External Certificate Authority Configuration
Use an External Certification Authority (ECA) to ensure secure communication and authentication with CloudVision. By default, Streaming Agent and other applications communicate with CloudVision using mutual-TLS certificates signed by a local certificate authority (CA). You now have the option to integrate CloudVision with Venafi, an external CA, to sign and verify these certificates.
When executing a CA rotation, CloudVision will become inaccessible for up to 10 minutes. Only the progress of the rotation will be displayed. If you close the tab or browser or navigate away from this screen, you will not be able to monitor the progress of the configuration.
To rotate an external certificate authority
- Navigate to Settings > Certificates.Note: All devices must be running Streaming Agent version 1.33.0 or higher to configure an external CA. Version 1.33.0 is available from EOS version 4.32.1F. View Streaming Agent and EOS versions for all devices in Devices > Inventory.
- Select Configure External Certificate Authority.
Figure 1. Configure External Certificate Authority 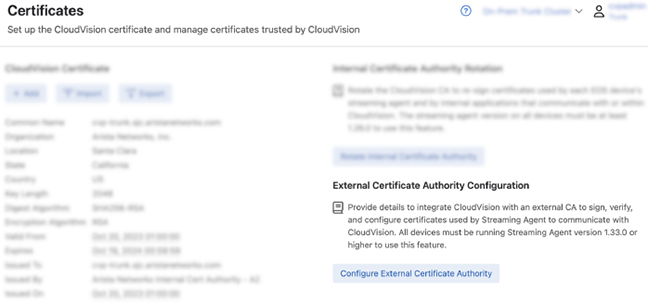
- Certificate Vendor: Select Venaf or Internal
Select Internal to change to authentication via CloudVision’s local CA.
- CA Certificate: Paste the certificate generated by the external CA authority
- Client Zone: Retrieve Client Zone details from your Venafi setup
- Refresh Token: Supply an API Key from your Venafi setup
- Server Zone: Retrieve Server Zone details from your Venafi setup
- URL: Retrieve the URL from your Venafi setup
- Enter the details for the certificate authority.
Figure 2. Certificate Authority Details 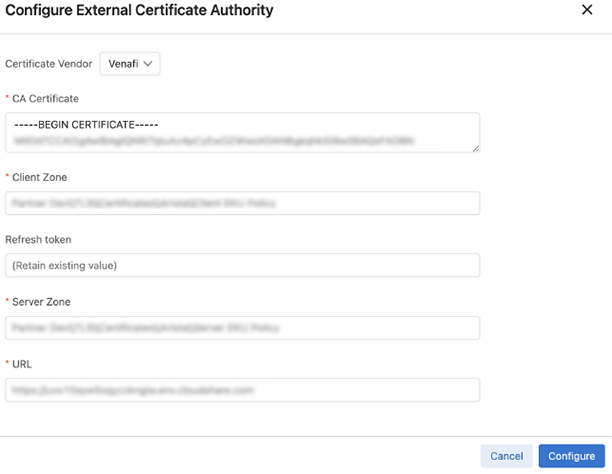
- Click Configure.
The CA rotation will then begin. You will see a modal displaying its process.
The browser tab will refresh, and the CA configuration will be complete. Devices will briefly stop streaming to CloudVision while the web server reboots. They will re-enroll automatically and streaming will resume.
