, another one for video cameras, and so on. You can also assign roles to each Group PSK.
- A small branch office or a retail establishment might want to segment users on the same SSID by department (HR, finance, legal, etc.). Such establishments typically do not have 802.1X infrastructure; they can use Group PSKs to segment users.
Limitations
- Group PSKs are supported for only the following security methods:
- WPA2 with PSK and
- WPA/WPA2 Mixed Mode with PSK.
- Secondary Authentication (e.g., RADIUS MAC Authentication or Google Authentication) is not supported for Group PSKs.
- Captive Portal is not supported with Group PSKs.
- Group PSKs are not supported for SSIDs using VPN (L3 tunnel) or NAT.
Unique PSKs
UPSKs allow users to connect to the same SSID using a unique PSK which is user specific. UPSK provides added security as compared to single PSK because single PSKs are easily compromised.
- Increased security by using individual PSKs per student and MAC authentication. When a user leaves the organization, administrators can deactivate their account so their PSK will no longer be valid to connect to the university network.
- Easily managing a group of devices. For example, consider an enterprise having multiple categories of IOT devices such as cameras and printers. The administrator can assign different PSK to different categories of devices and manage the group of devices easily.
- Easily managing a group of devices. For example, consider an enterprise having multiple categories of IOT devices such as cameras and printers. The administrator can assign different PSK to different categories of devices and manage the group of devices easily.
- Monitoring of devices. One user may have multiple devices. In such cases, RADIUS assigns each device a specific PSK making it unique. Network administrators can easily track individual devices.
UPSK New User Onboarding Flow
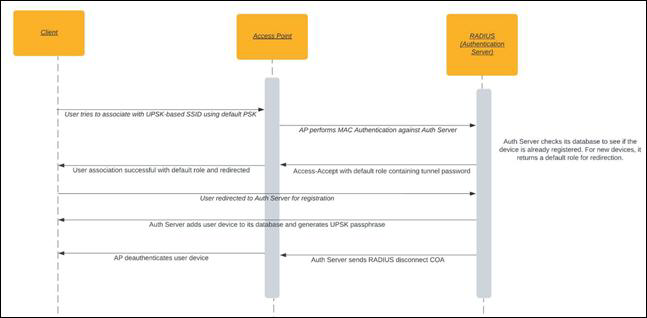
- New user logs in and connects its clients using the default PSK (shared by admin).
- Access Point (AP) initiates the MAC-Auth with the RADIUS server. As the MAC address is not registered, the RADIUS server assigns a default role to the client.
- Client gets redirected to a portal for registration.
- After registration, the user gets an auto-generated or admin-configured Unique PSK. The user can use this UPSK to connect other devices after MAC registration in the RADIUS server. This PSK remains unique to that user.
- Once the device is registered, the RADIUS server can now send COA-Disconnect to the client.
UPSK Registered User Onboarding Flow
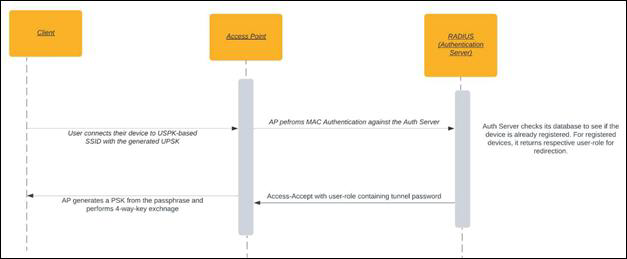
- The user connects the registered device to the UPSK enabled SSID and enters the assigned PSK.
- AP initiates the MAC-Auth with the RADIUS server. As the MAC address is already registered, RADIUS server sends an access-accept containing RADIUS Tunnel-Password attribute, which carries the assigned PSK.
- Attribute Name: Tunnel-Password
- Attribute ID: 69
- AP matches the hash of the PSK entered by the user and the hash of the PSK received in the access-accept packet. If it's a correct match, the user device is onboarded.
Use Case
Consider a new student trying to connect to the university network. The student first connects to the SSID using the default credentials provided by the network administrator. The student is connected to the network using the default role and is redirected to the registration portal. The student can then provide their device information and register their device. The registration portal assigns a user-specific PSK and the client is disconnected. Post registration, the student can log into the network using the unique PSK assigned to them.
Unique-PSK User Private Network and Identity Lookup
Along with UPSK, you can also enable User Private Netwtoks and Identity Lookup.
UPSK User Private Networks
You can enable UPSK User Private Networks option to generate UPSK with isolation between multiple users’ devices. After you enable this setting, User-A’s devices onboarded using UPSK-A cannot reach or communicate with devices onboarded using User-B’s UPSK-B.
This setting further enhances the security provided by UPSK.
UPSK Identity Lookup
You can enable UPSK Identity Lookup to auto-register a new client using the generated UPSK Password. This feature lets you onboard a new client without the need of manual intervention.
Enabling UPSK
- Go to
- Under the Security tab, select your security level for associations.
Note: UPSK is unavailable for Open, OWE, and Hotspot 2.0 OSEN security levels.
- Select the UPSK radio button.
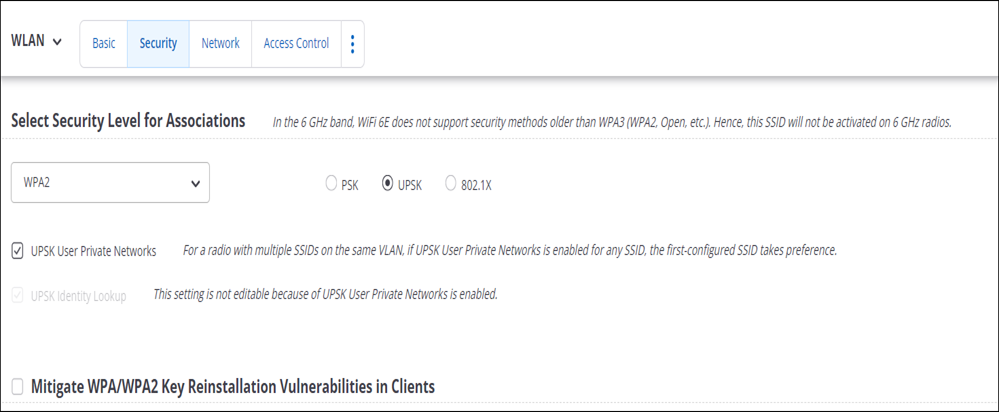
- Select UPSK User Private Network to enable isolation between client devices.
Note:For WPA2 and WPA/WPA2 Mixed Mode, UPSK Identity Lookup is auto-enabled. For WPA3 and WPA3 Transition Mode, you cannot enable UPSK Identity Lookup.
-
Under the Access Control tab, provide details for the RADIUS Settings.
- Save the settings.
- AP Platforms - WiFi 6 and above
- Supported Security Methods
- WPA2
- WPA3
- WPA/WPA2 Mixed
- WPA3 Transition mode
Note: For WPA3 and WPA3 Transition Mode, you cannot enable UPSK Identity Lookup.
Local Authentication of Wireless Clients
Local Authentication (also known as authentication survivability) is the ability of access points (AP) to authenticate and onboard clients to the network using CA certificates through the integrated EAP server of the AP. Use Local Authentication when the RADIUS servers are not reachable to authenticate the clients. It is typically a temporary authentication mechanism; avoid using it as a primary authentication.
When the AP cannot reach the RADIUS server, it goes into authentication survivability mode. While the AP is in this mode, if any client tries to connect to the AP, the AP uses certificate-based authentication to on-board the AP and connect to the network. As soon as the RADIUS servers are reachable, the client gets reauthenticated by the RADIUS server.
Workflow
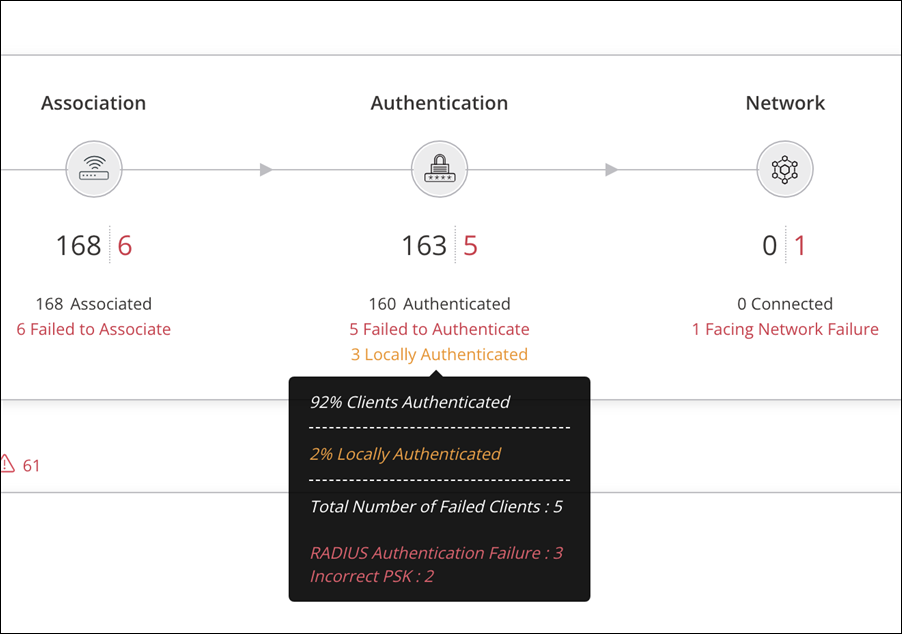
You can define up to four RADIUS servers in CloudVision Cognitive Unified Edge (CV-CUE) for 802.1X authentication. When the Primary RADIUS server computer is unreachable, the AP retries connecting to the Primary RADIUS server a certain number of times before switching to the next RADIUS server. When all the RADIUS servers are unreachable, the AP falls back to the local authentication mode. While the AP is in this mode, if any client tries to connect to the AP, the AP uses certificate-based authentication to on-board the client and connect to the network. Such clients are called locally authenticated clients.
The AP remains in the local authentication mode for the duration defined in the Dead Time configuration. After the dead time is over, the AP repeats the cycle of connecting to the RADIUS servers. If it successfully connects to the RADIUS server, it disconnects all locally authenticated clients. The clients reauthenticate using the RADIUS server.
Enable Authentication Survivability
- Go to or edit an existing SSID.
- Click the Security tab and navigate to the Local Authentication section.
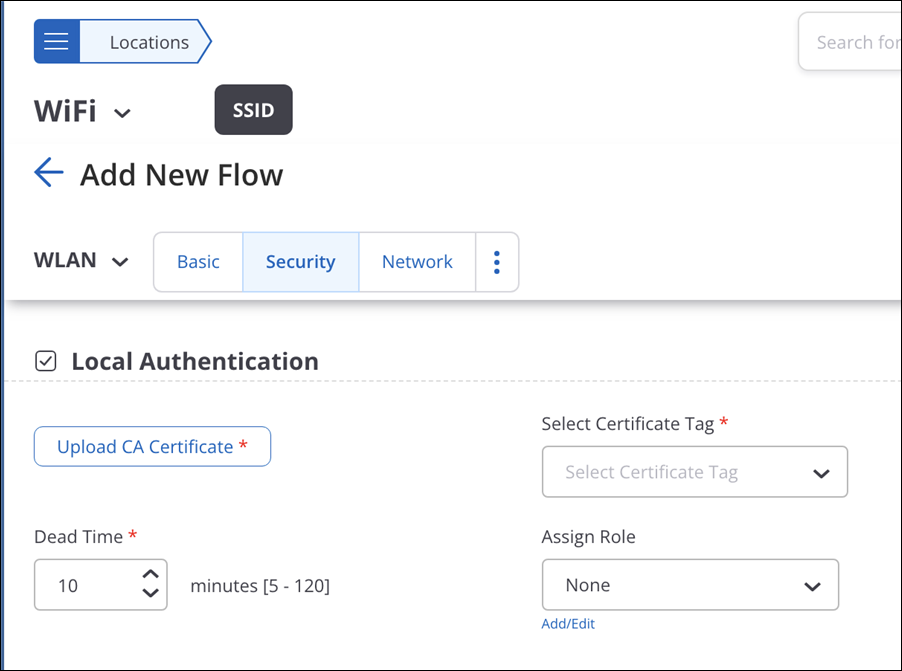
- Select Local Authentication and provide the CA Certificate.
- Upload the CA Certificate and then select a certificate tag.
- Select the dead time. Dead Time indicates the duration for which the AP remains in the Local Authentication mode before connecting to the RADIUS server.
- (Optional) Select a role for the clients from Assign Role for locally authenticated clients
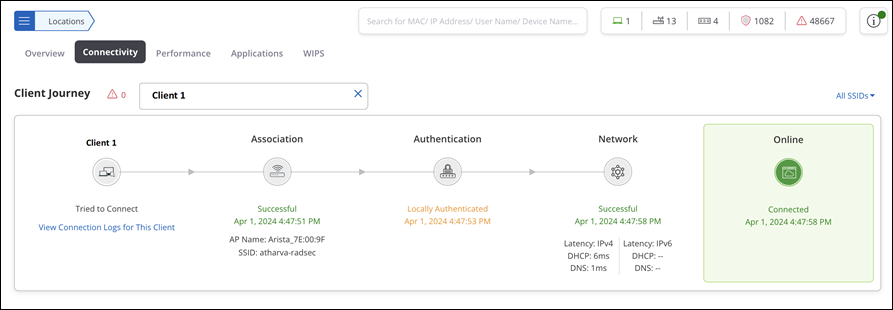
- Connectivity Dashboard — Client Journey
- Client Details — Client Journey
- Client Listing: Locally Authenticated column in client listing (MONITOR > WiFi > Clients)
- AP Listing: Locally Authenticated column in AP listing (MONITOR > WiFi > Access Points)
Configure and Monitor Alerts
You can configure and monitor alerts related to Local Authentication by navigating to . For more information, refer to Configure System Alerts

SSID RADIUS Pooling
RADIUS Pooling lets you assign a pre-defined list of RADIUS Servers that Access Points (AP) can use to authenticate, authorize, and maintain clients' accounts. It offers better load-balancing capabilities and improved scalability.
You do not have to specify the order of the RADIUS servers as Primary or Secondary. Every AP randomly chooses the RADIUS servers from the pool, and then independently decides the sequence of the RADIUS servers and follows the order. Two APs sharing the same RADIUS pool may not share the same order for the RADIUS servers. APs automatically distribute the client load based on an intelligent algorithm.
Also, there is no separate list of RADIUS servers for Accounting and Authentication. The AP uses the same active RADIUS for accounting and authentication. If the AP doesn’t receive any Accounting messages from the active RADIUS server, it switches to the next RADIUS in the order. If all the RADIUS servers are disconnected and Local Authentication (Authentication Survivability) is enabled, the AP goes into the Local Authentication mode.
RADIUS Pooling is an SSID setting in the Security and Access Control tabs.
Configure RADIUS Pooling
Follow these steps to configure VLAN Pooling in SSID settings:
- Go to CONFIGURE > WiFi > Add SSID.
- Select the Security tab and select any 802.1X Authentication security level association, such as WPA3, WPA3 transition Mode, or WPA2.
- Select Enable RADIUS Pooling and select a maximum of four RADIUS servers from the drop-down list. If you have not configured any RADIUS servers, they won’t be visible in the drop-down list.
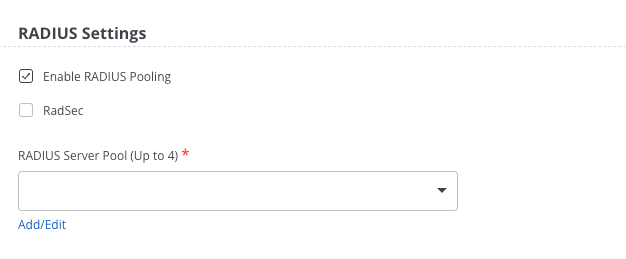
- (Optional) Click Add/Edit to add RADIUS servers or edit existing RADIUS servers.
- Save the settings.
Note: On enabling RadSec, only the RadSec-capable RADIUS servers will be displayed in the drop-down list. On disabling RadSec, the RadSec-capable RADIUS servers are not displayed in the drop-down list.
Event Logs
When the AP decides the order of the RADIUS server, it generates an event log that displays the order of the RADIUS Server. You can view the event logs from TROUBLESHOOT > Event Logs > Access Points.
SSID Network Settings
The Network tab is the third of the three SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it ON.
You must enter the default VLAN ID for this SSID.
You can have access points on this SSID operate in bridged, NAT or Tunneled modes.
Bridged
Use a bridged network when you want an AP and clients associated with the AP to be on the same subnet.
NAT
To configure NAT, you need to enter the Start IP Address, theEnd IP Address, and the Subnet Mask. Together, these define the IP pool from which the AP will assign IP addresses to clients. The Local IP Address is the IP address of the AP on the wireless side, i.e., the client-facing IP address. It serves as the gateway for associated clients. Upon successful association, wireless clients get their DNS information from the list of IP addresses you have entered in the DNS Servers field. You must enter at least one DNS server IP address. You can enter up to six DNS server IP addresses. The Lease Time is the DHCP lease time in minutes, after which the IP allocated to the client expires.
Tunneled
A Tunnel Interface is useful when you want to route network traffic on the SSID to and from a single end point, and apply policies at this end point. In the tunneled mode, APs on the SSID route all traffic via the tunnel to a remote endpoint configured on the Tunnel Interface that you select. See Tunnel Interface for details. If you have not yet defined a Tunnel Interface, you can do it from within the Network tab using the Add / Edit link.
- All types of tunnel interfaces support tunneling of RADIUS messages between APs and a RADIUS server located behind the tunnel endpoint.
- For tunnel types other than the RAP VPN tunnel, an AP obtains its IP address from the DHCP server in the remote network on the SSID VLAN. A RAP running an SSID with a VPN tunnel obtains its VPN IP address from the remote VPN endpoint, e.g., a firewall appliance.
- The RAP VPN tunnel does not support IPv6. So for a RAP to communicate with a RADIUS server, the RADIUS server must have an IPv4 address.
- Authentication (802.1X or RADIUS MAC Authentication)
- Accounting
- CoA (Change of Authorization)
With Layer 2 Traffic Inspection and Filtering (L2TIF) enabled on an SSID, Arista APs running the SSID send all packets to a wired endpoint, i.e., a tunnel endpoint or a switch. You can then configure the wired endpoint to inspect and filter traffic. An effect of enabling L2TIF on an SSID is that two clients associated with the SSID cannot communicate directly with each other on the wireless link; their packets are sent to the wired endpoint. What happens to these packets depends on the policies configured at the endpoint.
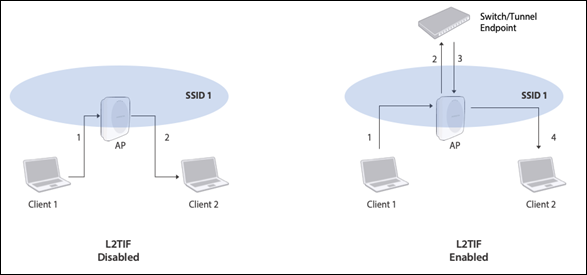
- L2 Broadcast: APs broadcast their information over the wired network. L2 broadcast works on the SSID VLAN and, if Layer 2 GRE is enabled, it works on the communication VLAN. You can Use Tunneling for Inter AP Coordination so that information related to inter-AP coordination flows through the tunnel, i.e., from one AP to the tunnel endpoint to another AP.
- RF Neighbors: APs exchange information only with their RF neighbors. Dual-radio APs use Background Scanning to find their RF neighbors, tri-radio APs use their third radio. If you have not enabled Background Scanning under Device Settings, CV-CUE prompts you to do so when you turn the SSID ON. You can Use Tunneling for Inter AP Coordination so that information related to inter-AP coordination flows through the tunnel, i.e., from one AP to the tunnel endpoint to another AP.
Note: RF Neighbor can be used only with 802.11ac or higher Arista APs.
- This Server:APs exchange information via the Wireless Manager server. The information is shared from a parent location to its child locations.
Note: Since the Arista server is involved, you cannot use the tunneling mode for inter-AP information.
If you select Advertise Client Associations on SSID VLAN, APs on this SSID broadcast their client associations to other APs on the same SSID VLAN.
DHCP Option 82 (DHCP Agent Information Option) is generally used in a distributed DHCP server environment to assign IP addresses to clients based on their location. The AP inserts DHCP Option 82 in all DHCP packets, such as DHCP Discover and DHCP Request, thereby providing additional information to identify the client's point of attachment. DHCP Option 82 contains a Circuit ID that you can configure at this location and on the DHCP server as well. The DHCP server then selects an appropriate IP pool for the Circuit ID it receives, and assigns an IP address to the client from this pool. For an example, see Example Use Case for DHCP Option 82.
DHCP Packet Forwarding is used to send a copy of DHCP Packets from Access Points (AP) to Network Access Control (NAC) solutions for profiling clients and assigning appropriate network segments. When you enable the packet forwarding option on the UI, the AP forwards a copy of the DHCP packets to Port 67 of the destination server.
The destination server can be an IPv4 or IPv6 address, not a hostname. You can provide a maximum of eight IP addresses for the destination server. You also have the option to send the DHCP packets through a tunnel if the Network Mode is L2 Tunnel or L3 Tunnel. However, you cannot send the DHCP packets to IPv6 addresses if the network mode is L3 Tunnel.
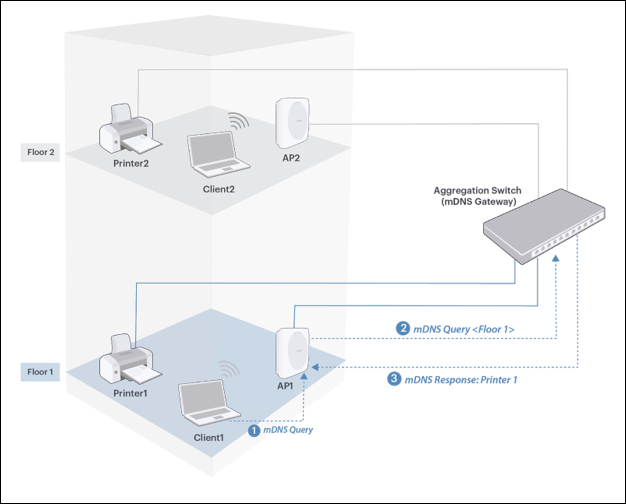
- mDNS tagging is not supported in NAT or VPN Tunnel modes.
- For mDNS tagging to work, make sure your aggregation switch supports mDNS gateways. See the Supported Features page on the Arista website to check if a particular switch model supports an mDNS gateway.
- Make sure you have assigned the correct location tag to each location because mDNS gateways return devices based on location tags. See Set Location Tag for steps on how to assign location tags.
Example Use Case
Let us consider an enterprise deployment with two branch offices and a single DHCP server hosted in the data center at the HQ. Only one SSID is configured and the same configuration is assigned to all the branch office locations. The same VLAN ID is configured but different subnets are assigned to the branch office locations.
- HQ
- Branch1
- Branch2
DHCP Option 82 is enabled and the Circuit ID is set to “%l” which sends the location tag to the DHCP server.
- If Circuit ID = HQ then assign IP from 172.16.0.0/16 – 172.16.8.255/16 subnet
- If Circuit ID = Branch1 then assign IP from 172.16.9.0/16 – 172.16.12.255/16 subnet
- If Circuit ID = Branch2 then assign IP from 172.16.13.0/16 – 172.16.15.255/16 subnet
Configure SSID Network Settings
The Network tab is the third of the three SSID tabs (Basic, Security and Network) that you must configure before you can save an SSID and turn it ON.
- Go to
- Enter the default VLAN ID for the SSID.
- Select the AP mode of operation for the SSID.
- If you select Bridged mode, you do not need to configure anything more and you can proceed to the next step.
- If you select NAT, you need to configure the following NAT-related parameters:
- Start IP Address defines the starting IP address of the IP pool from which the AP assigns IP addresses to clients.
- End IP Address defines the end IP address of the IP pool from which the AP assigns IP addresses to clients.
- Local IP Address is the local IP address of the APs on the wireless side.
- Subnet Mask is the subnet mask for the IP pool.
- DNS Servers are the DNS servers that clients will use to get DNS information. You must enter at least one DNS server IP address. You can enter up to three such DNS server IP addresses.
- Lease Time is the DHCP lease time in minutes, after which the IP allocated to the client expires.
- Select Wired Extension to extend a NAT-enabled wireless LAN to the wired side using the second Ethernet port on the AP.
- If you select L2 Tunnel or VPN Tunnel , you need to select the Tunnel Interface which contains the endpoint to which the AP will tunnel all traffic. If you have not yet defined a tunnel interface, you can do so by clicking Add / Edit. This opens a Tunnel Interface window on the right-pane. You can create the interface and return to network settings.
- Enable Use Tunnel for RADIUS Messages if the enterprise RADIUS server is behind the tunnel endpoint and you wish to tunnel RADIUS messags to the endpoint.
Note: Either 802.1X or RADIUS MAC Authentication must be enabled for communication with a remote RADIUS server.
- For EoGRE tunnels, you can Synchronize Failover and Fallback of RADIUS Server with EoGRE Interface. This is helpful if the primary and secondary RADIUS servers are bound to the respective EoGRE interfaces but they do not mutually sync client authentication states. In such cases, selecting this prevents a "split-brain" situation, where the client data flows via the secondary EoGRE tunnel while RADIUS messages are exchanged with the primary RADIUS.
- Enable Use Tunnel for RADIUS Messages if the enterprise RADIUS server is behind the tunnel endpoint and you wish to tunnel RADIUS messags to the endpoint.
- Select the Inter AP Coordination mechanism.
- If you select L2 Broadcast, APs broadcast their information over the wired network. Select Use Tunneling for Inter AP Coordination if you want the inter-AP coordination related information to flow through the tunnel.
- If you select RF Neighbors, APs exchange information only with their RF neighbors. Select Use Tunneling for Inter AP Coordination if you want the inter-AP coordination related information to flow through the tunnel.
- If you select This Server, APs exchange information via the Wireless Manager server.
Note: Since the Arista server is involved, you cannot use the tunneling mode for inter-AP information.
- Select Advertise Client Associations on SSID VLAN if you want APs on the SSID to broadcast their client associations to other APs on the same SSID VLAN.
- Select DHCP Option 82 to assign clients IP addresses based on their location in a distributed DHCP server environment.
- Select Multicast DNS (mDNS) Packet Tagging if you want APs to tag client mDNS query packets with the location name. mDNS gateways running on the switch return appropriate network services (printers) based on the location tag.
- Select DHCP Packet Forwarding to send a copy of DHCP Packets from Access Points (AP) to Network Access Control (NAC) solutions for profiling clients and assigning appropriate network segments.
- Click Save or Save & Turn SSID On.If you select Save & Turn SSID On, see Turn an SSID On for details.
SSID VLAN Mapping
- Go to Click Add SSID.
- Click the Network tab.
- In VLAN, select the VLAN Name radio button and provide your VLAN name.
- Provide a fallback VLAN ID.
- Click SSID VLAN Mapping.
- Add the VLAN name and ID and save the settings.
- Save and turn on the SSID.
SSID VLAN Pooling
VLAN Pooling is a list of VLAN IDs defined by the Network Administrator. The Access Point (AP) distributes the VLAN IDs from this pool of VLAN to the clients connecting to the SSID. VLAN Pooling offers better scalability and optimized load-balancing of traffic.
VLAN Pool can be Static or Dynamic. Static VLAN Pool is manually defined by Network Administrators in the SSID. Dynamic VLAN Pool is assigned by RADIUS servers depending on the device identity.
VLAN Pooling also supports MVRP.
Rules and Restrictions for VLAN Pool
The following VLAN rules and restrictions apply to VLAN Pool:
- You can provide a maximum of 128 VLAN IDs in the VLAN Pool.
- VLAN IDs must be in the range of 0-4094.
- You can provide a VLAN range separated by a hyphen. Example, 10-20
- Duplicate VLAN IDs are not allowed.
- Inverse or decreasing VLAN range is not allowed. For example, 20-10 is not allowed.
Configure VLAN Pooling
Follow these steps to configure VLAN Pooling in SSID settings:
- Go to CONFIGURE > WiFi > Add SSID.
- Select the Network tab and then select the VLAN Pool option.
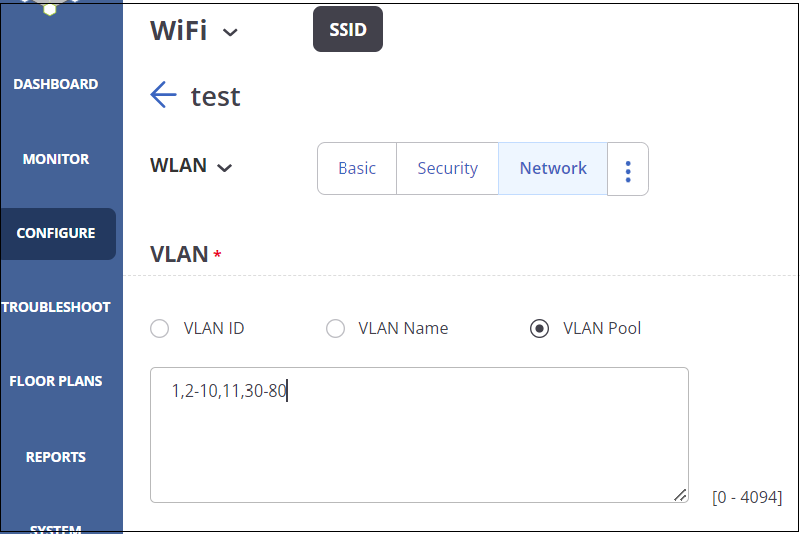
- Specify the VLAN IDs.
- Save the settings.
Alternatively, to configure the VLAN Pool from the Role profile, navigate to CONFIGURE > Network Profile > Role and specify the VLAN Pool.
SSID Access Control
The SSID Access Control tab contains settings that control access to the SSID, for example, Firewall and Client Authentication settings.
To configure the firewall settings, see Configure Firewall Settings.
To configure Redirection, see Configure Redirection in SSID Access Control.
Organizations such as enterprises and educational institutions (K-12 and higher education) often implement a centralized Authentication, Authorization and Accounting (AAA) management to enforce Role Based Control , also called Role Based Access Control (RBAC). RBAC enables network administrators to restrict system access to authorized users. Users are granted controlled access to network resources based on the roles assigned to them or the groups to which they belong. Typically, organizations implement this kind of controlled access by using RADIUS. When users connect to the network, they are first authenticated and then authorized to access appropriate resources on the network.
In the case of a WLAN network, user access restrictions could mean that only specific VLANs or a fixed bandwidth is provided to users based on the user roles defined in the RADIUS server. You can also enforce which applications a user can access over the WLAN network based on the user role.
Arista uses Role Profiles to define various WLAN access roles, and to create RADIUS Vendor Specific Attribute (VSA) based rules and Google Organizational Unit (OU) rules to authorize Wi-Fi users. A network administrator can define various role profiles that specify the restrictions to be placed on the Wi-Fi user to whom the profile is assigned. The administrator can then define multiple VSA rules (for RADIUS) or Google OU rules (for Google Integration) here in SSID Access Control, and assign role profiles through these rules to the Wi-Fi users that connect to the SSID.
Let us consider an example. When you define a Rule Type for RBAC, then the OU returned from Google or the role obtained from the RADIUS VSA must contain the string entered in the Enter Value field. For example, if the string in the Enter Value field is ‘/*/Elementary School/*/Student’, then this will match with ‘/SJUSD/Elementary School/Almaden Elementary/Student’ in Google/VSA.
It could happen that you have different settings in the SSID tabs and different ones in the Role Profiles tab. What happens then? For the answer, see Role Profile.
To configure Role Based Control, see Configure Role Based Control.
To control clients that can access this SSID, you can create Allow and Deny lists of client MAC addresses. See How the Client MAC Allow and Deny Lists Work and Requirements for details on the feature.
With Client Isolation enabled on an SSID, Wi-Fi clients associated with the SSID are allowed to communicate only with their gateway; they cannot communicate directly with any other hosts on the same subnet—including other clients on the same SSID, clients associated with other SSIDs on the same subnet, and hosts connected to the wired network on the same subnet. An AP running an SSID with Client Isolation discards all packets from a client if the destination IP address is on the same network as the client, except for packets destined to the gateway.
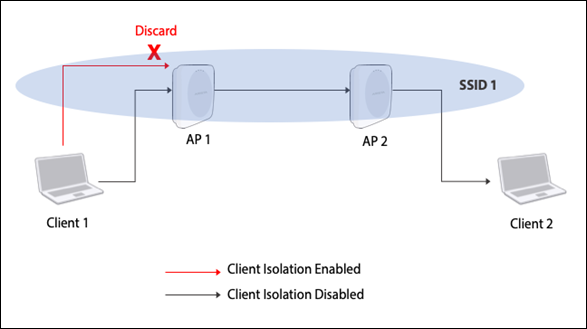
If NAT is enabled on an SSID, an AP running the SSID becomes the gateway node of its own private subnet. Consider Client 1 and Client 2 in the figure above. If these clients are associated with a NAT-ed SSID, they cannot see each other’s IP address. Thus, it is NAT rather than Client Isolation that prevents direct connections between these clients; Client Isolation prevents direct connections only between clients of the same AP.
Note that even with a NAT-ed SSID, the net effect of enabling Client Isolation is the same as in the case of a bridged or tunneled SSID: clients on the same SSID cannot communicate directly with each other. But the mechanisms that prevent such communication are different: NAT prevents direct communication between clients on different APs and Client Isolation prevents direct communication between clients of the same AP.
For the other RADIUS settings, see Configure SSID Security Settings.
You can choose to either Disconnect or Stay Connected and Assign Role to the user. To assign a role, you need to select one from those defined on the Role Profile tab. You might configure Client Authentication before you have created any Role Profile. When you click Add / Edit under Select Role, a window appears in the right pane, allowing you to define a Role Profile without having to leave Client Authentication.
To configure Client Authentication, see Configure Client Authentication.
Configure SSID Access Control
You can configure settings that control access to the SSID, for example, Firewall and Client Authentication settings.
SSID Access Control consists of the following settings:
- Configure the Firewall settings. See Configure Firewall Settings for details.
- Configure Bonjour Gateway settings.
See Configure Bonjour Gateway for details.
- Configure Redirection settings.
See Configure Redirection Settings for details.
- Configure Role Based Control settings.
See Configure Role Based Control for details.
- Configure WiFi Clients in Allow List and Deny List settings.
See Configure Allow and Deny Lists of Wi-Fi Clients for details.
- Enable Client Isolation to prevent clients of the same AP from being able to access each other's data.
- Configure Client Authentication settings.
See Configure Client Authentication for details.
- Click Save or Save & Turn SSID On.
If you select Save & Turn SSID On, see Turn an SSID On for details.
L3-4 Firewall
Arista Access Points (APs) have firewall capabilities. The AP firewall monitors the traffic passing through the AP and takes actions based on user-defined rules.
The firewall is stateful, that is to say, it keeps track of whether the connection has been opened in the outgoing direction (wireless to wired-side) or in the incoming direction (wired-side to wireless), and takes appropriate actions on the packets based on the direction in which the connection was opened. The following image illustrates the conventions used for directions.
Note that this is not the Internet facing firewall. Its main purpose is to facilitate traffic controls, such as allowing/disallowing access to certain assets and/or applications for wireless users. The firewall rules are defined and enforced on a per SSID basis. Arista APs support multiple SSID profiles, thereby enabling multiple firewall configurations to co-exist.
- Block guest Wi-Fi users from accessing the private/corporate subnet. This serves as an additional security control to ensure that guest Wi-Fi users can access only public Internet and nothing in the private address space.
- Block or allow access to specific domain names.
- Allow guest Wi-Fi users to access only HTTP and HTTPS content in the Internet. This is typically done to control the type of traffic guest users can generate.
- Implement DNS-based content filtering to prevent access to non-family-friendly web sites, security threats, and peer-to-peer file sharing. The firewall can be used to ensure that Wi-Fi clients necessarily use the specified content filtering DNS server, such as Norton ConnectSafe, and cannot bypass it.
- Enforce use of IPsec VPN for wireless clients.
- When you enable L3-4 Firewall Rules, you can see the default rule Action : Block on the UI. If you enable L3-4 Firewall Rules and do not define any rules at all, the default rule applies, i.e., all traffic is blocked.
- The AP compares traffic with rules from top to bottom until it finds the first match. Once it finds the first match, the AP does not compare the rest of the rules. If it finds no match with any of the defined rules, the AP uses the default rule at the end. You can re-order the rules using the drag-and-drop feature to reposition them at the desired level.
In case of a conflict between rules on the L3-4 Firewall and those on the Application Firewall, the AP decides using this Decision Table.
Example Use Case of L3-4 Firewall
Let us look at a rule set that might be found on a Guest SSID in a retail store deployment.
| Rule Number | Rule Name | IP / Hostname | Port | Action | Protocol | Direction |
|---|---|---|---|---|---|---|
| 1 | Content Filtering DNS1 | 199.85.126.30 | 53 | Allow | UDP | Outgoing |
| 2 | Content Filtering DNS2 | 199.85.127.30 | 53 | Allow | UDP | Outgoing |
| 3 | Block All Other DNS | * | 53 | Block | UDP | Outgoing |
| 4 | No Local Access | 192.168.0.0/16, 172.17.0.0/21, 10.0.0.0/8 | Block | Any | Any | |
| 5 | Allow HTTP / HTTPS | * | 80, 443 | Allow | TCP | Outgoing |
| 6 | Default | Block |
Rule 1 - Allow outbound UDP port 53 to Content Filtering (Norton) DNS1/199.85.126.30. This rule implements DNS-based content filtering to block access to web sites that contain non-family-friendly content, pose security risks, and promote file sharing applications. DNS uses UDP port 53. So this rule allows outgoing UDP connections destined to port 53 on a content filtering DNS server with the 199.85.126.30 host IP address.
Because the firewall is stateful, the return path is automatically allowed and you do not need a separate rule for the return path. This is true for the other rules as well.
Rule 2 - Allow outbound UDP port 53 to Content Filtering (Norton) DNS2/199.85.127.30. Like Rule 1, this rule also implements DNS-based content filtering. This rule provides DNS server redundancy.
Rule 3 - Block all outbound UDP 53. This rule blocks all DNS traffic excluding that which is allowed by Rules 1 and 2. This rule prevents users from statically configuring DNS server addresses on their clients to circumvent content filtering.
Rule 4 - Block traffic to destination 192.168.0.0/16, 172.17.0.0/21 and 10.0.0.0/8. Blocks access to private/corporate subnets. This rule blocks any wireless traffic addressed to any host in the 192.168.0.0/16, 172.17.0.0/21 and 10.0.0.0/8 subnets. The Protocol specified for this rule is Any, which covers any protocol carried over IP. Because there are protocols that do not implement the port concept (e.g. ICMP), the port number gets grayed out when Any is selected as protocol. This rule is ideal for restricting users on the Guest Wi-Fi from accessing private subnets.
Rule 5 - Allow any traffic outbound to TCP port 80, 443. Allow clients to open outgoing TCP connections to port 80 (allows outgoing HTTP connections) and allow clients to open outgoing TCP connections to port 443 (allows outgoing HTTPS connections). The wildcard character (*) represents “any” hosts.
Rule 6 - Default rule is set to Block, which means that all other kinds of communication, except the ones enabled by the rules 1-5, are disallowed.
Application Firewall
You can define firewall rules at the application level.
- To enable Application Firewall Rules, you must enable Application Visibility under the SSID Analytics tab. CV-CUE prompts you to enable Application Visibility from within the Application Firewall Settings, so you do not need to navigate to the Analytics tab.
- When you enable Application Firewall Rules, you can see the default rule Action : Block on the UI. If you enable Application Firewall Rules and do not define any rules at all, the default rule applies, i.e., all traffic is blocked.
- The AP tests packets with rules from top to bottom until it finds the first match. Once it finds the first match, the AP does not compare the rest of the rules. If it finds no match with any of the defined rules, the AP uses the default rule at the end. You can re-order the rules using the drag-and-drop feature to reposition them at the desired level.
Example Use Case of Application Firewall
| Rule Name | Category | Application Name | Action |
|---|---|---|---|
| Block Facebook and Twitter | Social Networking | Facebook, Facebook Apps, Facebook Event, Facebook Messages, Facebook Post, Facebook Search, Facebook Video, Facebook Video Chat, Twitter | Block |
| Default | Block |
L3-4 versus Application Firewall Decision Table
| L3 Firewall Action | Application Firewall Action | Final Action |
|---|---|---|
| Deny | Any | Deny |
| Allow | Deny | Deny |
| Allow | No Match | Allow |
| No Match | Deny | Deny |
| No Match | Allow | Allow |
| No Match | No Match | Default |
| Allow and Mark | Allow and Mark | Allow with App Mark |
| Allow and Mark | Allow | Allow with L3 Mark |
| Allow and Mark | No Match | Allow with L3 Mark |
| No Match | Allow and Mark | Allow with App Mark |
| No Match | No Match | Default Mark |
Configure Firewall in SSID
You can configure both L3-4 and Application firewalls.
- Go to
- Click Firewall.
- Select Layer 3-4 Firewall Rules to set up a L3-4 firewall.
- Click the "+" sign to add a new rule to the firewall.
- Configure the following details of the firewall rule:
- Enter the Rule Name, what you want to call the rule.
- Enter IP / Hostname to which you want to apply the rule.
- Enter the Port number to which you want to apply the rule.
- Select the Action, whether you want to Allow, Block, or Allow and Mark the packets under this rule.
- Select the Protocol to which you want to apply the rule.
- Select the Direction, whether you want the rule to apply to Any direction, to Incoming packets or to Outgoing packets.
- Select Application Firewall Rules to set up an application firewall.
- Click the "+" sign to add a new rule to the firewall.
- Configure the following details of the firewall rule:
- Enter the Rule Name, what you want to call the rule.
- Select the application Category to which you want to apply the rule.
- Select the Application Name to which you want to apply the rule.
- Select the Action, whether you want to Allow, Block, or Allow and Mark the packets under this rule.
- Click Save or Save & Turn SSID On. If you select Save & Turn SSID On, see Turn an SSID On for details.
What is Bonjour Gateway?
Bonjour is Apple's implementation of zero-configuration networking (Zeroconf). It is used to discover devices and services advertised by Bonjour capable devices on a local network using multicast Domain Name System (mDNS).
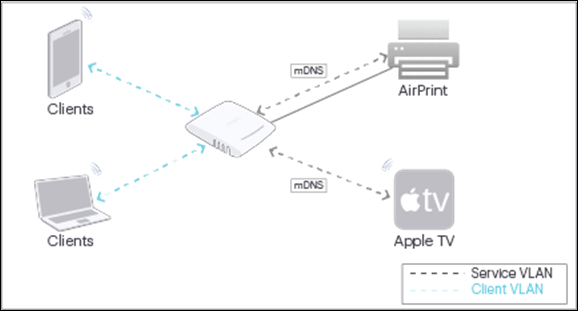
How Arista Supports Bonjour Gateway
- A service VLAN on which the Bonjour capable devices are deployed.
- A client VLAN on which the clients are deployed.
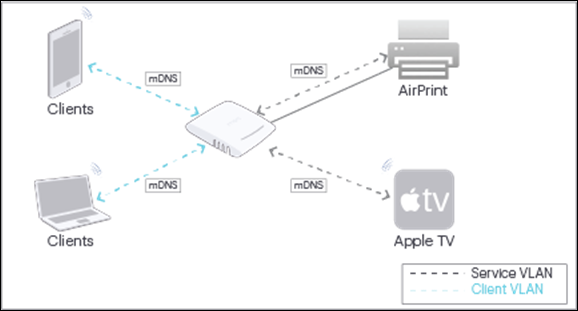
As shown in the figure, after a client connects to an SSID that has Bonjour Gateway enabled and the service VLAN configured, the AP forwards the mDNS packets from the service VLAN to the client VLAN (i.e. the VLAN ID configured in the SSID) and vice versa. The client now knows about the Bonjour services available on the WLAN and can connect to such services.
Note: Bonjour Gateway can be configured only if the Network type on the SSID is set to Bridged. This feature is not available for a NAT type network.
Configure Bonjour Gateway
You can configure Apple's Bonjour Gateway feature that allows access to Apple devices on the network.
- Go to
- Select Bonjour Gateway.
Note: Bonjour Gateway does not work when the Network is set to NAT mode. If you have set the Network to NAT mode, CV-CUE grays out Bonjour Gateway and prompts you to change the Network setting from within the Access Control tab.
- Enter the Service VLANs.These are the VLANs with the Bonjour devices. The AP forwards packets from the service VLAN to the client VLAN (i.e. the VLAN ID configured in the SSID) and vice versa.
- Click Save or Save & Turn SSID On.
DHCP Fingerprinting-based Access Control
Using DHCP Fingerprinting-based access control, you can allow or deny clients getting connected to an SSID.
The AP can identify the Operating System (OS) of the client based on the DHCP exchange packets between the client and the DHCP server. DHCP has many request parameters; in this case, DHCP uses Option 55 to capture and exchange client OS (Macintosh, Windows, and others). Leveraging this client-specific information, you can restrict certain types of clients from connecting to the network.
As a network administrator, you can use DHCP fingerprinting to allow or deny a client from associating with an Access Point (AP), put clients in a specific VLAN, apply bandwidth control or firewall rules, and apply other network policies.
- Navigate to
- Enable the DHCP Fingerprinting based Access Control check box.
- For Identified Clients, first specify the Default Rule. The OS Type is Any and you cannot change it. Select either Allow or Deny for Action. The default rule applies to all identified clients.
- (Optional) Specify the exceptions to your default rule, if any. You can add multiple exceptions.
- Click Allow or Deny for Unidentified clients.
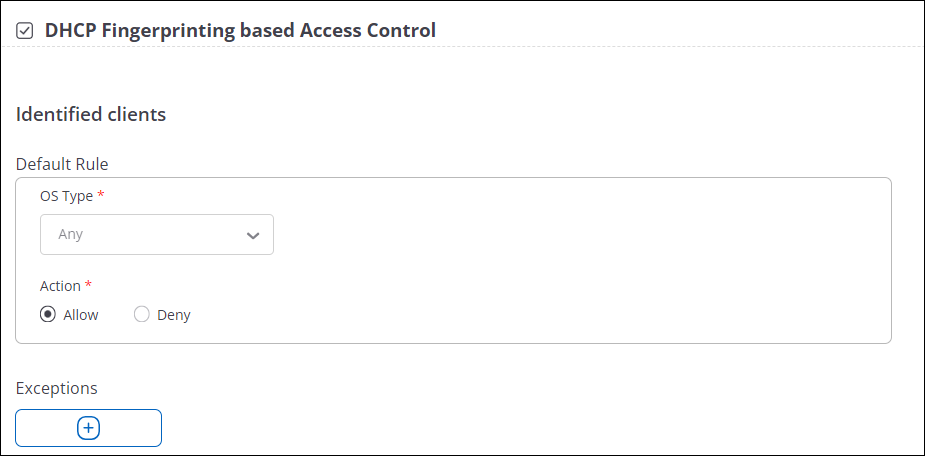
- Save the settings.
Identified and Unidentified Clients
The AP categorizes clients into identified and unidentified based on client information captured from DHCP exchange request.
When the client tries to connect to the AP the next time, the client data is matched with the fingerprint database. If the data matches, the client is classified as identified. If not, the client is considered as unidentified.
How the Rules Work for Identified and Unidentified Clients
For unidentified clients, you can specify whether to Allow or Deny such clients to connect to the network. For identified clients, you can specify a default rule and exceptions to the default rule. Exceptions are given priority over the default rule.
In a default rule, the OS type is Any for clients and you cannot change it. You can change the action as Allow or Deny for such clients. In exceptions, you can specify only the OS type. The action will be the opposite of what you select in the default rule. For example, if the default rule for an identified client is Allow for Windows OS, and in the exceptions you have added Android as the OS type, then Windows clients will be allowed to connect to the network but Android clients will be denied connection to the network.
When a client successfully connects to the network, you can see the status of the client as Successfully connected in . For clients that failed to connect, the status is seen as Failed client. DHCP Fingerprinting Failure. The client events are also captured in the client event logs.
Configure Redirection in SSID Access Control
You can redirect clients of the SSID to a URL of your choice.
- Go to
- Select Redirection.
- Select whether you want to redirect Smartphones / Tablets only or All Clients.
- Enter the Redirect URL.
- Select HTTPS Redirection if you wish to move to secure version of HTTP.
Info:Enabling HTTPS Redirection enables three fields, these three fields provide the information of the customer using the certificate.
- Common Name: Identifies the host name associated with the certificate.
- Organization: Name of an organization.
- Organization Unit: Name of an organizational unit.
- Enter the list of Walled Garden sites.
Note: You must enter at least the Redirect URL in the Walled Garden field, since the user must be able to access that URL before login.
- Click Save or Save & Turn SSID On.
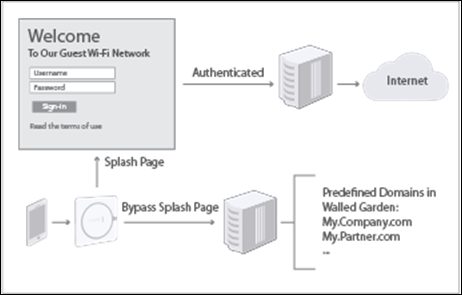
What is a Walled Garden?
Let us understand the concept of a “walled garden” and its typical applications within Arista Wi-Fi. A walled garden allows Wi-Fi providers to control which destinations users can or cannot access on a wireless network.
Walled garden functionality is used in conjunction with Arista’s captive portal. The captive portal function serves as a vehicle to interact with users when they log into Wi-Fi network.
- Asking the user to accept terms and conditions
- Facilitating user authentication using a web-based login and password screen
- Facilitating logins using social Wi-Fi credentials
How the Client MAC Allow and Deny Lists Work
You can define either an Allow list or a Deny list of client MAC addresses on a per SSID basis. It is basically an Access Control List for an SSID – you get to decide which devices can or cannot connect to an SSID. For example, you might want to allow only employees on the Corporate SSID. You could then create an Allow list of MAC addresses that can connect to the Corporate SSID. Conversely, you might want to restrict some clients from connecting to an SSID. You could then create a Deny list of client MAC addresses for that SSID to prevent those clients from connecting to the SSID. Below are the definitions of Allow and Deny lists.
Allow list: Only clients in the Allow list can connect to the SSID. No other clients are allowed.
Deny list: Clients in the Deny list cannot connect to the SSID. All other clients are allowed.
Requirements for Allow Deny Lists of Client MAC Addresses
- For a given SSID, you can create either an Allow list or a Deny list, but not both
- Per SSID Allow list or a Deny list works only for 802.11ac and higher Arista devices
- For each SSID, you can add a maximum of 1024 clients to its Allow list or Deny list
Google Integration for Client Device Authorization
Google provides App sets for enterprises (Google for Work) and educational institutions (Google for Education). These enable users to communicate and collaborate from a single platform. From network administrators’ perspective, key functions provided by Google are User and Device Management, and Organizational Units. Network administrators can create an organizational structure and control which settings and policies must be applied to users and devices. User directory offers SSO for all Google applications, while device management enables administrators to authorize devices that can access the network and restrict access based on the user role. Once a user logs in with his official Google credentials, the device MAC is listed on the Google Device Management page. The administrator can then authorize or reject the device when it attempts to connect to the network.
Configure Client Authentication
You can configure client authentication using either Google Integration or RADIUS MAC Authentication.
- Go to
- Select Client Authentication.
- Select either Google Integration or RADIUS MAC Authentication.
- If you select Google Integration, then select what happens If Client Authentication Fails:
- Select Disconnect to disconnect the client if authentication fails.
- Select Stay Connected and Apply Role and select the role you want to assign to the client if authentication fails. If you want to define a role, click Add / Edit. A right-panel window appears where you can configure the Role Profile and continue with Client Authentication. See Configure a Role Profile.
- If you select RADIUS MAC Authentication, RADIUS Settings appear.
Note: RADIUS MAC Authentication is not available If you have configured 802.1X authentication in the SSID Security tab, since 802.1X already is a RADIIUS-based mechanism.
- If you select Google Integration, then select what happens If Client Authentication Fails:
- Click Save or Save & Turn SSID On. If you select Save & Turn SSID On, see Turn an SSID On for details.
Configure Role Based Control
You can assign role profiles to users connecting to the SSID based on the Google Integration or RADIUS rules you define here in Role Based Control.
- To implement Role Based Control using Google, you must enable Google Integration.
- To implement Role Based Control using RADIUS, you must enable 802.1x.
You do not have to leave the SSID Access Control tab to configure Google or RADIUS. Just click Change Settings? under Role Based Control. CV-CUE opens a right-pane window, allowing you to configure and save the relevant settings and continue with Role Based Control.
- Select Role Based Control
- Select RADIUS VSA to assign roles based on rules for the RADIUS server.
- Select the Rule Type. This could be either Arista-Role RADIUS VSA or Custom RADIUS attributes VSA.
- Enter the Vendor ID and Attribute ID if you selected Custom RADIUS attributes VSA. For the Arista-Role RADIUS VSA case, the vendor is Arista and the Vendor ID and Attribute ID are pre-defined in the RADIUS server, so you do not have to enter those values here.
- Select the Operand for the string pattern that you want to use for the rule.
- Enter the string pattern in the Enter Value field.
- Select the role you want to assign for this rule in Assign Role. If you have not yet defined the role you want to assign, click Add / Edit. A right-pane window appears allowing you to define a role and continue with Role Based Control. See Configure a Role Profile for details.
- Select Google OU to assign roles based on rules for Google OU.
- The Rule Type is preset to Google OU.
- Select the Operand for the string pattern that you want to use for the rule.
- Enter the string pattern in the Enter Value field.
- Select the role you want to assign for this rule in Assign Role. If you have not yet defined the role you want to assign, click Add / Edit. A right-pane window appears allowing you to define a role and continue with Role Based Control. See Configure a Role Profile for details.
- Select RADIUS VSA to assign roles based on rules for the RADIUS server.
- Click Save or Save & Turn SSID On.
Typical RADIUS MAC Authentication Flow
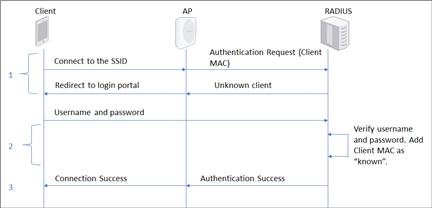
- The RADIUS server notifies the AP that the client MAC is unknown. The AP then redirects the client to a login portal.
- The user enters a username and password into the portal. The RADIUS server authenticates these credentials and registers the client MAC address against this user.
- The RADIUS server notifies the AP of the successful authentication. The user is now connected to the network.
Typically, in such cases, subsequent attempts by this client to connect to the SSID are seamless, i.e., the RADIUS server knows its MAC address and the client is not redirected to the login portal.
- Role Profiles
- Captive Portal hosted on the Arista Cloud
- Captive Portal hosted on a Third Party server
Implementation Using Role Profiles
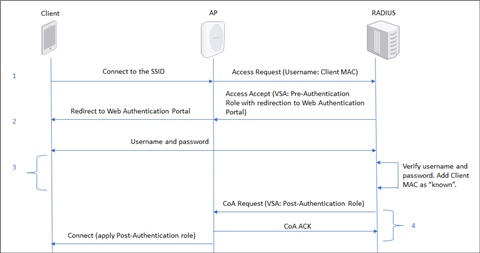
- When the client first connects to the SSID, the WiFi Access Point (AP) sends an Authentication Request containing the client’s MAC address to the RADIUS server.
- The RADIUS server responds with an Access-Accept message containing the Pre-Authentication role. The Pre-Authentication role redirects the client to a web authentication portal hosted on the RADIUS server.
- The user enters a username and password into the portal. The RADIUS server authenticates these credentials and registers the client MAC address against this user.
- The RADIUS server sends a Change of Authorization (CoA) message containing the Post-Authentication role to the AP. The AP connects the client to the network.
Configure Roles with RADIUS MAC Authentication
Let us look at how to define the two roles in CloudVisionWiFi to implement the role-based MAC authentication workflow.
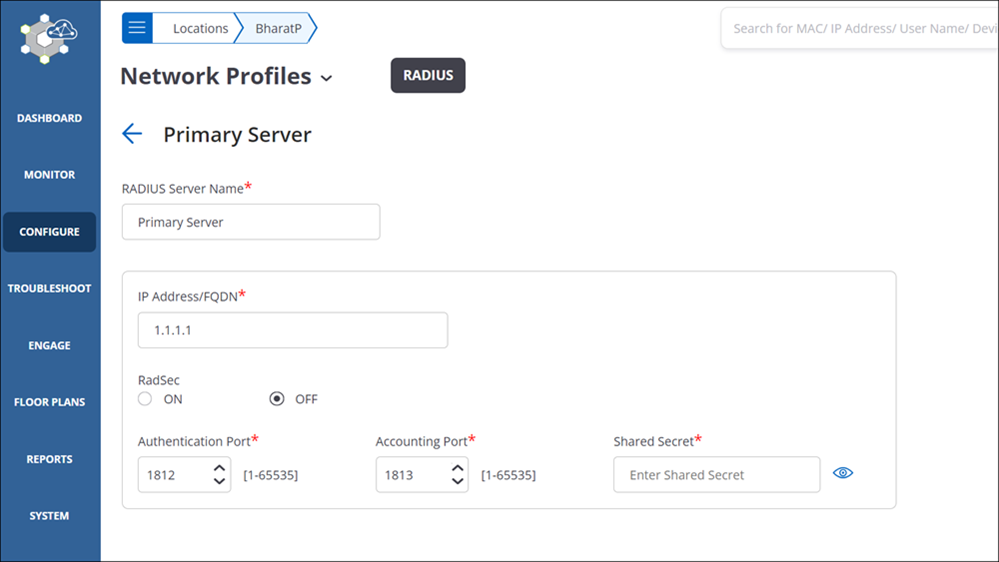
RADIUS Profile
Under click Add RADIUS Server and enter the RADIUS server details as shown below:
Pre-Authentication Role
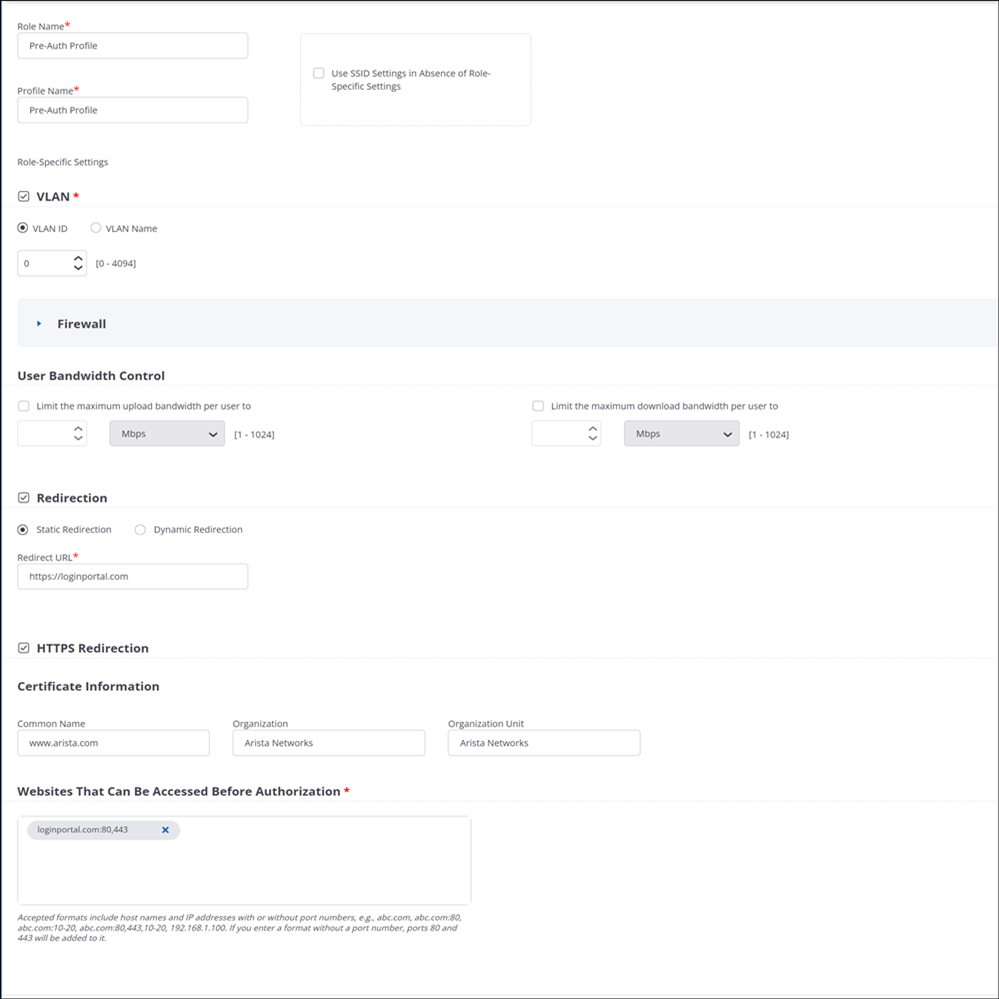
This implements Step 2) from the workflow above, redirecting the client to the RADIUS server authentication portal. You need to configure the RADIUS server to return this role in the Access-Accept message it sends to the AP.
Post-Authentication Role
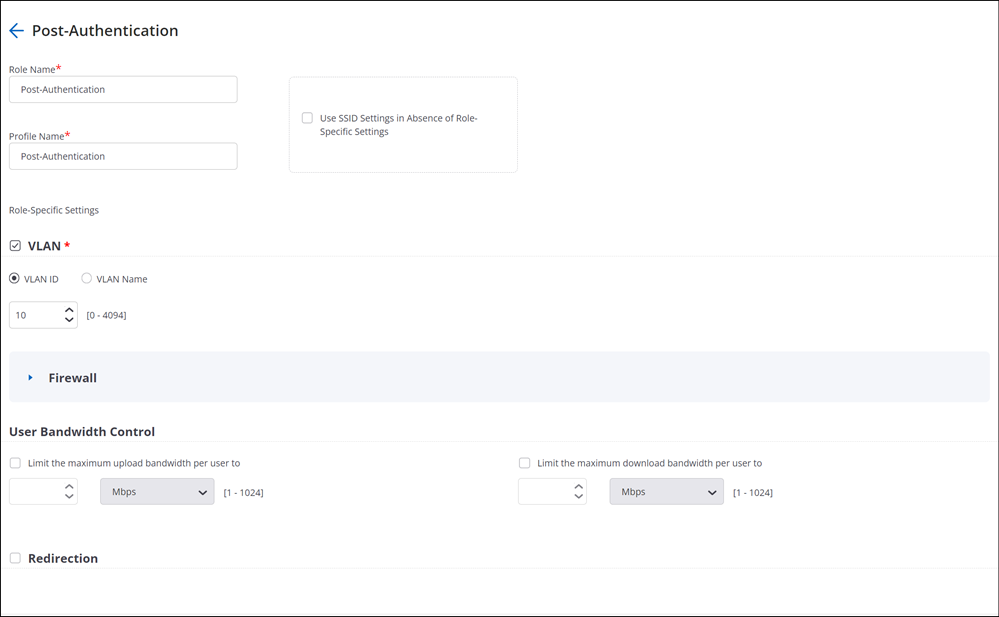
You need to configure the RADIUS server to return this role in the Change Of Authorization (CoA) message it sends to the AP.
RADIUS MAC Authentication and Role-Based Control
- Under SSID > Access Control, enable Client Authentication > RADIUS MAC Authentication and select “Disconnect” if authentication fails. This causes the client to disconnect if authentication fails. If authentication succeeds, roles defined in the SSID are applied.
- Next, under RADIUS Settings, select the RADIUS server you want to use.
Note: Set the Calling Station ID to %m-%s (MAC Address and SSID), and the NAS ID to “%s” (only the SSID).
- Finally, enable Role-Based Control on the SSID and assign the two roles via the RADIUS VSA, as shown below.
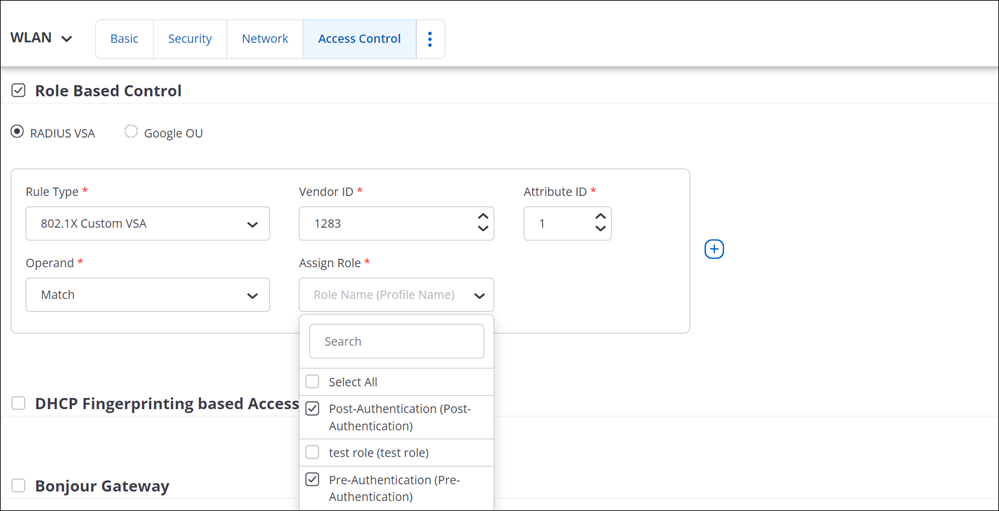
SSID Analytics
The SSID Analytics tab contains settings to control what analytics information is stored and where.
Arista APs collect, process and present useful and easy-to-understand Analytics information. You can choose to store this information on the Arista server and / or on a third-party server of your choice. Analytics information is broadly classified into Association and Application Visibility analytics.
Association
- Client MAC address
- Protocol
- SSID of the network to which the client connects
- Location of the client in the Arista Location Hierarchy
- Start time of client association with the AP (GMT)
- End time of client association with the AP (GMT)
- Start time of client association with the AP according to local time of the user
- End time of client association with the AP according to local time at the user
- Session duration
- Data transfer from client device in bytes
- Data transfer to client device in bytes
- Data rate in Kbps
- Smart device type
- Local Time Zone
- RSSI data of connected clients as well probing clients without the local MAC address
- RSSI data of neighboring Arista APs
- Channel information with each RSSI record
- Domain name accessed by the clients
- Data transferred to the domain (in bytes)
- Data received from the domain (in bytes)
Application Visibility
You can choose to send the analytics to a third-party server. In this case, when you select HTTP Content, you need to enter the Username and Password for the server. The Send Interval determines how often the data are sent to the server.
You can select which HTTP fields you want to send as part of the analytics. Arista APs send client MAC and RSSI data as part of the HTTP Post message. For details, see HTTP Post Format.
HTTP POST Format
The curl program is used to post the RSSI values to the server. The command format used is as follows:
curl <upload_URL>?sensor_mac=<sensor's MAC address>×tamp=<time in seconds> -F data=@"<file_on_airtight_device>"
- sensor_mac: The MAC address of the Arista device. Example 00:11:74:90:00:1F
- timestamp: The time in number of seconds from boot of the Arista device.
Each line in the file is of the following format:
<client_mac>, <RSSI in dBm>, <time in seconds at which RSSI reading was taken>
Configure Analytics in SSID Settings
To configure Analytics in SSID, includes two steps, one is to store analytics information on the server, and to push analytics information to third-part server.
- Navigate to
- Configure settings within the Store Analytics on This Server tab to store analytics information on the server.
- Select Association for information about the clients that connect to or associate with the Arista APs. Selecting this enables HTTP Content field.
- Select HTTP Content to capture information about the internet domains accessed by the clients associated with the Arista APs.
- Select Application Visibility to turn ON the application visibility feature.
- Scroll down to Push Analytics to Third-Party Server tab and configure the below settings to push analytics data to third-party server.
- Enter Server URL of the external server.
- Enter Username to log in to external server.
- Enter Password for the user to log in to external server.
- Enter Send Interval in minutes.
- Select HTTP Content information like Post Request Body, User Agent, Referer that you would like to share with the third party server.
- Click Save.
Analytics Parameter
| Fields | Description |
|---|---|
| Store Analytics on This Server | |
| Application Visibility | This check box turns ON the application visibility feature. If you enable Application Visibility for a selected SSID, then a list of all applications above layer 2 for the selected SSID will be displayed in the Monitoring > Applications tile. Note: We recommend not to enable Application Visibility feature for C-65, C-75, W68, and O-90. If you enable Application Visibility for these models, then it may impact the AP performance. Application Visibility feature is not supported on 802.11n and older devices. |
| Association | This check box, if enabled presents information about the clients that connect to or associate with the Arista APs. You can choose to collect analytics data for reporting purpose about the client-AP association. Association analytics and content analytics can be collected if you enable the collection of these analytics in the Wi-Fi profile. Association Analytics comprises the data related to the client - AP communication. The following data is collected as association analytics:
|
| HTTP Content | This check box captures information about the internet domains accessed by the clients associated with the Arista APs. This information is present in the association analytics file. The following information is present for each internet domain as content analytics information:
|
| Push Analytics to Third-Party Server | |
| Server URL | URL of the external server where the information is to be stored. |
| Username | Username to log in to external server. |
| Password | Password for the user to log in to external server. |
| Send Interval | Recurrent time interval, in minutes, after which the HTTP content analytics JSON file must be sent to the external server. Value can vary from [1 - 60] mins, default value is 10 mins. |
| HTTP Fields | |
| HTTP Content | Arista AP supports the transfer of client HTTP content analytics or browsing data from clients over HTTP or HTTPS to an external server where this information can be stored. If this feature is enabled then user has to configure below options. |
| Post Request Body | If checked then include the POST method request body in the JSON file. |
| User Agent | If checked then include the user agent (browser) in the JSON file. |
| Referer | If checked then include the HTTP referrer in the JSON file. |
SSID Captive Portal
A Captive Portal is a page that appears when a user attempts to access the SSID. This could be a Facebook login enabled page for a public Wi-Fi network, a simple Terms-of-Use page for a Guest SSID on a corporate network, or a custom-branded page for a coffee shop chain. The Captive Portal tab in CV-CUE is designed so that you can configure all portal related settings for your SSID (social media plugins, splash page, etc.) from this tab.
The captive portal can reside on the Arista AP, on Arista Cloud or on a third-party server. The AP Hosted portal is the simplest case. It is simply a clickthrough splash page, typically asking a user to accept some terms of use. You can upload a splash page bundle, which is a ".zip" file containing components of the splash page. A Download Sample can help you with creating your own bundle.
- Click-Through: This is basically no authentication, only a Welcome or Terms-of-Use type page on which the user can click and access Wi-Fi.
- Social Media Plug-Ins: Users authenticate using their social media login credentials to access the Wi-Fi. For details, see Access WiFi Using Social Media Plug-ins. Arista supports the following social media plugins: Facebook, Twitter, LinkedIn, Foursquare, Instagram, and Google+.
- Username and Password: There are two options within this method:
- You can Allow Guest Users to Self-Register. Self-Registration can be for Free Wi-Fi, Paid Wi-Fi, a combination of the two, or with Host Approval. For the Free case, there are options to allow guest users to set their own passwords or to auto-login, to enable "Forgot Password" links, and to activate expired accounts. For the Paid case, Arista uses the Stripe Payment Gateway. You can define tiers of payment. So, you can charge different amounts for different session durations — say, $1 for an hour and $3 for 2 hours. The access time must be consumed as soon as it is purchased. So, if a guest user purchases 1 hour of access for $1, the session will expire after exactly 1 hour of purchase, irrespective of how much session time the guest actually consumes. Even if the user explicitly logs off, the session continues to be billed. The Free + Paid case is a mixed mode - in addition to combining options from both cases, it allows you to keep the Wi-Fi free for some time and then start charging. For example, many airports offer free Wi-Fi for the first half an hour and charge users after that. Host Approval is for enterprise setups, where you want to authorize the guest Wi-Fi access. The host, whom the guest has come to visit in the enterprise, can be the authorizer. Host-approved Wi-Fi access ensures that only authorized users can access the WLAN network. To understand how host-approved guest access works, see Guest WiFi Authentication with Host Approval.
- Admin Generated Credentials uses the Guestbook method. This is where you maintain a private guestbook and allow guest users to log in and access Wi-Fi with guest user account credentials that you have defined. The guestbook can include other user-specific information. When you enable this in CV-CUE, it opens up in a new tab once you save the SSID.
- Passcode through SMS: Users provide their mobile number to receive an authentication code via SMS. They use this code to authenticate and access the Wi-Fi. You can define settings related to the passcode (such as maximum length) and to the SMS (such as maximum number of times the SMS is resent).
- Web Form: This is an enhanced form of clickthrough. There is no authentication. To access Wi-Fi, users fill out specific information such as their name, e-mail address, and contact number.
- External RADIUS: Authentication happens via an external RADIUS server. You can select a RADIUS server from the ones you have added, or add a new one using the Add / Edit option. CV-CUE allows you to add and save the new RADIUS server and return to the portal settings.
Note: You cannot use the RADIUS plugin with any other plugins. If you select External RADIUS, CV-CUE automatically disables the other plugins.
Important Notes on Payment Gateway
- Some scripts from the payment gateway do not load in Android native web view (i.e. the native browser that Android uses). To avoid this, you must add ssl.gstatic.com to the Walled Garden list of the captive portal. if you do not add this entry to the Walled Garden, the user sees an error message saying that the page could not be loaded and asking them to use a different browser.
- For best Wi-Fi user experience, we recommend that you add the general sites mentioned in Walled Garden Sites for Captive Portal to the Walled Garden list of the captive portal. The reason for this is that when a user attempts to access a Wi-Fi connection, some Operating Systems (e.g. iOS) try to reach some sites — let us call them "test sites" — to detect if the user is behind a captive portal. If they are unable to reach the "test sites", these operating systems conclude that the user is behind a captive portal and open the splash page using an "in-app" browser. This could cause problems because, in conventional browsers, the page containing the usage time and the logout option opens in a separate tab from the splash page. Thus, with an "in-app" browser, users could end up not being able to see the usage and logout page at all. While users are sent reminders to logout once they close their sessions, they could miss these messages or attend to them after a while. This means that users could get billed for time they have not spent using the Wi-Fi. To avoid such problems, it is best to add those "test sites" to your Walled Garden so that users can access the time and logout tab as well.
- Currently, you can define only time limits on the payment gateway. You cannot define bandwidth or data limits; usage evaluation based on either bandwidth or data volume is not supported.
- You can define amounts with up to 2 decimal points (e.g. $1.35).
Apart from the plugins, you can configure Common Settings such as e-mail, SMS and payment gateway accounts used to communicate with your Wi-Fi users. Common settings are applicable not only across plugins within an SSID captive portal, but also across SSIDs and across locations. So if you define a new location and an SSID at that location, the common settings apply there as well. This means that Wi-Fi users of an organization see the same e-mail and use the same SMS account, no matter what location they are at.
You can use a combination of plug-ins on your captive portal. For example, you can use all the social media plugins to provide guests with the option of using any social media account of their choice to authenticate and access the Wi-Fi. Or, if you are organizing an event and want to provide Wi-Fi access to guests, you can create a batch of guest user accounts in Guest Manager and provide the account details to the guests to access the Wi-Fi by using these account credentials.
A Third-Party Hosted captive portal resides on an external server. As such, you must enter the Splash Page URL and the Shared Secret of the server that hosts the portal. You can enable RADIUS Authentication and enter the 802.1X Settings. See 802.1X RADIUS Settings for details. With third-party hosted portal, you need to configure Advanced Portal Parameters, namely the Request and Response Attributes that the portal uses for its challenge-response based user authentication.
There are some general fields that apply to AP-hosted, Cloud Hosted and Third-Party hosted portals. For example, you can define Websites that users can access before login and some Post Login fields such as a URL the user is redirected to after login (for instance, a coupon for the 100th customer), and login and blackout times. For a third-party hosted portal, you can define a post-login Service Identifier for the user
Walled Garden Sites for Captive Portal
For best results with splash pages, there are some sites you need to add to the Walled Garden list of the captive portal. Some of these sites are general, for all splash page based captive portals, while others are for specific plugins or content type.
General Sites
- Host name of the Guest Manager; for example, gms.cloudwifi.com.
- akamaihd.net
- googleapis.com
- gstatic.com
- Country specific Google domain where the access point using the SSID profile is deployed. For example, if an AP deployed in France is using the SSID profile, then you must add google.co.fr to the walled garden. If the SSID profile is used by access points deployed in different geographies, then the corresponding geography-specific Google domain must be included in the walled garden.
- appleiphonecell.com
- captive.apple.com
- itools.info
- ibook.info
- airport.us
- thinkdifferent.us
Site for Payment Gateway
If you use the Paid or the Free + Paid option, you are using a payment gateway. Some scripts from the payment gateway do not load in Android native web view (i.e. the native browser that Android uses). To avoid this, you must add ssl.gstatic.com to the Walled Garden list of the captive portal. if you do not add this entry to the Walled Garden, users see an error message saying that the page could not be loaded and asking them to use a different browser.
Sites based on Content
| Content Type | Walled Garden Entries |
|---|---|
| Vimeo | vimeo.com
vimeocdn.com google-analytics.com |
| PollDaddy | polldaddy.com |
| YouTube | youtube.com
googlevideo.com ytimg.com google.com googleusercontent.com (for thumbnail images) lh5.googleusercontent.com (for thumbnail images) |
Configure Access Point Hosted Captive Portal
- Navigate to
- Select the Captive Portal check box to display a portal page to be shown to the client on using the guest network.
- Select the mode of access as AP Hosted to the internet through the captive portal.
- Click Download Sample to download the factory default portal bundle file.
- Click Upload Custom Splash Page Bundle to upload the bundle.
Info:The bundle must be a .zip file of the portal page along with any other files like images, style sheets and upload this file. The zip file must satisfy the following requirements for the portal to work correctly:
- The zip file should have a file with the name "index.html" at the root level (i.e., outside of any other folder). This is the main portal page. It can have other files and folders, (and folder within folders) at the root level that are referenced by the index.html file.
- The total unzipped size of the files in the bundle should be less than 100 KB. In case, large images or other content is to be displayed on the page, this content can be placed on an external web server with references from the index.html file. In this case, the IP address of the external web server must be included in the list of exempt hosts (see below).
- The index.html file must contain the following HTML tags for the portal to work correctly:
- A form element with the exact starting tag: <form method="POST" action="$action">
- A submit button inside the above form element with the name "mode_login". For example: <input type="image" name="mode_login" src="/images/login.gif">. The exact tag: <input type="hidden" name="redirect" value="$redirect"> inside the above form element.
- Select HTTPS Redirection if you wish to move to secure version of HTTP. Enabling HTTPS Redirection enables three fields, these three fields provide the information of the customer using the certificate.
- Common Name: Identifies the host name associated with the certificate.
- Organization: Name of an organization.
- Organization Unit: Name of an organizational unit.
- Enter the list of Websites that users can access before login.
- For Post Login configuration enter details for the below fields:
- Specify the Redirect URL. The browser is redirected to this URL after the user clicks the submit button on the portal page. If left empty, the browser is redirected to the original URL accessed from the browser for which the portal page was displayed.
- Specify Login Timeout, in minutes, for which a wireless user can access the guest network after submitting the portal page. After the timeout, access to guest network is stopped and the portal page is displayed again. The user has to submit the portal page to regain access to the guest network. If the user disconnects and reconnects to the guest network before his session times out, he does not have to enter his credentials on the splash page.
- Specify Blackout Time, in minutes. This is the time for which a user is not allowed to login after his previous successful session was timed out. For example, if the session time-out is 1 hour and the blackout time is 30 minutes, a user will be timed out one hour after a successful login. Now after this point, the user will not be able to login again for 30 minutes. At the end of 30 minutes, the user can login again.
- Select Detect when Internet connection is down and inform guest users, if you want to check the internet connectivity and inform guest users in case of loss of Internet connectivity.
Configure Cloud Hosted Captive Portal
This is the default option when you first access the SSID > Captive Portal tab. With this option, the captive portal is hosted on Arista Cloud.
- Go to
- Select Captive Portal.
- Design the splash page. See Design a Splash Page for details.
- Configure the plugins you want to use. The default plugin is Clickthrough. The settings are different for different plugins. For information on these settings, see:
- Select Skip Splash Page and the Duration in days, if you want to skip presenting the splash page to the user for that duration.
- Select HTTPS Redirection if you wish to move to secure version of HTTP. Enabling HTTPS Redirection enables Certificate Information section. This section provides the information of the customer using the certificate.
- Enter the valid information for the below fields from Certificate Information section.
- Common Name: Identifies the host name associated with the certificate.
- Organization: Name of an organization.
- Organization Unit: Name of an organizational unit.
- Enter the Websites that users can access before login. This is the Walled Garden of sites that you are allowing the user to access before login. For best results with captive portal, we recommend that you add some sites to the walled garden. See Walled Garden Sites for Captive Portal.
- Configure the Post Login parameters.
- Redirect URL to which you want to redirect the user.
- Login Timeout after which the user's login expires.
- Blackout Time which is the time period for which a user cannot log in to the portal after the last successful login has timed out.
- Select if you want the AP to detect when the internet is down and inform users.
- Click Save to save the SSID or Save & Turn SSID On to save and turn it on.
Guest Wi-Fi User Authentication with Host Approval
- The guest user connects to the SSID and is redirected to a splash page. The guest user registers on the splash page by providing his contact information and the email address of the host. The guest user account information is stored in the guestbook of the portal.
- The user is shown a message that the request has been sent for approval.
- The host receives an email for the registration performed by the guest user.
A sample email is displayed as follows:
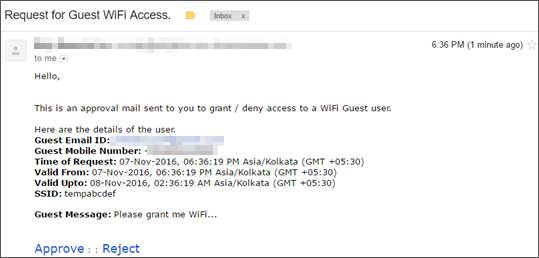
- Once the host clicks Approve in the email, the guest user will receive an approval message. If the approval is granted within 5 minutes from the time of request, the guest user can access Wi-Fi without logging in again. The login page is displayed as follows:
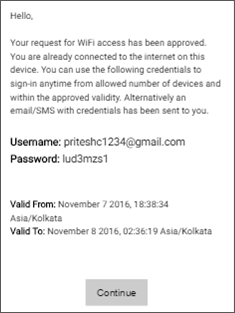
The guest user is automatically logged in after clicking Continue.
- If the request approval is granted after 5 minutes, the guest user must explicitly log in using the provided username and password. The guest user must click Click Here to Login to authenticate and access Wi-Fi.
Design a Splash Page
The Cloud Hosted captive portal comes with a default splash page. You can edit this splash page.
You must select Cloud Hosted captive portal under to edit the splash page.
- Click the "pen" (edit) icon on the Splash Page section.
- Expand the Logo option to add your logo to the splash page.
- Click Upload Logo Image and select the logo image you want to upload.
- You can use the slider below the image to adjust the size of the logo.
- Expand the Background Image option to add your background image to the splash page.
- Click Upload Image and select the background image you want to upload.
- Expand the Background Color option.
- Select the background color from the color bar on the right.
- Select the exact shade of the color by clicking at a particular location on the rectangle.
- Set the level of Transparency using the slider below the color pane. The rgba values below the slider correspond to the color, shade and the transparency level you select. RGBA stands for Red, Green, Blue and Alpha, where Alpha is the transparency parameter (0 - fully transparent, 1 - fully opaque).
- Expand the Terms of Use option to define the terms of use.
- Enter the Title for the terms of use.
- Enter the Body of text for the terms of use.
- Expand the Privacy Policy option.
- Enter the Title of the privacy policy.
- Enter the Body of the privacy policy.
- Expand the Text option. You can use this to enter your caption or welcome message (e.g. "Enjoy Free Wi-Fi") and your copyright info.
- Enter the Plugin Title. This is your caption or welcome message.
- Enter the Copyright text.
- Click Save.
Configure Common Settings for Plugins
Common settings are system wide — they are applicable not only across plugins within an SSID captive portal, but also across SSIDs and across locations. Common settings include settings for email, SMS and payment gateway accounts used to communicate with your Wi-Fi users.
Configure Email Account Settings
This is the email account used to communicate with your Wi-Fi users.
You must select Cloud Hosted captive portal under SSID > Captive Portal to configure common settings.
- On the tab, click Select login method for guest WiFi users.
- Click the "gear" icon for Common Settings.
- Click the "envelope" icon for Email Account.
- Select the Email Service Type.
- If you select System Email:
- Enter the From Email ID and the From Name. These will appear in the "From" field of the email the user gets.
- Enter the Return Email ID. This is the email ID to which the user can send a response. You can test by clicking Verify to receive a test message on the return ID.
- If you select SMTP Configuration:
- Enter the From Email ID and the From Name. These will appear in the "From" field of the email the user gets.
- Enter the Return Email ID. This is the email ID to which the user can send a response.
- Enter the SMTP Server Host name or IP address.
- Enter the Server Port number of the SMTP server.
- Select the Login Method for the SMTP server.
- Enter the Login Username and the Login Password for the SMTP server.
- Select the Connection Security type for the connection to the SMTP server.
- If you select System Email:
- You can enter a Test Account and click Send Test Email to verify that the configuration works.
- Click Save to save the configuration.
Configure SMS/MMS Account Settings
This is the SMS / MMS account used to communicate with your Wi-Fi users.
Select Cloud Hosted captive portal under SSID > Captive Portal to configure common settings.
- On the tab, click Select login method for guest WiFi users.
- Click the "gear" icon for Common Settings.
- Click the "message" icon for SMS / MMS Account.
- Under the Account option, select an existing account or select Add New to add a new account.
- Provide an account name.
- Select a Service Provider.
Info:You can select Twilio, Msg91 or a custom service provider. The configuration varies depending on your choice.
- If you select Twilio, enter the Account SID, the Auth Token and the Twilio Number.
- If you select Msg91, enter the Username, Password, and Sender ID, and select the SMS Route.
- If you select Custom, enter the Service URL.
- Enter a Test Account number, provide the DLT Template ID, and Test SMS Settings to verify that the configuration works.
- Click Save to save the configuration.
Configure Payment Gateway Settings
This is the payment gateway used to bill users when you select Paid or Free + Paid Wi-Fi.
- On the tab, click Select login method for guest WiFi users.
- Click the "gear" icon for Common Settings.
- Click the "two coins" icon for Payment Gateway.
- Under the Stripe Account option, select an existing account or select Add New to add a new account.
- Enter a Name for the account.
- Open the Stripe website in a new tab and login to your Stripe account.
- On the Stripe home page, click API on the left navigation menu.
Note: If you were already logged in to Stripe, you need to logout and log back in to be able to access the API menu.
- Copy the Live Publishable Key and the Live Secret Key from the Stripe API menu, and paste them in the respective fields in the payment gateway settings in CV-CUE.
- Click Save to save the configuration.
Configure Clickthrough Plugin
The Clickthrough plugin has no authentication, only a Welcome or Terms-of-Use type page on which the user can click and access Wi-Fi.
You must select Cloud Hosted captive portal under to configure plugins.
- On the tab, click Select login method for guest WiFi users.
- Select Clickthrough and click the edit icon (pencil) to edit settings.
- Configure the Common Plugin Settings.
- Click Save.
- Click Save on the Plugin & QoS page to save the clickthrough settings.
- Save the SSID.
Configure SAML
You can integrate SAML SSO with a captive portal for authentication.
- Navigate to tab.
- Select the Captive Portal checkbox and select Cloud Hosted from the dropdown list.
- In Authentication Plugins and Quality of Service, click SAML in Custom.
- From the right panel, click the Custom > SAML checkbox and click the SAML logo. You can add your custom logo or keep the default logo. The SAML Settings right panel opens.
- Provide the display name. Users will see this name on the splash page. A maximum of 15 characters, including spaces, is allowed for the display name.
- (Optional) Upload a logo for the SAML icon. Once uploaded, you will see this logo appear in the previous screen.
- Click the Download SP Metadata XML link and share the downloaded metadata with the identity provider.
- Provide the metadata information received from your IDP Vendor. You can add the metadata manually or upload an XML with all the metadata details. To add metadata manually, provide these information:
- Entity ID — The ID of the SAML SSO identity provider (IDP).
- Login URL — The URL of the IDP application.
- Hash Algorithm
- Upload Certificate — Certificate used by the IDP to sign or encrypt the data.
- To upload the metadata, click Upload XML and upload the XML file from your local or shared drive.
- Provide a mapping between SAML attribute and target attribute. The SAML attributes are predefined attributes that users see on the UI. The Target attributes are attributes defined by the identity service provider.
- Define the Quality of Service parameters:
- Login Timeout
- Blackout Time
- Limit the maximum download bandwidth to
- Limit the maximum upload bandwidth to
- Specify the redirect URL. Users will be redirected to this URL after authentication.
Note: There is another redirect URL field in the Post Login section in Captive Portal settings. If both the fields have different redirect URLS, then the URL defined in the SAML settings page takes precedence over the general Captive Portal redirect URL settings.
- Save the SAML settings and then save the Captive Portal settings.
Configure OpenID Connect
You can integrate OpenID Connect with a captive portal for authentication. .
- Navigate to tab.
- Select the Captive Portal checkbox and select Cloud Hosted from the dropdown list.
- In Authentication Plugins and Quality of Service, click Custom.
- From the right panel, click the Custom > OpenID Connect radio button and click the OpenID Connect logo. You can either keep the default logo or add your custom logo in the next screen. The OpenID Settings right panel opens.
- Provide the display name. Users will see this name on the splash page. A maximum of 15 characters, including spaces, is allowed for the display name.
- (Optional) Upload a logo for the OpenID Connect icon. Once uploaded, you will see this logo appear in the previous screen.
- Specify the login details for the OpenID Connect account:
- Client ID — The client ID or login ID of your OpenID Connect account. It is used to identify your application on IDP.
- Client Secret — The password of your OpenID Connect account. Client secret ensures that the access tokens are granted to authorized applications only. By adding the client secret in SSID settings, we ensure that our application is considered as authorized by the IDP.
- Issuer URL — The URL of the OpenID server. This is the landing page url of the IDP. The user gets to the sign-in page through this URL.
Note: The maximum character limit for all the three fields is 200 characters. - Define the Quality of Service parameters:
- Login Timeout
- Blackout Time
- Limit the maximum download bandwidth to
- Limit the maximum upload bandwidth to
- Specify the redirect URL. Users will be redirected to this URL after authentication.
Note: There is another redirect URL field in the Post Login section in Captive Portal settings. If both the fields have different redirect URLS, then the URL defined in the SAML settings page takes precedence over the general Captive Portal redirect URL settings.
- Save the OpenID settings and then save the Captive Portal settings.
Access Wi-Fi Using Social Media Plug-Ins
The figure below explains how Arista authenticates the guests using social media plug-ins.
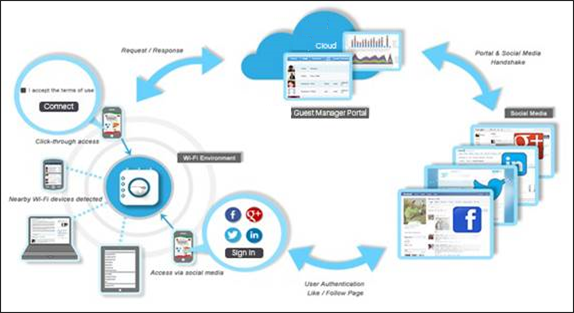
When guests try to access the Wi-Fi through an Access Point (AP), the captive portal page is displayed. The portal provides options for authenticating with social media accounts. When a guest chooses a social media to authenticate, the portal redirects the user to the social media login page for his social media account credentials. The social media validates the user account credentials. If successful, the portal and the social media exchange certain information and perform a handshake. The user is requested for permission to share some of the information in his social media account with the social media App. The social media checks whether the user Likes or Follows your page on the social media and, if not, requests the user to Like or Follow your page. The AP then opens the gate for the users to access the Internet.
Configure Social Media Plugins
Configure Facebook Plug-In
To configure the Facebook plug-in on your captive portal, you need to know App ID and App Secret of your Facebook App.
- Navigate to
- Select Facebook.
- Enter App ID provided by Facebook to communicate with the Facebook API.
- Enter App Secret.
- Select Display Like Page if you wish the guests must Like your Facebook page when they authenticate using their Facebook account credentials.
- Enter Like Page URL of the the Facebook page that guests see and can 'Like'.
- Select Extended Profile Permissions if you want to ask the guest user for permission to access additional information such as email address, birthday, likes and location.
Info: If selected, the user is asked for permissions to access above-mentioned information from the user profile. Select the check boxes for the information fields (Email address, Birthday, Likes, Location) that you want to request access for from the guest user.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure Twitter Plug-In
You can configure Twitter plug-ins on your captive portal. You must have the Administrator role to configure the Twitter plug-ins. Before you configure the Twitter plug-in you must ensure that you have created your application/ project in the social media.
- Navigate to
- Select Twitter.
- Enter Customer Key provided by Twitter to communicate with the Twitter API.
- Enter Customer Secret.
- Select Display Follow Page if you wish the guests must Follow you on Twitter when they authenticate using their Twitter account credentials.
- Enter the Follow Page URL for the Twitter page that the guests can see and 'Follow'.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure LinkedIn Plug-In
You can configure LinkedIn plug-ins on your captive portal. You must have the Administrator role to configure the LinkedIn plug-ins. Before you configure the LinkedIn plug-in you must ensure that you have created your application/project in the social media.
- Navigate to
- Select LinkedIn.
- Enter App ID provided by LinkedIn to communicate with the LinkedIn API.
- Enter Secret Key.
- Select Display Follow Page if you wish the guests must Follow you on LinkedIn when they authenticate using their LinkedIn account credentials.
- Enter the Follow Page URL to be displayed to the guest.
- Select Extended Profile Permissions if you want to ask the guest user for permission to access additional information such as Email Address.
Info:If selected, the user is asked for permissions to access above-mentioned information from the user profile. Select the check boxes for the information fields (Email address) that you want to request access for from the guest user.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure Foursquare Plug-In
- Navigate to
- Select Foursquare.
- Enter Client ID provided by Foursquare to communicate with the Foursquare application that uses OAuth 2.0 protocol to call Foursquare APIs.
- Enter Client Secret.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure Google+ Plug-In
To configure the Google+ plug-in:
- Navigate to
- Select Google+.
- Enter the Client ID provided by Google+ to communicate with the Google+ application that uses OAuth 2.0 protocol to call Google APIs.
- Enter the Client Secret.
- Enter an API Key generated by Google+ for each project and is used to communicate with other APIs enabled in the project.
- Select Extended Profile Permissions if you want to ask the guest user for permission to access additional information such as email address, and advanced profiles.
Info:If selected, the user is asked for permissions to access above-mentioned information from the user profile. Select the check boxes for the information fields(Email address, and Advanced Profiles) that you want to request access for from the guest user.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure Instagram Plug-In
- Navigate to
- Select Instagram.
- Enter Client ID provided by Instagram to communicate with the Instagram application that uses OAuth 2.0 protocol to call Instagram APIs.
- Enter Client Secret.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Click Save.
Configure Okta Plug-In
You must be an Administrator to configure the Okta plug-in on your captive portal. Before you configure the plug-in, ensure that you have created your application/project in the social media.
- Log in to CV-CUE, and go to
- Create a new SSID or edit an existing SSID. Click the Captive Portal tab.
- Click the Captive Portal check box and then ensure that Cloud Hosted is selected from the drop-down list.
- Click Social in the Authentication Plugins and Quality of Service tile.
- Select the Okta check box under the Social check box.
- Configure the Client ID, Client Secret and Organization Domain. Use the values that you have previously noted during Okta Configuration.
- Refer Configure Commom Social Media Plugin Settings for Quality of Service and Redirect URL configuration.
- Save the Okta configuration and then save the SSID configuration.
Configure QOS and Redirect Settings
Quality of Service and Redirect URL are the two common settings to be configured for every plugin.
To know more about the below configuring parameters refer QoS Settings for Plugins.
- Scroll down to Quality of Service on Social Media Plugin Settings page.
- Enter the Login Timeout.
- Enter the Blackout Time.
- Enter Limit the maximum download bandwidth to.
- Enter Limit the maximum upload bandwidth to.
- Enter Custom URL in Redirect URL section.
Configure Username Password Plugin
With the Username/Password plugin, you can allow users to self-register or have them use Guestbook, i.e., admin generated credentials.
You must select Cloud Hosted captive portal under to configure plugins.
- On the tab, click Select login method for guest WiFi users.
- To let users self-register, select Allow Guest Users to Self-Register.
- Select the option you want to use for self-registration.
- Select Free Wi-Fi to allow free Wi-Fi access to users. Click on the "gift" icon to configure the free Wi-Fi. With free Wi-Fi you can:
- Allow self-registered users to set password
- Enable Forgot Password Link
- Allow guest users to activate expired account
- Allow self-registered guest users to auto login
- Show credentials to a self-registered guest user on a webpage
- Select Paid Wi-Fi to have users pay for Wi-Fi access. Click on the "$" icon to configure paid Wi-Fi. With paid Wi-Fi, you can do all of the things listed in free Wi-Fi above, such as allow self-registered users to set password, enable forgot password link, etc. Additionally, you can define Payment Tiers for a payment gateway to bill users. The steps are:
- If you have not yet configured a payment gateway, you must do so before you can proceed any further. Click Configure to set up a payment gateway. See Configure Payment Gateway Settings for details.
- Select Currency for payment
- Click the "+" icon to Add Tier.
- Configure the Amount, and the access Duration for this amount.
- Enter the Email Content you want to include as part of the paid Wi-Fi welcome message.
- Enter the SMS Content you want to include as part of the paid Wi-Fi welcome message.
- Select Free & Paid Wi-Fi to offer users free access for some time and then charge them. The configuration is essentially a combination of the items in the free Wi-Fi and the paid Wi-Fi cases. The only additional task is that you need to define the initial period for which the Wi-Fi is free and how often you want to renew this free period. The steps for this task are:
- Expand the Free for first option.
- Enter the Free WiFi Duration.
- Select Renew Every and enter the period after which you want to renew the free access.
Note: Some scripts from the payment gateway do not load in Android native web view (i.e. the native browser that Android uses). To avoid this, you must add ssl.gstatic.com to the Walled Garden list of the captive portal. if you do not add this entry to the Walled Garden, the user sees an error message saying that the page could not be loaded and asking them to use a different browser. - Select Host Approval for users to request host approval vie email. To understand how this works, see Guest WiFi Authentication with Host Approval. Click on the host approval icon (person with tick mark) to configure the Host Approval Settings. For host approval settings:
- Enter the Email domains to receive approval requests for guest access. With this you can ensure that requests are only sent to authorized domains.
- You can define approvers by entering Approver Email Addresses.
Additionally, you can:- Allow guest users to skip host's email on splash page
- Allow self-registered guest users to auto login
- Show credentials to a self-registered guest user on a webpage
- Select Free Wi-Fi to allow free Wi-Fi access to users. Click on the "gift" icon to configure the free Wi-Fi. With free Wi-Fi you can:
- To use a Guestbook to authorize logins, select Admin Generated Credentials.
Note: You can use the Guestbook icon only after you have saved the SSID.
- Click on the Guestbook icon.
Info:This opens a new Guest Manager tab in your browser, where you can define new guest Wi-Fi accounts. For details on how to configure Guestbook, see the Guest Manager User Guide.
- Click Save.
- Click Save on the Plugin & QoS page to save the plugin settings.
- Save the SSID.
Configure Passcode Through SMS Plugin
In this method, users provide their mobile numbers and receive a passcode for Wi-Fi access via SMS.
You must select Cloud Hosted captive portal under to configure plugins.
- On the tab, click Select login method for guest WiFi users.
- Select Passcode through SMS and click the edit icon (pencil) to edit settings.
- Select the limit for the maximum number of devices per user.
- Select the Passcode Length and the Passcode Validity.
- Select the parameters for re-sending the SMS: the limit for the maximum number of times you want the SMS to be re-sent, and the minimum time interval that must elapse before an SMS is re-sent.
- Enter the text to be sent to guest users in the SMS.
- Enter the DLT Template ID. The DLT Template ID is provided by the SMS service provider.
- Configure the Quality of Service settings and the Redirect URL. See Common Plugin Settings.
- Click Save.
- Click Save on the Plugin & QoS page to save the clickthrough settings, and then save the SSID.
Configure Webform Plugin
This is an enhanced form of clickthrough. There is no authentication but users fill out their details such as name, email, and contact number.
You must select Cloud Hosted captive portal under to configure plugins.
- On the tab, click Select login method for guest WiFi users.
- Select Webform and click the edit icon (pencil) to edit settings.
- For each Field (e.g. First Name), select whether you want to Display the field on the webform and whether you want the field to be Mandatory.
- Configure the Common Plugin Settings.
- Click Save.
- Click Save on the Plugin & QoS page to save the clickthrough settings.
- Save the SSID.
Configure External RADIUS Plugin
In this method, authentication happens via an external RADIUS server.
- On the tab, click Select login method for guest WiFi users.
- Select External RADIUS. The 802.1X Settings appear. For an explanation of these settings, see 802.1X or RADIUS Settings.
- For common plugin settings, click the edit icon (pencil).
Info:The External RADIUS Settings window appears. For details on these settings, see Common Plugin Settings.
- Select the Authentication Server.
Info:If you have not yet added any RADIUS servers, you can do so by clicking Add / Edit. The RADIUS Server Settings window appears. For details on how to add a RADIUS server, see Configure RADIUS Profile.Note: You must select at least one Primary Authentication server. Optionally, you can select a Primary Accounting sever and Secondary Authentication and Accounting servers as well.
- Select the Accounting Server.
Info:If you have not yet added any RADIUS servers, you can do so by clicking Add / Edit. The RADIUS Server Settings window appears. For details on how to add a RADIUS server, see Configure RADIUS Profile.
- Select the Accounting Interval.
- Enter the Called Station and NAS ID values.
Note: No two SSIDs on the same AP should use the same NAS ID.
- Click Save.
- Click Save on the Plugin & QoS page to save the plugin settings, and then save the SSID.
QoS Settings for Plugins
| Field | Description |
|---|---|
| Login Timeout | The time period after which the guest user session for the portal expires. The user must re-authenticate with his login credentials if he wants to continue using the Wi-Fi service. "0" indicates that the user session does not timeout and the user must explicitly log out from the portal. A non-zero timeout configured on the plug-in takes precedence over the timeout configured on the SSID profile. The time period, can be specified in Hours, Minutes, Days, Weeks or Months. |
| Blackout Time | The time period for which a user cannot log in to the portal after the last successful login has timed out. "0" indicates no blackout time. The blackout time configured on the plug-in takes precedence over the blackout time configured on the SSID profile. The time period, can be specified in Hours, Minutes, Days, Weeks or Months. |
| Redirect URL | The URL of the page to which the guest user must be redirected to on successful login from the portal using the plug-in. |
| Max Download Bandwidth | Maximum download bandwidth, in Kbps or Mbps, for this plug-in on the portal. |
| Max Upload Bandwidth | Maximum upload bandwidth, in Kbps or Mbps, for this plug-in on the portal. |
Configure Third-Party Hosted Captive Portal
- Navigate to .
- Select Captive Portal to display a portal page to be shown to the client on using the guest network.
- Select the mode of access as Third-Party Hosted.
- To configure basic settings within Third-Party Hosted do the following:
- Select With RADIUS Authentication.
Info: The guest user is authenticated by a RADIUS server, when he logs in to the external portal. Once you select With RADIUS Authentication a link to configure 802.1X Settings.
- To configure 802.1X Settings, see Configure External RADIUS Plugin.
- Enter Splash Page URL.
- Enter a Shared Secret for SSID-external portal communication.
- Select HTTPS Redirection if you wish to move to secure version of HTTP.
Info:Enabling HTTPS Redirection enables three fields, these three fields provide the information of the customer using the certificate.
- Common Name: Identifies the host name associated with the certificate.
- Organization: Name of an organization.
- Organization Unit: Name of an organizational unit.
- Enter Websites that users can access before login..
- Select With RADIUS Authentication.
- For Post Login configuration enter details for the below fields:
- Specify the Redirect URL.
Info:The browser is redirected to this URL after the user clicks the submit button on the portal page. If left empty, the browser is redirected to the original URL accessed from the browser for which the portal page was displayed.
- Specify the value of the Service Identifier.
- Specify Login Timeout, in minutes, for which a wireless user can access the guest network after submitting the portal page.
Info:After the timeout, access to guest network is stopped and the portal page is displayed again. The user has to submit the portal page to regain access to the guest network. If the user disconnects and reconnects to the guest network before his session times out, he does not have to enter his credentials on the splash page.
- Specify Blackout Time, in minutes.
Info:This is the time for which a user is not allowed to login after his previous successful session was timed out. For example, if the session time-out is 1 hour and the blackout time is 30 minutes, a user will be timed out one hour after a successful login. Now after this point, the user will not be able to login again for 30 minutes. At the end of 30 minutes, the user can login again.
- Select the Detect when Internet connection is down and inform guest users, if you want to check the internet connectivity and inform guest users in case of loss of Internet connectivity.
- Specify the Redirect URL.
- To configure Advanced Portal Parameters refer Request and Response Parameters.
- Click Save.
Request and Response Parameters
| Request Attributes | Description |
|---|---|
| Request Type | Field name for request type field. |
| Challenge | Field name for random text used for authentication. |
| Client MAC Address | Field name for the MAC address of the client. |
| Access Point MAC Address | Field name for MAC address of the access point that is communicating with the external portal. |
| Access Point IP Address | Field name for the IP address of the access point that is communicating with the external portal. This should match the field name used by the external portal. |
| Access Point Port Number | Field name for the AP port number on which the AP and external server communicate. |
| Failure Count | Field name for the count of the number of failed login attempts. |
| Requested URL | Field name for the requested URL that is the URL requested by the client through the AP, to the external server. |
| Login URL | Field name for the login URL. |
| Logoff URL | Field name for the logoff URL. |
| Remaining Blackout Time | Field name for the remaining blackout time. |
| Service Identifier | Name of the portal parameter that is used to pass the service identifier value to the external portal. The service identifier value is specified in the Captive Portal section of the SSID Profile. This parameter can be used by the external portal to implement SSID profile specific functionality like different portals for different SSIDs etc. |
| Response Attributes | |
| Challenge | Field name for the challenge |
| Response Type | Field name for the response type. |
| Challenge Response | Field name for the challenge response. |
| Redirect URL | Field name for the redirect URL |
| Login Timeout | Field name for login timeout. |
| User name | Field name for user name. |
| Password | Field name for password. |
SSID RF Optimization
The RF (Radio Frequency) Optimization tab is where you can enable RF related optimizations on the SSID.
Enforce Steering is enabled by default . Some clients directly send Association Request packets by listening to beacons. Enforce Steering causes an AP to reject such requests on 2.4GHz, thereby force-steering clients to 5GHz.
You can enable 802.11k Neighbor List. This allows clients to request neighbor lists from APs, which speeds up roaming. See 802.11k Use Case for details. When you enable 802.11k, you can select Neighbor List Dual Band if you want the AP to send the client neighbor information on both bands. While 802.11k defines methods that help individualclients understand their radio environment, 802.11v defines services that help improve overall network performance. See 802.11v Use Case for details.
Address Resolution Protocol (ARP) is an IPv4 protocol used to resolve a device’s IP address to its physical MAC address so communication can occur on the Layer 2 segment. A device sends an ARP broadcast packet containing an IP address, in effect asking who on the Layer 2 segment knows which MAC address is associated with that IP address. A client may also send an ARP broadcast that contains its own IP and MAC address to update Layer 2 device ARP tables. IPv6 does not use broadcast packets, it uses a Neighbor Discovery Protocol (NDP). NDP uses multicast to resolve addresses and to find other network resources.
An AP can act as a proxy for the wireless clients associated to it. When you enable Proxy ARP and NDP, the AP itself responds to the ARP and NDP requests instead of forwarding them and transmitting them at a low, basic data rate. Downstream Group-Addressed Forwarding (DGAF) blocks all broadcast/multicast traffic from the wired to the wireless side. It is used only with Hotspot 2.0. You can disable it by selecting Disable DGAF.
When you enable Broadcast/Multicast Control, the AP blocks broadcast/multicast packets from Ethernet to wireless. This cleans up the RF airspace is by blocking unnecessary traffic. You can also block broadcast/multicast packets from wireless to Ethernet by selecting Block Wireless to Wired. Broadcast / Multicast Control should be used carefully as many network functions use broadcast packets for basic operations.
For applications that must be allowed to use broadcast / multicast packets, you can create an exemption by adding the protocol information to the Exemption List.
Bonjour is an Apple protocol designed to make Bonjour-enabled devices and services easy to use and configure over the network. Bonjour makes heavy use of broadcast and is essential for Apple products. You can select Allow Bonjour to automatically apply an exemption.
IGMP Snoopingis a mechanism to prune multicast packets so that they are forwarded only to ports on which clients have subscribed. This saves bandwidth by avoiding unnecessary packet flows. For details, see IGMP Snooping.
Target Wake Time (TWT) is one of the advanced features of Wi-Fi 6. It enables access points (AP) and stations (STAs) to negotiate schedules for active and sleep durations.
802.11k - Use Case
The IEEE 802.11k amendment, also called Radio Resource Measurement (RRM), defines methods allowing stations to inform each other about their respective radio frequency (RF) environments. That way, they can make faster and better informed decisions on roaming. With 802.11k, a client can request an Arista AP to send a Neighbor Report. In case of the client in the above figure, it requests a Neighbor Report from AP1. It is basically asking AP1, “Which APs are advertising my current SSID? What channels are these APs operating on? What are their signal strengths as you see them?” AP1 reports on all the APs it can sense that are advertising this SSID. Suppose there are 4 such neighbors in the 5GHz band (AP2 through AP5 in the figure). The client then receives a Neighbor Report containing 4 candidate channels to scan. At 100ms a channel, the client can decide in under half a second which AP to move to. It no longer needs to spend 2.1 seconds scanning all available channels for target APs.
| 5GHz (w DFS) | All Channels | 11k Neighbors |
|---|---|---|
| Channels to scan | 21 | 4 |
| Scan Time | 2.1s | 400ms |
802.11v - Use Case
Consider a client connected to an AP. The signal strength from the client could drop below a configured threshold, or the network’s load balancing algorithm might decide that a different AP can serve the client better. In such situations, an AP might disassociate with the client. This can be an unexpected shock to a client, causing it to go through a complete scan before selecting an AP to associate with. This could cause poor user experience, especially for real-time applications.
The IEEE 802.11v amendment is also called Wireless Network Management (WNM). As the name suggests, 802.11v has a broader scope than 802.11k. While 802.11k defines methods that help individual clients understand their radio environment, 802.11v defines services that help improve overall network performance.
An important service is BSS Transition Management (BSTM). When an Arista AP decides to disassociate with a client, it sends an 802.11v frame called a BSTM Request. It is basically the AP warning the client, “Beware. I am going to disassociate in 60 seconds.” (The actual time interval is configurable.) This is called an Unsolicited Request. It allows a client some time to find and associate with another AP. The message includes a list of neighboring APs on the same ESS that the client can associate with. In an 802.11v message called the BSTM Response, the client can accept or reject the AP's request. It can also ask the AP for more time – the BSTM Response message includes a BSS Termination Delay field. Essentially, it is the client saying, “60 seconds is too short. Let us disassociate after 3 minutes”. The AP honors this request.
Note that with 802.11k, only a client can request a Neighbor List. With 802.11v, however, either the client or the AP can initiate a conversation about transitioning. So, a client can send a BSTM Query asking an Arista AP, “Should I associate with a different AP? If yes, which one?” Depending on its implementation, the client may send this query periodically or based on triggers such as low signal strength. The AP responds with a BSTM Request - called a Solicited Request - containing the list of recommended APs the client can associate with.
Every time an Arista AP sends an 802.11v frame, it does not necessarily want to disassociate. It might simply want to nudge the client into looking for another AP by sending a BSTM Request with the list of neighbors but without a disassociation warning. This could happen, for instance, if a neighbor AP is less loaded and close enough. Since 802.11v has a network-wide view of things, it might recommend (but not force) the client to move to the less loaded AP. To allow this, 802.11v provides a Disassociation Imminent flag bit, which indicates whether the AP intends to disassociate with the client.
Configure RF Optimization in SSID Profile
- Select types of steering you want to enable. Types of steering are:
- Smart Client Load Balancing
- Smart Steering
- Min Association RSSI
- Band Steering
- Enforce Steering
- You can enable 802.11k Neighbour List, 802.11v BSS Transition and 802.11r (Fast Transition). By default these standards are disabled. Enabling these standards enables few new sub fields.
- If you enable 802.11k Neighbour List, you can also optionally enable Neighbor list for all bands - Both 2.4 GHz, 5 GHz, and 6 GHz.
- If you enable 802.11v BSS Transition, you must enable the Disassociation Imminent and configure it in the Disassociation Timer field. This is the time after which the client will be disconnected from the AP. The Disassociation Timer is expressed in number of beacon intervals. The range of the Disassociation Timer should be between 10 to 3000 TBTT (Target Beacon Transmission Time). Once the Disassociation Timer reaches zero, then the client can be disassociated based on the Force Disconnection setting.
- You can select Force Disconnection to forcefully disconnect the client after the disassociation timer expires. The client will be disconnected even if it responds with a negative BSS transition response. When Force Disconnection is not selected, the AP does not disconnect the client (but waits for the client to disconnect on its own).
- If you enable 802.11r, you can optionaly enable Mixed Mode. By enabling Mixed Mode, you allow both 802.11r capable and incapable clients (clients that do not support 802.11r) to connect to this SSID.
- Select Proxy ARP and NDP.
Info:When you enable Proxy ARP and NDP, then the AP filters downstream ARP (IPv4) and NDP (IPv6) packets and also responds as appropriate on behalf of wireless clients to conserve wireless bandwidth. Enabling Proxy ARP and NDP enables a field that allows you to Disable DGAF.
- Select Disable DGAF.
Info: It is applicable only for Hotspot 2.0. If you enable this option, then AP starts proxy ARP for IPv4 and proxy NDP for IPv6. It also drops all Multicast and Broadcast packets in the transmit path. Selecting this option disables Broadcast/Multicast control and IGMP Snooping.
- Select Target Wake Time, Broadcast/Multicast Control, IGMP Snooping.
- Click Save.
IGMP Snooping
Multicast is often used to stream video. Multicast packets need to flood the network to reach their recipients. Multicast packets are forwarded to many network segments. Video streaming packets, for example, could end up being sent to segments with no video streaming clients. These packets waste network bandwidth. The Internet Group Membership Protocol (IGMP) protocol was developed to cull such wasteful data. IGMP provides a way for a client to inform the Layer 2 device it is connected to that it wants to receive a multicast stream. A client does this by sending an IGMP Report with the multicast address of the multicast session it wants to join. Layer 2 devices use IGMP Snooping to look at multicast packets and match them to a list of multicast addresses that clients have joined. IGMP and IGMP snooping are effective ways to prune multicast packets so that they are forwarded only to ports on which clients have subscribed. When you enable IGMP Snooping, the AP blocks multicast traffic from Ethernet to wireless. To receive multicast packets, a client must send an IGMP Report with the address of the multicast group it wants to join (IGMP Report - Join).
The client application is responsible for sending the IGMP Report. If the client application does not support IGMP (e.g. legacy applications), you can still enable IGMP snooping. But you need to add the multicast address that the application uses to the IGMP Snooping Exception List. This will allow multicast traffic for that application to flow. When you add an address to the exception list, all APs using the SSID forward all multicast packets with that address, regardless of whether a client sent an IGMP Report to join. You can add a maximum of 30 multicast addresses to the exception list.
When a client receiving multicast packets roams to another AP, the snoop table is forwarded. The client does not need to send a new IGMP Report to join. Convert Multicast to Unicast converts multicast packets to unicast, except for the addresses in the exception list.
| Feature | Description | Default | Range |
|---|---|---|---|
| IGMP Snooping | Enables IGMP Snooping | Enabled | |
| IGMP Snooping Exception List | Allow multicast to be delivered without client sending an IGMP Report (Join) | 30 Max |
| Feature | Restrictions |
|---|---|
| IGMP Snooping | Enabled by default
Based on client IGMP Report (Join) Enable – blocks multicast, Disable – forwards all multicast Applies to multicast going from Ethernet to wireless Independent of multicast/unicast conversion Snoop table forwarded when client roams AP does not send IGMP Query |
| IGMP Snoop Protected Address | Max 30 multicast addresses
Internal protected addresses 224.0.0.1/24 – query for all systems 224.0.0.22/24 – IGMP v3 addresses Not converted to unicast even if Convert Mulicast to Unicast is enabled. All packets forwarded on match even if no client sends an IGMP Report to join |
Configure IGMP Snooping in SSID Profile
IGMP is Internet Group Management Protocol (IGMP). IGMP snooping is the process of listening to IGMP network traffic. Enabling IGMP Snooping for a selected SSID blocks the multicast packets if no client joins the multicast group. Enabling the IGMP snooping does not convert the packets from multicast to unicast until you specifically enable Multicast to Unicast.
To know more about parameters required in configuring IGMP Snooping refer IGMP Snooping Parameters.
- Navigate to
- Scroll down and select IGMP Snooping.
- Enter IP address in IGMP Snooping Exception List.
- Enter Snoop Timeout in minutes.
- Select Convert Multicast to Unicast.
Info:The Convert Multicast to Unicast is disabled by default. You can enable it only if IGMP Snooping is enabled. If you enable Convert Multicast to Unicast, then all the multicast packets are converted to MAC layer unicast packets after passing the snoop check.
- Select the appropriate value for Tag Packets with Selected Priority.
- Click Save.
Target Wake Time
Target Wake Time(TWT) is one of the advanced features of Wi-Fi 6. It enables access points (AP) and stations (STAs) to negotiate schedules for active and sleep durations.
TWT is beneficial for the following reasons:
- Pre-defined schedules allow STAs to manage their power consumption more effectively, thus helping conserve energy. STAs need to wake up only during the designated Service Periods (SP) to transmit and receive data.
- TWT can help reduce contention by time slicing. Individual STAs or STA groups can be assigned different SPs by the AP to ensure that contention within a BSS is limited to only the clients that have overlapping SP.
TWT Modes
TWT can be deployed in two modes: Individual and Group. Individual TWT allows each STA to independently negotiate one or more TWT sessions with its AP.
To understand more about TWT protocol, refer to TWT Help Article.
Enable TWT in CV-CUE
- Go to
- Navigate to your SSID and go to the RF Optimization tab.
- Select Individual under the Target Wake Time setting and click Save.
SSID WiFi 7 Setting - Multi-Link Operation
The WiFi 7 tab contains MLO setting.
Multi-Link Operation
Until now, a multi-band client (for example, a phone with 2.4, 5, and 6 GHz radios) could connect to an AP using only one of the bands. Therefore, only one connection link formed between the client and the AP. Multi-link Operation (MLO) is the capability of the client and the AP to connect to more than one band simultaneously establishing multiple links. The clients that are capable of communicating with each other over multiple radio links at the same time are called Multi-Link Devices (MLD).
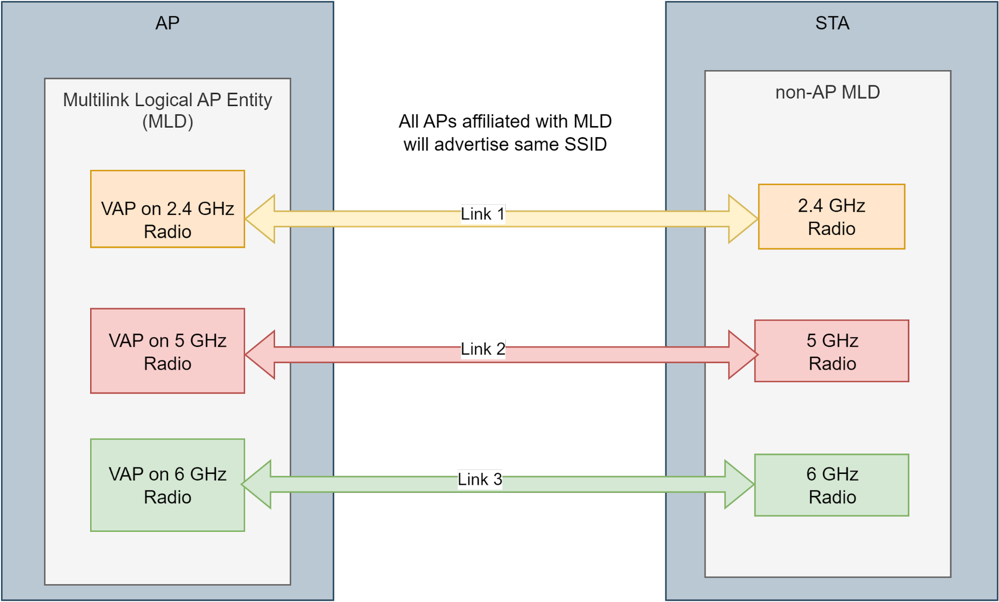
Enable MLO
MLO is a per-SSID configuration.
To enable MLO for the selected SSID:
- Go to CONFIGURE > WiFi > SSID.
- Open a new SSID or edit an existing one.
- Select the WiFi 7 tab and select the Mutli-Link Operation checkbox.
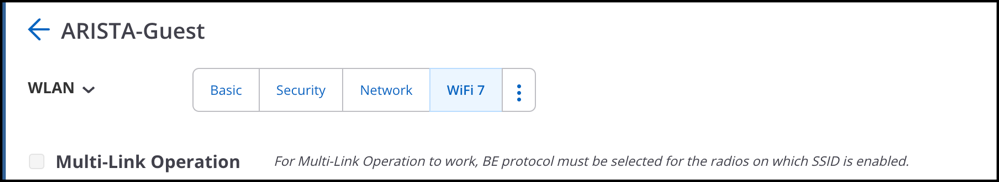
- Save the settings.
Verification
MLO Client Details
The client view tab is divided into 2 grids, client view and link view.
Client View
Link View
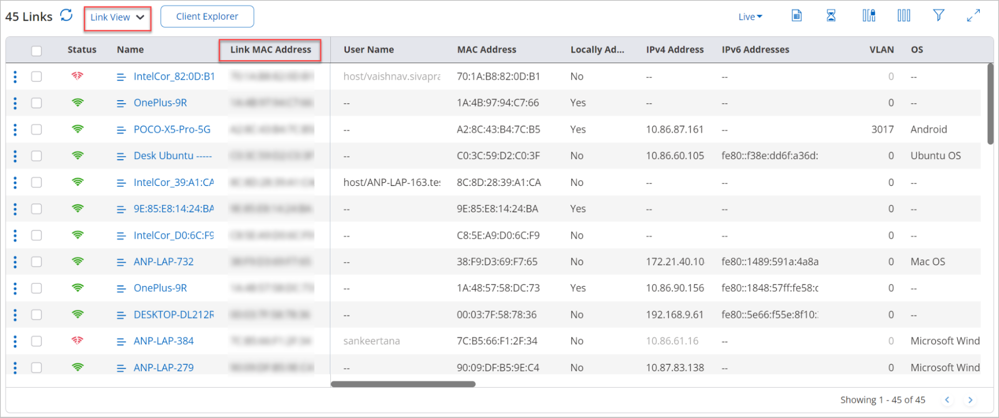
You can view the same information in a graphical format through the Link Explorer.
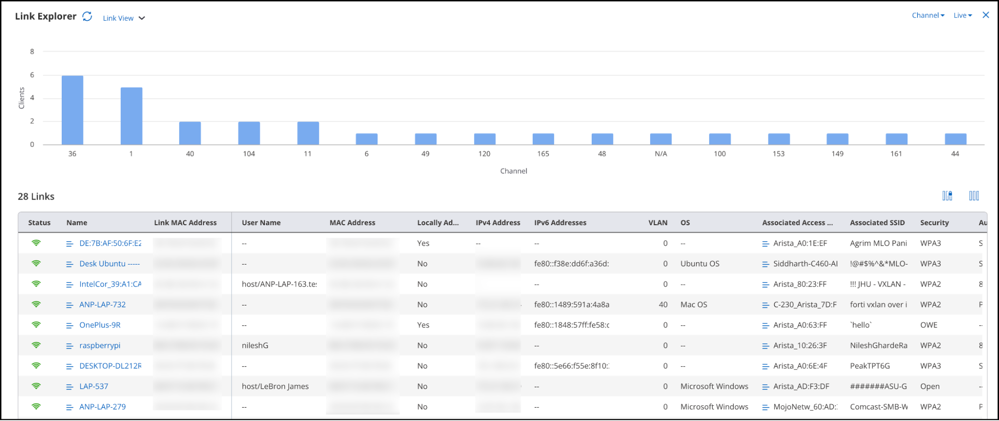
Wi-Fi Analytics for MLO Clients
- Overview Dashboard
- Connectivity Chart:
- Baseline - Clients Affected by Failure
- Performance Charts:
- Baseline - Clients Affected by Poor Performance
- Clients by Avg. Data Rate
- Clients by RSSI
- Clients by Retry Rate %
- Network Usage
- Application Charts:
- Application Experience
- Baseline - % Poor Application Experience
SSID Traffic Shaping and QoS
You can optimize bandwidth utilization and Quality of Service (QoS) settings for this SSID on the Traffic Shaping & QoS tab.
Traffic Shaping
You can restrict the upload and download bandwidths on the SSID. Such restrictions could be really useful for Guest or student SSIDs, for example. You can also limit the number of simultaneous associations that the SSID allows.
Depending on how you have set up the SSID, the bandwidth limits could come from a source other than the Traffic Shaping parameters defined here. For example, enterprise networks often use RADIUS servers to propagate network policies across APs. Users are divided into groups and policies are applied to each group. So the Sales group might have different bandwidth limits than those of the HR group. In such cases, the bandwidth limits could come from the RADIUS server. If an AP does not get values from the RADIUS server, it uses values defined on the Traffic Shaping & QoS tab.
- From a RADIUS server being used for authentication by an external Captive Portal. This is if you have configured an external Captive Portal on this SSID and that portal uses a RADIUS server to propagate policies.
- From a Captive Portal on Arista Cloud. This is if you have configured the SSID to use a Captive Portal on Arista Cloud.
- From a RADIUS server when you have configured the SSID to use 802.1X security.
- From the values defined here, in the Traffic Shaping & QoS tab on the Arista server.
Typically, only one of the above sources will apply. For example, if you have defined an external Captive Portal on this SSID, then obviously there is no portal on the Arista Cloud for this SSID. The only possibility is that a RADIUS server or a Captive Portal does not pass bandwidth control values on to an Arista AP, in which case the values defined in Traffic Shaping & QoS apply.
You can limit the data rate for Unicast traffic between a minimum and maximum value. The Set the data rate for multicast, broadcast and management traffic to parameter sets the Basic or Mandatory rate of the AP. This not only controls the data rate at which broadcast / multicast packets are sent but also sets the data rate at which Beacons are sent. You must set this rate carefully. Increasing the basic rate of the AP does reduce the transmission airtime, but it also reduces the effective coverage area. This could cause problems for the client if the AP's coverage at the client is not enough for that data rate. For example, real-time streaming of audio and video are applications that commonly use multicast packets for delivery. If clients have problems receiving multicast packets because the AP coverage is not good enough to support higher data rates, they will experience choppy audio or pixilation and screen freezing.
| Arista Attribute | RADIUS Attribute |
|---|---|
| Per-user download limit | 5 |
| Per-user upload limit | 6 |
QoS
Quality of Service determines the priorities assigned to various types of traffic. Applications such as voice over IP, video, and online games need a service guarantee. When network bandwidth is shared, defining priorities becomes a must for such applications. You must define the QoS parameters if you are using the SSID for such applications. QoS ensures that applications that need higher priority get it. The service guarantee for such applications is met by allocating adequate bandwidth based on the QoS priority.
- Type of Service (TOS) - a field in older versions of IPV4 header.
- Differentiated Services Code Point (DSCP) - the TOS field redefined for better QoS differentiation. DSCP is also specified in the IP header.
- 802.1p Class of Service - a field in the Ethernet frame
- 802.11e Wi-Fi Multi-Media (WMM) - an 802.11 enhancement that alters MAC-layer behavior based on the traffic type
For an 802.11n AP, Wi-Fi Multimedia (WMM) is mandatory. For 802.11n APs, if you do not enable QoS, the system uses the default QoS parameters.
- SSID Priority is Voice
- Priority Type is Ceiling
- Downstream Mapping is DSCP
- Upstream Marking is enabled and the value is 802.1p Marking
The system applies user-configured QoS settings if you enable QoS.
- Fixed:Select this if you want all traffic transmitted on this SSID to have the selected priority, irrespective of the priority indicated in the 802.1p or IP header. For example, you could set all traffic to Background, in which case the SSID treats even voice and video packets as Background traffic.
- Ceiling:Select this if you want traffic on this SSID to have priorities equal to or lower than the selected priority. For example, if you set SSID Priority to Video and Type to Ceiling, the SSID differentiates Background, Best Effort, and Video traffic but not Voice, since that is higher than Video. In effect, it treats Voice and Video equally.
If you select Fixed, CV-CUE grays out the Downstream Mapping, since all traffic is marked with the selected priority and there is no downstream mapping to be done. If you select Ceiling, however, you can choose from among DSCP, 802.1p or TOS to map downstream traffic.
| DSCP / TOS / 802.1p Class of Service | 802.11e/WMM access category |
|---|---|
| 0 (Background) | 1 (Background) |
| 1 (Best Effort) | 0 (Best Effort) |
| 2 (Excellent Effort) | 3 (Best Effort) |
| 3 (Critical Apps) | 4 (Video) |
| 4 (Video) | 5 (Video) |
| 5 (Voice) | 6 (Voice) |
| 6 (Internetwork Ctrl) | 7 (Voice) |
| 7 (Network Ctrl) | 7 (Voice) |
| 802.1p Class of Service | DSCP | 802.11e/WMM Access Category |
|---|---|---|
| 1 | 0 | 0 |
| 0 | 10 | 1 |
| 0 | 18 | 2 |
| 2 | 0 | 3 |
| 3 | 26 | 4 |
| 4 | 34 | 5 |
| 5 | 46 | 6 |
| 6 | 48 | 7 |
Configure Traffic Shaping
Traffic Shaping helps in effective utilization of network bandwidth by setting an upload and download limit for the network, restricting the number of client association, band steering etc. You can opt for one or more of these ways depending on the network traffic, the applications used on the SSID, and the Arista device model in use.
- Navigate to
- You can limit the upload and/or download bandwidth on an SSID in SSID Bandwidth Control. To restrict the upload bandwidth on the SSID:
- Select Limit the maximum upload bandwith on the SSID to and enter a data rate, from 0 through 1024 Kbps, to restrict the upload bandwidth for the SSID to the value specified here.
- Select Limit the maximum download bandwith on the SSID to and enter a data rate, from 0 through 1024 Kbps, to restrict the download bandwidth for the SSID to the value specified here.
- You can limit the number of clients associating with an SSID per radio. To limit the number of clients association:
- Select the Limit maximum number of simultaneous associations to, if you want to specify the maximum number of clients that can associate with an SSID per radio.
- Specify the maximum number of clients in the field below to the Limit maximum number of simultaneous associations to field.
- You can specify the minimum and maximum data rate for the AP-client communication in Unicast Rate Control. To specify a minimum and maximum data rate:
- Select Limit the maximum unicast traffic data rate to and Specify the minimum data rate for communication in the field below the Limit the minimum unicast traffic data rate to field.
- Select Limit the maximum data rate for unicast traffic to and Specify the maximum data rate for communication in the field below the Limit the minimum unicast traffic data rate to field. Maximum threshold for minimum as well as maximum data rate is 54 Mbps.
- Select Apply to all clients, including 802.11n and higher if you wish to apply the specified maximum data rate for unicast traffic to all clients, including those that support higher data rate 802.11 protocols.
- Click Save.
Configure Quality of Service (QoS)
Quality of Service determines the priorities assigned to various types of traffic. The service guarantee is imperative in case of streaming multimedia applications, for example, voice over IP, video, online games etc.
Before you configure Quality of Service settings for the SSID, refer SSID Traffic Shaping and QoS to understand the Quality of Service concept.
- Navigate to
- Scroll down and Select QoS to define your own QoS settings for Wi-Fi multimedia on the SSID profile.
- Select Enforce WMM Admission Control.
Info:This field helps you specify whether the admission control parameters configured in the device template applied to the Arista device must be enforced for the network. The admission control parameters are configured under Radio Advanced Settings for Arista devices functioning as access points.Note:The WMM Admission Control settings configured for the radio on which the Wi-Fi profile is applied, override the QoS Settings configured in the Wi-Fi profile.
- Select voice, video, best effort or background as the SSID Priority depending on your requirement.
- Select Priority Type as Fixed or Ceiling.
Info:Priority Type is selected as Fixed if all traffic of this SSID has to be transmitted at the selected priority irrespective of the priority indicated in the 802.1p or IP header. Priority Type is selected as Ceiling if traffic of this SSID can be transmitted at priorities equal to or lower than the selected priority.
- Downstream mapping option is enabled if Priority Type is selected as Ceiling. Select the appropriate Mapping Type.
Info:The priority is extracted from the selected field (802.1p, DSCP or TOS) and mapped to the wireless access category for the downstream traffic subject to a maximum of the selected SSID Priority. For the downstream mappings, the mapping depends on the first 3 bits (Class selector) of the DSCP value, TOS value or 802.1p access category. The only exception will be DSCP value 46 which will be mapped to WMM access category 'Voice'.
- Select the Upstream marking option as per the requirement.
Info:The incoming wireless access category is mapped to a priority subject to a maximum of the selected SSID priority and set in the 802.1p header and the IP header as selected.
- Click Save.
SSID Scheduling
If you want to limit the duration for which the SSID is active, you can define a schedule for the SSID.
You can also specify if an SSID is to be permanently active or valid for only a limited time duration. This could be useful if, for example, you have an event coming up for which you want to use a special Guest SSID with a different splash page. Another use case might be to restrict employee SSID use to office hours. When you enable Select Timeslot, CV-CUE shows a calendar view of the week split into days (rows) and hours (columns). You can then go ahead and select the timeslots when you want the SSID Turned On.
Configure SSID Scheduling
After you create a SSID profile, by default, the profile remains active throughout until you delete it. However, you can make a SSID available or active only for a limited time period, or only for a limited number of hours during the day, by using the SSID scheduling feature.
- Navigate to
- Click Add New SSID.
- Click menu icon (three vertical dots) next to Network tab.
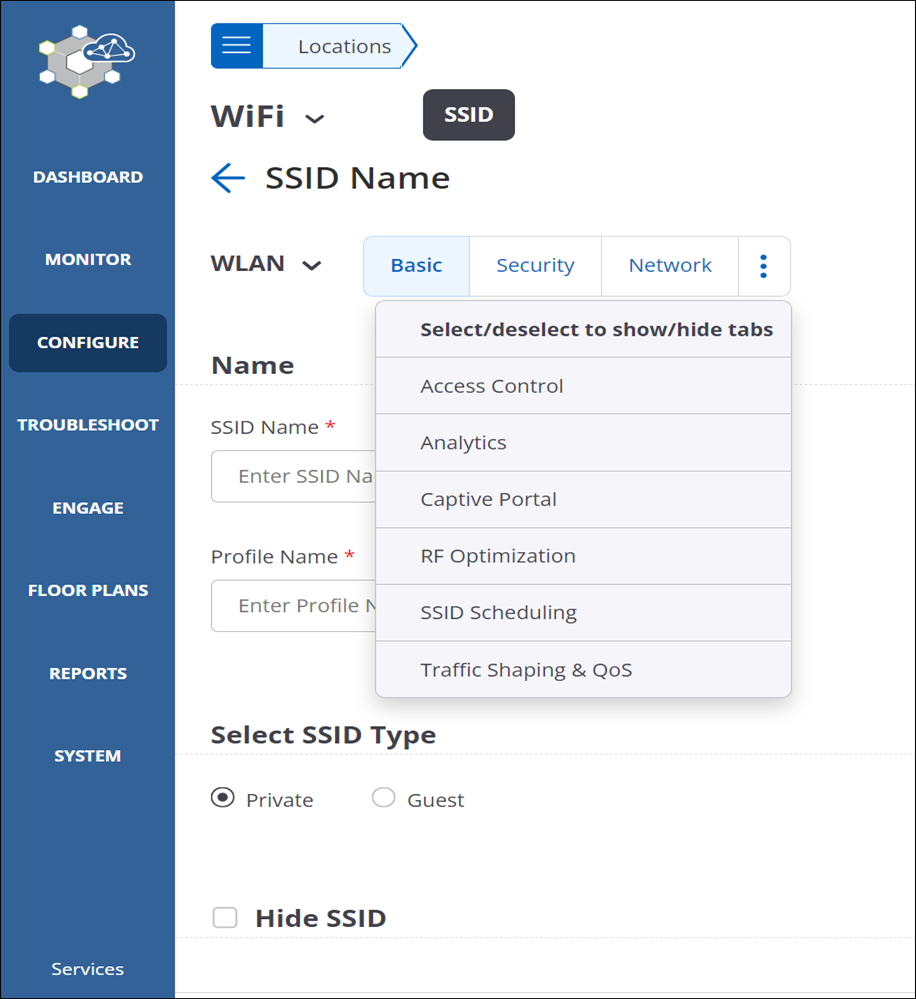
- Select SSID Scheduling.
- Select Validity Type as Now to Forever or Custom depending on you want to keep a SSID active throughout or for specific hours.
Info: Now to Forever indicates that the SSID is deployed permanently. Selecting Custom enables From and To fields.
- If you select Custom as validity type then specify start and end date in From and To fields.
- Select Select Timeslot.
- Select the active timeslots for the SSID.
Info:Active timeslots is the time during which the SSID is active. The minimum active time duration that you can select is 30 minutes. Click between the squares representing the time of the day (12 a.m. - 11 p.m.) to select the desired active intervals. The blue color indicates active duration and the white color indicates inactive duration.
- Click Save.
Hotspot 2.0
Hotspot 2.0 is a standard for public-access Wi-Fi that enables seamless roaming among Wi-Fi networks and between Wi-Fi and cellular networks. With Hotspot 2.0, Passpoint-certified mobile devices such as laptops and smartphones can automatically discover and connect to Wi-Fi networks without the need of signing in manually. It is based on IEEE 802.11u standard for Interworking with External Networks.
Hotspot 2.0 works only with WPA2 802.1x, WPA3 Enterprise or WPA3 Transition Mode. Ensure that you have configured the RADIUS Server and 802.11w Management Frame Protection is set as Required or Optional.
Hotspot 2.0 Settings
The Hotspot 2.0 settings for an Arista AP are divided into Network Settings, Roaming, Venue, Domain, NAI Realms, Friendly Names, Connection Capabilities and QoS Mapping.
This topic contains the following subtopics:
Hotspot 2.0 Network Settings
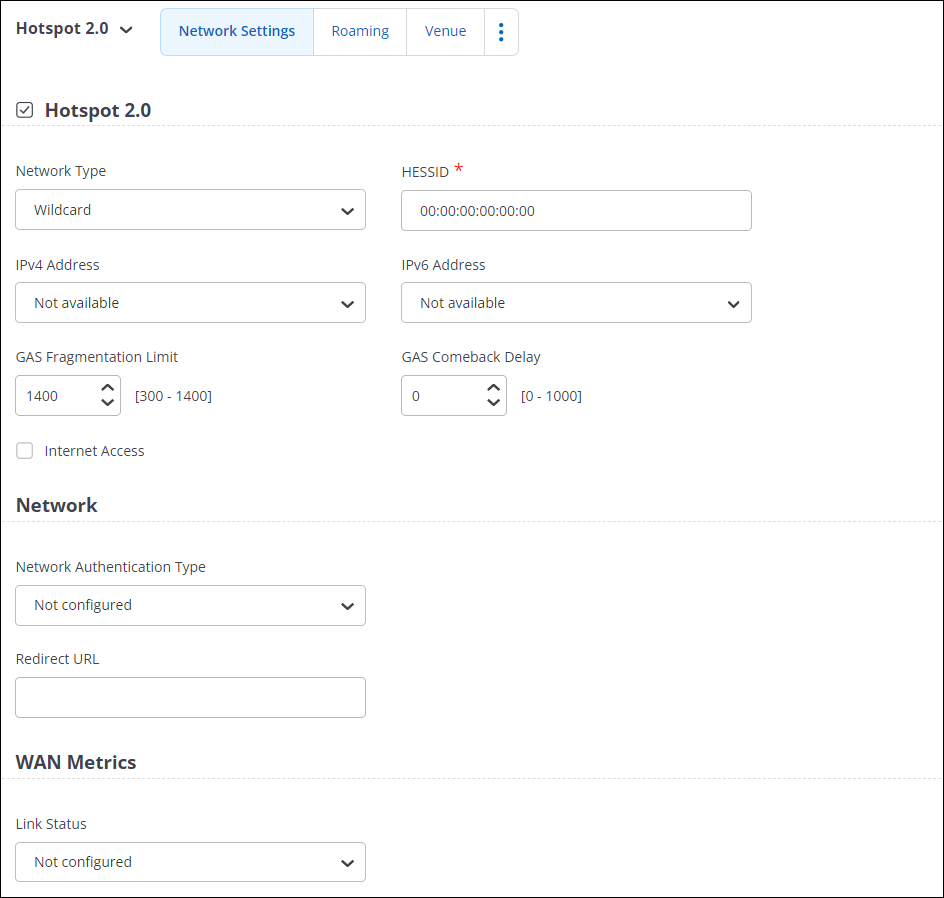
- Network Type: The type of the network.
- HESSID: HESSID stands for Homogenous Extended Service Set Identifier. It is used to identify hotspot AP. APs with the same HESSID have the same hotspot configuration.
- IPv4 Address: Select the appropriate IPv4 Address from the available options.
- IPv6 Address: Select the appropriate IPv6 Address from the available options
- GAS Fragmentation Limit: The maximum allowed size, in bytes, for the GAS response frame above which frame fragmentation needs to be done. Default value is 1400 bytes.
- GAS Comeback Delay: The comeback delay, in milliseconds, between initial GAS response and first comeback request.
- Internet Access: Select this checkbox if the network provides internet access to the client through the AP.
- Network Authentication Type: Select the network authentication type from one of the following options:
- Terms and conditions - Select this option if the network requires the user to accept terms and conditions.
- Online enrollment - Select this option if you want the user to enroll online.
- Https redirection- Select this option if the user is redirected for authentication.
- DNS redirection- Select this option if the network supports DNS redirection.
- Not configured- Select this option if you don't want to provide specific information when the client queries about network authorization type.
You can also provide the Redirect URL if you want the client to be redirected after connecting to the access point.
- Link Status: Select the status of the link
- Symmetric Link Status: Select the Same option if the uplink and downlink speeds are the same. Select the Different option if the uplink and the downlink speeds are different.
- Uplink Speed: Enter the uplink speed in Kbps or Mbps.
- Downlink Speed: Enter the downlink speed in Kbps or Mbps.
Hotspot 2.0 Roaming Settings
Enter the roaming consortium list using hex characters. Roaming consortium consists of one or more organization identifiers that are unique hexadecimal strings.
Hotspot 2.0 Venue Settings
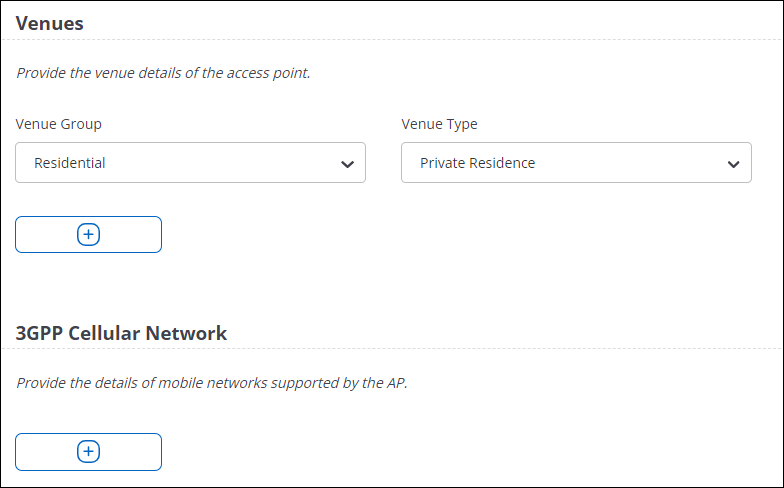
Venue Details
Venue details consist of venue groups and venue types. Select the venue group from the available options and based on the venue group, select your venue type.
3GPP Cellular Network
Provide the list of mobile networks supported by the access point.
Hotspot 2.0 Domain Settings
Under the Domain tab, provide the list of Hotspot 2.0 operator domain names.
Hotspot 2.0 NAI Realms Settings
The NAI Realm List corresponds to the NAI realm element. The NAI realm element provides a list of network access identifier (NAI) realms corresponding to service providers whose networks are accessible through the AP. A list of one or more EAP Methods is optionally included for each NAI realm.
Hotspot 2.0 Friendly Name Settings
Under Friendly Name, enter the friendly name of the Hotspot 2.0 operator in different languages along with their language code. You can provide up to 32 operator friendly names.
Hotspot 2.0 Connection Capabilities Settings
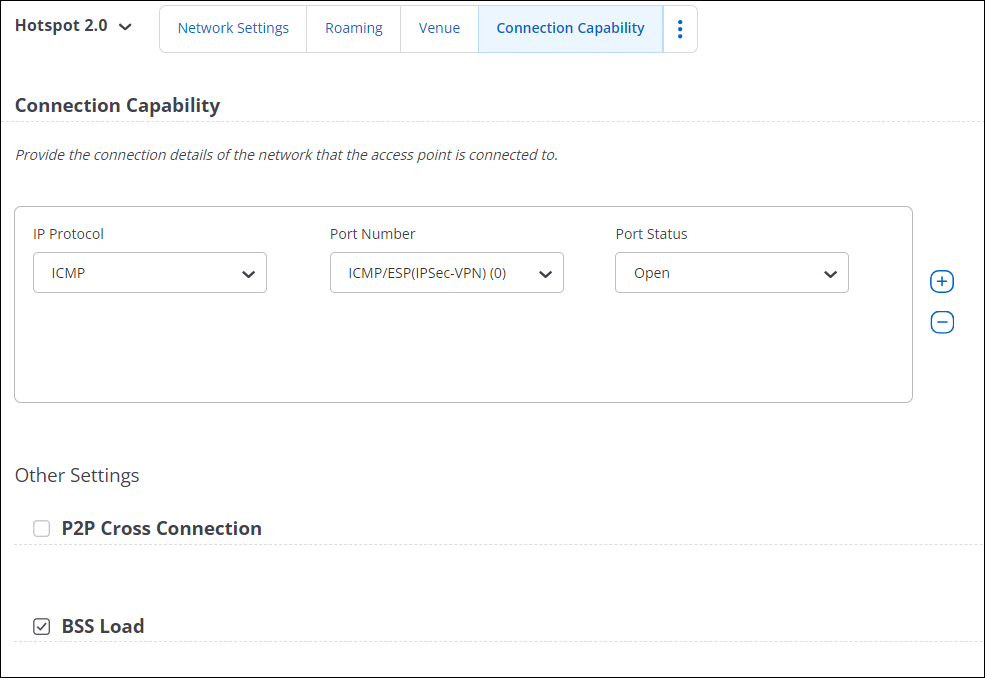
Specify the protocols supported by the network connection and the corresponding port numbers and the port status.
P2P Cross Connection
Enable P2P Cross Connection to allow the client to bridge the Wi-Fi direct network and the infrastructure network.
BSS Load
Enable BSS Load to include BSS Load element in the beacons and probe responses. The BSS Load element contains information on the number of currently associated stations and traffic levels in the BSS.
Hotspot 2.0 QoS Mapping Settings
Enter the QoS Mapping, only if required. The DSCP exception indicates the priority to be assigned when the specified DSCP value is detected in data packets. The value 255 indicates that the row is ignored.
Configuring a SSID with Hotspot 2.0
To configure a SSID profile with Hotspot 2.0:
- Click
- Click Add SSID.
- Enter the Profile Name and SSID Name.
- Under the Security section, select WPA2, WPA3 or WPA3 Transition Mode as the Security Level for Association.
- Select 802.1X and configure the RADIUS Settings.
- Set 802.11w Management Frame Protection as Optional or Required.
- Configure the required Network, Captive Portal, Firewall, and Traffic Shaping & QoS settings.
- Click Hotspot 2.0 from the WLAN drop-down menu.
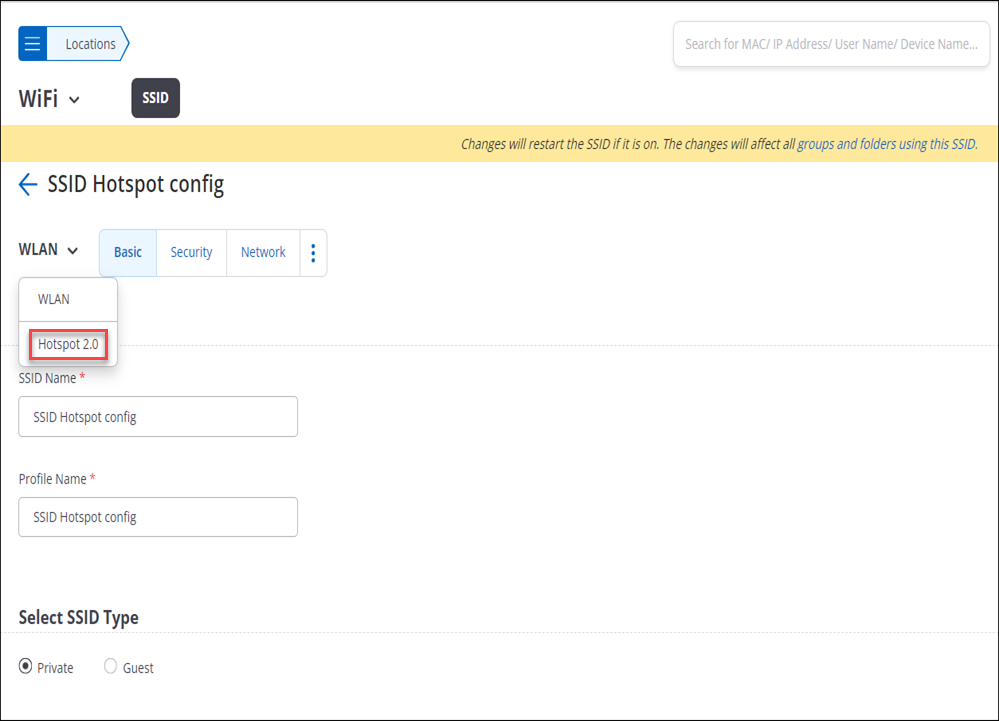
- Enable Hotspot 2.0.
- Configure all the Hotspot 2.0 settings.
- Save and turn on the SSID.
Configuring a Wi-Fi Profile for an AP Connecting to Online Sign-up Servers
A Hotspot 2.0 compatible mobile client can subscribe to online sign up servers from various service providers through a Hotspot 2.0 compliant Arista AP. The mobile client can choose an online service from the list of available online services and sign up for the chosen service through the Arista AP.
- Click
- Click Add SSID.
- Enter the Profile Name and SSID Name.
- Under the Security section, select Hotspot 2.0 OSEN.
- Configure the RADIUS Settings.
- Save the SSID settings.
Managing SSID
Turn an SSID On
You need to turn an SSID on before it becomes available for access to users.
- You can turn on a new SSID once you are done configuring it, or you can turn an existing SSID on.
Choose from:
- If you are adding a new SSID, you can click Save & Turn SSID On after you are done configuring at least the three mandatory SSID tabs (Basic, Security and Network).
- If you are turning an existing SSID on, just go to Configure and click the OFF / ON switch on the SSID you want to turn on.
- Select whether you want the SSID on the 2.4 GHz, 5 GHz , or 6 GHz bands and click Turn SSID On. You will also see the Dual 5 GHz mode option with Lower 5 GHz and Upper 5 GHz options in the Turn SSID On page if you have enabled Dual 5 GHz in the Radio Settings tab.
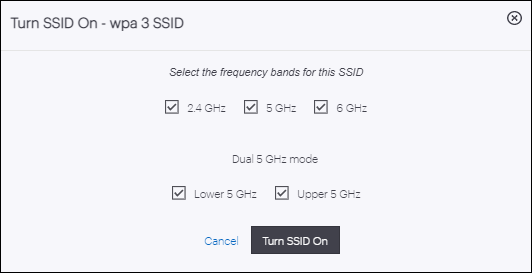
Choose from:
- Some features in an SSID depend on Background Scanning under CONFIGURE > Device settings. If you have enabled any such features on the SSID, but you have not enabled background scanning, then the dialog window prompts you to do so. Click Continue on the dialog window. This takes you to stage 2, where CV-CUE recommends that you turn background scanning on. You can still turn the SSID on without enabling background scanning, but features in the SSID that depend on background scanning might not work properly.
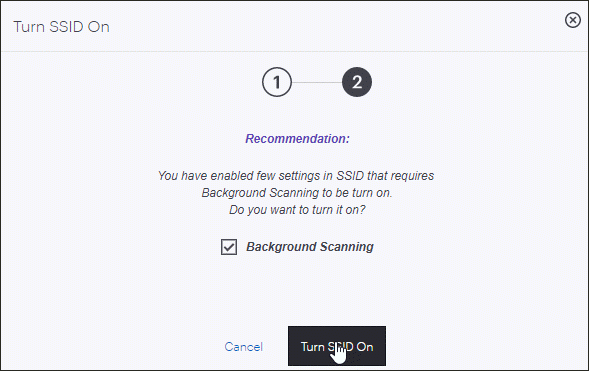
- Some features in an SSID depend on Background Scanning under CONFIGURE > Device settings. If you have enabled any such features on the SSID, but you have not enabled background scanning, then the dialog window prompts you to do so. Click Continue on the dialog window. This takes you to stage 2, where CV-CUE recommends that you turn background scanning on. You can still turn the SSID on without enabling background scanning, but features in the SSID that depend on background scanning might not work properly.
Edit an SSID
You can modify an existing SSID.
- Go to
- On the SSID you want to edit, click Edit (the pencil icon).
- To modify the settings on any of the SSID tabs, simply click the tab you want to edit. If the tab you want to edit is not visible, click the Menu icon (three vertical dots) next to the Network tab to see all the SSID tabs.
- Click Save to save the SSID or click Save & Turn SSID On to save and turn it on.
Delete an SSID
You can delete an SSID from a location
- Go to
- On the SSID you want to delete, click the Menu icon (three vertical dots) and select Delete.
- Click Delete.
Create a Copy of an SSID
You can create a copy of an SSID at the same location or at a different one.
- Go to
- On the SSID you want to duplicate, click the Menu icon (three vertical dots) and select Create a Copy.
- Select Currently Selected Folder to create a copy of the SSID in the current folder or At a Different Folder to create a copy of it at a different location, and click Continue.
Choose From:
- If you chose Currently Selected Folder, an appropriate message appears and you can see a copied SSID in the current location.
Note: If you copy the SSID at the current location, the SSID Profile Name is different for the copied copy. For example, if you copy "ABC Corp" at the same location, then the new SSID name will be "ABC Corp" but its profile name will be "Copy of ABC Corp(1)".
- If you chose At a Different Folder, the location hierarchy appears on the right pane window. Select the location where you want the SSID copied and click Create a Copy. An appropriate message appears.
- If you chose Currently Selected Folder, an appropriate message appears and you can see a copied SSID in the current location.
Location Based VLAN Mapping
Location-based VLAN mapping takes precedence over SSID VLAN mapping. As VLAN mapping is not inherited, you must map the VLAN ID to VLAN Name for each floor in a location hierarchy.
- Go to
- Navigate to your SSID and click Location Based VLAN Mapping from the three-dot more menu.
- Add the VLAN name, ID, and provide the location for the mapping.
- Save the settings.
Customize SSID Attributes for Location-Specific Overrides
Network Administrators can create SSIDs at any location in CV-CUE, and the same SSID can be inherited from a parent to a child location. The inherited SSIDs, by default, share the same attributes as the parent location. Administrators can override certain attributes of SSID at a child location without breaking the inheritance, so that the entire SSID configuration remains the same, except for the overridden attributes.
Overriding SSID attributes is useful if you want to have the same SSID configurations across your organization but want to have specific attributes for specific locations. For example, you can have the same corporate SSID across your geography but want a different RADIUS server for each location.
Note: Overriding SSID attributes is not supported for floors; it is available only for folders.
Attributes You Can Edit
- L2 Tunnel Interface in the Network tab
- VLAN Name
- VLAN ID
- Fallback VLAN ID
- SSID VLAN Mapping
- VLAN Pool
- RADIUS Pool
- RADIUS Authentication and Accounting Servers (Primary and all additional servers)
Override SSID Attributes
To override any SSID attribute:
- Select the location and then select Configure > WiFi.
- From the SSID list, select the three-dot menu for the SSID and select Customize SSID Attributes.
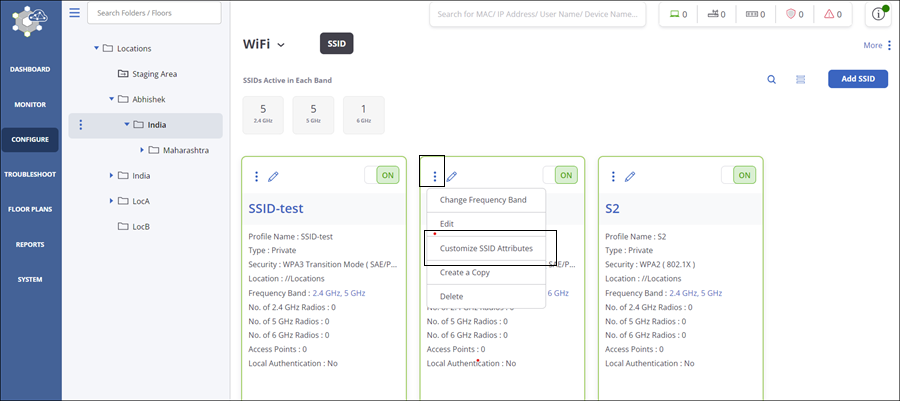
You see a table comparing the SSID attributes of the current folder and its parent folders side-by-side. - Select the Edit icon to edit the SSID’s attributes. You can edit one folder at a time.
- Save the changes by clicking the Save icon (check mark icon).
Compare Attributes Across Locations
You can select up to 10 locations to compare SSID attributes. To compare attributes across locations:
- Select the location and then select Configure > WiFi.
- From the SSID list, select the three-dot menu for the SSID and select Customize SSID Attributes.
You see a table with a side-by-side comparison of the SSID attributes between the current folder and its parent folders. The farthest column towards the right is the current folder. All its parent folders, up to the root folder where the SSID was created, are displayed towards the left of the current folder.
- Select the Edit icon to edit the SSID’s attributes. You can edit one folder at a time.
- Save the changes by clicking the Save icon (checkmark icon).
Inherit from Parent Vs. Manually Providing the Parent Value