Rotating Internal Certificate Authority
The streaming agent used by EOS devices and other applications that communicate with each other in CloudVision uses mutual TLS certificates signed by a local certificate authority (CA). To prevent the CA from expiring in the future, you should rotate the CA. Once rotated, by default, the CA becomes valid for a hundred years. This process re-signs the certificates used by each EOS device's streaming agent and internal applications that communicate with CloudVision. The streaming agent version on all devices must be at least 1.26.0 to use this feature.
You get the first notification through an event message around 90 days prior to the certificate expiry.
To rotate a certificate, go to Settings (gear icon) > Certificates on the CloudVision portal. The CA rotation process takes several minutes, and it is necessary to plan a maintenance window before rotating a CA. See the images below.
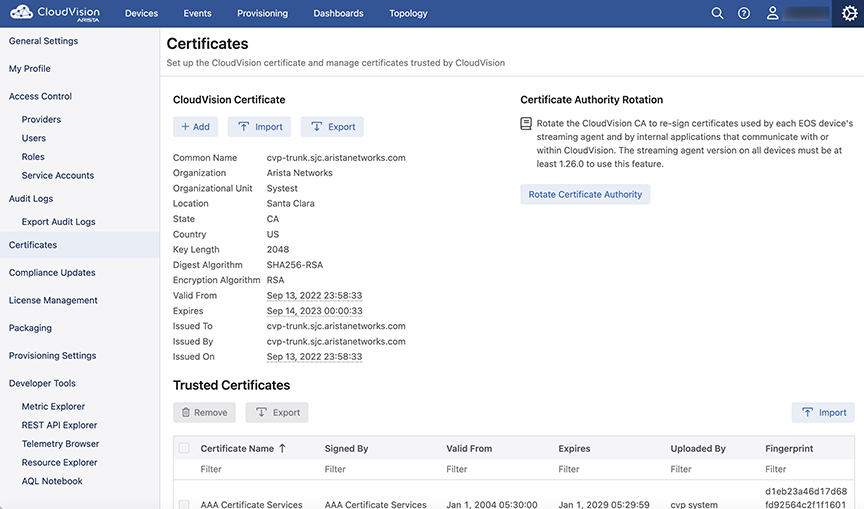
Click Rotate Certificate Authority.
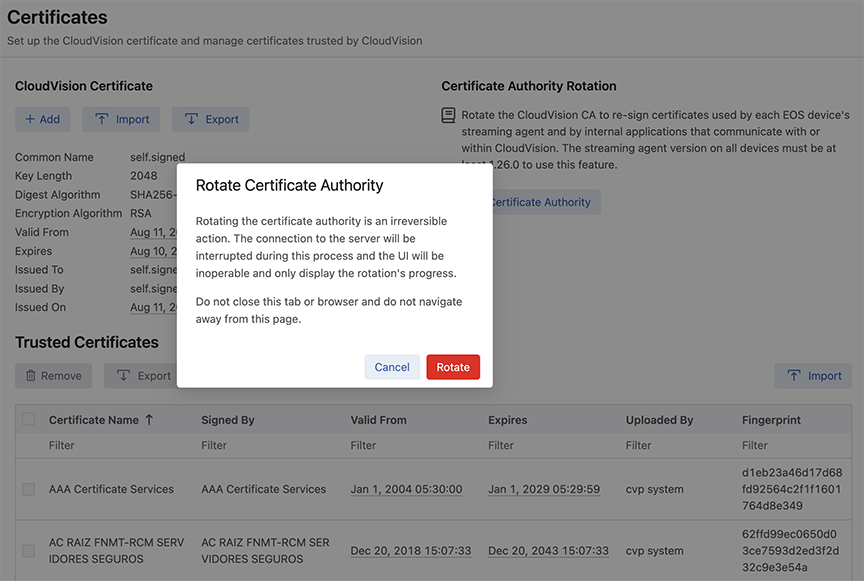
Click Rotate.
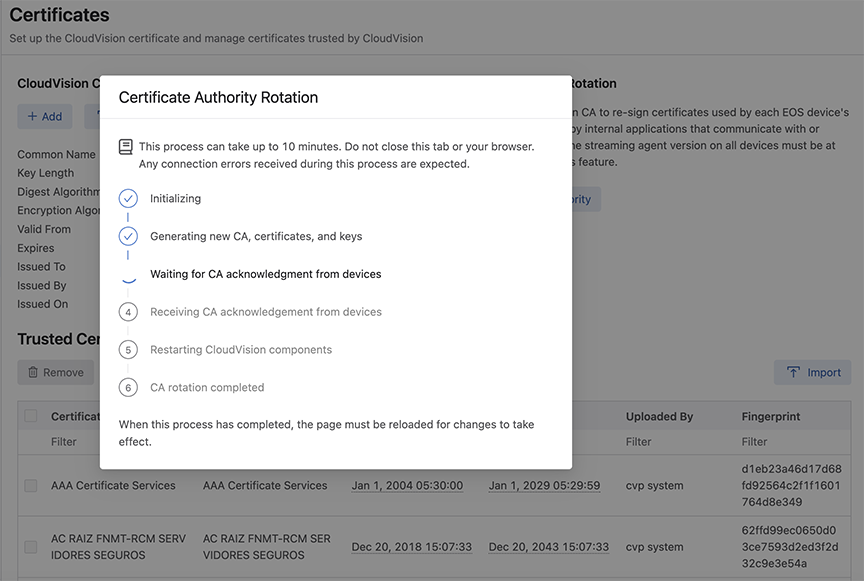
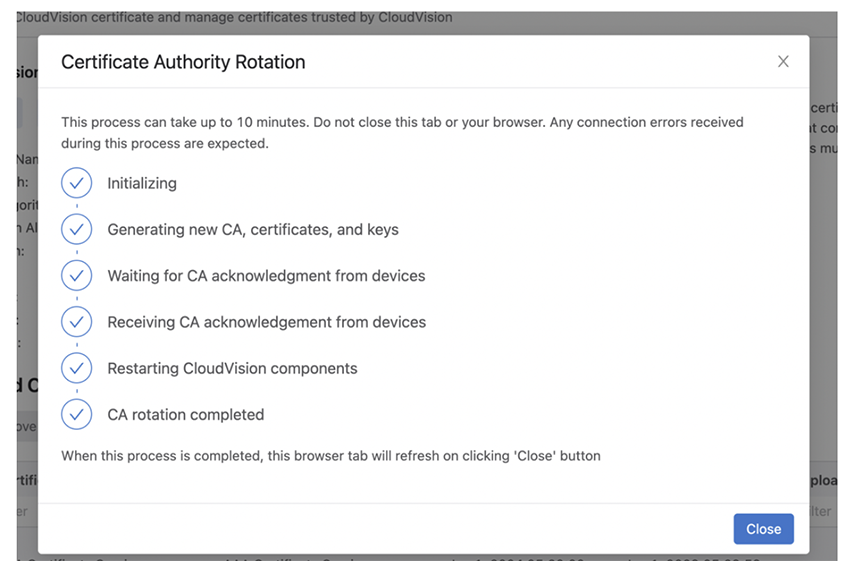
The browser tab refreshes, and the CA rotation is completed. The new CA is now valid for one hundred years and the devices get automatically re-enrolled, and the devices stop streaming momentarily to CloudVision while NGINX reboots.
If you see any errors during the CA rotation process, you can retry the rotation. If the rotation process fails after multiple retries, then you must contact Arista Support team (TAC) for a resolution.
Certificate Authority Expiry
When rotating a certificate authority (CA) you can now define how long the certificate is valid for.
The default value is 100 years. The minimum value that you should enter here is 24 hours. Any new value you enter will be used as the default value in any future rotations.
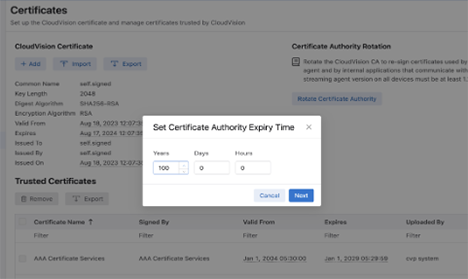
Once the rotation is completed, the new Certificate Authority will be valid for the time you have set.
